Trials by Fire: The Security Saga of Solana’s Blockchain
 Abraham Dahunsi
Abraham Dahunsi
Introduction
How secure is a blockchain that runs at web-speed? When Solana launched, it promised blazing transaction throughput and an experience to rival the traditional web. Yet from $321 million bridge heists to sudden network halts, Solana’s journey has been a gauntlet of security trials. In early 2022, an attacker minted 120,000 fake ETH on Solana and siphoned out a fortune.
Months later, a trader manipulated a token’s price to drain over $116 million from a Solana exchange. And on more than one occasion, a surge of traffic or a subtle bug brought the entire network to a standstill.

Why did these incidents happen, and what do they reveal about the hidden costs of pushing blockchain performance to its limits? This article dives deep into the history of security incidents on Solana, unpacking how innovation clashed with vulnerability. We’ll explore the full spectrum – from smart contract exploits and supply-chain attacks to consensus bugs, spam floods, governance dramas, validator mishaps, and social engineering scams. Along the way, we’ll identify recurring patterns and hard-learned lessons, aided by data visualizations and case studies. Finally, we look ahead: How is Solana hardening its defenses as it matures, and what proactive steps can ensure its ambitious blockchain stays secure?
Solana’s rise from a high-speed experiment to one of crypto’s most active Layer-1 networks has been anything but dull. Its security history is a saga of triumphs and setbacks – a story of speed versus safety. Let’s begin by understanding the broader landscape of blockchain vulnerabilities before zeroing in on Solana’s unique challenges.
The Anatomy of Blockchain Vulnerabilities
At first glance, blockchains appear nearly impregnable – secured by cryptography and decentralized consensus. Indeed, core cryptographic primitives (like digital signatures and hashes) have held strong. Yet, most blockchain breaches exploit something far less fundamental. They target the software, economics, or people around the blockchain, rather than breaking the math at its core. What are the main fronts in this battle?
Smart contracts form the application layer of blockchains, and they’re frequent targets. These programs manage funds and assets with absolute authority – a single bug can be catastrophic. For example, an attacker might find a flaw that lets them mint tokens without collateral or drain a contract’s funds. Such logic errors and unchecked assumptions have led to billions in losses across all chains. The allure of decentralized finance (DeFi) turned blockchain apps into a hacker’s playground, where one line of buggy code can equate to a bank vault left open.
Then there’s the network and consensus layer – the protocols that keep the blockchain running and in agreement. While rarer, failures here can be dramatic. A glitch in consensus code can cause network validators to crash or fall out of sync, effectively halting the blockchain. Unlike traditional systems, a public blockchain can’t be simply “rebooted” by an admin flip of a switch; coordinating a recovery is an arduous process involving thousands of independent nodes. Liveness (uptime) can sometimes conflict with safety (consistency of the ledger) in these systems. How do you upgrade an engine that’s running at full speed? A single obscure bug in an edge-case can stall a global network – as Solana painfully discovered.

Another attack surface lies in the supply chain – the ecosystem of software that developers and users rely on. If hackers can compromise a popular wallet app, library, or update server, they can smuggle malicious code to thousands of users in one stroke. This is exactly what happened when Solana’s widely used JavaScript library, @solana/web3.js, was hijacked in late 2024: two backdoored versions were briefly published, poised to steal private keys from any app that installed them (Solana Web3.js Library Backdoored in Supply Chain Attack - SecurityWeek). No cryptography was broken; instead, the trust in software distribution was exploited.
Even if the software is airtight, the human element remains. Social engineering and phishing attacks prey on people’s mistakes. In one infamous incident, an attacker breached an NFT project’s Discord server and posted a fake mint link. Eager fans who clicked had their wallets drained of SOL – totaling about $1.3 million stolen.

The hacker didn’t need to touch the blockchain’s code at all; they simply tricked users into handing over the keys to their own castle. This underscores a sobering truth: a blockchain can be secure by design, yet still suffer breaches if its users and developers are duped.
