SSL-based Security — An Introduction
 NonStop io Technologies
NonStop io Technologies
SSL-based authentication has emerged as the go-to method for server authentication. In the past, there were several different versions of SSL that servers and browsers used. However, as technology evolved, newer TLS algorithms have been developed and are now extensively utilized by servers. SSL-based authentication ensures that your sensitive data remains protected. It’s important to note that while the term “SSL” is often used interchangeably with TLS, only TLS algorithms should be relied upon as SSL algorithms are considered insecure and not suitable for use in applications.
In today’s digital landscape, the need for secure authentication is more crucial than ever. To ensure data privacy and protect sensitive information, protocols such as HTTPS and FTPS must be used. When combined with SSL certificates, these protocols provide an extra layer of security. SSL utilizes a powerful combination of symmetric encryption and asymmetric encryption to safeguard your data from unauthorized access or tampering. Rest assured that your information is well-protected with these cutting-edge technologies in place.
How SSL works
SSL is used to ensure confidentiality and integrity. It can be mainly divided into 3 parts:
Procuring CA-signed certificates
Three-way handshake
Procuring CA-signed certificates
In Secure Socket Layer (SSL), a crucial step involves the server sharing its public key with all the clients, which is essential for verifying the authenticity of the server. To ensure that this public key originates from a legitimate server, it is imperative to take certain precautions. One practical approach is to share the public key separately from other data and securely install it in the client’s browser. By implementing this practice, you can establish a robust and trustworthy connection between servers and clients in an SSL environment.
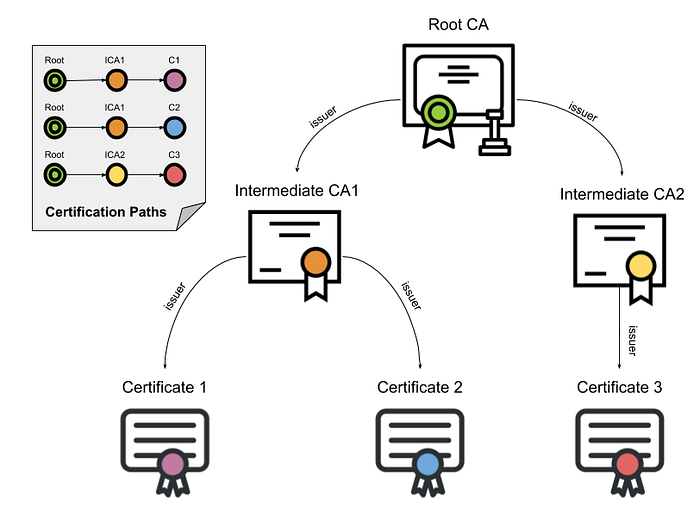
Sharing and updating the public key of every website can be impractical and time-consuming. Instead, a more efficient solution would be for server domains to register themselves and obtain a signed certificate. This way, browsers can already have certificates from Root Authorities pre-installed, making the process smoother and hassle-free for users.
Each root certificate authority authorizes multiple intermediary authorities by signing their public key. These intermediary CAs can then authorize by signing the public key of service providers after domain verification. The signed certificates are then installed on servers and served to the users.
(Image courtesy ssl.com)
It’s crucial to keep in mind that certificates issued by the appropriate authority have an expiration date. This means that server administrators need to be proactive in renewing their certificates before they have expired. By doing so, they can ensure uninterrupted and secure operations on their servers.
Three-way handshake
SSL authentication involves a secure two-step process. Firstly, it entails obtaining signed certificates from trusted authorities, which serves as a crucial validation for your website’s security. Secondly, it includes completing a three-way handshake to establish a secure connection between the client and the server. This comprehensive approach ensures that your online transactions and communications remain confidential and protected from unauthorized access.
Following are the steps(ref):
The client sends a message that lists cryptographic information, such as the TLS version and the CipherSuite supported by the client in their preferred order. The message also includes a random byte string that is used in subsequent computations.
The server responds with a message that includes the CipherSuite chosen by the server, the session ID, and another random byte string. Additionally, the server sends its digital certificate.
Verifying the server’s digital certificate is a crucial step for clients. Without properly signed and installed certificates, this process can fail and compromise the server's security. It is essential to procure and install valid certificates on the server.
The client sends the random byte string that is encrypted with the server’s public key.
If the server sends a “client certificate request”, the client sends a random byte string encrypted with the client’s private key, together with the client’s digital certificate, or a “no digital certificate alert”.
The server verifies the client’s certificate if the client has provided it.
The client sends the server a “finished” message, which is encrypted with the secret key, indicating that the client part of the handshake is complete.
The server sends the client a “finished” message, which is encrypted with the secret key, indicating that the server part of the handshake is complete.
For the duration of the session, the server and client can now exchange messages that are symmetrically encrypted with the shared secret key.

(Image courtesy ibm.com)
Conclusion
A three-way handshake is an authentication mechanism using an asymmetric key. It can be used to authenticate both the server as well as the client. Each SSL public key is required to be shared before the initiation of a three-way handshake. This can happen by installing the public key or the certificates for Root Certificate Authority. Most SSL authentication happens by bundling the Root certificate in the browsers. This SSL-based authentication is most common for authenticating servers.
During this process, there is a new symmetric encryption key shared between clients and servers. This symmetric key will be used to ensure the confidentiality of data sharing in the rest of the session.
Subscribe to my newsletter
Read articles from NonStop io Technologies directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

NonStop io Technologies
NonStop io Technologies
Product Development as an Expertise Since 2015 Founded in August 2015, we are a USA-based Bespoke Engineering Studio providing Product Development as an Expertise. With 80+ satisfied clients worldwide, we serve startups and enterprises across San Francisco, Seattle, New York, London, Pune, Bangalore, Tokyo and other prominent technology hubs.