One SQL Query That Could Destroy Your Entire Database (And How Hackers Use It)
 YuvaSec
YuvaSec
Introduction
Imagine logging into your bank account only to discover that someone else got in without your password. Scary, right? That’s not a movie plot—it’s often the result of an SQL Injection attack, one of the most dangerous yet common threats in cybersecurity today.
Here, we will embark on an exploration of the construction and use of malicious SQL queries by malicious attackers to bypass logins, retrieve confidential data, delete data or even run system commands.
With the rise of AI-driven automation and open-source utilities, the development of such attacks has become faster, easier, and more crippling making it more critical than ever for developers, tech enthusiasts, and security professionals to understand the basic methods at play.
⚠️ Disclaimer: This article is for educational and ethical hacking purposes only. Always have permission before testing any system.
Bypassing Login Mechanisms
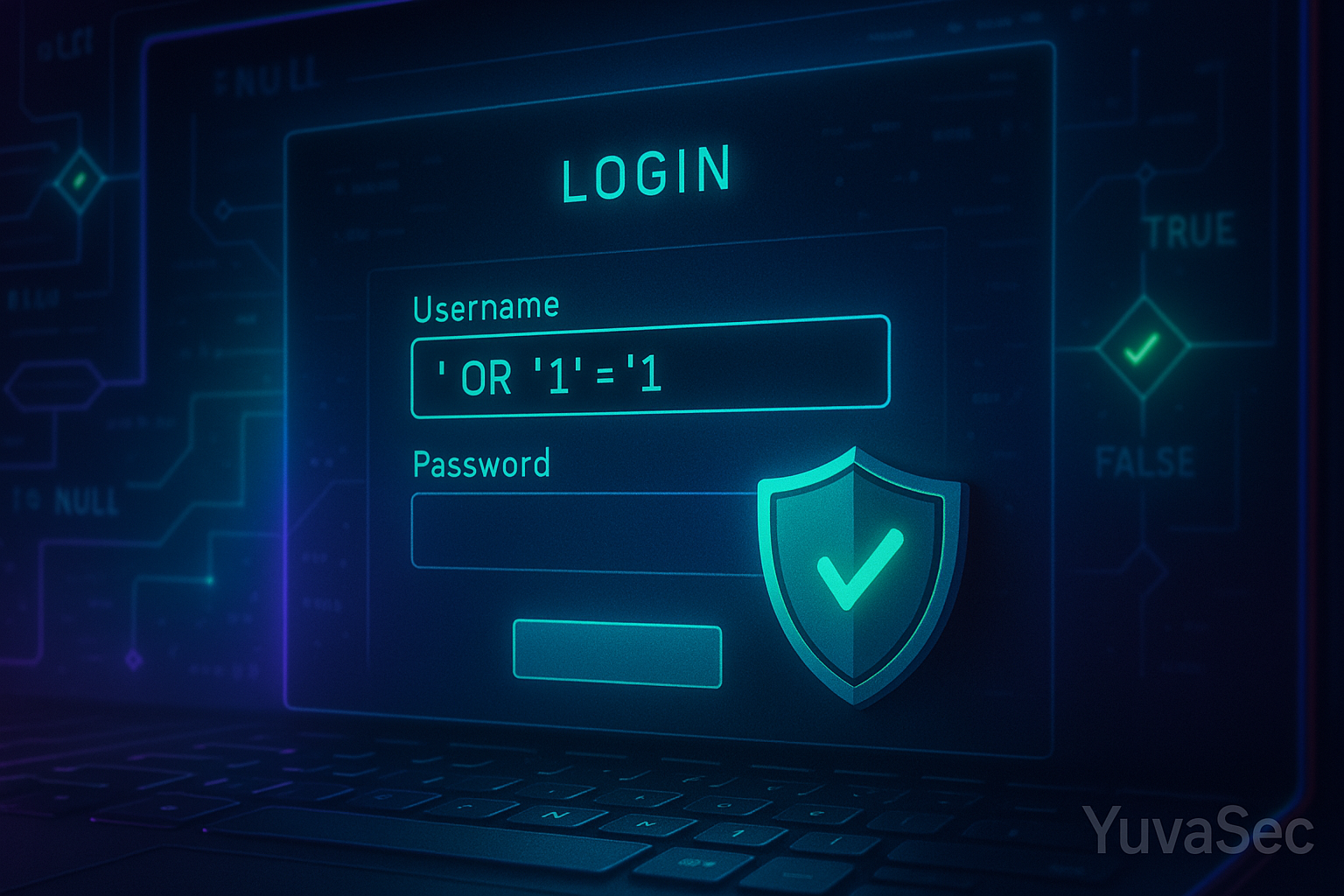
How Attackers Log In Without a Password
Many web apps rely on vulnerable login scripts like:
SELECT * FROM users WHERE username = '$input' AND password = '$pass';
If an attacker inputs:
Username: ' OR '1'='1
Password: anything
The query becomes:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = 'anything';
This always returns TRUE, allowing the attacker to bypass authentication.
