Networking Skills Every DevOps Engineer Should Master
 KubeCaptain
KubeCaptain
In today's fast-paced digital world, the role of a DevOps engineer is more critical than ever. With the increasing complexity of cloud environments and the need for seamless integration between development and operations, understanding networking is no longer optional—it's essential. Whether you're new to DevOps or looking to deepen your expertise, this guide will provide valuable insights to enhance your career.
By the end of this article, you will understand:
How OSI and TCP/IP Protocol works.
What is DNS and how it works.
IP subnetting and masking.
How to troubleshoot network issues.
Understanding the OSI Model
Open Systems Interconnection (OSI) model is set of standards that defines how computers communicate with each others over a network. Data flow is divided into 7 layers that are interconnected.
OSI Model works from bottom to top, beginning from layer 1 to layer 7. The top layer (application layer) is what a user get when searches for something. While reading this article you’re interacting with on layer 7.
Let’s go through each layer in the following.
Layer 1: Physical Layer
Lowest layer which is responsible for converting bit of information into electrical signals. The physical Layer defines the types of encoding (that is how the 0’s and 1’s are encoded in a signal). It is responsible for the communication of the unstructured raw data streams over a physical medium.
Layer 2: Data Link Layer
Data is organized into frames. Each frame includes error checking information to ensure data integrity. It also corrects error that have occurred at layer 1. Data Link Layers enables data transfer between two directly connected nodes or systems on the same network.
Layer 3: Network Layer
The Network Layer is responsible for data routing, forwarding, and addressing. It determines the best physical path for data to reach its destination based on network conditions, the priority of service, and other factors. This layer manages logical addressing through IP addresses and handles packet forwarding. For example, you’re trying to send a particularly large message, Network layer will convert into fragments of data at the node, send them separately and reassemble at the destination.
Layer 4: Transport Layer
Transport layer protocols provide host-to-host communication. It’s responsible for ensuring that data is transferred reliably and accurately between the connected devices. It uses TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) to manage network traffic between systems.
Layer 5: Session Layer
This layer responsible for creating and maintains the session (connections) that two systems needs to communicate with each other. A session refers to a connection or conversation that lasts for a certain period of time, such as when you are streaming a video or participating in a video call. Session layer sets up, starts, maintains and ends session. It can insert checkpoints during data transfer to make sure if there any failure occurs, communication can start from the end checkpoint instead of starting over.
Layer 6: Presentation Layer
