Dangerous phishing campaign exploits Google OAuth and DKIM replay to spoof emails from Google
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
Recently, FPT Threat Intelligence has recorded a sophisticated phishing campaign carried out by hackers on a large scale. The attackers exploit Google OAuth and the DomainKeys Identified Mail (DKIM) mechanism to send fake emails with valid signatures from Google. This attack is called a DKIM replay attack—a technique where the attacker reuses an email already authenticated by Google's signature to redistribute it with fraudulent content.
DKIM (DomainKeys Identified Mail) is an email authentication method that helps recipients verify that the email was actually sent from the sender's domain and that the email content was not altered during transmission. In other words, DKIM helps prevent email spoofing by using digital signatures.
The danger here is that recipients will see the DKIM-signed email as valid and coming from the google.com domain, making them more likely to trust and follow the requests in the email—such as logging into a fake page, granting OAuth permissions to a malicious app, or disclosing personal information.
Campaign Details
Initially, the attackers create a new Google account and an OAuth app that resembles a phishing email.
Next, the hackers grant permissions to the app, and Google sends a warning email to that same account. This email has a valid DKIM signature issued by Google, which allows it to easily bypass filters.
- Email phishing is sent from the address: “no-reply@google.com” and there are no warnings from Gmail. The email content states that their Google account is under investigation by law enforcement and asks them to click a link on Google Sites to "view case details" or "submit an appeal."
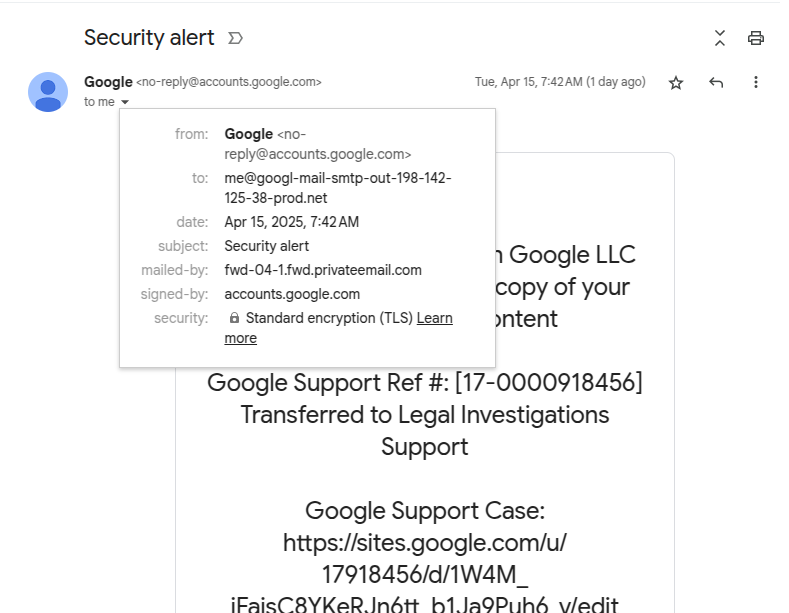
- When clicking the link, the victim's browser is redirected to a fake Google Support page designed to look very real. This page has buttons to "download documents" or "view case file," and both buttons lead to a fake Google login page named “sites.google.com“.

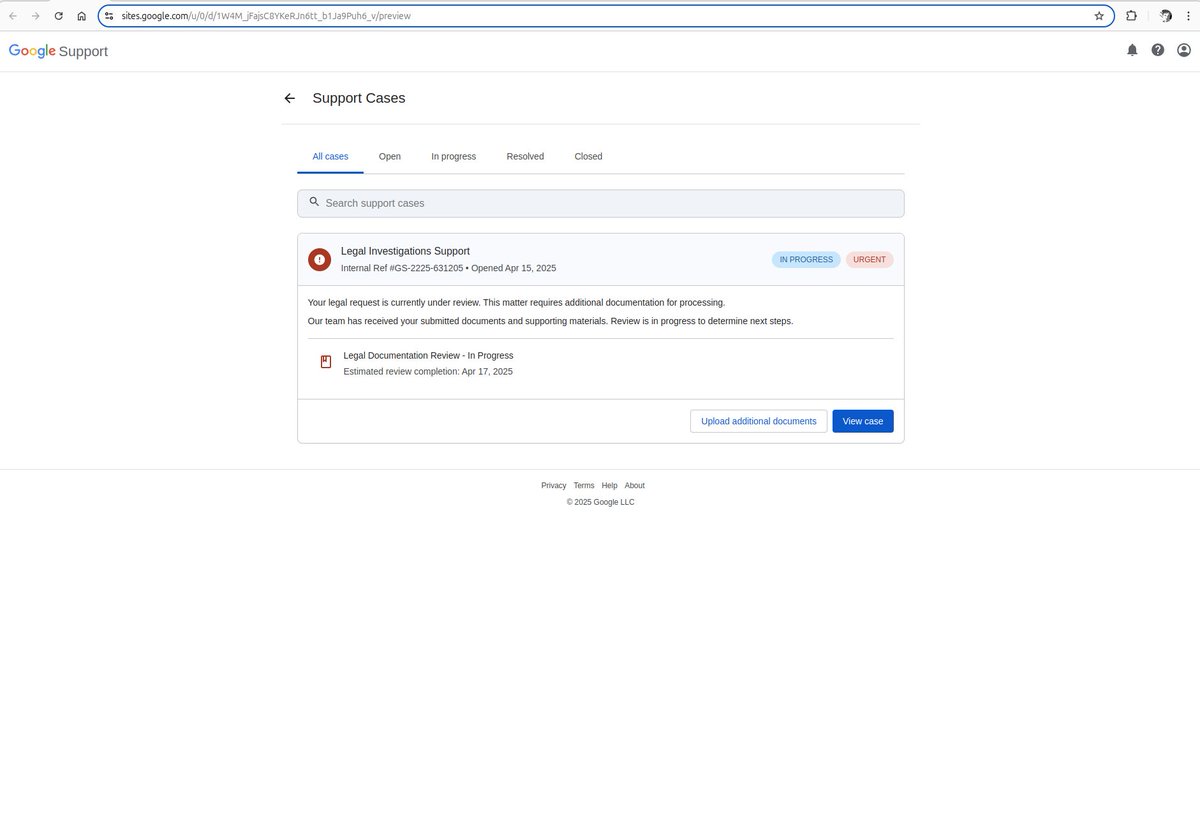
