A brief guide to UNIX
 Abhay Smaran Halemane
Abhay Smaran HalemaneUNIX- Unix is an operating system that lets multiple people use a computer at the same time and run different programs. it is known for being stable, secure, and efficient. many modern systems, like Linux and macOS, are based on UNIX. it’s often used in servers and big computer systems because it works well for managing files and running programs smoothly.
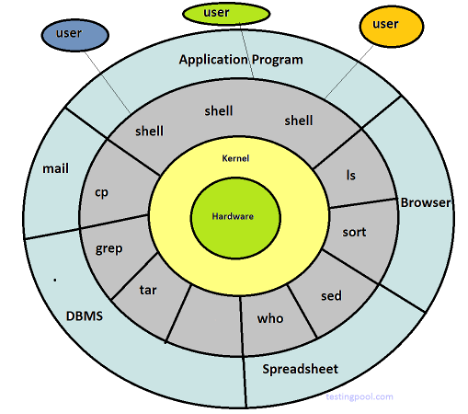
Unix architecture
Unix Architecture Explained
Unix architecture is typically divided into four main layers, each playing a crucial role in how the system operates:
Hardware:
This is the physical layer, including the CPU, memory, and storage devices.
It executes machine-level instructions provided by the operating system.
Kernel:
The core of Unix, responsible for managing hardware resources.
It handles process management, memory management, file system, device management, and system calls.
Directly interacts with the hardware and provides a layer of abstraction for software.
Shell:
The interface between users and the kernel.
It takes user commands, interprets them, and passes them to the kernel for execution.
Examples: Bash, C Shell (csh), Korn Shell (ksh), Z Shell (zsh).
Applications & Utilities:
These are user-level programs like text editors, compilers, and file management tools.
Common utilities include ls, cat, grep, awk, sed, vi, gcc.
Each layer ensures a structured and modular design, allowing Unix to be secure, stable, and multitasking.
Features of Unix
Unix is known for its stability, security, and efficiency. Here are its key features:
Multiuser System
- Multiple users can access the system simultaneously without interference.
Multitasking
- Supports running multiple programs at the same time using process scheduling.
Portability
- Written in C, making it adaptable to different hardware platforms.
Hierarchical File System
- Organizes files into directories (folders) in a structured manner.
Shell (Command-line Interface)
- Provides a powerful way to interact with the system using commands.
Piping & Redirection
- Allows combining multiple commands to process data efficiently (|, >, <).
Device Independence
- Treats hardware devices (printers, disks, etc.) as files, making management easier.
Security & Permissions
- Provides strong file and user-level security with permissions (read, write, execute).
Process Management
- Supports process creation, termination, and background execution.
Because of these features, Unix is widely used in servers, cloud computing, and enterprise environments.
Internal Commands (Built-in Shell Commands)
These are built into the shell (e.g., Bash, Zsh, etc.).
They do not require separate executable files.
They execute faster because the shell processes them directly.
Used for basic system operations like navigation, variable handling, and process control.
Examples of Internal Commands:
| Command | Description |
| cd | Change directory |
| pwd | Print current working directory |
| echo | Display a message or variable value |
| set | Set shell options and variables |
| unset | Remove shell variables |
| export | Export an environment variable |
| alias | Create command shortcuts |
| umask | Set default file permissions |
| exit | Close the shell session |
2. External Commands (Stored in /bin, /usr/bin, etc.)
These are separate executable files stored in system directories.
They require a full path or must be in the system’s $PATH to execute.
Typically, these are utility programs used for file manipulation, networking, etc.
Examples of External Commands:
| Command | Description |
| /bin/ls | List files in a directory |
| /bin/cp | Copy files and directories |
| /bin/mv | Move or rename files |
| /usr/bin/grep | Search for text in files |
| /usr/bin/find | Locate files in a directory |
| /usr/bin/tar | Archive files |
| /usr/bin/awk | Text processing tool |
| /usr/bin/gcc | GNU C compiler |
Basic Commands in UNIX
Echo Command in Unix
The echo command is used to display text, variables, or command outputs on the terminal.
Syntax:
echo [options] [text or variable]
Common Options & Examples
| Option | Description | Example |
| (No option) | Print simple text | echo "Hello, Unix!" → Hello, Unix! |
| -n | Print without a newline | echo -n "Hello" → Hello (No newline) |
| -e | Enable escape sequences | echo -e "Line1\nLine2" → Line1 (new line) Line2 |
| -E | Disable escape sequences (default) | echo -E "Line1\nLine2" → Line1\nLine2 (No new line) |
Date Command in Unix
The date command is used to display and format the system date and time.
Syntax:
date [OPTION] [+FORMAT]
Common Examples
| Command | Description | Example Output |
date | Show current date and time | Mon Mar 24 14:30:00 UTC 2025 |
date "+%Y-%m-%d" | Show date in YYYY-MM-DD format | 2025-03-24 |
date "+%d-%m-%Y %H:%M:%S" | Custom date and time format | 24-03-2025 14:30:00 |
date "+%A, %B %d, %Y" | Display full weekday and month names | Monday, March 24, 2025 |
date -u | Show time in UTC (Coordinated Universal Time) | Mon Mar 24 14:30:00 UTC 2025 |
date -d "next Monday" | Get the date of next Monday | Mon Apr 01 00:00:00 UTC 2025 |
date -s "2025-03-24 15:00:00" | Set system date and time (Requires root) | Changes system time |

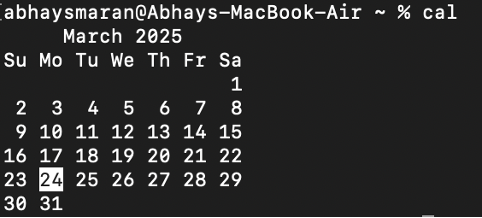
Calender Command in Unix
The cal command in Unix is used to display a calendar. By default, it shows the current month's calendar, but you can use various options to customize the output.
Basic Syntax:
cal [OPTION]... [MONTH] [YEAR]
OPTION: Options to modify how the calendar is displayed (e.g., displaying a specific year, setting the start of the week).MONTH: Optional. The month for which you want to display the calendar (1-12).YEAR: Optional. The year for which you want to display the calendar (e.g., 2025).
