🛡️ A Comprehensive Guide to OAuth2 and JWT Authentication for Modern Web Apps
 Dipman Majumdar
Dipman MajumdarTable of contents
- 🚀 What is Authentication and Authorization?
- 🚀 Why Modern Apps Need Better Authentication?
- 🔐 What is OAuth2?
- ⚡OAuth 2.0 Roles
- 🔁 OAuth2 Flow (Authorization Code Grant)
- ⚡OAuth 2.0 Grant Types
- 🧾 Understanding JWT (JSON Web Tokens)
- 🧩 JWT Structure
- 💡 How JWT Works?
- 🔗 How OAuth2 and JWT Work Together?
- ✅ Why JWTs Are Useful:
- ⚡OAuth 2.0 vs JWT
- 🛠️ Example Use Case: Logging in with Google (OAuth2 + JWT)
- 🔐Security Considerations
- 🧰 Tools & Libraries
- 📦 Sample JWT (Decoded)
- 🧭 When to Use What
- 🧠 Final Thoughts
- 🔭 Conclusion

Authentication and authorization are critical components of modern web applications. As applications grow in complexity, ensuring secure and scalable user authentication becomes essential. Two widely adopted technologies for handling authentication and authorization are OAuth 2.0 and JSON Web Tokens (JWT).
This article provides a deep dive into OAuth 2.0 and JWT, explaining how they work, their differences, and how they are used together in modern web applications.
🚀 What is Authentication and Authorization?
Before diving into OAuth 2.0 and JWT, it's essential to understand the difference between authentication and authorization:
Authentication (AuthN): Verifying a user's identity (e.g., username/password, biometrics).
Authorization (AuthZ): Determining what permissions an authenticated user has (e.g., read/write access).
OAuth 2.0 is primarily an authorization framework, while JWT is a token format often used for authentication.

🚀 Why Modern Apps Need Better Authentication?
Traditional login methods rely on sessions and cookies. While effective for monolithic apps, these methods struggle in distributed, API-driven, and mobile-first environments. That’s where token-based authentication using OAuth2 and JWTs shines.
🔐 What is OAuth2?
OAuth 2.0 is an authorization framework that allows third-party applications to access user data without exposing credentials. It is widely used by platforms like Google, Facebook, and GitHub for delegated access.
⚡OAuth 2.0 Roles
Resource Owner (User): The entity granting access (e.g., a user allowing an app to access their Google Drive).
Client (Application): The app requesting access (e.g., a web or mobile app).
Authorization Server: Issues access tokens after authenticating the user (e.g., Google’s OAuth server).
Resource Server: Hosts protected resources (e.g., Google Drive API).
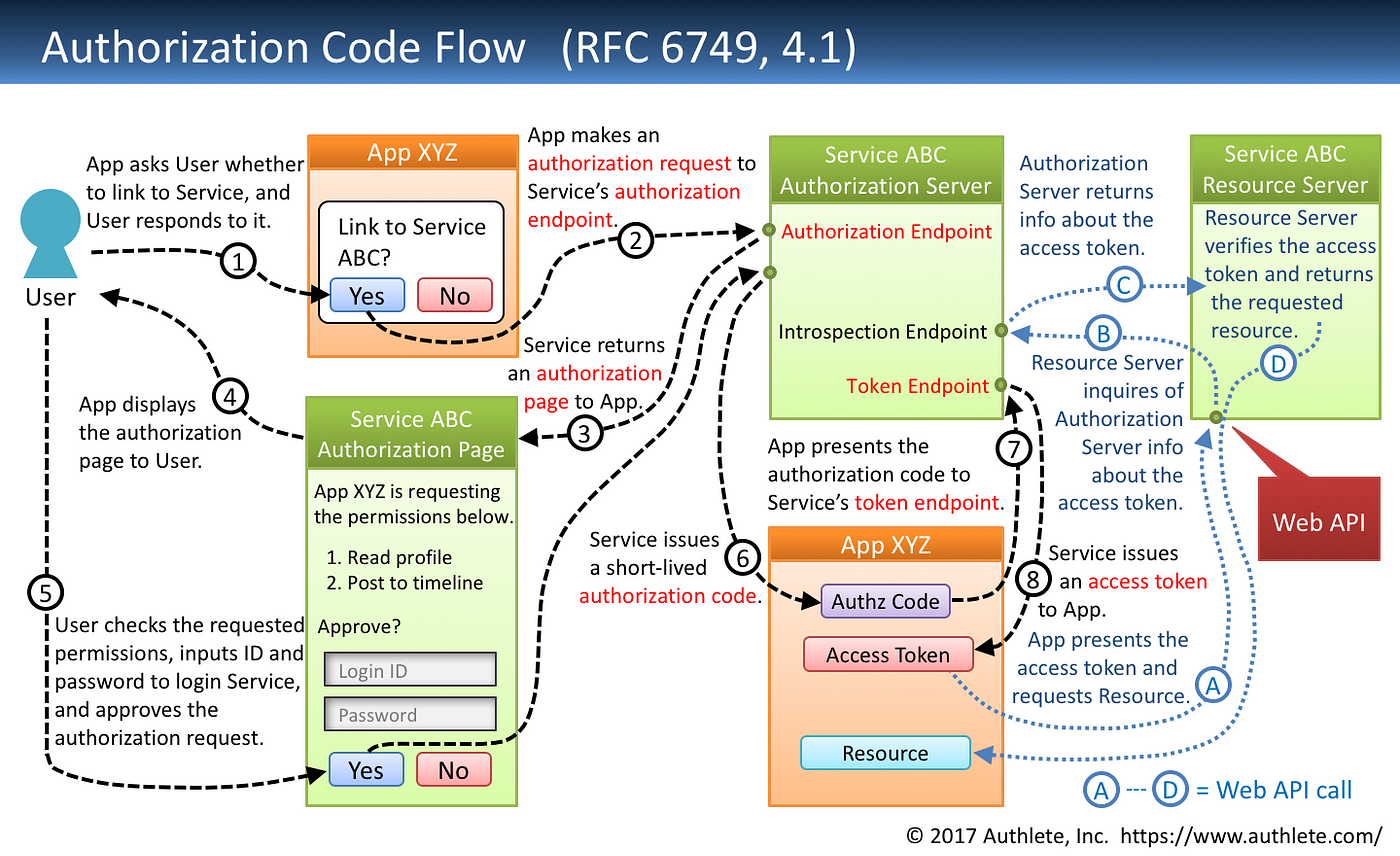
🔁 OAuth2 Flow (Authorization Code Grant)
User logs in to the authorization server.