Once users enter their account and password, all login information is collected by the hackers. Notably, the entire email passes all security checks like DKIM, SPF, and DMARC, which are usually used to identify fake emails.
Additionally, according to the latest cybersecurity news gathered by FPT Threat Intelligence, a similar campaign is being exploited by hackers targeting PayPal to steal users' payment information.
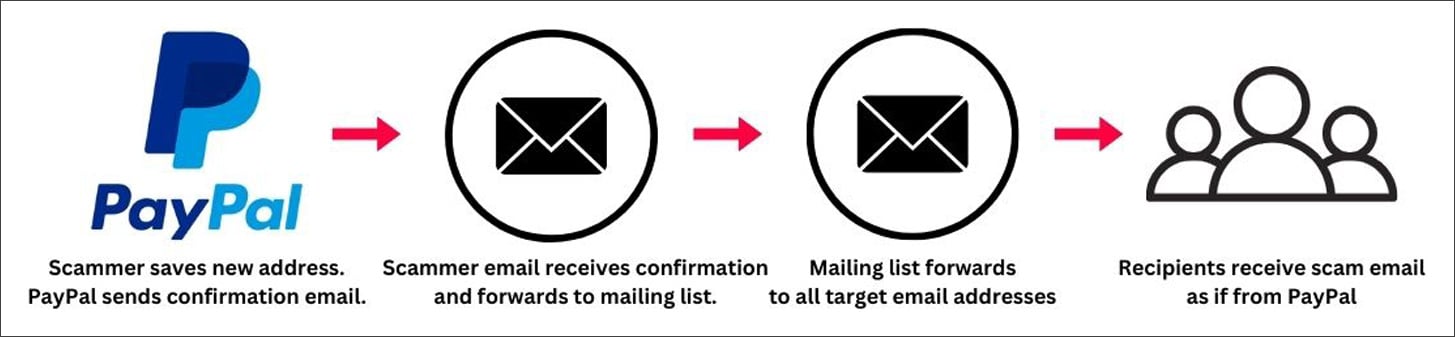
- In that case, the attacker used the gift address feature on the network to add emails and paste phishing content into PayPal's existing email templates. The created email also passed the DKIM checks, making it appear trustworthy. This tricked victims and stole their information.
Recommendation
- Apply advanced security controls in the email system
Implement strict DMARC policies (reject/quarantine), combined with DKIM and SPF to verify email validity.
Limit the replay count from the same DKIM signature (if the email service provider allows).
Monitor unusual indicators in DKIM signatures such as: too many identical emails sent from different IP addresses using the same DKIM signature.
- Train awareness and increase vigilance
Warn employees/users about fake OAuth tricks impersonating Google (e.g., clicking "Sign in with Google" on unfamiliar sites or granting unclear permissions to apps).
Train skills to check:
The real URL of the login page.
Suspicious email content.
The list of permissions that an app requests in OAuth.
- Monitor and check OAuth tokens
Use Google Admin Console (for G Suite) to track:
Which third-party apps are granted access.
Which tokens are being used.
Revoke access immediately if suspicious access is detected.
Conclusion
This attack shows that even strong authentication standards like DKIM can be exploited if not combined with additional checks like validity period or email sending context. Raising user awareness and applying strict authentication policies are key to minimizing risk.
Additionally, many other phishing campaigns are using SVG files containing malicious code to redirect users to fake Microsoft or Google Voice pages. According to information gathered from FPT Threat Intelligence, more than 4,100 such emails were detected in just the first few months of 2025.
IOC
Reference
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