Common Options:
-3: Shows the previous, current, and next months.-y: Displays the entire year.-m: Displays the month (default behavior).-1: Displays a single month (default).-A <number>: Displays the next<number>months.-B <number>: Displays the previous<number>months.-s <weekday>: Starts the week on the specified weekday (e.g.,-s sunday).-j: Displays the Julian date.
Common Examples:Display the current month's calendar:
Output:
Display the calendar :
1. cal
Output:
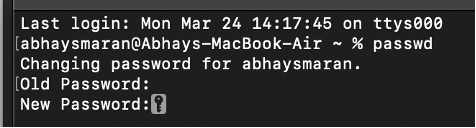
Passsword Command in Unix
The passwd command in Unix is used to change the user password. By default, it changes the password of the current user, but you can also specify other users (if you're an administrator or have the necessary permissions).
Basic Syntax:
passwd [OPTION]... [LOGIN]
OPTION: Various options that modify how the password command works.
LOGIN: The username of the account whose password you want to change. If not specified, it defaults to the current user.
Common Options:
-d: Deletes the password of a user (makes the account passwordless).
-e: Forces the user to change their password at the next login (expires the password).
-i: Sets the number of days after a password expires before the account is disabled (e.g., -i 7 means the account will be disabled 7 days after the password expires).
-l: Locks the user account, disabling login.
-u: Unlocks a previously locked account.
-n: Sets the minimum number of days between password changes.
-x: Sets the maximum number of days a password is valid.
-w: Sets a warning period before the password expires, notifying the user to change their password.
-h: Displays help information for the passwd command.
Common Examples:
- Change the current user's password:
Passwd This will prompt you to enter the current password and then ask for a new password.
Change the password for a specific user (requires root or sudo):
[sudo passwd username Replace username with the account name whose password you want to change.
Delete the password for a user (makes it passwordless):
- sudo passwd -d username This removes the password for username, effectively making it a passwordless account.
Man Command in Unix
The man command in Unix is used to display the manual (help) pages for various commands, system calls, library functions, and configuration files. It’s a great way to find detailed documentation for commands and their options.
Basic Syntax:
man [OPTION]... [COMMAND]
OPTION: Various options to modify how man displays the manual.
COMMAND: The name of the command or topic for which you want to view the manual.
The man command and its options:
| Option | Description | Example |
-k | Search for a keyword in the manual page database. | man -k keyword |
-f | Display a short description of a command (similar to whatis). | man -f command |
-a | Display all available manual pages for the given command (e.g., multiple sections). | man -a command |
-u | Update the manual page cache (refreshes or clears the cache). | man -u |
-t | Format the manual page as a PostScript document and send it to the printer or standard output. | man -t command |
-c | Once the manual page is displayed, it is cleared from memory. | man -c |
-w | Display the location of the manual page file without opening it. | man -w command |
-l | Open a manual page file directly from a file path rather than from the manual page database. | man -l /path/to/manual_page |
-M <path> | Set the location of the manual page directories (custom locations for manuals). | man -M /path/to/manuals command |
-P <pager> | Specify the pager program (e.g., less, more) to be used to view the manual pages. | man -P less command |
-S <section> | Specify a particular section of the manual to search in (e.g., system calls, user commands). | man -S 2 open |
-h | Display help information about the man command itself. | man -h |
-v | Display version information for the man command. | man -v |
Key Points:
Searching and Listing: Use
-kfor searching keywords,-ffor short descriptions, and-ato view all sections.Formatting and Customization: Use
-tto format as PostScript,-wto show the location of the manual page, and-Pto use a custom pager.Section and File: Use
-Sto view specific sections of the manual or-lto open a manual page file directly.Cache and Help:
-uupdates the cache,-cclears the page, and-hshows help for themancommand.
This breakdown covers the essential options you can use with the man command to explore and customize how you access manual pages.
Example
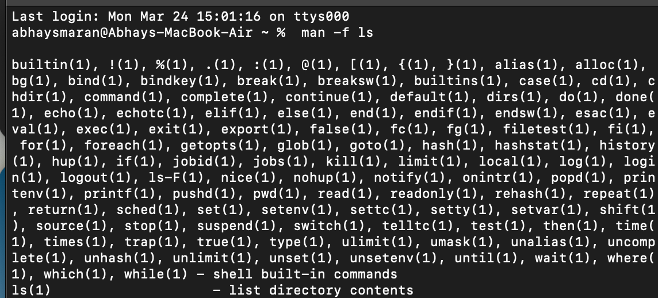
Superuser in Unix
In Unix, the superuser (also known as root) is the user account with the highest level of privileges. It has full control over the system, including access to all files, the ability to modify configurations, install software, and manage users. The root user is essential for system administration tasks.
How to Become a Superuser in Unix?
1. Using su (Switch User to Root)
The su (substitute user) command allows you to switch to the superuser account if you have the root password.
Syntax:
su -
Example:
su -
The
-option loads the root user’s environment variables.You will be prompted to enter the root password.
Once authenticated, the shell changes to
#, indicating root access.
You can also run a single command as root using:
su -c "<command>"
Example:
su -c "shutdown -h now"
2. Using sudo (SuperUser DO) – Recommended
The sudo command allows authorized users to execute administrative tasks without needing the root password. Instead, they authenticate with their own password.
Syntax:
sudo <command>
Example:
sudo ls /root
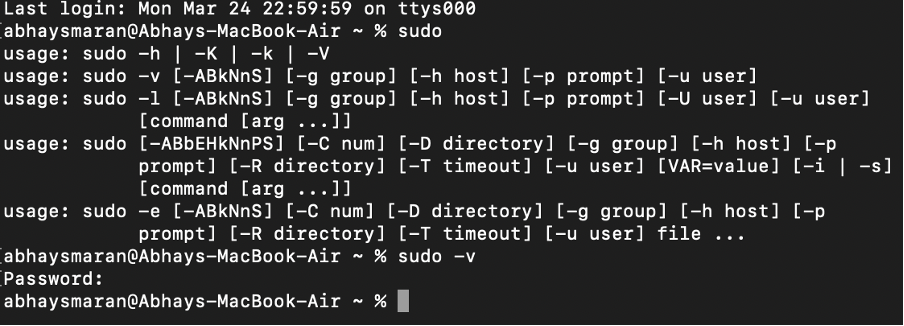
If you are using
sudofor the first time, it will ask for your user password.This is safer than
susince it logs commands and limits privileges to specific users.
