Azure Networking Infra setup
 bhuvanchand maddi
bhuvanchand maddi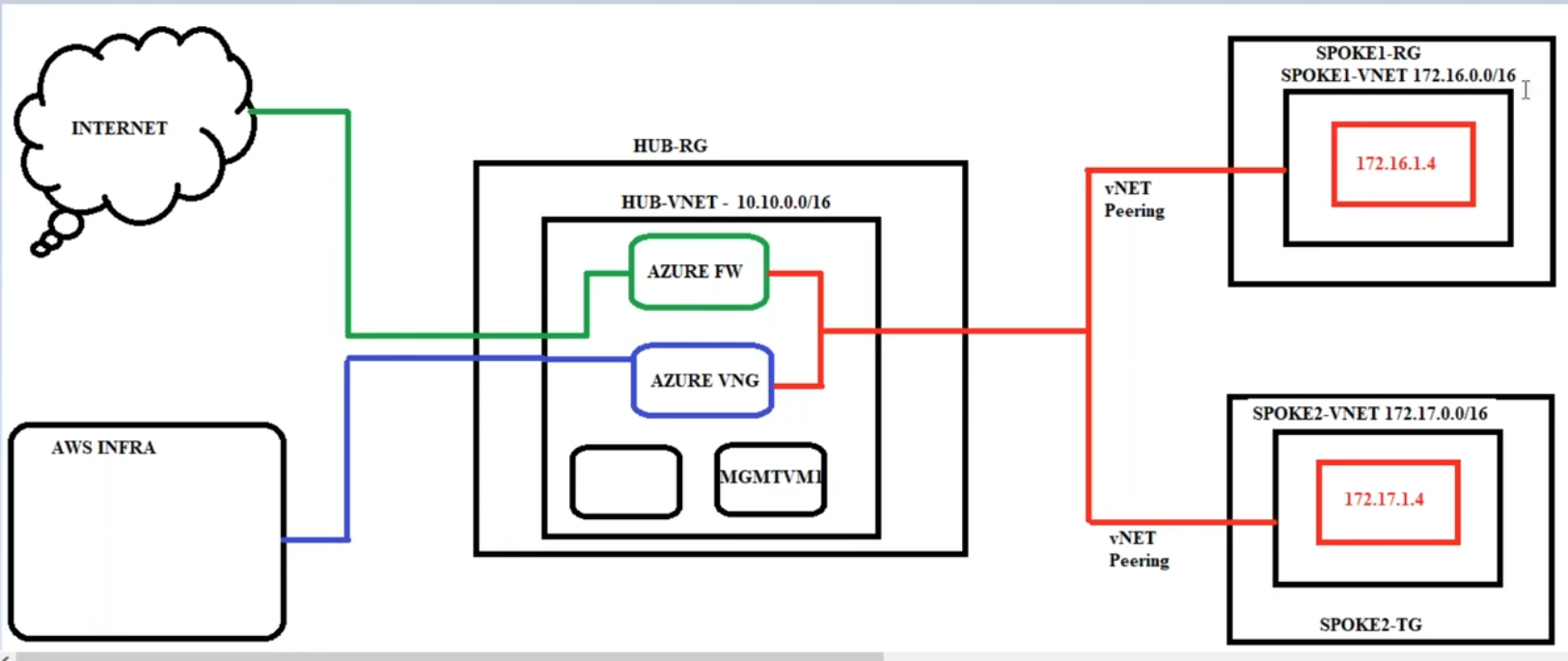
1. Overview
This document provides a step-by-step guide to setting up a basic Azure infrastructure using the Hub-and-Spoke network topology. This model helps centralize network security and routing in the Hub while allowing Spokes to connect securely.