Why it works:
SQL interprets
'1'='1'as a valid conditionPassword checks are effectively ignored
⚠️ Why Is This Dangerous?
It bypasses login mechanisms.
It can be used to extract data, modify databases, or escalate privileges if chained with other exploits.
It highlights the need for input sanitization and parameterized queries.
🔐 How to Prevent It?
Use parameterized queries or prepared statements like so (example in PHP with PDO):
$stmt = $pdo->prepare("SELECT * FROM users WHERE username = ? AND password = ?");
$stmt->execute([$input, $pass]);
This way, the input is treated as data, not executable SQL.
Counterargument:
Some may assume input validation on the front end is enough, but attackers can easily bypass it using tools like Burp Suite or custom scripts.
Dumping Sensitive Data Using UNION
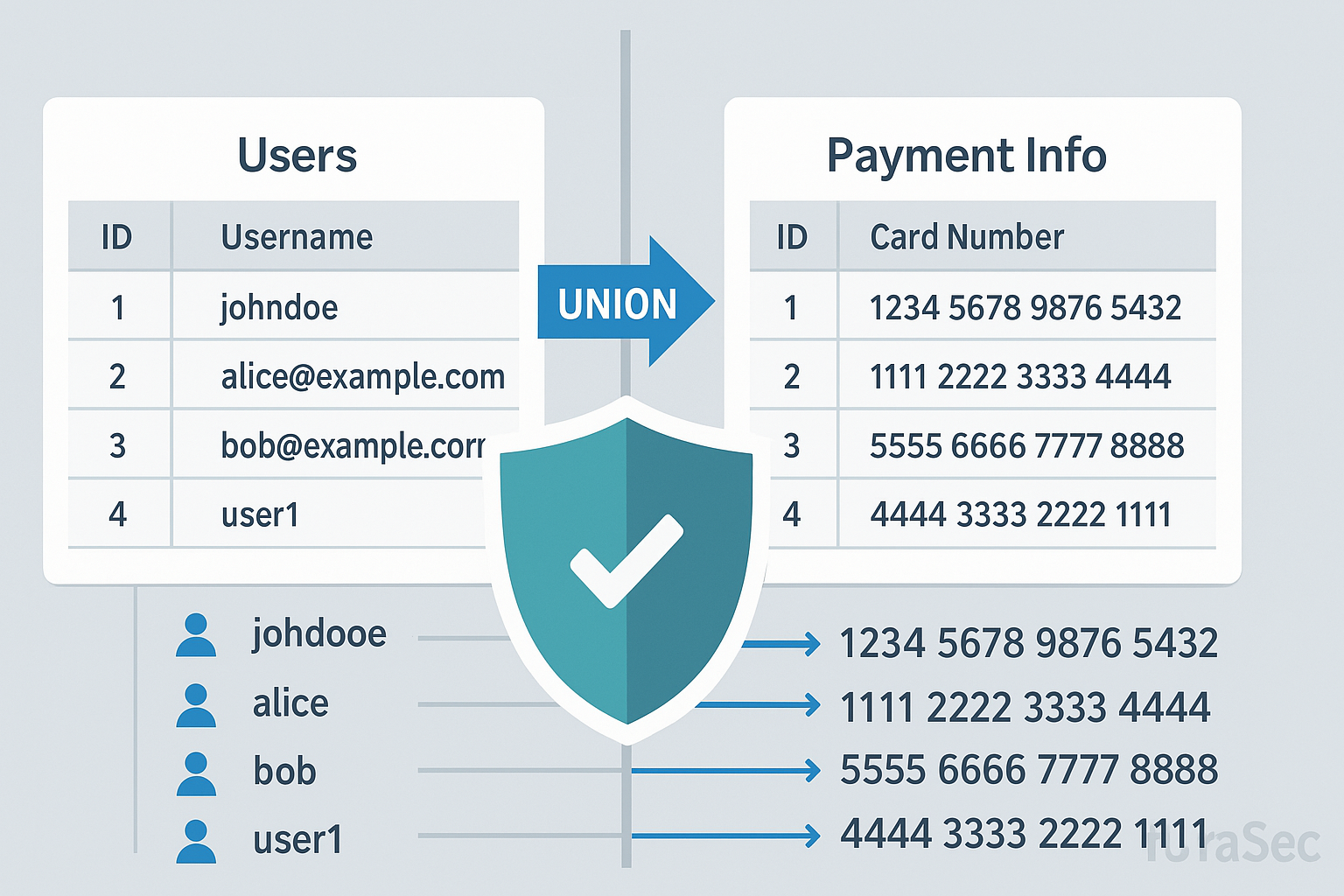
Merging Tables to Steal Information
If attackers get past the login, they might use SQL injection to exfiltrate data from other tables, like so:
' UNION SELECT credit_card_number, expiry_date FROM payments--
🔍 Breakdown:
'(Single Quote)This closes the original string input in the SQL query.
