Cyberstorm 2025 Writeup: Buzzard’s Poneglyph (Alternate Approach) [by Windows 9/11]
 Ishayu
Ishayu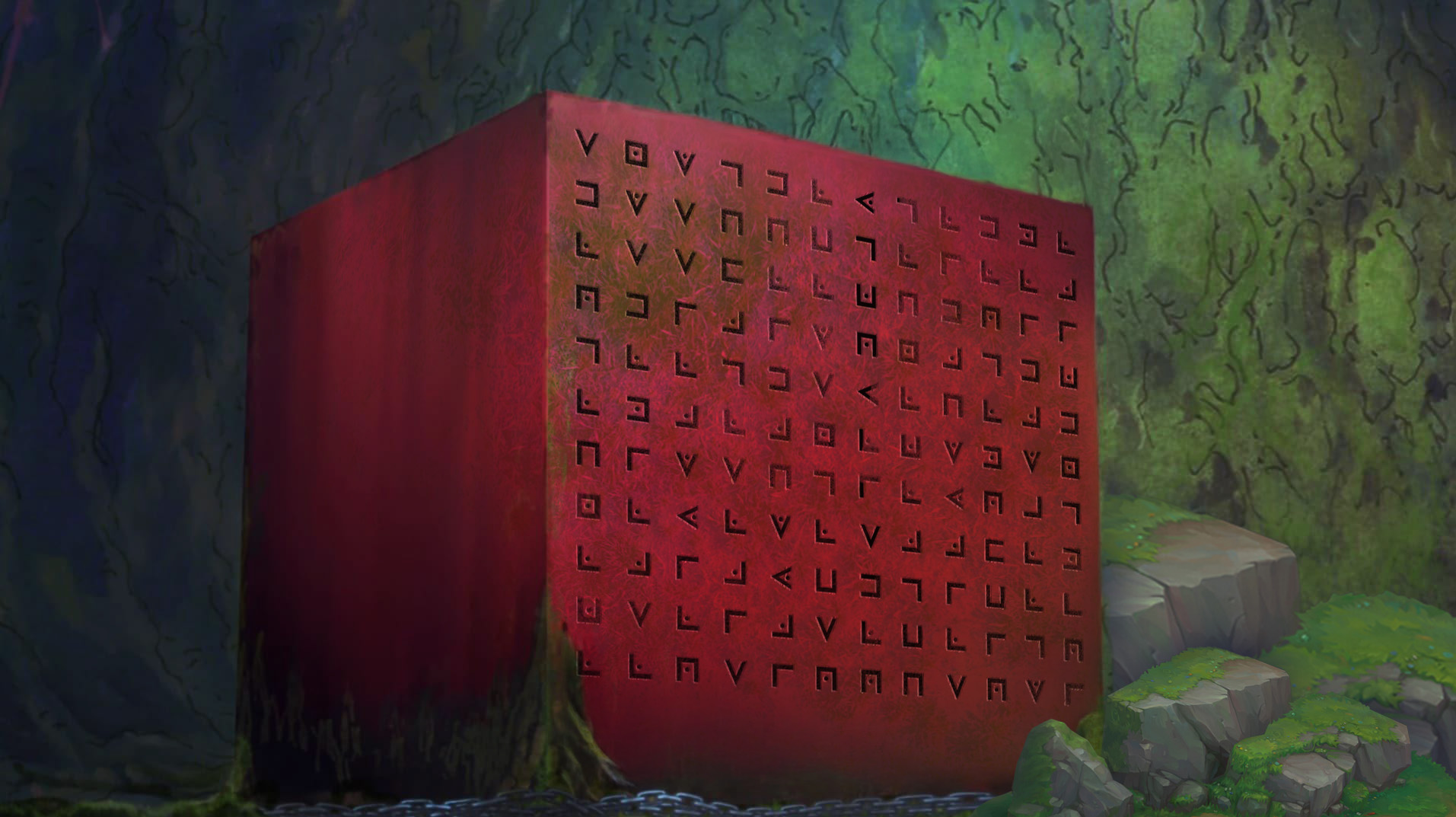
Category: Cryptography
Team Name : Windows 9/11
Points: 1000
Difficulty: easy-medium ( depending on how u approached it)
Author: Ishayu
Challenge Description
Name of Challenge: Buzzard’s Poneglyph
Robin uncovers an ancient Poneglyph during her exploration of a forgotten island, rumored to hold the key to a legendary pirate's treasure. The stone is encrypted with a long-lost cryptogram only a few can decode. Can you help Robin decipher the message and reveal the treasure’s location before it’s lost forever?