Also called Syntax Layer responsible for ensuring that data is in correct format for the application to process. It acts as a translator between the data formats used by the application and the format required for transmission over the network. Processes such as data encoding, compression, and encryption/decryption happen on this layer.
Layer 7: Application Layer
The Application Layer is the topmost layer in the OSI model and is responsible for providing network services directly to the end user or application. This layer interacts with software applications that use the network, like web browsers or email clients. This includes technologies such as HTTP, DNS, FTP, SSH, and much more.
Exploring TCP/IP
What is TCP/IP, and How is it Different From OSI?
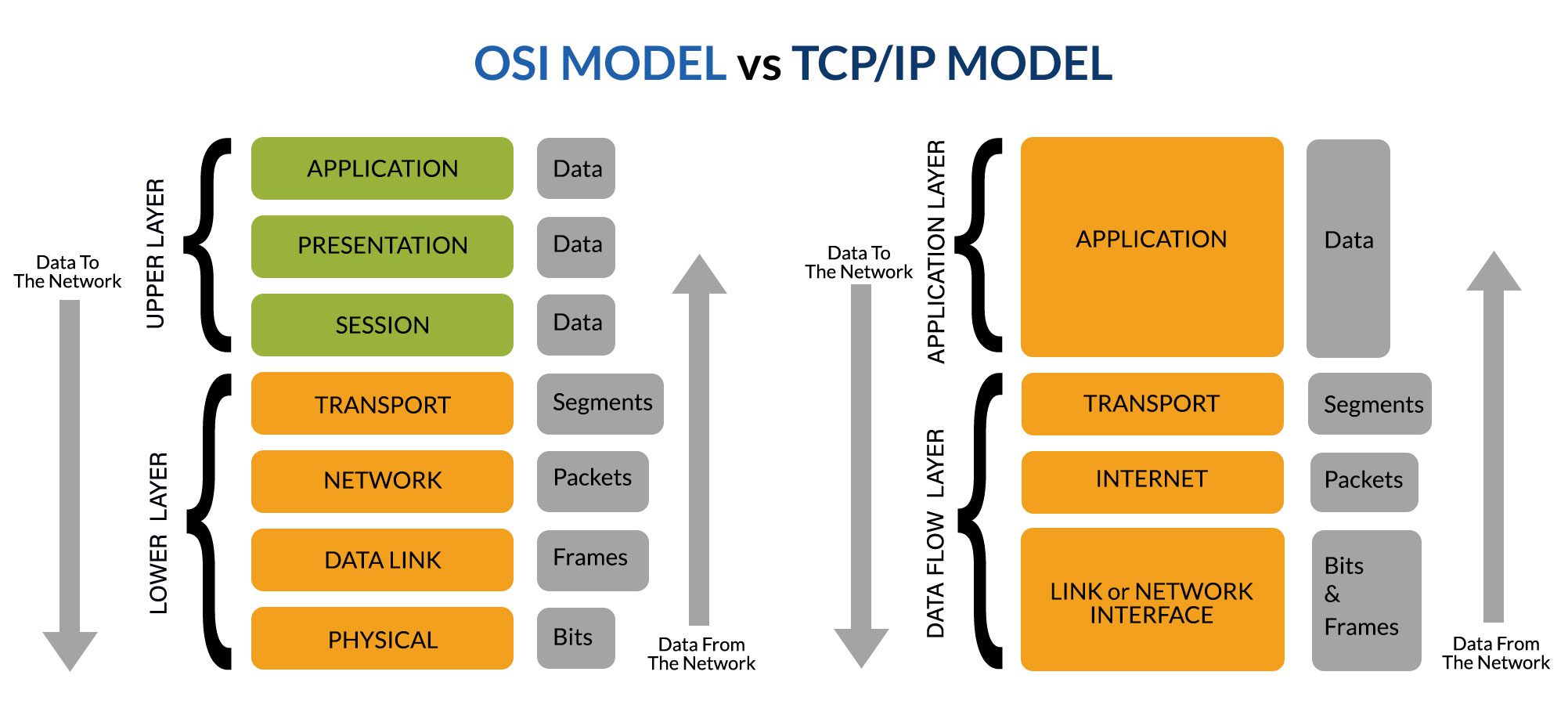
OSI and TCP/IP are widely used communication networking protocols. The main difference is that OSI is conceptual model for understanding of how network works. It defines how applications can communicate over a network. TCP/IP, on the other hand, is a practical execution that's widely used to establish links and network interaction. TCP describe the standards on which internet was created.
TCP combines the three top layers(Application, Presentation, Session) of OSI into single Application Layer, and two bottom most layers of OSI becomes Network Interface layer of TCP/IP. So it consists of 4 layers. The one of most important layer in TCP/IP is Application Layer. It is the topmost layer in the TCP/IP model, where all application-related communication happens. It’s responsible for managing and enabling the interaction between different applications over a network using protocols like HTTP, FTP, and SMTP. You interact with this layer every time you use a web browser, send an email, or transfer files.
The other layer of the TCP/IP model that requires particular special attention is the Transport layer because it introduces several important networking concepts.
TCP vs UDP
The Transport Layer of TCP/IP consists of two protocols:
TCP
UDP
Let’s see the difference between them.
TCP is a reliable, connection-oriented protocol that ensures data is delivered accurately and in the correct order. Before any data is sent, TCP establishes a connection between the sender and receiver, much like making a phone call. It also performs error-checking, meaning if any data is lost or corrupted during transmission, it will be re-transmitted. This makes TCP slower but more reliable. TCP is commonly used in applications where data integrity is crucial, such as web browsing (HTTP/HTTPS), SSH and file transfers (FTP).
UDP is a connectionless, unreliable protocol that focuses on speed rather than reliability. UDP sends data without establishing a connection, like sending a message without waiting for a response, and does not perform error-checking or ensure that the data arrives in order. As a result, it’s much faster than TCP but less reliable. This makes UDP ideal for applications where speed is more important than perfect accuracy, such as live streaming, online gaming, or video calls, where slight data loss is acceptable and doesn’t significantly affect the user experience.
