Azure Traffic Manager
 Pratul
Pratul
Prerequisites:
This blog is intended for readers who are familiar with Azure and its services.
I started my project by implementation of VPN among VNET so that seamless communication is established among resources within Subnets of respective VNETS.

AIM
Implementation of second load balancing solution named Azure Traffic Manager within my Azure Model Plan. Therefore, I created two Azure Web Apps in two different Azure Service Plans within two different regions.
My objective is to manage network traffic among these two Web Apps present in respective regions by the use of Traffic Manager profile. In short, configuring a network load balancing which mimics the concept of app service failover. I used endpoints of Traffic Manager to among primary web apps & failover web apps.
Most importantly, I used Priority as Routing Method for now & for continuity's sake I integrated this activity with my project.
NOTE: Currently, I am using these configurations for testing purpose. Later I will be changing based on the requirement of my project.
MY LAB
I started with creation of Azure Traffic Manager by entering the following details following my lab naming conventions,


| Setting | Value |
| Name | Enter a unique name for your Traffic Manager profile. (mrt-xxx-xx) |
| Routing method | Select Priority. |
| Subscription | Select the subscription you want the traffic manager profile applied to. |
| Resource group | Select <myResourceGroup>. |
| Location | This setting refers to the location of the resource group. It has no effect on the Traffic Manager profile that will be deployed globally. |
Note: The following traffic routing methods are available in Traffic Manager:
Priority: Select Priority routing when you want to have a primary service endpoint for all traffic. You can provide multiple backup endpoints in case the primary or one of the backup endpoints is unavailable.
Weighted: Select Weighted routing when you want to distribute traffic across a set of endpoints based on their weight. Set the weight the same to distribute evenly across all endpoints.
Performance: Select Performance routing when you have endpoints in different geographic locations and you want end users to use the "closest" endpoint for the lowest network latency.
Geographic: Select Geographic routing to direct users to specific endpoints (Azure, External, or Nested) based on where their DNS queries originate from geographically. With this routing method, it enables you to be in compliance with scenarios such as data sovereignty mandates, localization of content & user experience and measuring traffic from different regions.
Multivalve: Select Multivalve for Traffic Manager profiles that can only have IPv4/IPv6 addresses as endpoints. When a query is received for this profile, all healthy endpoints are returned.
Subnet: Select Subnet traffic-routing method to map sets of end-user IP address ranges to a specific endpoint. When a request is received, the endpoint returned will be the one mapped for that request’s source IP address.
Finally, we use the DNS name of Traffic Manager Profile to access the sites which consists of same site as configured in every
Next, I configured two Azure App Services with its respective App Service Plan deployed in different regions - East Asia & Japan East respectively.
App Services Configurations for app services present in East Asia & Japan East:
| Setting | Value |
| Subscription | Select your subscription. |
| Resource group | Select Create new/All created RG |
| Name | Enter a unique Name for your web app. |
| Publish | Select Code. |
| Runtime stack | Select .NET V8.0. |
| Operating System | Select Windows. |
| Region | Select <region>. |
| Windows Plan/App Service Plan | Select Create new and enter <app service plan> in the text box. |
| Sku and size | Select Standard S1 100 total ACU, 1.75-GB memory. |
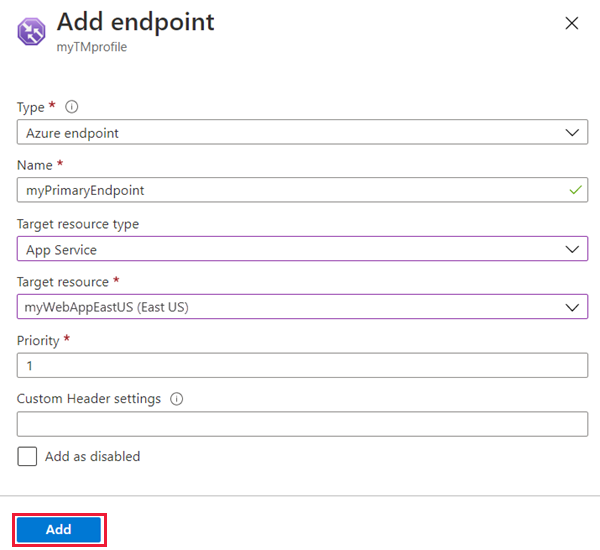
Once Respective App Services are configured based on the above Azure Plan Chart. I had setup the Endpoints in Azure Traffic Manager profile by configuring with Azure App Services respectively. One is set as “TMprimaryEndpoint“ with an App Service & other “TMfailoverEndpoint“ with another app service with below configurations:
| Setting | Value |
| Type | Select Azure endpoint. |
| Name | Enter myPrimaryEndpoint. |
| Target resource type | Select App Service. |
| Target resource | Select Choose an app service > East US. |
| Priority | Select 1. All traffic goes to this endpoint when it's healthy. |
Challenges:
After configuring and enabling Endpoints. I was facing issues at Monitor status showing as “Degraded“(which needs to be ONLINE).