To check if your user has sudo privileges, run:
sudo -l
Superuser Privileges in Unix
Once you have superuser access, you can:
Modify system files (
/etc/passwd,/etc/shadow)Install/remove software
Change user accounts and passwords (
useradd,passwd)Start/stop system services (
service,systemctl)Shutdown or restart the system (
shutdown,reboot)
Checking Superuser Status
To check if you are currently the superuser, run:
whoami
If it returns
root, you are the superuser.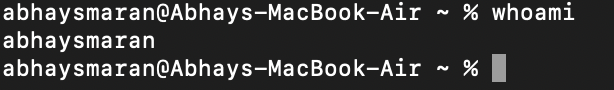
To verify if a user has sudo privileges, run:
sudo -l
Security Considerations for Superuser
Avoid using
rootfor daily tasks to prevent accidental system damage.Use
sudoinstead ofsuto improve security and auditing.Restrict superuser access to trusted users.
Edit sudo permissions carefully using:
· sudo visudo
- Disable direct root login via SSH for better security.
User and Group Management in Unix
In Unix, you can manage users and groups using the useradd, userdel, groupadd, and groupdel commands. These commands help system administrators create, delete, and manage user accounts and groups.
1. Adding a User (useradd)
The useradd command is used to create a new user in Unix.
Syntax:
useradd [options] <username>
Examples:
- Create a new user:
useradd john
- Create a user with a home directory:
useradd -m john
- Set a custom home directory for the user:
useradd -d /custom/home/john john
- Set a specific shell for the user:
useradd -s /bin/bash john
- Assign a user to a primary group:
useradd -g developers john
After adding a user, set a password:
passwd john
2. Deleting a User (userdel)
The userdel command is used to remove a user account.
Syntax:
userdel [options] <username>
Examples:
- Delete a user (without removing home directory):
userdel john
- Delete a user and their home directory:
userdel -r john
3. Adding a Group (groupadd)
The groupadd command creates a new user group.
Syntax:
groupadd [options] <groupname>
Examples:
- Create a new group:
groupadd developers
- Create a group with a specific Group ID (GID):
groupadd -g 5000 developers
4. Deleting a Group (groupdel)
- Delete a group:
Examples:
groupdel <groupname>
groupdel developers
Syntax:
The groupdel command removes a group.
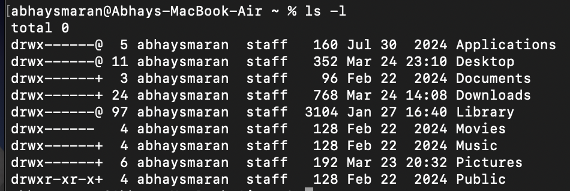
Significance of the ls Command in Unix
The ls command in Unix is used to list files and directories in the current or specified directory. It is one of the most commonly used commands for navigating and managing files in a Unix-based system.
1. Basic Syntax:
ls [options] [directory]
If no directory is specified, ls lists the contents of the current working directory.
2. Importance of ls Command:
File & Directory Management: Helps users view available files and directories.
Permissions & Ownership: Displays file permissions, owners, and group details.
Sorting & Filtering: Helps organize files based on various attributes like size, date, and type.
Troubleshooting: Useful in debugging file-related issues.
3. Commonly Used Options with ls
| Option | Description | Example |
ls | Lists files and directories in the current directory. | ls |
ls -l | Displays detailed information, including permissions, owner, and file size. | ls -l |
ls -a | Shows all files, including hidden files (files starting with .). | ls -a |
ls -h | Displays file sizes in a human-readable format (KB, MB, GB). | ls -lh |
ls -t | Sorts files by modification time (latest first). | ls -lt |
ls -r | Reverses the order of the listing. | ls -lr |
ls -S | Sorts files by size (largest first). | ls -lS |
ls -d */ | Lists only directories (not files). | ls -d */ |
ls -R | Lists all subdirectories recursively. | ls -R |
ls -i | Displays the inode number of files. | ls -i |
4. Examples
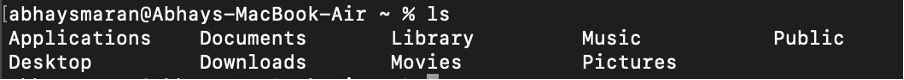
- List all files including hidden ones:
· ls -a
- List files with detailed information:
· ls -l
- List files sorted by size in human-readable format:
· ls -lhS
- List directories only:
· ls -d */
- List all files recursively from the current directory:
· ls -R
7 Fields in ls -l
When using the ls -l command in Unix, it displays a detailed list of files and directories with 7 key fields of information. Below is a breakdown of these fields:
Syntax of ls -l:
ls -l
Example Output:
-rw-r--r-- 1 user group 1024 Mar 24 10:00 file.txt
7 Fields in ls -l Output
| Field Number | Field Name | Description |
| 1 | File Permissions | Indicates the file type and permissions (e.g., -rw-r--r--). |
| 2 | Number of Links | The number of hard links to the file or directory. |
| 3 | Owner (User) | The user who owns the file. |
| 4 | Group | The group associated with the file. |
| 5 | File Size | The size of the file in bytes. |
| 6 | Modification Date & Time | The last modification date and time. |
| 7 | Filename | The name of the file or directory. |
Example Breakdown
-rw-r--r-- 1 user group 1024 Mar 24 10:00 file.txt
-rw-r--r--→ File permissions (regular file, read/write for owner, read-only for group/others)1→ Number of links (only one hard link)user→ Owner (User)group→ Group Name1024→ File size in bytes (1 KB)Mar 24 10:00→ Last modified date & timefile.txt→ Filename
Introduction to the Unix File System
The Unix file system is a methodology for logically organizing and storing large quantities of data such that the system is easy to manage. A file can be informally defined as a collection of (typically related) data, which can be logically viewed as a stream of bytes (i.e. characters). A file is the smallest unit of storage in the Unix file system.