Provided Data & Initial Analysis
In this challenge the author has used one-piece reference of poneglyph and encoded some cipher on it, initial analysis is to find the type of encoding used and way to decode.
In One Piece, Poneglyphs are ancient, mysterious stone tablets inscribed with a language that very few people can read. They are crucial to uncovering the world's hidden history and play a major role in the story.
Data Format / Encoding
We find the data on poneglyph is in form of pigpen cipher
Initial Hypotheses
Based on the cipher text engraved it was a pigpen cipher , so we normally tried to decrypt it using standard
Dcode : https://www.dcode.fr/pigpen-cipher . We also found a aws link from solve of Treasure Trove Pt2 which was the Last challenge of Reverse Engineering Category which is maybe the hint for our poneglyph challenge
Woah, is this a road poneglyph here
https://redfox-ctf.s3.ap-south-1.amazonaws.com/new-ctf/third.jfif
Step-by-Step Solution
This challenge was solved by us in a different way than what was intended which you might think is a very insane thing to do.
Step 1: [Inputting the cipher in Dcode]
Like a sane man I wrote the cipher row wise and inputted it, we got few results here

The first result was more intriguing than the other lets see why in the next step
Step 2: [Rail-Fence Cipher]
In Dcode there are 9 methods by which a pigpen cipher can be solved
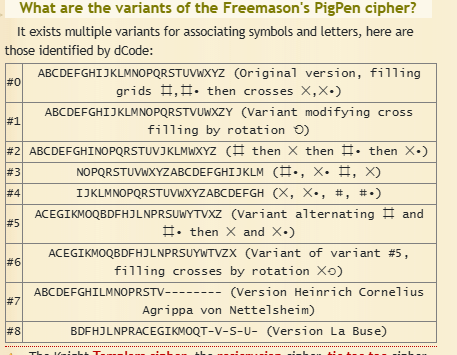
The First 8 methods gave useless results but the #8 one gave something unique while performing frequency analysis we find its a rail-fence cipher
There were few words which came in common while decoding it with rail-fence cipher
| 12↕ ↘↗ (+1) | UNCOVERTHEODNAECEIPENTERHAPSUAREPRDLOGENOEHIGERHASBEENTOFGNIHCRAESHEONEPIECEOETAERGEHTSNTTREASUREOSTRAETENALPHPERHAPSUARROTDENITSEDE | |
| 12↕ ↗↘ (+1) | EHTREVOCNUTNEPIECEANDOERAUSPAHREIHEONEGOLDRPNEEBSAHREGSEARCHINGFOTECEIPENOEHNSTHEGREATEOOERUSAERTTHPLANETEARTSRAUSPAHREPEDESTINEDTOR | |
| 12↕ ↘↗ | TUNCOVERTHEODNAECEIPENIERHAPSUAREPRDLOGENOEHSGERHASBEENTOFGNIHCRAENHEONEPIECEOETAERGEHTSHTTREASUREOSTRAETENALPEPERHAPSUARROTDENITSED | |