Server sends back an authorization code.
The client app exchanges the code for an access token.
The access token is used to request data from APIs (resource servers).
⚡OAuth 2.0 Grant Types
OAuth 2.0 supports multiple grant types depending on the use case:
Authorization Code Grant (Most secure for web apps)
Used by server-side apps.
Involves an authorization code exchanged for a token.
Prevents exposure of tokens to the browser.
Implicit Grant (Legacy, less secure)
Used by single-page apps (SPAs).
Returns tokens directly in the URL (less secure).
Client Credentials Grant (Machine-to-machine)
- Used for server-to-server communication (no user involved).
Password Grant (Not recommended)
- Requires direct username/password (risky).
Refresh Token Grant
- Used to obtain new access tokens without re-authentication.
🧾 Understanding JWT (JSON Web Tokens)
JWT is a compact, URL-safe token format used for securely transmitting claims between parties. Unlike traditional session-based authentication, JWTs are stateless and contain all necessary user data within the token itself.
🧩 JWT Structure
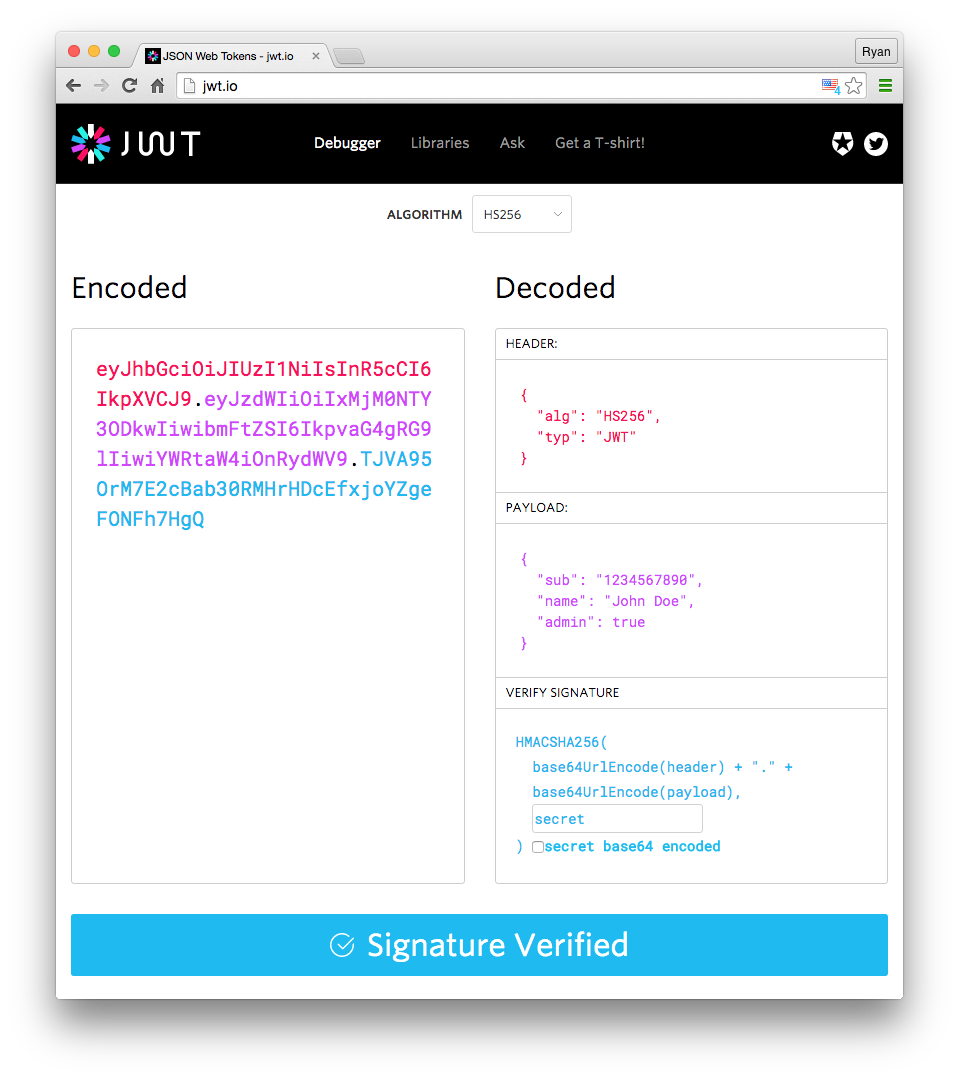
A JWT consists of three parts:
Header (Algorithm & token type)
{ "alg": "HS256", "typ": "JWT" }Payload (Claims - user data)
{ "sub": "1234567890", "name": "John Doe", "iat": 1516239022 }Signature (Verifies token integrity)
- Created using the header, payload, and a secret key.