By contrast, a file system consists of files, relationships to other files, as well as the attributes of each file. File attributes are information relating to the file, but do not include the data contained within a file. File attributes for a generic operating system might include (but are not limited to):
a file type (i.e. what kind of data is in the file)
a file name (which may or may not include an extension)
a physical file size
a file owner
file protection/privacy capability
file time stamp (time and date created/modified)
Additionally, file systems provide tools which allow the manipulation of files, provide a logical organization as well as provide services which map the logical organization of files to physical devices.
From the beginners perspective, the Unix file system is essentially composed of files and directories. Directories are special files that may contain other files.
The Unix file system has a hierarchical (or tree-like) structure with its highest level directory called root (denoted by /, pronounced slash). Immediately below the root level directory are several subdirectories, most of which contain system files. Below this can exist system files, application files, and/or user data files. Similar to the concept of the process parent-child relationship, all files on a Unix system are related to one another. That is, files also have a parent-child existence. Thus, all files (except one) share a common parental link, the top-most file (i.e. /) being the exception.
Below is a diagram (slice) of a "typical" Unix file system. As you can see, the top-most directory is / (slash), with the directories directly beneath being system directories. Note that as Unix implementaions and vendors vary, so will this file system hierarchy. However, the organization of most file systems is similar.
While this diagram is not all inclusive, the following system files (i.e. directories) are present in most Unix filesystems:
bin - short for binaries, this is the directory where many commonly used executable commands reside
dev - contains device specific files
etc - contains system configuration files
home - contains user directories and files
lib - contains all library files
mnt - contains device files related to mounted devices
proc - contains files related to system processes
root - the root users' home directory (note this is different than /)
sbin - system binary files reside here. If there is no sbin directory on your system, these files most likely reside in etc
tmp - storage for temporary files which are periodically removed from the filesystem
usr - also contains executable commands
File Types
All files in the Unix file system can be loosely categorized into 3 types, specifically:
ordinary files
directory files
device files
The first type of file listed above is an ordinary file, that is, a file with no "special-ness". Ordinary files are comprised of streams of data (bytes) stored on some physical device. Examples of ordinary files include simple text files, application data files, files containing high-level source code, executable text files, and binary image files. Note that unlike some other OS implementations, files do not have to be binary Images to be executable (more on this to come).
The second type of file listed above is a special file called a directory Directory files act as a container for other files, of any category. Thus we can have a directory file contained within a directory file (this is commonly referred to as a subdirectory). Directory files don't contain data in the user sense of data, they merely contain references to the files contained within them.
It is perhaps noteworthy at this point to mention that any "file" that has files directly below (contained within) it in the hierarchy must be a directory, and any "file" that does not have files below it in the hierarchy can be an ordinary file, or a directory, albeit empty.
The third category of file mentioned above is a device file. This is another special file that is used to describe a physical device, such as a printer or a portable drive. This file contains no data whatsoever, it merely maps any data coming its way to the physical device it describes.
Device file types typically include: character device files, block device files, Unix domain sockets, named pipes and symbolic links. However, not all of these file types may be present across various Unix implementations.
Relative Pathname vs. Absolute Pathname in Unix
In Unix, pathnames are used to specify the location of a file or directory in the filesystem. There are two types of pathnames:
Absolute Pathname
Relative Pathname
1. Absolute Pathname
An absolute pathname specifies the full path of a file or directory from the root (/) directory.
It always starts with
/.It provides a unique location in the filesystem, no matter where you are.
Example:
/home/user/Documents/file.txt
/→ Root directoryhome→ Directory under rootuser→ User’s home directoryDocuments→ A subdirectoryfile.txt→ Target file
Command Example Using Absolute Path:
cd /usr/local/bin
This command moves to /usr/local/bin, no matter the current directory.
2. Relative Pathname
A relative pathname specifies a file or directory location relative to the current working directory (pwd).
It does not start with
/.Uses
.(current directory) and..(parent directory) for navigation.
Example:
If the current directory is /home/user, then:
cd Documents
is equivalent to:
cd /home/user/Documents
because Documents is relative to /home/user.
Common Relative Path Commands:
- Move to the parent directory:
· cd ..
- Move to a subdirectory:
· cd Downloads
- Move up two levels:
· cd ../../
Key Differences Between Absolute and Relative Pathnames
| Feature | Absolute Pathname | Relative Pathname |
| Starts With | / (root directory) | No /, depends on pwd |
| Example | /etc/passwd | ../Documents/file.txt |
| Works From Any Directory? | Yes | No, depends on location |
| Usage | System-wide access | Shortcuts for navigation |
Which One to Use?
Use absolute paths when you need a fixed reference to a file, like in scripts or system configurations.
Use relative paths for easier navigation in the terminal when working within a known directory.
Commands and Arguments in Unix
In Unix, a command is an instruction given to the shell to perform a specific task. Commands often take arguments, which modify their behavior or specify inputs.
1. Command Syntax
command [options] [arguments]
command → The actual Unix command.
options (flags) → Modify the behavior of the command (usually start with
-or--).arguments → Specify the target file, directory, or value for the command.
2. Examples of Commands with Arguments
Basic Example
ls -l /home/user
ls→ Command to list files-l→ Option (long format)/home/user→ Argument (directory to list)
3. Types of Arguments in Unix
(a) Positional Arguments
These are the normal arguments passed to a command.
Example:
· cp file1.txt file2.txt
cp→ Commandfile1.txt→ Source file (argument)file2.txt→ Destination file (argument)
(b) Options (Flags) as Arguments
Options modify how a command behaves.
Example:
· rm -r myfolder
rm→ Command to remove-r→ Recursive option (needed to delete directories)myfolder→ Argument (directory to delete)
(c) Combined Options
Multiple options can be used together.
Example:
· ls -lah /var/log
-l→ Long format-a→ Show hidden files-h→ Human-readable sizes/var/log→ Argument (directory)
4. Checking Command Arguments (man and --help)
- Use
manto check details:
· man ls
- Use
--helpfor quick help:
· ls –help
Relative and Absolute Permissions in Unix
Unix file permissions determine who can read, write, or execute a file or directory. There are two ways to change permissions:
Relative (Symbolic) Permissions
Absolute (Numeric) Permissions
1. Relative (Symbolic) Permissions
Relative permissions use symbols (u, g, o, a, +, -, =) to modify specific permissions without affecting other existing permissions.