| 12↕ ↗↘ (+4) | REVOCNUTNEPIECETHEODNAUSPAHREIHEONEGOAREPRDLBSAHREGSEARCHINEENTOFGIPENOEHNSTHEGREECEOETAUSAERTTHPLANETEREOSTRASPAHREPEDESTINEUARROTD | |
| 12↕ ↗↘ | OEHTREVOCNUTNEPIECEANDPERAUSPAHREIHEONEGOLDRTNEEBSAHREGSEARCHINGFOOECEIPENOEHNSTHEGREATESOERUSAERTTHPLANETEARTRRAUSPAHREPEDESTINEDTO | |
| 12↕ ↘↗ (+3) | COVERTHEODNAECEIPNUTNEHAPSUAREPRDLOGENOREIHERHASBEENTOFGNIHCREGSEAONEPIECEOETAERGEHEHNSTREASUREOSTRAETENATTHPLRHAPSUARROTDENITSEPEDE | |
| 12↕ ↗↘ (+3) | TREVOCNUTNEPIECEAHEODNAUSPAHREIHEONEGOLREPRDEBSAHREGSEARCHINGENTOFEIPENOEHNSTHEGREACEOETRUSAERTTHPLANETEAEOSTRUSPAHREPEDESTINEDARROT | |
| 12↕ ↗↘ (+2) | HTREVOCNUTNEPIECEANEODRAUSPAHREIHEONEGOLDEPREEBSAHREGSEARCHINGFNTOCEIPENOEHNSTHEGREATEOEERUSAERTTHPLANETEAROSTAUSPAHREPEDESTINEDTRRO | |
| 12↕ ↗↘ (+9) | NUTNECOVERTHEODNAECEIPREIHEHAPSUAREPRDLOGENOEGSEARHASBEENTOFGNIHCREHNSTONEPIECEOETAERGEHTTHPLREASUREOSTRAETENAEPEDERHAPSUARROTDENITS | |
| 12↕ ↘↗ (+2) | NCOVERTHEODNAECEIPEUTNRHAPSUAREPRDLOGENOEEIHERHASBEENTOFGNIHCRAGSEEONEPIECEOETAERGEHTHNSTREASUREOSTRAETENALTHPERHAPSUARROTDENITSEPED | |
| 12↕ ↘↗ (+9) | HEODNTREVOCNUTNEPIECEAREPRDAUSPAHREIHEONEGOLENTOFEBSAHREGSEARCHINGCEOETEIPENOEHNSTHEGREAEOSTRRUSAERTTHPLANETEAARROTUSPAHREPEDESTINED | |
| (⁻¹)13↕ ↘↗ (+2) | EHSENEANCGILGROTREANSPAEEEIETIECRAADESNTOEESTREONDLSNITEATTHPERHAPSUAREPEATENEDROUTCRVARUHEONSPHEGEENTPEHHOPEUIRCTHEOREHONDFORGRABES | |
| 12↕ ↘↗ (+8) | THEODNAREVOCNUTNEPIECEAREPRDLUSPAHREIHEONEGOEENTOFGBSAHREGSEARCHINECEOETAIPENOEHNSTHEGREREOSTRAUSAERTTHPLANETEUARROTDSPAHREPEDESTINE |
Decryption Script / Tool Usage
Since dcode had limited area for bruteforce we searched up the web for python script which could mass bruteforce the rails and offset as much as we want and we expected to get the flag directly
We found this website
https://cryptii.com/pipes/rail-fence-cipher
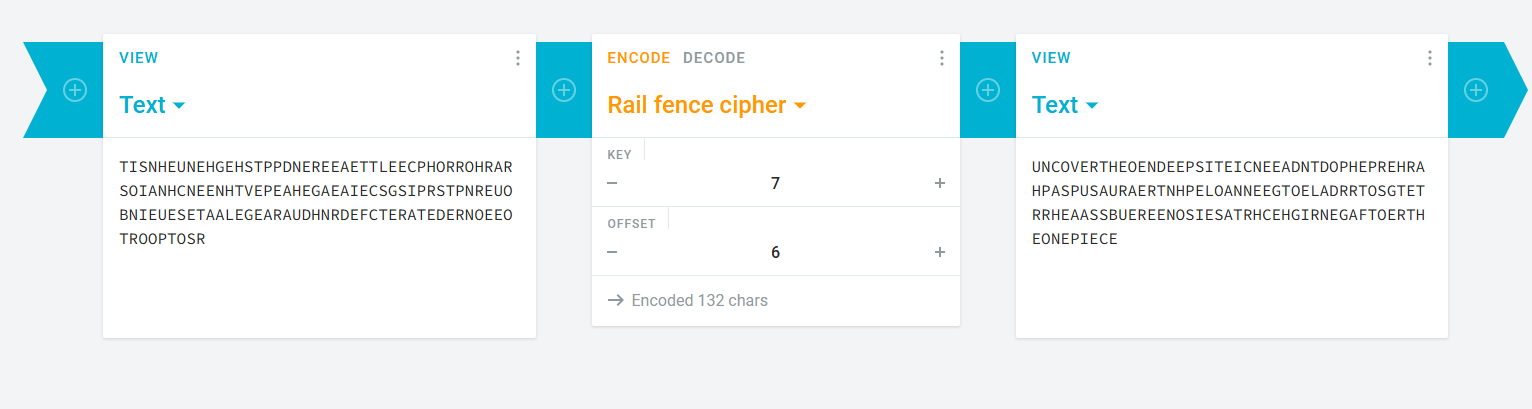
Based on this we automated rails/key and offset using python script
script we found on this github : https://github.com/burturt/railfence-bruteforce/blob/main/railfence.py