On diagnosis (investing over internet), I used the command below on Azure CloudShell, to check the status that was being returned from my app service (this is because Traffic Manager execute some health probes checks to validate the endpoints), and I noticed that when I was using HTTP was returning 301 (Moved permanently), but when using HTTPS it was returning 200.
Invoke-WebRequest 'http://appservice-demo-1.azurewebsites.net' -MaximumRedirection 0 -ErrorAction SilentlyContinue | Select-Object StatusCode,StatusDescription
Invoke-WebRequest 'https://appservice-demo-1.azurewebsites.net' -MaximumRedirection 0 -ErrorAction SilentlyContinue | Select-Object StatusCode,StatusDescription


HTTPS might be the cause for the Monitor status “Degraded”.
Therefore, I configured HTTPS for endpoints.
To configure HTTPS, in the Traffic Manager profile, go to the Configuration page and update the Protocol to HTTPS and the Port to 443:

After few minutes (around 10-15 mins), they will be with the status “Online”.

App Service Site Configuration
I wanted to test out the webapp failover thing, for that I had to differentiate the web apps for which I relied on App Service Editor to configure the site page as below:

For webApp1
<html>
<body>
<h1>This is the Primary web Application</h1>
</body>
</html>
For webApp2:
<html>
<body>
<h1>This is the failover web Application</h1>
</body>
</html>
Once web sites are configured, with Azure Traffic Endpoints successfully in place with respective web apps. We test the failover using DNS of Traffic Manager which is created by default as below:
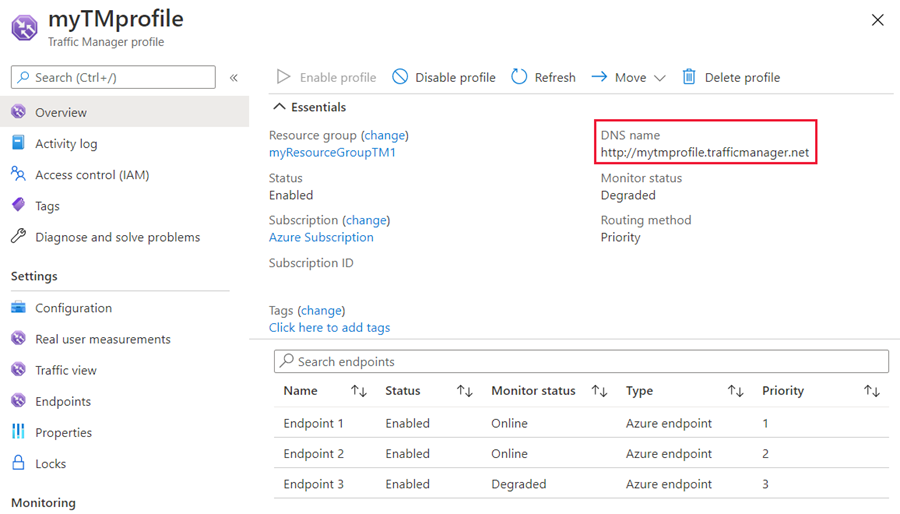
RESULTS

To Test Failover: Got below Web page for second Azure Web App once the Primary Endpoint of Traffic Manager is disabled or the First Web App is stopped.

Challenges:
I was receiving this page while accessing Traffic Manager DNS for which endpoints were setup with necessary web apps.

NOTE: I was accessing this site without configuring the web page of web apps (which is essential).
Therefore, I relied on App Service Editor feature present in Azure Web App to configure basic level website as discussed over App Service Site Configuration. Once configured I got my desired output.
REFERENCES
Subscribe to my newsletter
Read articles from Pratul directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pratul
Pratul
A passionate L1 Server Engineer with a growing focus on DevOps practices. With experience in server administration, troubleshooting and infrastructure management, I am skilled at optimizing workflows through automation and CI/CD pipelines. Currently working with cloud platforms like AWS & Azure, virtualization technologies, and configuration management tools. Committed to enhancing efficiency and productivity. Through this blog, I will be sharing hands-on insights, tutorials, and practical tips aimed at helping fellow professionals in server engineering and DevOps.