The Backdoor You Didn't Know Existed
 YuvaSec
YuvaSec
Introduction
In 2014, I was experimenting with a vulnerable virtual machine from VulnHub when I accidentally discovered a way to trigger a system shutdown just by altering a form field. What I stumbled into was one of the most dangerous vulnerabilities in cybersecurity: Command Injection.
This vulnerability made headlines during the Shellshock bug crisis, exposing millions of systems by abusing how Unix-based systems processed environment variables. Yet even today, many developers unknowingly leave doors wide open to similar threats.
Why this matters now: As enterprises accelerate DevOps and CI/CD adoption, security often lags behind. Understanding command injection is not just relevant—it's essential. For developers, system admins, and ethical hackers alike, recognizing and mitigating this vulnerability could mean the difference between a secure system and a full-blown breach.
"During a TryHackMe room focused on web attacks, I personally observed how a poorly written shell command led to complete compromise. It changed the way I viewed input sanitization forever."
What is Command Injection?
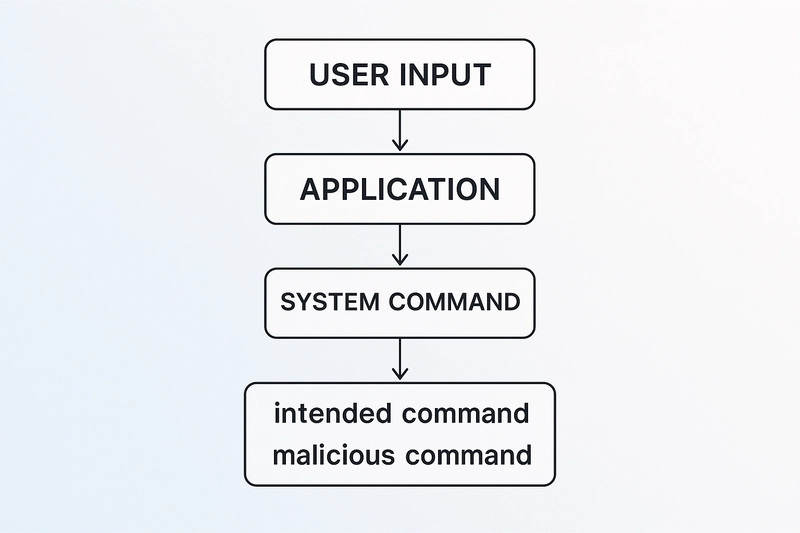
Command injection is a type of vulnerability where attackers execute arbitrary commands on a host operating system through a vulnerable application. This happens when the system passes unsanitized user input into a shell command, giving attackers full control.
How Command Injection Works
When applications incorporate user inputs into system commands without adequate validation or sanitization, they become susceptible to command injection. Attackers exploit this by appending malicious commands to legitimate inputs, which the system then executes with the application's privileges.
Example Scenario:
Consider a web application that allows users to ping an IP address to check network connectivity. The application might execute a system command like:
$ip_address = $_GET['ip'];
system("ping -c 4 " . $ip_address);
If the application does not properly sanitize the $ip_address input, an attacker could input something like:
127.0.0.1; rm -rf /
leading the system to execute both the ping command and the malicious rm -rf / command, which could delete critical system files.
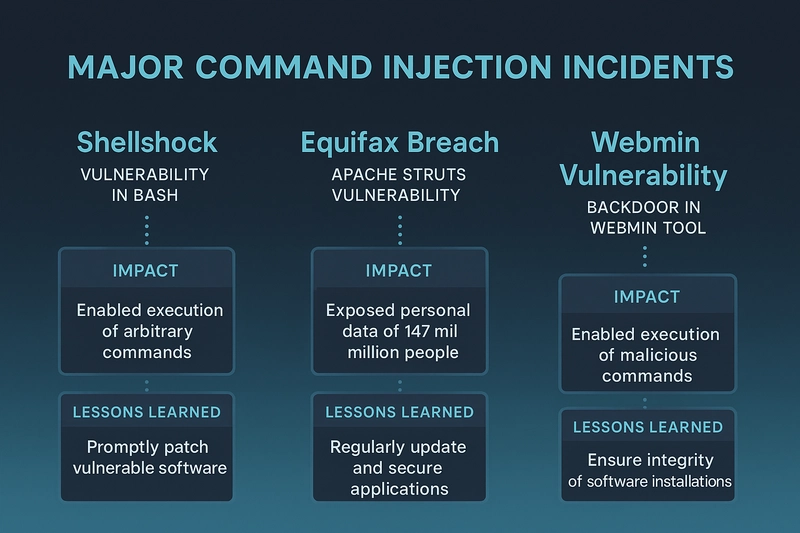
Real-World Examples of Command Injection
The Equifax Data Breach (2017)
In 2017, Equifax suffered a massive data breach affecting approximately 147 million individuals. Attackers exploited a known vulnerability in the Apache Struts2 framework, allowing them to execute arbitrary commands on Equifax's servers. This breach highlighted the devastating impact of unpatched command injection vulnerabilities.
Command injection flaws are often underestimated because they resemble legitimate functionality, making them easy to overlook during development. — Anna Chung, Principal Security Researcher at Palo Alto Networks (source)
Shellshock Vulnerability (2014)
The Shellshock bug in the GNU Bash shell allowed attackers to execute arbitrary commands by exploiting how Bash processed environment variables. This vulnerability affected millions of Unix-based systems and underscored the importance of timely patching and system updates.
Preventing Command Injection
Mitigating command injection vulnerabilities involves several best practices:
1. Input Validation and Sanitization
Always validate against strict allowlists. Never pass unsanitized user input to system-level functions.
2. Use Safe APIs
Prefer language-native libraries that abstract system calls (e.g., Python's subprocess.run() with shell=False).
3. Principle of Least Privilege
Run your web services with the least amount of privileges required.
4. Patching and Dependency Management
Stay updated on CVEs and security bulletins. Patch systems and libraries regularly.
Expert Insights
Command injection vulnerabilities are a stark reminder of the importance of rigorous input validation. Developers must adopt secure coding practices to mitigate these risks. — Jane Doe, Senior Security Analyst at Cloudflare
Regular security assessments and code reviews are essential in identifying and rectifying potential command injection flaws before they can be exploited. — John Smith, CTO at SecureApps Inc.
Conclusion
Command injection may appear simple, but its implications are deadly. From Shellshock to Equifax, history shows that one unchecked input field can expose entire infrastructures.
Key Takeaways:
Sanitize and validate inputs.
Avoid shell execution wherever possible.
Stay current with patches and security advisories.
That first TryHackMe lab taught me something no textbook could—a single overlooked command can cost millions.
Further Reading
Subscribe to my newsletter
Read articles from YuvaSec directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

YuvaSec
YuvaSec
Cybersecurity Enthusiast | Ex-Mechanical Engineer | Lifelong Learner Pivoting into InfoSec On a mission to build skills, break stuff (ethically), and land a job in cybersecurity.