Ransomware Albabat is expanding its attack targets by exploiting GitHub to carry out its campaign.
 Vũ Nhật Lâm
Vũ Nhật Lâm
Overview of Albabat ransomware
The Albabat ransomware was reported to have emerged in late 2023 and early 2024, and its recent version was discovered by the research team at Trendmicro. In versions 2.0.0 and 2.5, the ransomware not only targets computers running the Windows operating system but also collects information on machines running Linux and macOS. Last January, after detecting signs of Albabat ransomware on a computer screen mentioning Linux, Fortinet warned that this ransomware could operate on multiple operating systems.

Analysis of ransomware behavior
In the latest version, this malware retrieves configuration information through the GitHub REST API using a user-agent named "Awesome App." The retrieved configuration includes the malware's behavior settings and execution parameters.
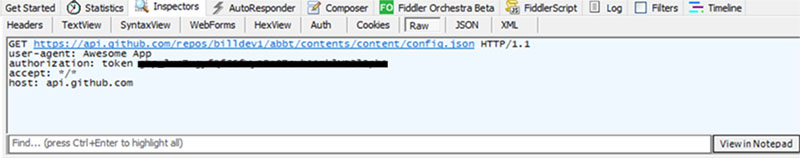
Analyzing the configuration information, researchers found that:
The malware will skip certain folders: Searches, AppData, $RECYCLE.BIN, System Volume Information, windows.old, steamapps, perflogs, ansel, tmp, node_modules, cache, vendor, target, Mozilla, venv, env, Chrome, google-chrome, pypoetry, vimfiles, viminfo, site-packages, scoop, go, and temp.
It encrypts files with the following extensions: ~$, .src, .ico, .cur, .theme, .themepack, .bat, .com, .cmd, .cpl, .prf, .icls, .idx, .mod, .pyd, .vhdx, ._pth, .hta, .mp3, .CHK, .pickle, .pif, .url, .ogg, .tmp, .dat, .exe, .lnk, .win, .vscdb, .bin, .cab, .inf, .lib, .tcl, .cat, .so, .msi, .vpk, .vc, .cur, .ini, .bik, .sfx, .xnb, .ttf, .otf, .woff, .woff2, .vfont, .resource, .N2PK, .log, .pkg, .desktop, .dll, .pkr, .arc, .sig, .bk2, .arz, .swf, .qt, .wma, .mp2, .vdf, .pdb, .nfo, .whl, .mui, .srm, .smc, .dic, .lock, .pyc, .TAG, .locale, .store, .sdi, .library-ms, .acf, .po, and .mo.
Additionally, it will stop the following processes: askmgr.exe, processhacker.exe, regedit.exe, code.exe, excel.exe, powerpnt.exe, winword.exe, msaccess.exe, mspub.exe, msedge.exe, virtualboxvm.exe, virtualbox.exe, chrome.exe, cs2.exe, steam.exe, postgres.exe, mysqlworkbench.exe, outlook.exe, mysqld.exe, windowsterminal.exe, powershell.exe, cmd.exe, sublime_text.exe, microsoft.photos.exe, and photosapp.exe.
After gathering information on the victim's machine, the malware will connect to the PostgreSQL database.
postgres://postgres.<username>:<password>@aws-0-us-west-1.pooler.supabase[.]com:5432/postgres
The use of the database is intended to track infections and transactions. The information obtained helps attackers make ransom demands and sell the victim's data.
Additionally, the setup information includes some commands for computers running Linux and macOS, indicating that the malware is designed to target these operating systems.