Syntax:
chmod [who][operator][permission] filename
[if !supportLists]· [endif]Who (u, g, o, a):
u→ User (owner)g→ Groupo→ Othersa→ All (user, group, others)
[if !supportLists]· [endif]Operator (+, -, =):
+→ Add permission-→ Remove permission=→ Set exact permission (overwrites previous settings)
[if !supportLists]· [endif]Permissions (r, w, x):
r→ Readw→ Writex→ Execute
Examples:
- Give the owner (
u) execute permission (+x)
2. chmod u+x file.txt
- Remove write (
-w) permission for group (g)
4. chmod g-w file.txt
- Give all users (
a) read (r) and write (w) permissions
6. chmod a+rw file.txt
- Set exact permissions (only read for group and others)
8. chmod g=r,o=r file.txt
2. Absolute (Numeric) Permissions
Absolute permissions use octal (numeric) values to represent permissions, making it a faster way to set file permissions.
Octal Values:
| Permission | Symbolic | Octal Value |
| No permission | --- | 0 |
| Execute only | --x | 1 |
| Write only | -w- | 2 |
| Write + Execute | -wx | 3 |
| Read only | r-- | 4 |
| Read + Execute | r-x | 5 |
| Read + Write | rw- | 6 |
| Read + Write + Execute | rwx | 7 |
Syntax:
chmod [###] filename
Each digit represents user (owner), group, and others in that order.
Examples:
- Give full permissions (
rwx) to owner, read and execute (r-x) to group, and read (r--) to others
2. chmod 754 file.txt
7→ Owner (rwx)5→ Group (r-x)4→ Others (r--)
- Give read and write (
rw-) to owner, read-only (r--) to group and others
4. chmod 644 file.txt
- Give full permissions to everyone (
rwxrwxrwx)
6. chmod 777 file.txt
- Remove all permissions (
---------)
8. chmod 000 file.txt
Key Differences Between Relative and Absolute Permissions
| Feature | Relative (Symbolic) Permissions | Absolute (Numeric) Permissions |
| Method | Uses u, g, o, a, +, -, = | Uses octal numbers (0-7) |
| Flexibility | Can modify specific permissions | Sets all permissions at once |
| Readability | Easier to understand | Faster to apply but less readable |
| Example | chmod u+x file.txt | chmod 744 file.txt |
Conclusion
Use relative permissions (
chmod u+x file.txt) when modifying specific permissions.Use absolute permissions (
chmod 755 file.txt) when setting all permissions at once.
Wildcards in Unix
Wildcards are special characters used in Unix to match file names or patterns in commands. They help simplify searching and batch processing of files.
Types of Wildcard Characters in Unix
| Wildcard | Description | Example |
* (Asterisk) | Matches zero or more characters | ls *.txt → Lists all .txt files |
? (Question Mark) | Matches exactly one character | ls file?.txt → Matches file1.txt, file2.txt but not file10.txt |
[ ] (Square Brackets) | Matches one character from a set | ls file[12].txt → Matches file1.txt, file2.txt but not file3.txt |
[^] (Negation in Brackets) | Matches one character not in a set | ls file[^3].txt → Matches file1.txt, file2.txt but not file3.txt |
{ } (Curly Braces) | Expands into multiple patterns | ls file{1,2,3}.txt → Matches file1.txt, file2.txt, file3.txt |
- (Range in Brackets) | Matches a range of characters | ls file[1-5].txt → Matches file1.txt to file5.txt |
~ (Tilde) | Expands to home directory | cd ~ → Moves to home directory |
! (Negation) | Used with find to exclude files | find . ! -name "*.txt" → Finds files excluding .txt |
Examples of Using Wildcards
1. Using * (Asterisk)
ls *.sh
- Lists all files ending with
.sh.
2. Using ? (Question Mark)
ls file?.txt
Matches
file1.txt,file2.txt, etc.Does not match
file10.txt(because?represents exactly one character).
3. Using [ ] (Character Set)
ls file[12].txt
Matches
file1.txt,file2.txt.Does not match
file3.txt.
4. Using [^ ] (Negation)
ls file[^3].txt
- Matches
file1.txt,file2.txtbut notfile3.txt.
5. Using { } (Brace Expansion)
ls file{1,3,5}.txt
- Matches
file1.txt,file3.txt,file5.txt.
6. Using - (Range)
ls file[1-5].txt
- Matches
file1.txttofile5.txt.
7. Using ~ (Tilde)
cd ~
- Moves to the home directory.
8. Using ! (Negation with find)
find . ! -name "*.txt"
- Finds all files except
.txtfiles.
Summary of Wildcard Usage
| Wildcard | Usage Example | Matches |
* | ls *.txt | file.txt, notes.txt, data.txt |
? | ls file?.txt | file1.txt, file2.txt, not file10.txt |
[ ] | ls file[12].txt | file1.txt, file2.txt |
[^ ] | ls file[^3].txt | Matches file1.txt, but not file3.txt |
{ } | ls file{1,3,5}.txt | file1.txt, file3.txt, file5.txt |
- | ls file[1-5].txt | file1.txt to file5.txt |
~ | cd ~ | Moves to home directory |
! | find . ! -name "*.txt" | Finds all files except .txt |
Grep Command in Unix
The grep command helps search for words or patterns inside files. Below is a table with common grep commands, explanations, and examples.
