🕵️♂️ How I Got Access to a UK Government Organization’s SMTP Server? 📧🚨
 B4LOGI
B4LOGI
While researching Google Dorking over my favorite cup of coffee ☕, I stumbled upon something unexpected—an exposed mail server belonging to a UK government organization. Excited by the discovery, I decided to investigate further. Using Telnet, I attempted to connect, and to my surprise, I gained access to their mail server!
Curious about the extent of the exposure, I followed a structured approach to assess the risk while ensuring ethical boundaries. In this blog, I’ll walk you through my methodology, how I responsibly disclosed the issue through their Vulnerability Disclosure Program (VDP) on HackerOne, and the lessons we can learn from this security lapse.
Before that, let me introduce myself—I’m Ganesh Balaji V., an ethical hacker and pentester who thrives on uncovering vulnerabilities and making the digital world a safer (and more interesting) place. 🔍💻😏
How I got connected?
With my usual, yet favorite coffee in hand, I fired up my Kali terminal—the classic black screen that every hacker loves. Curious about the exposed mail server, I decided to interact with it directly using Telnet. I ran the following command:
telnet domain 25
To my surprise, the connection was successful—I was now interacting with a UK government organization’s mail server! What followed was a mix of excitement, curiosity, and responsibility.
I wanted to assess how vulnerable the server was without crossing ethical boundaries. To do this, I tested its email handling capabilities using standard SMTP commands. Below is the sequence I used:
HELO domain
MAIL FROM: <mail@mail.com>
RCPT TO: <mail@mail.com>
DATA
From: mail@mail.com
To: mail@mail.com
Subject: Test Mail
<Needed content>
.
If every command in the above snippet executes successfully, congratulations—you’ve discovered an open relay vulnerability in the SMTP mail server!
An open relay allows anyone to send emails on behalf of legitimate domains without proper authentication, making it a prime target for spammers and attackers. This vulnerability can be exploited for phishing, email spoofing, or even large-scale spam campaigns—posing a significant risk to the organization.
To validate my findings, I performed a Proof of Concept (PoC), demonstrating how an attacker could misuse this vulnerability. Below is the PoC I conducted:
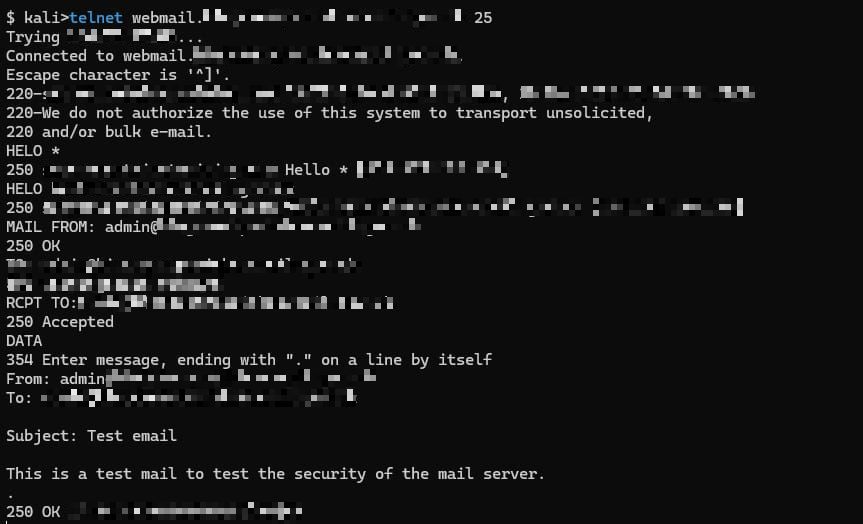
I successfully reported the issue to the security team through their Vulnerability Disclosure Program (VDP) on HackerOne. Given the severity of the vulnerability, I expected a responsible fix or at least an acknowledgment of its potential risks.
But to my surprise, they marked it as “informational”—stating that future awareness campaigns would be conducted instead of addressing the issue directly.
Seriously? An open relay vulnerability that allows unauthorized users to send emails impersonating legitimate personnel—brushed off as just informational?
Frustrated with their response, I sighed, leaned back, and reached for another cup of coffee—because clearly, caffeine was the only fix happening here.
Despite their dismissal, the reality remains: this vulnerability, if left unchecked, could lead to email spoofing, phishing campaigns, and even large-scale cyber threats. Ignoring it doesn't make the risk disappear.
📢 Disclaimer: The knowledge shared here is strictly for educational purposes. The usage of these commands to perform malicious actions is a serious offense and punishable by law. 🚨
Conclusion
Even though the report was marked as informational, I still found it to be a valuable learning experience. This was my first-ever HackerOne report, and despite the unexpected response, it felt like an important milestone in my journey. 🥳🥳
Security research is all about persistence, learning from every experience, and continuously improving. While this report didn’t get the recognition I had hoped for, it was a stepping stone toward bigger challenges and more impactful discoveries.
This was just the beginning of my HackerOne journey, and I can't wait for what’s next! 🚀
Let’s connect on LinkedIn — because networking isn’t just for packets! 😉💻
Subscribe to my newsletter
Read articles from B4LOGI directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