It's used to break out of the intended input context.
UNION SELECTUNIONCombines the result of the original query with another query.This lets the attacker fetch additional data from other tables in the database.
credit_card_number, expiry_date FROM paymentsThis part selects sensitive data from the
paymentstable.The attacker is attempting to read
credit_card_numberandexpiry_datecolumns.
--(Double Dash)This starts a comment in SQL.
Everything after
--is ignored, effectively cancelling out the rest of the original query.
🧪 Hypothetical Vulnerable Query
If the original code on the server is:
SELECT name, email FROM users WHERE username = 'input_here';
Then with the injection:
SELECT name, email FROM users WHERE username = '' UNION SELECT credit_card_number, expiry_date FROM payments--';
This bypasses authentication or retrieves unintended data, like credit card info.
🔐 How to Prevent This
Use Parameterized Queries / Prepared Statements
Employ ORMs that abstract raw SQL
Implement Input Validation
Limit database permissions
Use Web Application Firewalls (WAFs)
Destroying Data with Chained Queries
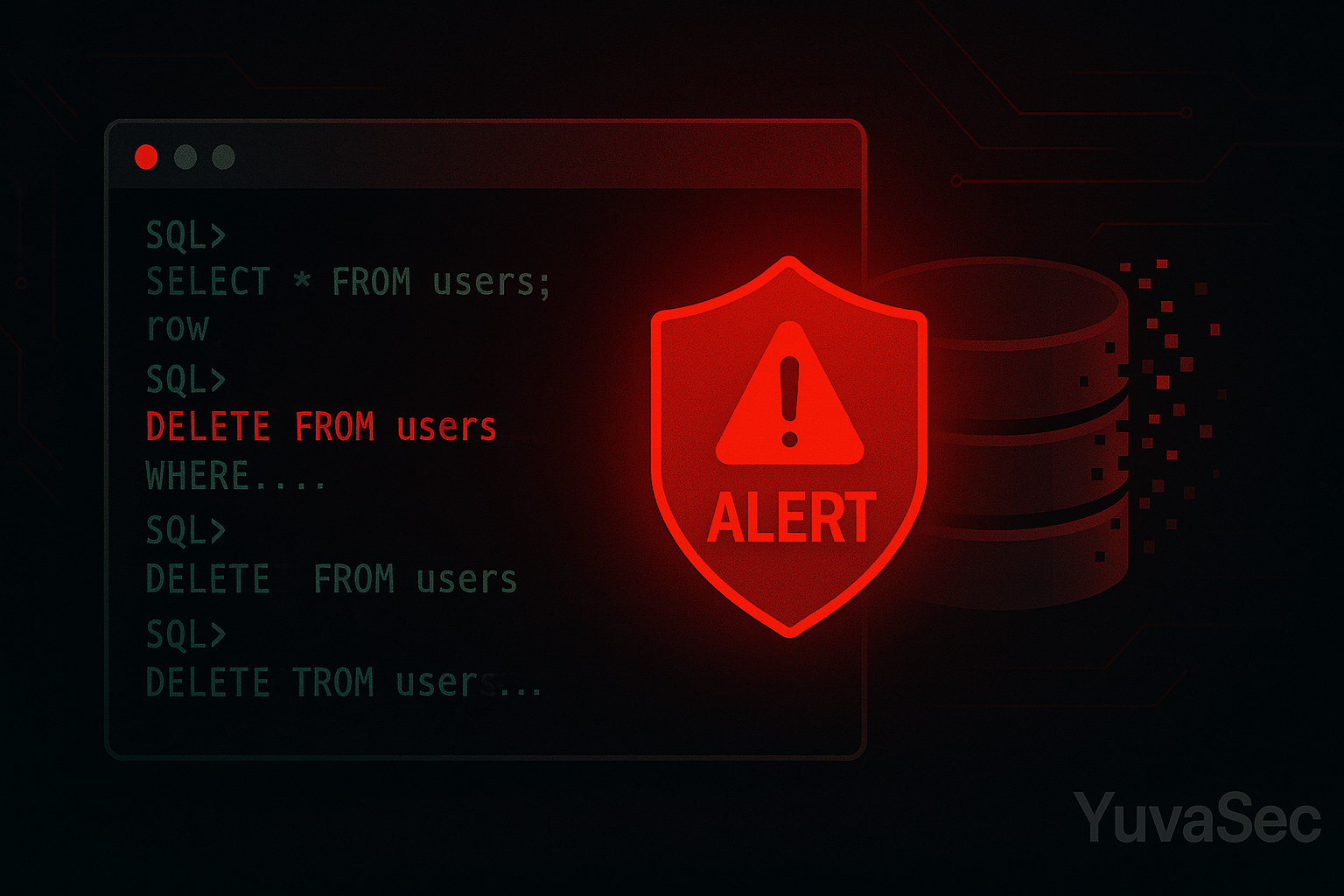
SQL Destruction in One Line
Some attackers go beyond theft—they destroy:
'; DELETE FROM users; --
🔍 Breakdown:
'— Closes the current string in the SQL statement.;— Ends the current SQL statement.DELETE FROM users;— Executes a new SQL command to delete all rows from theuserstable.--— This is a SQL comment. Everything after this is ignored by the database, so the rest of the original query is commented out and doesn’t interfere.
Example in context:
Suppose the backend code is like this (which is vulnerable):
SELECT * FROM users WHERE username = 'user_input';
If someone enters:
' ; DELETE FROM users; --
It becomes:
SELECT * FROM users WHERE username = ''; DELETE FROM users; --';