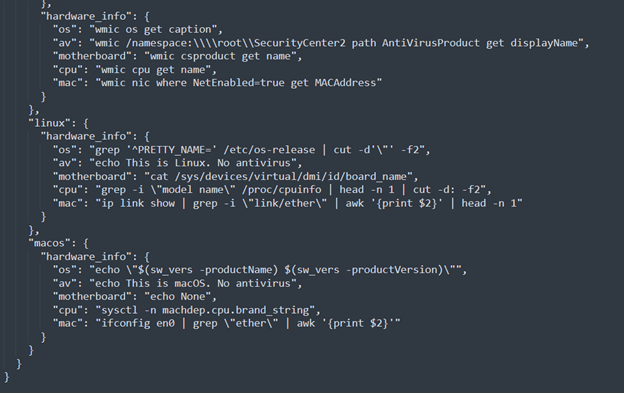
Related to GitHub
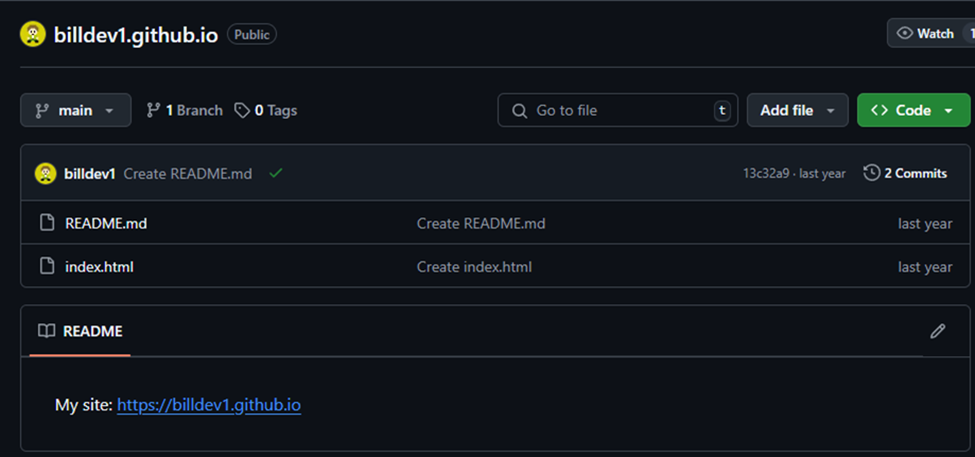
The malware setup information is stored in a GitHub repository at billdev.github.io and is set to private, but it can still be accessed using an authentication token obtained in Fiddler. Further investigation into the GitHub account revealed that it was created on 02/27/2024 and registered under the name Bill Borguiann. The commit history shows the most recent commit was on 02/22/2025, and the email used was billdev@morke[.]org.

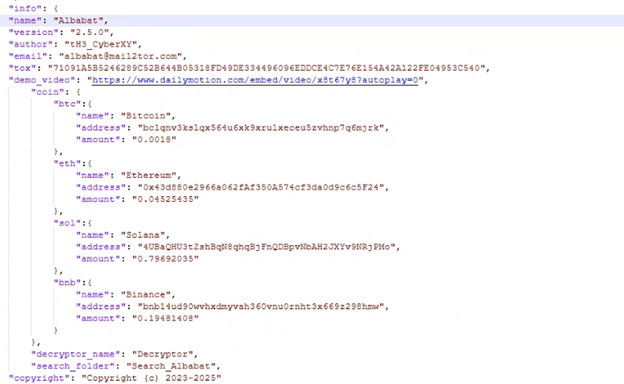
Additionally, a folder named 2.5.x was discovered, suggesting that a newer version of the Albabat malware may be in development. This folder contains a config.json file, which includes cryptocurrency wallet information for Bitcoin, Ethereum, Solana, and BNB.
Recommendations
To promptly detect, prevent, and take precautionary measures, FPT Threat Intelligence offers the following recommendations:
Regularly back up important data and check backup processes to ensure quick recovery if an incident occurs.
Segment the network to minimize the spread of malware within the organization. Sensitive data and critical systems can be isolated in a separate area.
Regularly update and patch vulnerabilities, as this is crucial to prevent attackers from exploiting them to deploy malware.
Conduct awareness training for employees and users to avoid phishing, strange links, as well as malicious and cracked software.
Update the IOC of the malware to quickly detect and prevent it.
IOC
| SHA1 | Detection |
| 1cc2d1f2a991c19b7e633a92b1629641c019cdeb | Ransom.Win64.ALBABAT.THBBEBE |
| c7c52fdaecf325dfaf6eda14e0603579feaed40a | Ransom.Win64.ALBABAT.THBBEBE |
| 8a3ea65147a156d381d8f1773e91eb8e0f6b1e40 | Ransom.Win64.ALBABAT.THBBEBE |
| 8de54cad9d6316679580c91117b484acb493ab72 | Ransom.Win64.ALBABAT.THBBEBE |
| d67dc8c4232a3943a66608d62874923e9a3fb628 | Ransom.Win64.ALBABAT.THBBEBE |
Reference
Albabat Ransomware Expands Targets, Abuses GitHub - SecurityWeek
Subscribe to my newsletter
Read articles from Vũ Nhật Lâm directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