Understanding Network Ports
In computer networking, ports serve as communication endpoints for each application or service on a device. When an application on one computer sends data to another application on a different computer, it uses an IP address to identify the device and a port number to specify the particular application. Think of ports as door numbers that direct data to the correct application or service.
Here are some commonly used ports:
| PORT NUMBER | SERVICE |
| 22 | SSH |
| 21 | FTP (File Transfer Protocol) |
| 25 | SMTP (Simple Mail Transfer Protocol) |
| 80 | HTTP (Hyper Text Transfer Protocol ) |
| 443 | HTTPS |
| 53 | DNS |
| 3306 | MYSQL Database |
Mastering IP Subnetting and CIDR(Classless Inter-Domain Routing)
To connect to a network, three key components are required:
IP Address: Every device needs an IP address to interact with the internet. Even while reading this blog, your phone or computer has an IP address. An IP address is a
32-bitlogical address divided into four8-bitsections called octets . It is used to identify a device on a network. We call it logical because it is not permanently bound to a device, It can change based on the network and one device can have multiple IP addresses. IP addresses are represented by four numbers ranging from 0 to 255, such as87.18.121.120. They are displayed in dotted-decimal notation for human readability but actually represent binary bits.Subnet Mask: A subnet mask is a
32-bitnumber used to determine the network and host portions of an IP address. This is essential for routing and network organization. It is represented in decimal-dotted notation and CIDR (Classless Inter-Domain Routing) format. Each octet in the subnet mask can only take on values that represent a continuous series of 1s followed by 0s. The network section is represented by 1s, and the host section by 0s. For example, in the subnet mask255.255.0.0, the first two octets (255, 255) represent the network, and the last two (0, 0) represent the host.Default Gateway: This is the device that routes traffic from a local network to other networks or the internet.
Binary Representation of 255
Each bit in an 8-bit octet has a value based on powers of 2, starting from the rightmost bit:
| Bit Position | Binary Value | Power of 2 | Decimal Value |
| 1st Bit | 1 | 2^7 | 128 |
| 2nd Bit | 1 | 2^6 | 64 |
| 3rd Bit | 1 | 2^5 | 32 |
| 4th Bit | 1 | 2^4 | 16 |
| 5th Bit | 1 | 2^3 | 8 |
| 6th Bit | 1 | 2^2 | 4 |
| 7th Bit | 1 | 2^1 | 2 |
| 8th Bit | 1 | 2^0 | 1 |
If all bits are set to 1, the sum of the decimal values for each position is:
128 + 64 + 32 + 16 + 8 + 4 + 2 + 1 = 255
This is why each octet in an IP address can have a value between 0 and 255.
Calculating the Number of Available IPs in a Subnet
To calculate the number of available IPs in a subnet:
Find the number of 0’s in the subnet mask.
Raise 2 to the power of the number of 0’s.
Total IP Addresses = 2^(number of ‘0’s in subnet mask) - 2
For example, with a subnet mask of 255.255.0.0. In binary, it looks like 11111111.11111111.00000000.00000000. There are 16 0’s, so:
2^16 - 2 = 65,534 available IP addresses.
IP Address Classes
To understand IP address classes, you should first know about unicast and multicast IPs.
Unicast IPs send data from one sender to one receiver, following a one-to-one communication model. Example: Sending an email to one person.
Multicast IPs send data from one sender to multiple specific receivers in a group, following a one-to-many communication model. Example: Streaming a live event to selected viewers.
IP addresses are distributed into different classes:
| Class | IP Range | |
| Class A | 0.0.0.0 – 127.255.255.255 | Unicast |
| Class B | 128.0.0.0 – 191.255.255.255 | Unicast |
| Class C | 192.0.0.0 – 223.255.255.255 | Unicast |
| Class D | 224.0.0.0 – 239.255.255.255 | Multicast |
| Class E | 240.0.0.0 – 255.255.255.255 | Research and Experimental Purposes only |
Subnet Mask
A subnet mask is 32-bit number which is used to determine the network part and host part. This is essentials for routing and network organization.
It is represented by decimal-dotted representation and CIDR (Explained later in detail). Each octet in the subnet mask can only take on values that represents a continuous series of 1s followed by 0s. Network section represented by 1 and host section by 0.