A JWT looks like this:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
You can play with JWTs here: https://jwt.io
💡 How JWT Works?
User logs in → Server generates a JWT.
Client stores JWT (usually in
localStorageor cookies).Subsequent requests include the JWT in the
Authorizationheader.Server validates JWT (checks signature & expiry).
Since JWTs are self-contained, they reduce database lookups compared to session tokens.
🔗 How OAuth2 and JWT Work Together?
OAuth2 can use JWTs as access tokens. When a client app receives an access token from the authorization server, it could be a JWT.
Many modern apps combine OAuth 2.0 for authorization and JWT for authentication:
User logs in via OAuth 2.0 (e.g., "Sign in with Google").
Authorization server issues a JWT (instead of an opaque token).
Client uses JWT for API requests (stateless validation).
This approach provides:
✅ Scalability (no session storage needed).
✅ Security (short-lived JWTs + OAuth scopes).
✅ Interoperability (JWTs work across services).
✅ Why JWTs Are Useful:
Stateless: No need to store session on the server.
Secure: Can be signed and optionally encrypted.
Portable: Easy to use in headers (
Authorization: Bearer <token>).
⚡OAuth 2.0 vs JWT
| Feature | OAuth 2.0 | JWT |
| Purpose | Authorization framework | Token format for authentication |
| Usage | Delegated access (e.g., Google) | Secure stateless authentication |
| Token Type | Access tokens, refresh tokens | Self-contained signed tokens |
| Flow | Requires multiple steps (grants) | Simple token issuance & validation |
| State | Can be stateful (depends on impl.) | Stateless |
🛠️ Example Use Case: Logging in with Google (OAuth2 + JWT)
User clicks “Login with Google”.
Redirected to Google’s OAuth2 authorization server.
User consents and is redirected back with an authorization code.
Your app exchanges the code for a JWT access token.
The token is sent to your backend for secure access to APIs.
🔐Security Considerations
While OAuth 2.0 and JWT are powerful, they require proper implementation:
⚡ OAuth 2.0 Security Best Practices
Use PKCE (Proof Key for Code Exchange) for public clients.
Avoid the Implicit Grant (use Authorization Code + PKCE instead).
Validate redirect URIs to prevent phishing.
⚡ JWT Security Best Practices
Use strong algorithms (e.g.,
RS256overHS256).Set short expiration times (use refresh tokens).
Store JWTs securely (HttpOnly cookies for web apps).
Avoid storing sensitive data in JWTs (they are base64-encoded, not encrypted).
🧰 Tools & Libraries
OAuth2 Providers: Google, GitHub, Facebook, Auth0, Okta
Libraries:
Node.js:
passport.js,jsonwebtoken,oauth2orizeFrontend:
oidc-client,react-oauth/googlePython:
authlib,pyjwt
📦 Sample JWT (Decoded)
Header:
jsonCopyEdit{
"alg": "HS256",
"typ": "JWT"
}
Payload:
jsonCopyEdit{
"user_id": "abc123",
"role": "admin",
"exp": 1715093800
}
JWT looks like this:
CopyEditeyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...
🧭 When to Use What
| Use Case | Recommended Strategy |
| Third-party login (e.g. Google) | OAuth2 |
| API authentication | JWT |
| Stateless mobile app auth | OAuth2 + JWT |
| Enterprise SSO | OpenID Connect (on top of OAuth2) |
🧠 Final Thoughts
OAuth2 and JWT are cornerstones of modern authentication and authorization. Together, they allow developers to build secure, scalable, and user-friendly systems — especially for SPAs, APIs, and mobile apps.
Take the time to understand the flow, and implement proper security practices — because authentication is often your first line of defense.
🔭 Conclusion
OAuth 2.0 and JWT are foundational technologies for modern authentication and authorization:
OAuth 2.0 enables secure delegated access (e.g., third-party logins).
JWT provides a stateless, scalable way to handle authentication.
By combining them, developers can build secure, scalable, and user-friendly authentication systems.
📚 Useful References
Subscribe to my newsletter
Read articles from Dipman Majumdar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by