| Command | What It Does | Example Output |
grep "error" logfile.txt | Finds lines containing "error" inside logfile.txt. | System error detected |
grep -i "error" logfile.txt | Case-insensitive search (matches Error, ERROR, etc.). | CRITICAL ERROR found |
grep -n "error" logfile.txt | Shows line numbers where "error" appears. | 5: System error detected |
grep -o "error" logfile.txt | Shows only the matching word, not the full line. | error |
grep -c "error" logfile.txt | Counts how many times "error" appears. | 10 (meaning found 10 times) |
grep -v "error" logfile.txt | Shows lines that do NOT contain "error". | System is running fine |
grep -w "error" logfile.txt | Matches the exact word "error", not "errors" or "error_log". | error found in logs |
grep -r "error" /var/logs/ | Searches for "error" in all files inside /var/logs/. | log1.txt: System error detected |
| `grep -E "error | failure" logfile.txt` | Uses extended regular expressions to find "error" or "failure". |
grep --color "error" logfile.txt | Highlights the word "error" in red for easy identification. | ⚠️ error found in logs |
| `ps aux | grep "firefox"` | Finds if a process like "firefox" is running. |
| `dmesg | grep "usb"` | Searches system logs for USB-related messages. |
| `grep "failed" /var/log/auth.log | wc -l` | Counts how many times "failed" appears in the login logs. |
Explanation of Key Features
Case Sensitivity: Use
-ito ignore uppercase/lowercase differences.Count Matches: Use
-cto see how many times a word appears.Exclude Lines: Use
-vto find lines that do not contain a word.Recursive Search: Use
-rto search inside all files in a folder.Highlighting: Use
--colorto make matches easier to see.
Difference Between grep and Wildcards in Unix
Both grep and wildcards are used for searching, but they work differently.
1. Wildcards (*, ?, [ ])
Wildcards are used to match file names in Unix commands like ls, rm, cp, etc.
They do not search inside files.
Example (Wildcards in ls)
ls *.txt
👉 Lists all files ending in .txt.
2. grep (Global Regular Expression Print)
grep is used to search inside files for specific words or patterns.
Example (Search for "error" in a log file)
grep "error" logfile.txt
👉 Finds lines containing "error" inside logfile.txt.
Key Differences
| Feature | Wildcards (*, ?, [ ]) | grep |
| Use | Matches file names | Searches inside files |
| Where it Works | Commands like ls, rm, cp, mv | Reads file content |
| Example | ls *.txt → Lists all .txt files | grep "error" logfile.txt → Finds "error" in a file |
| Can search inside files? | ❌ No | ✅ Yes |
| Can filter by content? | ❌ No | ✅ Yes |
| Supports complex patterns? | ❌ Limited (*, ?, [ ]) | ✅ Uses regular expressions (.*, ^, $) |
When to Use What?
✅ Use Wildcards when you need to match file names.
✅ Use grep when you need to search inside files.
Shell
What is a Shell in Unix/Linux?
A shell is a command-line interface that allows users to interact with the Unix/Linux operating system. It takes user commands, processes them, and sends them to the operating system to execute.
Functions of a Shell
· Accepts commands from the user.
· Interprets and converts commands into machine instructions.
· Executes commands and displays the output.
· Supports scripting (writing programs with commands).
Common Types of Shells
| Shell Type | Description | Command to Check |
| Bash (Bourne Again Shell) | Default shell in most Linux systems. | echo $SHELL |
| Sh (Bourne Shell) | The original Unix shell. | sh |
| C Shell (csh) | Uses C-like syntax for scripting. | csh |
| Korn Shell (ksh) | Advanced shell with scripting improvements. | ksh |
| Z Shell (zsh) | Powerful shell with auto-completion and plugins. | zsh |
Shell Interpretive Cycle (How the Shell Works)
The Shell Interpretive Cycle describes how the shell processes user commands. It follows these steps:
1. User Inputs a Command
- Example:
· ls -l
- The user types a command and presses Enter.
2. Shell Reads the Command
- The shell takes the input command and breaks it down into command and options.
3. Shell Interprets the Command
- It checks if the command is built-in (like
cd,echo) or an external program (ls,grep).
4. Shell Finds the Command
If it is an external command, the shell looks for it in system directories (
/bin,/usr/bin) using thePATHvariable.Example:
· which ls
Output:
/bin/ls
5. Shell Executes the Command
The shell sends the command to the kernel (OS core) for execution.
The command runs and produces output.
6. Shell Displays Output
The shell prints the result on the terminal.
Example Output:
· drwxr-xr-x 5 user user 4096 Mar 24 10:30 Documents
7. Shell Waits for Next Command
- After execution, the shell returns to the prompt, waiting for the next command.
Example of Shell Interpretive Cycle
User Enters Command
echo "Hello, World!"
Shell Processing
Recognizes
echoas a built-in command.Passes
"Hello, World!"as an argument.
Execution & Output
Hello, World!
Shell Script Example (Automating Commands)
Instead of typing multiple commands manually, we can write a script:
#!/bin/bash
echo "Hello, this is a shell script!"
date
ls
🔹 Saves time by automating tasks!
Summary Table
| Step | Action | Example |
| 1. User Inputs Command | User types a command. | ls -l |
| 2. Shell Reads Command | Breaks it into parts. | Command: ls, Option: -l |
| 3. Shell Interprets | Checks if it's built-in or external. | ls is an external command. |
| 4. Shell Finds Command | Looks for it in system directories. | Found in /bin/ls |
| 5. Shell Executes | Sends it to the OS (kernel). | Runs the command. |
| 6. Shell Displays Output | Prints result on screen. | Shows file list. |
| 7. Shell Waits | Returns to prompt for next input. | $ (Waiting for new command) |
Why is the Shell Important?
· Helps users communicate with the OS.
· Automates tasks using shell scripts.
· Provides a flexible and powerful interface.
Exit Status in Unix/Linux
The exit status (also called the return code) is a numeric value returned by a command after it executes. It helps determine whether a command succeeded or failed.
Checking Exit Status
After running a command, you can check its exit status using:
echo $?
✅ If the exit status is 0, the command was successful.
❌ If the exit status is non-zero (e.g., 1, 2, 127), the command failed.
Examples of Exit Status
1. Successful Command (exit status = 0)
ls
echo $? # Check exit status
0
✅ Output:
0
Exit code 0 means the command ran successfully.
2. Failed Command (exit status ≠ 0)
ls nonexistentfile
echo $? # Check exit status
❌ Output:
ls: cannot access 'nonexistentfile': No such file or directory
2
Exit code 2 indicates an error.