Finally, there are governance and administrative keys. Many blockchain projects have upgrade authorities or DAO governance tokens that control critical parameters. If those are mismanaged or exploited, an attacker could seize control without writing a line of code. We’ve seen this in other ecosystems (like an infamous attack where a hacker used a flash loan to gain voting power and empty a DeFi treasury). Solana’s community has so far avoided a direct governance takeover attack, but it’s not because the risk isn’t there – indeed, the Mango Markets saga in 2022 showed how blurring the line between attacker and voter can create chaos, as we’ll discuss.
In summary, blockchain security is multi-layered. We have to consider application-level bugs, protocol-level flaws, supply chain risks, human factors, and governance controls. With this framework in mind, we can better appreciate how Solana’s particular design and journey made it both resilient in some ways and fragile in others. Every blockchain faces these categories of risk; what makes Solana’s story unique is how its quest for high-speed, high-capacity performance introduced new twists on these age-old problems.
Speed vs. Safety: Solana’s Design Trade-offs
Solana was born to break barriers. Branded as one of the fastest blockchains, it introduced novel approaches like Proof of History (PoH) – a cryptographic clock that helps order transactions – and a parallel processing engine (Sealevel) that can execute thousands of contracts concurrently.
These innovations give Solana its throughput edge. But they also mean Solana’s software stack is complex, and complex systems inevitably hide unexpected bugs. What happens when you push a Ferrari engine to its limits without enough road testing? You get blazing laps… until something blows. Solana’s early years were akin to stress-testing a race car in real time, on the track with millions of dollars at stake.
A crucial aspect of Solana is its extremely low fees and high capacity, which in 2021–2022 had no built-in fee market for congestion. This was by design: keep fees cheap for users. The downside? It was cheap for attackers (or overzealous bots) to flood the network with traffic. In Ethereum, a sudden rush of demand simply drives fees sky-high, pricing out many transactions; painful for users, but the chain keeps chugging. On Solana, by contrast, sudden overload could clog the pipes so badly that the network would stall entirely – a much more acute failure mode. Solana’s engineers eventually introduced quality-of-service improvements (like fee prioritization for critical packets and stake-weighted QoS) to mitigate this, but those came after early incidents taught hard lessons.
Another trade-off was Solana’s choice to prioritize consistency over availability. In distributed systems theory (CAP theorem), Solana leaned toward safety – it would rather halt than produce an inconsistent ledger. So, if validators ever got wildly out of sync or hit an error, they’d stop advancing until humans could intervene. This is arguably the right call for a financial network (nobody wants an inconsistent double-spend scenario), but it meant Solana could “go dark” in ways users of Bitcoin or Ethereum never experienced. Each such halt required a coordinated restart by the validator community, a process that, while impressively orchestrated at times, drew criticism about centralization and reliability.
Solana’s rapid growth also meant immature infrastructure was sometimes strained. In 2021, the network went from handling a few thousand transactions per second to peaks of hundreds of thousands.

Software like rpc nodes (which applications use to submit transactions) buckled under duress, and retry mechanisms that were meant to be helpful actually exacerbated floods by re-submitting tons of duplicate transactions. The project was effectively scaling up in production, like trying to expand a highway during rush hour.
Moreover, Solana’s youth meant many developers were writing on it for the first time. While Ethereum had years of battle-tested tooling and patterns for secure smart contracts, Solana’s equivalent (the Anchor framework, Rust-based programs) was new territory. Early DeFi projects on Solana sometimes repeated mistakes their Ethereum counterparts had made – or made entirely new ones thanks to Solana’s parallel execution model. One misconfigured assumption in a Solana program could allow a rogue user to, say, bypass an authority check or overflow a number, with devastating effect.