For example 11111111.1111111.11111111.00000000 First 3 octet represents network section and last one which is starting by zero represents host section. In decimal notation the network octet can be 9 possible values which are 0, 128, 192, 224, 248, 252, 254 and 255.
Now, you might wonder how these numbers are formed. Here is an explanation:
| Binary Representation | Binary to Decimal | Explanation |
| 00000000 | (0 × 2^7) + (0 × 2^6) + ... + (0 × 2^0) = 0 | No network bits (all host bits) |
| 10000000 | (1 × 2^7) + (0 × 2^6) + ... + (0 × 2^0) = 128 | 1 network bit, 7 host bits |
| 11000000 | (1 × 2^7) + (1 × 2^6) + ... + (0 × 2^0) = 192 | 2 network bits, 6 host bits |
| 11100000 | (1 × 2^7) + (1 × 2^6) + (1 × 2^5) + ... + (0 × 2^0) = 224 | 3 network bits, 5 host bits |
| 110000 | (1 × 2^7) + (1 × 2^6) + (1 × 2^5) + (1 × 2^4) + ... + (0 × 2^0) = 240 | 4 network bits, 4 host bits |
| 110000 | 1 × 2^7) + (1 × 2^6) + (1 × 2^5) + (1 × 2^4) + (1 × 2^3) + ... + (0 × 2^0) = 248 | 5 network bits, 3 host bits |
| 11111100 | (1 × 2^7) + (1 × 2^6) + (1 × 2^5) + (1 × 2^4) + (1 × 2^3) + (1 × 2^2) + ... + (0 × 2^0) = 252 | 6 network bits, 2 host bits |
| 11111110 | (1 × 2^7) + (1 × 2^6) + (1 × 2^5) + (1 × 2^4) + (1 × 2^3) + (1 × 2^2) + (1 × 2^1) + ... + (0 × 2^0) = 254 | 7 network bits, 1 host bit |
| 11111111 | (1 × 2^7) + (1 × 2^6) + (1 × 2^5) + (1 × 2^4) + (1 × 2^3) + (1 × 2^2) + (1 × 2^1) + (1 × 2^0) = 255 | 8 network bits, 0 host bit |
Here’s an example to understand this. We have a subnet mask of 255.255.0.0, and we can differentiate that the first two decimal numbers (255, 255) represents network and later (0.0) represents host. Can we also determine the number of possible hosts? Let's calculate it:
Total IP Addresses = 2^(number of 0's in subnet mask) -2
So we have 255.255.0.0 subnet mask. In Binary It looks like 11111111.11111111.00000000.00000000 . We have 16 ‘0’s so
Possible IPs = 2^16 = 65,536-2 = 65,534 are possible IPs in our network.
Every Subnet has 2 reserved IPs which are Network IP (First IP in Subnet) and Broadcast IP (Last IP in Subnet ).
Let’s calculate for subnet mask of 255.255.240.0 as well to get more understanding. In binary they’re 11111111 11111111 11110000 00000000. As the number of 0s are 12 so,
Total IP Addresses = 2^12 -2 = 4094
Routing
Routing is the process of determining the path that data packets take from a source to a destination across interconnected networks. It is essential for ensuring that data reaches its intended destination efficiently and accurately.
Think of routing as choosing the best path to travel from one place to another. Different routes are available for different destinations, and routers use routing tables to determine the most efficient path. It's similar to choosing between local roads, highways, or interstates depending on your travel destination.
Example of a Routing Table
This screenshot demonstrates a typical Route Table in AWS:
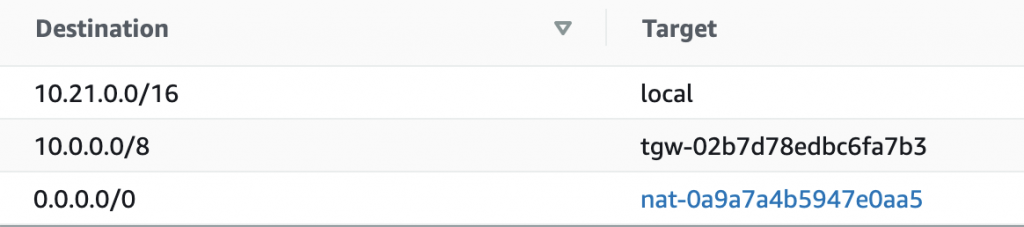
If the packet destination is in the range of
10.21.0.0/16, then it will remain in local network.If the packet destination is in the range of
10.0.0.0/8, then the request will be sent to transit gatewaytgw-02b7d78edc6fa7b3interface.If the packet destination is not in theses ranges, the widest one is evaluated which is
0.0.0.0/0which means it is internet traffic. And the packet will be redirected to NAT(Network Address Translation ) Gatewaynat-0a9a7a4bGeneral5947e0aa5.