Common Exit Codes
| Exit Code | Meaning |
0 | Success |
1 | General error |
2 | Misuse of shell command |
126 | Command found but not executable |
127 | Command not found |
130 | Command terminated by Ctrl+C |
Using Exit Status in Scripts
You can use exit codes to control script execution.
Example: Checking if a Command Succeeded
#!/bin/bash
mkdir myfolder # Create a folder
if [ $? -eq 0 ]; then
echo "Folder created successfully!"
else
echo "Failed to create folder!"
fi
✅ If mkdir runs successfully, it prints "Folder created successfully!"
❌ Otherwise, it prints "Failed to create folder!"
Manually Setting Exit Status in Scripts
#!/bin/bash
echo "This script will fail"
exit 1 # Manually return error code 1
🔹 Running this script will always fail with an exit status of 1.
Logical Operators for Conditional Execution in Unix/Linux
Logical operators allow combining commands and executing them conditionally based on their exit status.
Types of Logical Operators
| Operator | Name | Usage | Meaning |
&& | Logical AND | command1 && command2 | Runs command2 only if command1 succeeds (exit status = 0). |
| ` | ` | Logical OR | |
; | Command Separator | command1 ; command2 | Runs command1, then command2 regardless of success or failure. |
! | Logical NOT | ! command | Runs command and reverses the exit status (0 → 1, 1 → 0). |
| `&& | ` | Ternary Operator |
Examples
1. Logical AND (&&)
Runs the second command only if the first one succeeds.
mkdir myfolder && echo "Folder created successfully!"
If
mkdirsucceeds,"Folder created successfully!"is printed.If
mkdirfails, nothing happens.
2. Logical OR (||)
Runs the second command only if the first one fails.
ls myfile || echo "File not found!"
If
ls myfilefails (file does not exist), it prints"File not found!".If
lssucceeds, nothing happens.
3. Command Separator (;)
Runs both commands regardless of success or failure.
echo "Hello"; ls nonexistentfile
"Hello"is printed.lsfails, but it does not affect the first command.
4. Logical NOT (!)
Reverses the exit status of a command.
! ls myfile
echo $?
If
ls myfilesucceeds (exit status 0),!changes it to 1.If
ls myfilefails (exit status 1),!changes it to 0.
5. Combining && and || (Ternary Operator)
Runs command2 if command1 succeeds, otherwise runs command3.
mkdir myfolder && echo "Success" || echo "Failure"
If
mkdirsucceeds, it prints"Success".If
mkdirfails, it prints"Failure".
Summary Table
| Operator | Example | When Command2 Runs? |
&& | mkdir test && echo "Success" | If mkdir succeeds (exit 0). |
| ` | ` | |
; | echo "Hello"; ls file | Always runs both. |
! | ! ls file | Reverses success/failure. |
| `&& | ` |
When to Use These Operators?
For efficient scripting (run commands conditionally).
To automate error handling (
&&for success,||for failure).To chain multiple commands in one line.
Three Ways of Using the test Command in Unix/Linux
The test command is used to evaluate numeric comparisons, string operations, and file conditions.
1. Numeric Test (-eq, -ne, -gt, -lt, -ge, -le)
Used to compare numbers.
Example: Check if Two Numbers are Equal
num1=10
num2=20
if [ $num1 -lt $num2 ]; then
echo "$num1 is less than $num2"
fi
Explanation:
-eq(equal)-ne(not equal)-gt(greater than)-lt(less than)-ge(greater than or equal to)-le(less than or equal to)
2. String Test (=, !=, -z, -n)
Used to check strings, including their length and equality.
Example: Check if a String is Empty
str=""
if [ -z "$str" ]; then
echo "String is empty"
fi
Explanation:
=(equal)!=(not equal)-z(string is empty)-n(string is not empty)
3. File Test (-f, -d, -e, -r, -w, -x)
Used to check if a file or directory exists and its properties.
Example: Check if a File Exists and is Writable
if [ -f myfile ] && [ -w myfile ]; then
echo "File exists and is writable"
}
Explanation:
-f(file exists)-d(directory exists)-e(file/directory exists)-r(readable)-w(writable)-x(executable)
Summary Table
| Test Type | Operator | Example |
| Numeric | -eq, -ne, -gt, -lt, -ge, -le | [ $a -gt $b ] |
| String | =, !=, -z, -n | [ -z "$str" ] |
| File | -f, -d, -e, -r, -w, -x | [ -f file ] |
General UNIX File APIs
UNIX provides several File APIs for creating, opening, reading, writing, and closing files. These APIs are part of the POSIX standard and are commonly used in C programming.