Yet, it’s not all dark. Solana’s saving grace in many incidents has been a strong core team and community of contributors that reacted quickly. For instance, when a critical vulnerability was discovered in 2022, Solana’s developers quietly coordinated with validators to patch it before any exploit occurred. And when the worst did happen (like the Wormhole hack), ecosystem players stepped up – Jump Crypto famously replaced the stolen Ether with their own funds to make users whole, a bold vote of confidence in Solana.
In summary, Solana’s design choices – a single global state machine processing tens of thousands of events per second, with minimal fees – gave it a unique security profile. It invited new kinds of stresses (like massive bot swarms) and exposed novel bugs (like the “durable nonce” issue we’ll detail). The network’s philosophy of fast iteration meant some features rolled out with less seasoning than ideal. However, each incident spurred improvements: rate-limits were added, code was audited and hardened, and the architecture refined. To truly appreciate these evolutions, we need to examine the major incidents themselves. Let’s turn to the case studies – the pivotal exploits and outages that have defined Solana’s security journey.
Application-Level Exploits: DeFi’s Double-Edged Sword
Solana’s booming DeFi and NFT ecosystem has been a magnet for creative new applications – and unfortunately, for attackers looking to strike at those apps. Application-level exploits are incidents where the flaw lies in a smart contract or on-chain program (not the core Solana code), typically allowing theft of funds. Two of the most dramatic heists in crypto history happened on Solana, serving as stark lessons in the risks of on-chain programming.
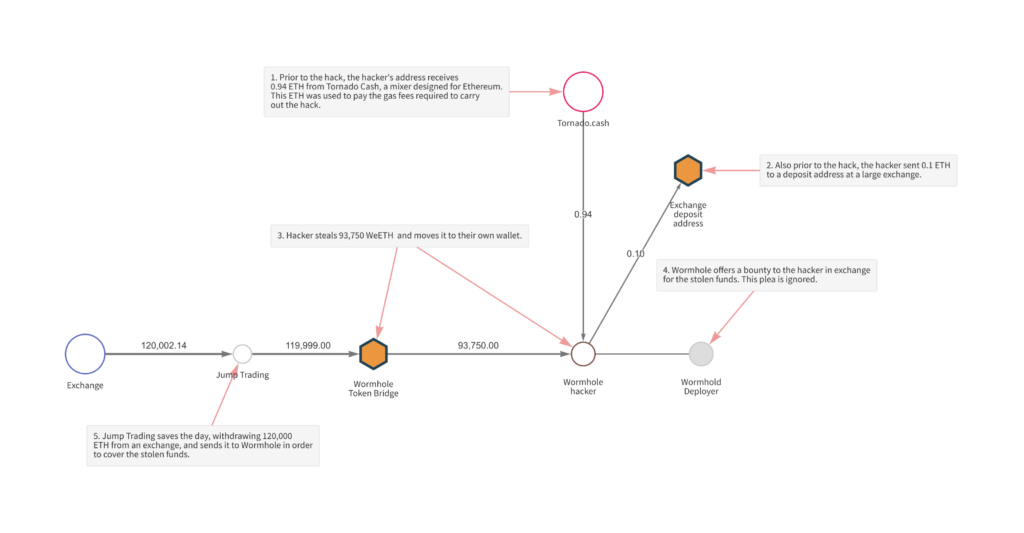
Wormhole: The $321 Million Bridge Breach (Feb 2022). Wormhole is a cross-chain bridge protocol that connects Solana with other networks like Ethereum. Bridges are notoriously attractive targets because they hold pooled assets from multiple chains – essentially giant honeypots. In Wormhole’s case, users would lock ETH on Ethereum and receive “Wrapped ETH” (WeETH) on Solana, backed 1:1. On February 2, 2022, an attacker found a bug in Wormhole’s Solana smart contract that allowed them to mint WeETH without depositing any ETH. In essence, they forged a valid signature that fooled the contract into thinking a deposit occurred when it hadn’t. The result: the attacker minted 120,000 WeETH (worth roughly $320–326 million) out of thin air and immediately swapped much of it for real assets on Solana.