What is Router?
Device which sends data packets between networks. It works at OSI layer 3 (network layer)
Key Functions of a Router Includes
Packet Forwarding: Routers analyze data packets received from one network and determine the best path for forwarding them to their destination network based on routing tables and network protocols.
Network Address Translation (NAT): Routers can perform NAT, which allows multiple devices within a local network to share a single public IP address when communicating with devices on the internet.
Firewall Services: Many routers include built-in firewall capabilities to monitor and control incoming and outgoing traffic, enhancing network security.
Wireless Access Point (WAP): Some routers incorporate wireless access points, enabling wireless devices to connect to the network.
Dynamic Host Configuration Protocol (DHCP): Routers can act as DHCP servers, assigning IP addresses dynamically Generalto devices within the local network.
Domain Name System (DNS)
DNS Overview
As discussed computers communicate using IP addresses. While human on the other hands, identify things with name. Humans and computers interact a lot but humans are not good good at memorizing the IP addresses while same computers with names. To resolve this Domain Name System (DNS) comes. This protocol is used to convert the Human Readable Domain Names into computer-friendly IP addresses.
Here’s a simple, step-by-step explanation of how DNS (Domain Name System) works:
User Request:
You type a website address say (www.example.com) in your browserLocal Query:
Your computer first checks its own cache to see if it already knows the IP address for that domain. If not, it sends a DNS query to a DNS resolver(usually provided by your Internet Service Provider).Recursive Lookup:
The DNS resolver checks its cache. If it doesn’t have the answer, it starts a process called recursive lookup by asking other DNS Servers.Root Servers:
The resolver contacts one of the root DNS servers. These servers don't know the exact IP address but can direct the resolver to the correct top level domain (TLD) server (like for *.*com, *.*net, .edu etc).TLD Servers:
The resolver then queries the appropriate TLD server (for example, the .com server) to find out which authoritative DNS server holds the records forexample.com.Authoritative Name Server:
Finally, the resolver contacts the authoritative DNS server forexample.com. This server has the actual DNS records (like an A record) that map the domain name to its corresponding IP address.Return the IP Address:
The authoritative server returns the IP address (for example, 93.184.216.34) back to the DNS resolver, which then caches this information for future use.Website Connection:
The DNS resolver sends the IP address back to your computer. Now your browser uses this IP address to connect to the web server and load the website.
This process happens very quickly, often in just a few milliseconds, making it seem like the website loads instantly. Essentially, DNS acts like a phone book for the Internet, translating human-friendly domain names into machine-friendly IP addresses.
DNS Record Types
DNS Records, also called Zone files, provide information about a domain. This includes the IP address that is associated with this domain and how to handle queries for it. Each DNS record has a time-to-live setting (TTL) which indicates how often a DNS server will refresh it.
Here are the most commonly used types of DNS records and their meaning.
| Type | Name | Description |
| A | Host Address | The most basic and the most commonly used DNS record. It translates human-friendly domain names into computer-friendly IP addresses. |
| AAAA | IPv6 Host Address | Same as A but for IPv6 (a host address that can have more than one IP address). |
| CNAME | Canonical Name for an Alias | Maps a name to another name. It should only be used when there are no other records on that name. |
| MX | Mail Exchange | Specifies the e-mail server(s) responsible for a domain name. |
| NS | Name Server | Identifies the DNS servers responsible for a zone. One NS record for each DNS server in a zone. |
| TXT | Descriptive Text | Holds general information about a domain name such as who is hosting it, contact person, phone numbers, etc. Widely used for domain ownership verification. |
Understanding HTTP
HTTP Methods
HTTP (Hypertext Transfer Protocol) is the set of rules used to transfer data over the web. It allows your browser (like Chrome or Firefox) to communicate with websites.