This executes two statements:
SELECT * FROM users WHERE username = '';DELETE FROM users;← ⚠️ Dangerous!
The -- comments out the rest of the line.
⚠️ Why Is This Dangerous?
All user records could be deleted.
This is why SQL injection is one of the most critical web vulnerabilities.
🔐 How to Prevent This
Use parameterized queries / prepared statements.
Implement input validation and sanitization.
Avoid dynamically building SQL queries with user input.
Remote Command Execution with xp_cmdshell
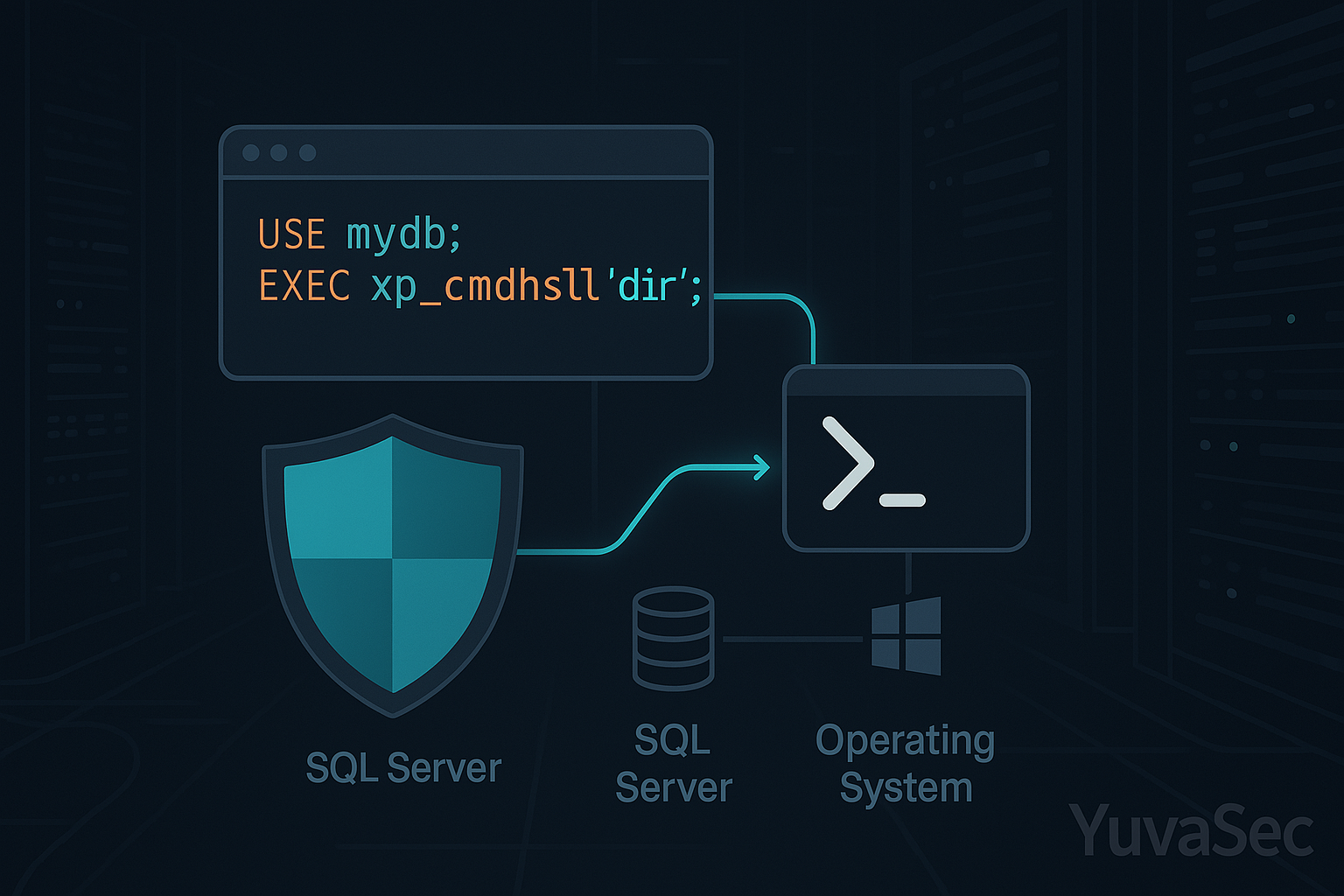
🖥️ From SQL to System-Level Control
Some databases (e.g., Microsoft SQL Server) allow system commands:
EXEC xp_cmdshell('net user hacker pass123 /add')
🔍 Breakdown:
EXEC: Executes a SQL command or stored procedure.xp_cmdshell: A special (and dangerous) extended stored procedure in Microsoft SQL Server that allows execution of arbitrary operating system commands.'net user hacker pass123 /add': This is the actual Windows command being executed. It does the following:net useris a command-line utility used to manage user accounts in Windows.hackeris the username being created.pass123is the password assigned to the account./addtells Windows to add the new user.Risk Level:
What This Code Does:
If successfully run on a vulnerable SQL Server instance with xp_cmdshell enabled and proper privileges, it will:
- Create a new user named
hackerwith passwordpass123on the Windows machine.
⚠️ Why This Is Dangerous:
It’s often seen in SQL Injection attacks where the attacker gains access to the database and uses
xp_cmdshellto escalate privileges or compromise the underlying system.xp_cmdshellis disabled by default in modern versions of SQL Server for this reason.If enabled and misconfigured, it can be used to fully compromise the operating system.
🔐 How to Prevent This:
Disable