This exploit had cascading implications. Suddenly, the WeETH circulating on Solana was unbacked – a massive hole in the bridge’s balance. If users realized this, they would lose trust in WeETH’s value, potentially dumping it and causing a wider crash in Solana’s DeFi markets. In effect, one contract’s bug threatened systemic risk. The story ended with a dramatic twist: Jump Crypto (which had acquired the Wormhole developer) stepped in within hours to replenish the 120,000 ETH from their own treasury, restoring full backing to WeETH. This was an extraordinary bailout, underscoring how severe the incident was. The vulnerability itself – a deprecated signature verification function that failed to properly authenticate guardians – was quickly patched, and Wormhole offered the hacker a $10M bounty to return funds (an offer ignored to this day). The Wormhole hack remains one of the largest DeFi exploits ever, and a cautionary tale: in cross-chain bridges, a single lapse can burn multiple networks at once. Chainalysis noted that by August 2022, 69% of all crypto stolen that year was from bridge hacks like this, marking them as the top security risk in DeFi at the time.
Mango Markets: Price Manipulation to Pillage $116M (Oct 2022). If Wormhole was a brute-force code exploit, the Mango Markets attack was more of a financial loophole exploitation. Mango Markets was a popular Solana-based trading platform for perpetuals and lending. On October 11, 2022, an attacker (later infamously self-identified as Avraham Eisenberg) took out a massive position on Mango’s order books to artificially pump up the price of MNGO (Mango’s own governance token).

By driving MNGO’s price sky-high in a thin market, the attacker inflated the value of collateral they had posted on Mango. This suddenly allowed them to borrow against that collateral far more than should have been possible – effectively taking out loans from Mango’s treasury using phantom collateral. In a rapid sequence, the attacker borrowed and withdrew around $116 million worth of various crypto from Mango’s liquidity pools, draining the platform.
What makes Mango’s case notable (beyond the dollar amount) is the governance twist that followed. Mango was a DAO; the attacker, now holding a large amount of MNGO tokens (whose price he’d manipulated upwards), proposed a governance vote to let him keep a portion of the funds as a bounty and return the rest. Remarkably, he voted for his own proposal with millions of stolen tokens, achieving quorum. Essentially, the thief tried to use Mango’s decentralized governance against itself to legitimize the theft. This caused an uproar. While a settlement was eventually reached (roughly $67M was returned, with the attacker keeping a hefty “bug bounty”), the incident blurred lines: Was it a hack or savvy (if unethical) trading? The U.S. SEC and CFTC later declared it outright market manipulation and charged Eisenberg. For Solana, Mango’s exploit highlighted how economic design is part of security – the attack didn’t exploit a coding bug, but rather an oracle and liquidity vulnerability (Mango’s token was thinly traded and its value could be gamed).

It was also a wake-up call on governance attacks: a malicious actor can accumulate voting power under certain conditions to twist a protocol’s arm.
Other DeFi Exploits on Solana. Wormhole and Mango grab headlines, but they were not isolated. 2022 in particular saw a string of Solana projects hacked or exploited via smart contract bugs:
Cashio (March 2022): A stablecoin protocol where a hacker discovered an infinite mint bug – they forged a fake collateral token account that passed a validation check, allowing unlimited CASH stablecoins to be minted. The result was a $50 million loss, as the attacker minted and swapped out all value. CASH became worthless overnight. The root cause was a missing check in the contract’s account validation logic.