2. Resources to be Created
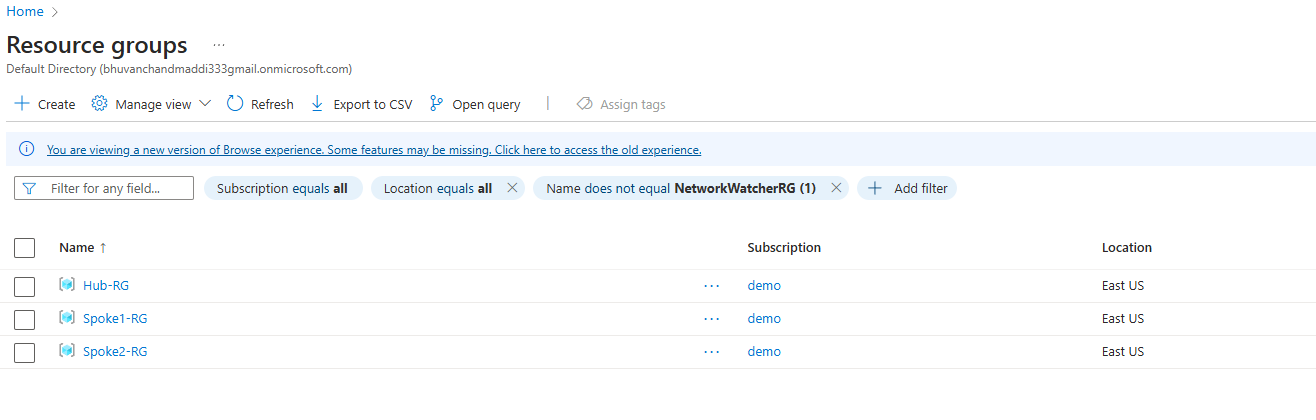
3 Resource Groups:
Hub-RGSpoke1-RGSpoke2-RG
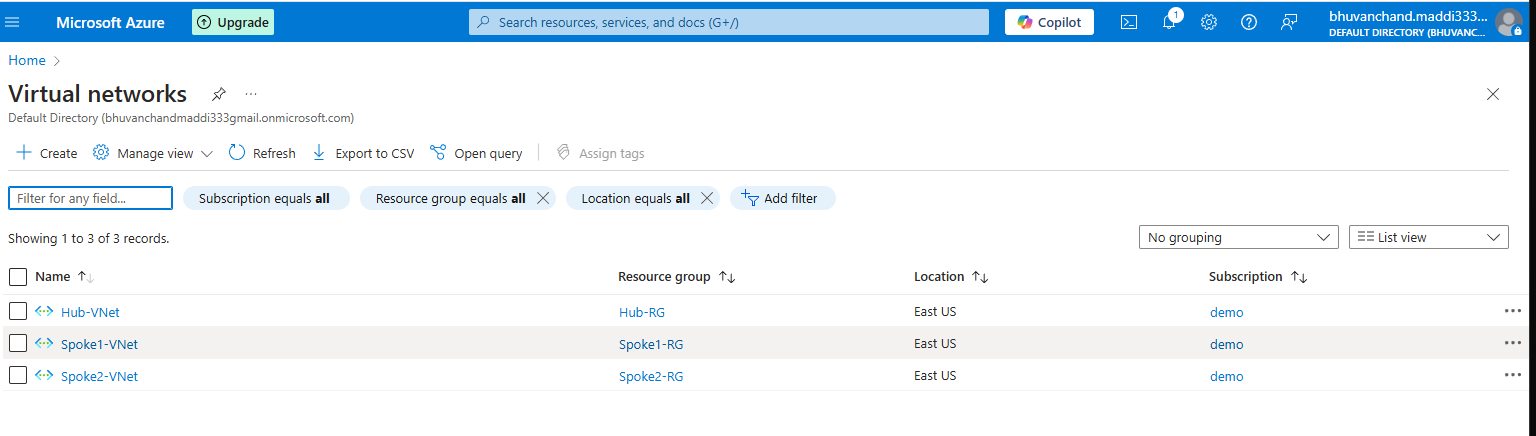
3 Virtual Networks (VNets):
Hub-VNet (10.10.0.0/16)Spoke1-VNet (172.16.0.0/16)Spoke2-VNet (172.17.0.0/16)
Subnets in Each VNet:
Hub-VNet:AzureFirewallSubnet (10.10.1.0/24)(This subnet must be named exactly asAzureFirewallSubnetfor the firewall to function properly.)Management Subnet(10.10.1.0/24)(This is to provision bastion host machine to connect to hosts in spoke vnet`s)
Spoke1-VNet:Workload Subnet (172.16.1.0/24)
Spoke2-VNet:Workload Subnet (172.17.1.0/24)
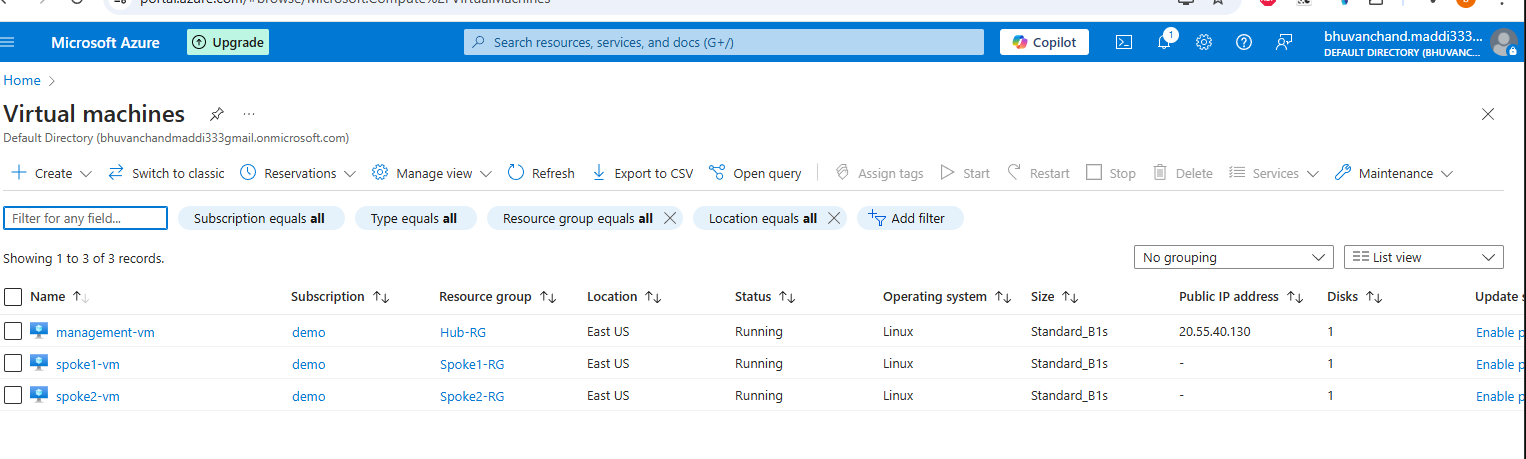
3 Linux Virtual Machines:
One VM in each of the workload subnets (Spoke1 & Spoke2)
One VM in the management subnet (Hub-VNet)
3. VNet Peering
Peer
Hub-VNetwithSpoke1-VNetPeer
Hub-VNetwithSpoke2-VNetEnsure that traffic is allowed between VNets via peering settings.
4. Deploying the Azure Firewall in the Hub
What is Azure Firewall? Azure Firewall is a managed cloud-based network security service that provides threat protection and enforces network security policies across Azure VNets. It acts as a centralized security checkpoint in a Hub-and-Spoke model, ensuring that traffic between the Spokes and outbound traffic to the internet follows security policies.
Why do we need Azure Firewall?
It provides centralized security controls.
It allows secure internet access from Spoke VNets.
It enforces application and network-level policies to allow or block traffic.
Deployment Steps:
Deploy
Azure Firewallin theHub-VNetwithin theAzureFirewallSubnet(which must be named exactly asAzureFirewallSubnet).Assign a static public IP to the firewall.
Configure firewall rules to control traffic flow.
5. Define Routes and Route Tables