xp_cmdshellunless absolutely required.Use least privilege principles for database accounts.
Ensure input sanitization and parameterized queries to prevent SQL injection.
🔒 Note: Most modern SQL configurations disable
xp_cmdshellby default—but it's often re-enabled for legacy compatibility.
Expert Insights
“SQL Injection remains one of the easiest yet most powerful tools for attackers—often requiring no more than a browser and a keyboard.” – Troy Hunt, Cybersecurity Researcher, Founder of Have I Been Pwned
“The root problem isn't SQL itself—it's developers trusting user input too much. Input should always be treated as hostile.” – Katie Moussouris, Founder of Luta Security, former Microsoft Security Strategist
Both experts stress that SQLi isn't just a code flaw—it's a trust flaw. Failing to enforce proper boundaries between user input and query execution opens the door to exploitation.
Conclusion
From simple login bypasses to system-level compromise, malicious SQL queries can cause devastation with just a few characters of code. These attacks are cheap, easy to execute, and difficult to detect—making them a favorite weapon in the attacker’s arsenal.
🔐 Actionable Takeaways:
Always use parameterized queries or ORMs
Sanitize and validate all user inputs
Regularly audit your database permissions
Disable features like
xp_cmdshellunless absolutely necessarySimulate attacks in safe environments like TryHackMe or Hack The Box
We opened with a terrifying idea—losing control of your digital identity. Now you know how that nightmare starts.
Further Reading
Subscribe to my newsletter
Read articles from YuvaSec directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

YuvaSec
YuvaSec
Cybersecurity Enthusiast | Ex-Mechanical Engineer | Lifelong Learner Pivoting into InfoSec On a mission to build skills, break stuff (ethically), and land a job in cybersecurity.