#
# rail fence cipher implementation with optional offset feature
#
# for educational use only! (rail fence cipher is a very weak cipher.)
#
# https://en.wikipedia.org/wiki/Rail_fence_cipher
#
def printFence(fence):
for rail in range(len(fence)):
print(''.join(fence[rail]))
def encryptFence(plain, rails, offset=0, debug=False):
cipher = ''
# offset
plain = '#' * offset + plain
length = len(plain)
fence = [['#'] * length for _ in range(rails)]
# build fence
rail = 0
for x in range(length):
fence[rail][x] = plain[x]
if rail >= rails - 1:
dr = -1
elif rail <= 0:
dr = 1
rail += dr
# print pretty fence
if debug:
printFence(fence)
# read fence
for rail in range(rails):
for x in range(length):
if fence[rail][x] != '#':
cipher += fence[rail][x]
return cipher
def decryptFence(cipher, rails, offset=0, debug=False):
plain = ''
# offset
if offset:
t = encryptFence('o' * offset + 'x' * len(cipher), rails)
for i in range(len(t)):
if (t[i] == 'o'):
cipher = cipher[:i] + '#' + cipher[i:]
length = len(cipher)
fence = [['#'] * length for _ in range(rails)]
# build fence
i = 0
for rail in range(rails):
p = (rail != (rails - 1))
x = rail
while (x < length and i < length):
fence[rail][x] = cipher[i]
if p:
x += 2 * (rails - rail - 1)
else:
x += 2 * rail
if (rail != 0) and (rail != (rails - 1)):
p = not p
i += 1
# print pretty fence
if debug:
printFence(fence)
# read fence
for i in range(length):
for rail in range(rails):
if fence[rail][i] != '#':
plain += fence[rail][i]
return plain
if __name__ == "__main__":
import sys
# CHANGE THIS
# THE LAST NUMBER DOES NOT GET USED
rails = range(2, 133)
offsets = range(0, 133)
# DONT CHANGE THIS
if len(sys.argv) != 2:
print("Usage: python3 " + sys.argv[0] + " [ciphertext]")
print("You may need to use quotes around the ciphertext if it contains spaces")
else:
ciphertext = sys.argv[1]
print("-----------------------------")
print("Brute forcing all rails and offsets:")
print(list(rails))
print(list(offsets))
for i in rails:
for j in offsets:
print(decryptFence(ciphertext, i, offset=j, debug=False))
The Output was not as quite expected there was no proper flag in the output
But we noticed there were few words which possibly formed the flag
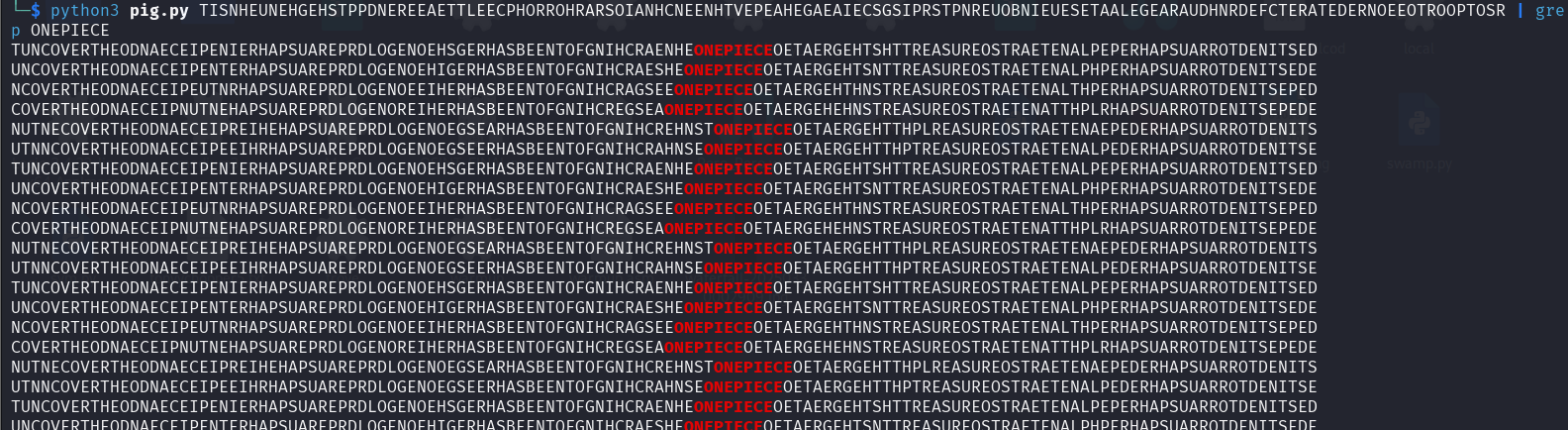
Recovering the Plaintext / Flag
THE MOST INSANE PART OF OUR SOLVE
Recovering the flag was an insane task , we had the flag format
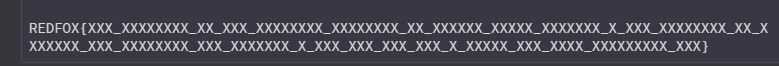
The flag format had