Why are we defining routes? By default, Azure allows direct routing between VNets, but in a Hub-and-Spoke model, we need to enforce security by directing traffic through the Hub firewall. This ensures that all outbound and inter-Spoke traffic is inspected and controlled.
Steps to Create Route Tables:
Create a route table in
Spoke1-VNetandSpoke2-VNet.Define routes:
Default Route: Direct all internet-bound traffic (
0.0.0.0/0) to the Azure Firewall's private IP.Inter-Spoke Traffic: Ensure that communication between Spokes is routed through the firewall.
Associate these route tables with the respective workload subnets.
Impact on Private IPs of Spoke VMs:
Once the route is applied, all outbound traffic from the Spoke VMs is routed through the firewall.
The public IPs of the Spoke VMs become irrelevant for external communication since all traffic is NATed through the firewall’s public IP.
The firewall ensures that only allowed outbound traffic can access the internet, adding a layer of security.
6. Configuring Firewall Rules
NAT Rules:
- Define rules to allow inbound traffic from specific sources.
Application Rules:
- Allow/Deny application-specific traffic based on policies.
Network Rules:
- Manage inter-VNet traffic flow.
7. Validation
Test connectivity between VMs across Spokes via the Hub.
Verify that the firewall enforces the defined security rules.
Ensure internet-bound traffic from the Spokes passes through the firewall.
8. Summary
This setup establishes a secure and scalable Hub-and-Spoke architecture, ensuring controlled communication between workloads while enforcing centralized security policies using Azure Firewall.
Subscribe to my newsletter
Read articles from bhuvanchand maddi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