It’s like a language that your browser and the website use to talk to each other. When you search for a website like google.com, your browser sent a HTTP request to the server where the website is hosted. We have covered it in DNS resolve for a website. The Server sends back an HTTP response with the web page data.
There are 7 main HTTP request methods:
| Name | Description |
| GET | Requests the data of an object. The data entity is returned in a response body. |
| HEAD | Identical to GET, but without a response body. More for meta information or testing. |
| POST | Submits a change to an object. |
| PUT | Replaces an object. |
| PATCH | Updates an object. |
| OPTIONS | Describes the communication options for an object. |
| DELETE | Deletes an object. |
HTTP Response Codes
HTTP response indicates the status of request- success or failure both. There’re four categories of HTTP responses:
200s: Successful Response
300s: Redirects
400s: Client errors
500s: Server errors
Here are some of the most common response codes:
HTTP Code
What It’s Telling
What it Means
200
OK
Request succeeded.
302
Found, Temporary Redirect
The URI of the requested resource has been changed temporarily.
400
Bad Request
The server can’t understand the request being sent.
401
Unauthorized
The client must authenticate itself before sending the request.
403
Forbidden
The client does not have enough permission to access the content.
404
Not Found
The server can’t find the requested resource.
408
Request Timeout
The response was sent to an idle connection and the server wants to terminate it.
500
Internal Server Error
The server does not know how to handle a request.
502
Bad Gateway
The server you are trying to access is a gateway or a reverse proxy (it sits between the client and an actual server that serves the page). You get this error when the gateway gets an incorrect response from a source server.
503
Service Unavailable
The server can’t process the request. This usually happens when a server is down or overloaded.
504
Gateway timeout
Similar to 502, the gateway can’t get a response in time.
HTTP Headers
HTTP Headers are additional information sent between a client (like a browser) and a server during a HTTP request or response. They define the parameters of the request or response, and help both during the client and the server understand how to process the data being transmitted. HTTP headers allow the client to add additional information to a request for purposes such as authentication, caching, and specifying the type of client device sending the request.
Headers fall into 4 general contexts:
General Header: A header that works for both response and requests messages.
Request Header: A header that only applies to request messages from a client.
Response Header: A header that only applies to responses from a server.
Entity Header: A header that gives information about the entity itself or the resource requested.
Headers are case-insensitive in the structure name.
Network Troubleshooting Tools
Ping
Easiest tool to test internet network connection is ping. It helps determine the reachability of a host on an Internet Protocol (IP) network and measures the round-trip time for messages sent from the originating host to a destination computer. By sending multiple packets, ping can determine if any packets are lost during transmission. Packet loss can indicate network congestion or connectivity issues.
Here is how you can ping a host:
ping www.google.com
Traceroute
Traceroute is a diagnostic command that can show you possible routes across an IP network and calculate any transit delays in that route. Whereas the ping command only shows a final round trip time for packets to go from host to destination and back, traceroute calculates the total time spent establishing a connection by adding up the mean respective round trip times for each subsequent node along a given route.
Let’s see how traceroute works with an example:
ubuntu@kubecaptain :~$ traceroute google.com
traceroute to google.com (172.217.19.206), 30 hops max, 60 byte packets
1 _gateway (10.10.20.1) 1.346 ms 1.915 ms 2.628 ms
2 192.168.1.1 (192.168.1.1) 2.568 ms 2.505 ms 3.233 ms
3 * * *
4 10.0.6.5 (10.0.6.5) 4.487 ms 4.146 ms 5.488 ms
5 10.253.8.96 (10.253.8.96) 5.428 ms 10.253.8.36 (10.253.8.36) 5.366 ms 10.253.8.96 (10.253.8.96) 8.018 ms
6 10.253.4.16 (10.253.4.16) 24.368 ms 23.866 ms 23.270 ms
7 10.253.4.26 (10.253.4.26) 23.674 ms 10.253.4.8 (10.253.4.8) 23.014 ms 10.253.4.26 (10.253.4.26) 21.660 ms
8 74.125.118.170 (74.125.118.170) 42.277 ms 39.795 ms 39.690 ms
9 * * *
10 192.178.96.204 (192.178.96.204) 41.711 ms 172.253.66.40 (172.253.66.40) 42.206 ms 142.251.51.54 (142.251.51.54) 39.281 ms
11 108.170.238.19 (108.170.238.19) 41.989 ms 38.992 ms 108.170.237.73 (108.170.237.73) 38.806 ms
12 fjr04s13-in-f14.1e100.net (172.217.19.206) 39.350 ms 40.904 ms 39.941 ms
In the above example we have a detailed view of how our request is processed and the hops from where the request passed by.