So we made a list of words from our brute force python approach and also by playing around with offsets and rails randomly but smartly from that this website : https://cryptii.com/pipes/rail-fence-cipher , we found few words which do make up the flag, we wrote them down and started assembling our flag guessing what it could be
Here what it looked like :0
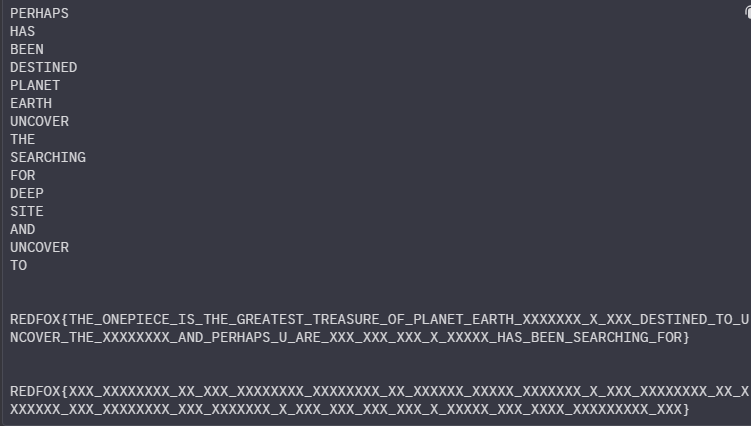
We did almost guessed all of em few were remaining until our teammate who had watched one piece came and told us a few things , which made our minds click and we got the final flag
REDFOX{THE_ONEPIECE_IS_THE_GREATEST_TREASURE_ON_PLANET_EARTH_PERHAPS_U_ARE_DESTINED_TO_UNCOVER_THE_ONEPIECE_AND_PERHAPS_U_ARE_THE_ONE_GOL_D_ROGER_HAS_BEEN_SEARCHING_FOR}
INSANITY INDEED
Tools & Resources Used
Python3: For scripting the decryption logic.
Online Calculators : dCode.fr (for various ciphers).
Frequency Analysis Tools: Online analyzers or custom scripts.
Text Editor: For viewing data and writing scripts.
Lessons Learned and Takeaways
Cipher Identification: Analyzing which cipher is being used is the key part of challenge
Basic Analysis: Even simple frequency analysis (like checking single-letter words) can quickly confirm or deny hypotheses for classical ciphers.
Takeaway: sometimes things are arent they way you think they are you have to think a bit outside of box ( not row but column )
Tooling: python script and dcode helped a lot
Deadends
When I solved the Treasure Trove Pt2 : The Last challenge of Reverse Engineering Category which I had solved pretty early
There was an aws link to it with third.jfif
here is the link for reference : https://redfox-ctf.s3.ap-south-1.amazonaws.com/new-ctf/third.jfif
third.jfif was not in readable or viewable format so after performing some forensic analysis and decrypting it we found third.png from it which had these values
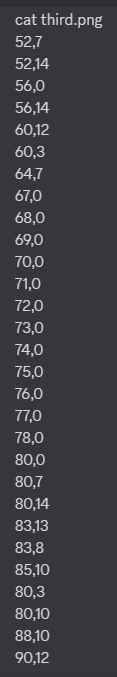
But this was a Deadend for us , if anybody reached any further with this let us know
Easier Approach
The simple approach which I cam to know later was to just write a pigpen cipher column wise instead of row-wise and that actually gave out the correct flag ,
but most importantly we were happy with our approach cause it pushed us to our limits and who doesnt like that :)
Credits : Nishith Savla, Ishayu
Discord : @drago0287
Subscribe to my newsletter
Read articles from Ishayu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