1. open() – Open or Create a File
Syntax:
int open(const char *pathname, int flags, mode_t mode);
Explanation of Parameters:
| Parameter | Description |
pathname | The name (path) of the file to open or create. |
flags | Specifies the mode of opening the file (read, write, append, etc.). |
mode | (Optional) If creating a file, defines the file permissions (e.g., 0644). |
Common flags Options:
| Flag | Description |
O_RDONLY | Open for read only. |
O_WRONLY | Open for write only. |
O_RDWR | Open for read and write. |
O_CREAT | Create the file if it does not exist. |
O_TRUNC | Truncate the file to 0 bytes if it exists. |
O_APPEND | Append to the file instead of overwriting. |
Example: Open a File for Writing
int fd = open("example.txt", O_WRONLY | O_CREAT, 0644);
if (fd == -1) {
perror("Error opening file");
}
2. read() – Read Data from a File
Syntax:
ssize_t read(int fd, void *buf, size_t count);
Explanation of Parameters:
| Parameter | Description |
fd | File descriptor obtained from open(). |
buf | Pointer to a buffer where data will be stored. |
count | Number of bytes to read. |
Example: Read 100 Bytes from a File
char buffer[100];
ssize_t bytesRead = read(fd, buffer, sizeof(buffer));
if (bytesRead == -1) {
perror("Error reading file");
}
3. write() – Write Data to a File
Syntax:
ssize_t write(int fd, const void *buf, size_t count);
Explanation of Parameters:
| Parameter | Description |
fd | File descriptor obtained from open(). |
buf | Pointer to the buffer containing data to write. |
count | Number of bytes to write. |
Example: Write a String to a File
const char *msg = "Hello, UNIX!";
ssize_t bytesWritten = write(fd, msg, strlen(msg));
if (bytesWritten == -1) {
perror("Error writing file");
}
4. lseek() – Move the File Pointer
Syntax:
off_t lseek(int fd, off_t offset, int whence);
Explanation of Parameters:
| Parameter | Description |
fd | File descriptor. |
offset | Number of bytes to move the pointer. |
whence | Position reference (SEEK_SET, SEEK_CUR, SEEK_END). |
Common whence Values:
| Value | Description |
SEEK_SET | Move to offset from the beginning of the file. |
SEEK_CUR | Move offset bytes from the current position. |
SEEK_END | Move offset bytes from the end of the file. |
Example: Move to the 10th Byte
off_t newPos = lseek(fd, 10, SEEK_SET);
if (newPos == -1) {
perror("Error seeking file");
}
5. close() – Close a File
Syntax:
int close(int fd);
Explanation of Parameters:
| Parameter | Description |
fd | File descriptor to be closed. |
Example: Close the File
if (close(fd) == -1) {
perror("Error closing file");
}
6. unlink() – Delete a File
Syntax:
int unlink(const char *pathname);
Explanation of Parameters:
| Parameter | Description |
pathname | Name of the file to delete. |
Example: Delete a File
if (unlink("example.txt") == -1) {
perror("Error deleting file");
}
Summary of UNIX File APIs
| Function | Purpose | Example Usage |
open() | Open or create a file | `int fd = open("file.txt", O_RDWR |
read() | Read from a file | read(fd, buffer, 100); |
write() | Write to a file | write(fd, "Hello", 5); |
lseek() | Move file pointer | lseek(fd, 10, SEEK_SET); |
close() | Close a file | close(fd); |
unlink() | Delete a file | unlink("file.txt"); |
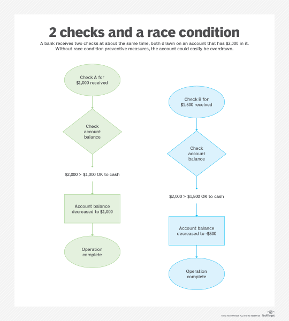
What is a Race Condition?
A race condition occurs when two or more processes or threads attempt to access and modify shared resources simultaneously, leading to unpredictable results. This typically happens in multithreading or multi-processing environments when proper synchronization is not used.
Example Scenario
Imagine two bank customers trying to withdraw money from the same account at the same time:
Person A checks the balance – it shows $1000.
Person B checks the balance – it also shows $1000.
Person A withdraws $500, leaving $500 in the account.
Person B also withdraws $500, thinking there is still $1000 available.
Now, the account should have $0, but due to the race condition, it may become negative (-$500) or still show $500 incorrectly!
Causes of Race Conditions
Concurrent Access to Shared Resources – Multiple processes access the same file, variable, or database without control.
Context Switching – The operating system switches between tasks unpredictably, causing conflicts.
Lack of Synchronization – No locking mechanism to ensure one process completes before another starts.
Uncontrolled Input/Output (I/O) Operations – Multiple users or programs reading/writing to the same file simultaneously.
Common Examples of Race Conditions
| Scenario | What Happens? |
| File Writing | Two processes write to a file at the same time, leading to corrupted or missing data. |
| Bank Transactions | Two users withdraw money at the same time, causing incorrect balance updates. |
Process Creation (fork()) | A parent process modifies data, but a child process reads an old value before it is updated. |
| Printing to Console | Two threads print at the same time, mixing or overlapping output. |
How to Prevent Race Conditions?
To avoid race conditions, we use synchronization mechanisms that control the order of execution.
| Method | How It Works? |
| Mutex (Mutual Exclusion) | Only one thread/process can access the resource at a time. |
| Semaphore | Limits the number of processes that can access a resource simultaneously. |
| File Locking | Prevents multiple processes from modifying the same file at once. |
| Atomic Operations | Ensures that shared resource updates happen in one step, avoiding conflicts. |
Real-World Example
In online ticket booking systems, multiple users may try to book the last seat at the same time. If proper synchronization is not used, two users might receive confirmation for the same seat, leading to double booking and customer disputes.
What is a Daemon Process in Unix/Linux?
A daemon is a background process in Unix/Linux that runs continuously and is not controlled by a user. It typically performs system-level tasks, such as handling network requests, scheduling jobs, or managing hardware.
🔹 Example: Web servers, database services, and logging processes are all daemon processes.
Characteristics of Daemon Processes
| Feature | Description |
| Runs in Background | Does not require user interaction and runs independently. |
| No Controlling Terminal | Detached from the user’s shell session to prevent accidental termination. |
| Started at Boot | Many daemons start automatically when the system boots (e.g., cron, syslog). |
Parent Process is init or systemd | Once a daemon starts, its parent process is usually init (older systems) or systemd (modern systems). |
Examples of Daemon Processes
| Daemon | Function |
cron | Runs scheduled jobs (e.g., backups, script execution). |
sshd | Manages SSH remote login sessions. |
httpd (Apache/Nginx) | Web server daemon handling HTTP requests. |
mysqld | Manages MySQL database operations. |
syslogd | Handles system logging and stores logs. |
How to Identify Running Daemons?
1. Using ps Command
ps aux | grep daemon_name
🔹 This lists processes related to a particular daemon.
2. Using systemctl (for systemd-based systems)
systemctl status sshd
🔹 Checks the status of a daemon (e.g., SSH service).
How to Create a Daemon Process?
A daemon is typically created by forking a child process and detaching it from the terminal.
Steps to Create a Daemon Process:
Fork the process – The parent exits, and the child continues.
Create a new session – Detach from the terminal using
setsid().Close standard I/O (stdin, stdout, stderr) – Prevents accidental terminal output.
Change working directory – Usually set to
/to avoid tying the process to a mount point.Run in an infinite loop – To keep the daemon running.
Advantages of Daemon Processes
Automates tasks – Runs scheduled or background tasks without manual intervention.
Improves system performance – Handles specific tasks efficiently in the background.
Supports multitasking – Allows multiple services to run simultaneously.
Subscribe to my newsletter
Read articles from Abhay Smaran Halemane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