SSH
SSH is Secure Shell is a cryptographic network protocol used for secure communication over an unsecured network. It provides a secure channel over an unsecured network by using a client-server architecture, allowing users to log into another computer over a network, execute commands, and transfer files securely. SSH is widely used for remote administration of systems and network devices. To connect a remote machine far away from you or from other country, SSH is used. By default, It works on port 22.
Let’s see how you can use SSH:
ubuntu@kubecaptain: ssh username@rmeote_host
Netstat
Netstat, short for Network Statistics, is a command line tool that provides information about the network connections, routing tables and network interface statistics. It is commonly used to monitor and troubleshoot network issues by displaying active connections and listening ports.
Here are a few common netstat commands:
netstat -a: Display all active connections and listening ports.
netstat -t: Shows only TCP connections.
ubuntu@kubecaptain: netstat -t
Active Internet connections (w/o servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 192.168.1.22:54878 ec2-3-219-222-214:https ESTABLISHED
tcp 0 0 192.168.1.22:37472 fjr04s12-in-f14.1:https TIME_WAIT
tcp 0 0 192.168.1.22:33222 23.171.198.88.in-:https ESTABLISHED
tcp 0 0 192.168.1.22:37486 fjr04s12-in-f14.1:https TIME_WAIT
tcp 0 1 192.168.1.22:58366 188.27.250.142.in-:5228 SYN_SENT
tcp 0 1 192.168.1.22:50996 rb-in-f188.1e100.n:5228 FIN_WAIT1
tcp 0 1 192.168.1.22:58358 188.27.250.142.in-:5228 SYN_SENT
tcp 0 0 192.168.1.22:39592 fjr04s12-in-f1.1e:https TIME_WAIT
tcp 0 0 192.168.1.22:40796 fjr04s11-in-f2.1e:https ESTABLISHED
tcp 0 0 192.168.1.22:39598 fjr04s12-in-f1.1e:https TIME_WAIT
tcp 0 0 192.168.1.22:46706 199.232.57.140:https ESTABLISHED
tcp 0 0 192.168.1.22:41198 151.101.141.51:https ESTABLISHED
tcp 0 1 192.168.1.22:50982 rb-in-f188.1e100.n:5228 FIN_WAIT1
tcp 0 0 192.168.1.22:55958 199.232.57.140:https ESTABLISHED
tcp 0 0 192.168.1.22:49036 162.159.136.234:https ESTABLISHED
tcp 0 0 192.168.1.22:41454 96.91.189.91.in-ad:http TIME_WAIT
tcp 0 0 192.168.1.22:43294 172.64.152.241:https ESTABLISHED
tcp 0 0 192.168.1.22:48450 104.18.38.60:https ESTABLISHED
netstat -u: Displays only UDP connections.
netstat -r: Displays the routing table.
netstat -i: Provides statistics for network interfaces.
Conclusion
You've reached the end of this article—what's next? You've absorbed a lot of information on various networking topics. How can you use this new knowledge?
Consider each section of this article as a tool in your DevOps toolkit. Each tool has a unique purpose and application. As a DevOps engineer, you'll encounter tasks that require networking skills. Understanding these tools and the basics of networking will help you tackle these tasks effectively.
Here's a quick recap of what you've learned:
DevOps engineers need networking skills.
The OSI model has 7 layers that build upon each other.
The TCP/IP model simplifies the OSI model and is widely used.
TCP is a secure, connection-oriented protocol, UDP is faster but connectionless.
TCP ports identify processes for commands.
IP addresses are essential for internet use.
Routing involves sending information over a network.
DNS translates computer language to human language, assigning domain names.
HTTP enables interaction with web pages and files, using commands and response codes.
Troubleshooting Networking commands.
Now that you have these tools, practice using them. Explore what you've learned in this article.
If you're eager to learn more about DevOps, follow us and subscribe to our weekly newsletter. Good luck!
Subscribe to my newsletter
Read articles from KubeCaptain directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