Solana Program Library (SPL) Exploits: Some core building blocks were found to have issues. For example, a bug in the SPL Token/Lending library affected protocols like Solend and Larix in 2022, where an attacker could have tricked the system into treating an account as if it were a liquidity provider when it wasn’t. In Solend’s case, an exploit was attempted but quickly mitigated. The Solend team caught a suspicious transaction tweaking the protocol’s parameters (an **unauthorized use of
updateReserveConfig()function) and reversed its effects. Funds were saved, though a few users got liquidated and later compensated. It showed that Solana teams and auditors had to be vigilant not just in their own code, but in upstream libraries.Crema Finance (July 2022): A liquidity protocol hit by a flash-loan attack, losing around $8.7M. The hacker manipulated price tick accounts in Crema’s concentrated liquidity market, exploiting a math error to falsely boost their liquidity value and withdraw others’ funds. Crema paused and later negotiated a return of some funds, similar to many Ethereum DeFi hacks.
Raydium (Dec 2022): Technically a private key compromise rather than a code bug, but at a major DeFi app. Raydium, one of Solana’s biggest decentralized exchanges, saw an attacker use the platform’s admin wallet to withdraw liquidity provider funds from all pools – stealing about $4.5–$5.5M. How did the attacker get the key? Raydium suspects a developer’s computer was infected by a Trojan, giving up access to the admin wallet. The incident underscored that even a well-audited smart contract can be undone by a single hot wallet with too much privilege (a centralization risk noted by auditors). In response, the community pushed for multi-sig or timelocked control of admin functions to avoid single points of failure.
By the end of 2022, Solana’s DeFi exploits totaled over $500M in losses, making it one of the worst-hit ecosystems that year (largely due to Wormhole and Mango). Ten separate incidents exceeded $1M lost. This was an intense trial by fire for Solana’s nascent DeFi scene. However, each exploit also drove improvements: better audits (many projects engaged firms like OtterSec, Neodyme, etc.), more robust oracle mechanisms (e.g. switching to more reliable price feeds), and risk management (circuit breakers to pause protocol operations when things go haywire).
Supply Chain Attacks: When Dependencies Turn Dangerous
Even the most secure on-chain code can be undermined if a critical piece of off-chain software is compromised. Supply chain attacks target the tools and libraries that developers and users rely on, inserting malicious code at the source. In late 2024, Solana’s ecosystem experienced a stark example of this, reminding everyone that security isn’t just about smart contracts – it’s about the entire software pipeline.
The Solana Web3.js Library Backdoor (Dec 2024). @solana/web3.js is a popular JavaScript library used by countless Solana dApps and wallets to interact with the blockchain. With over 400k weekly downloads, it’s effectively the backbone of Solana’s web tooling. In December 2024, attackers managed to compromise a maintainer’s GitHub account with publish rights to this library. They used this access to quietly slip in two malicious releases: versions 1.95.6 and 1.95.7 on npm, which contained code to steal users’ private keys. For about five hours on December 2, these poisoned versions were live on the official repository before the breach was noticed and the updates pulled.
In those hours, any project that unfortunately updated to the new versions essentially installed a trojan. The malicious code would reportedly exfiltrate secret keys whenever the library was used in contexts where keys might be present (for example, a server-side script handling transactions on behalf of users, or a wallet that mistakenly used the library with an exposed key). Thankfully, most non-custodial wallets (like Phantom) were unaffected – they don’t expose private keys even to their own code, let alone a library. The attack primarily threatened projects that ran their own backends with direct key management. The incident was caught early: developers noticed the suspicious code and raised alarms, leading to a rapid patch (version 1.95.8) and revocation of the compromised maintainer’s credentials.
While no major theft was reported from this, it was a close call. The Solana Foundation and security community treated it with utmost severity, as it could have been a mass compromise of wallets if undetected. In response, Solana’s ecosystem moved to tighten supply chain security: encouraging use of package signing, two-factor authentication on developer accounts (the compromised account apparently lacked hardware 2FA), and better monitoring of critical libraries. This attack echoed similar supply-chain hacks in crypto (like the event-stream npm package incident in 2018) and underscored an industry-wide challenge: open-source software is only as secure as the weakest link in its maintainers’ ops.
Other Supply Chain Vectors. Beyond web3.js, one can imagine other points of entry: malicious browser extensions or fake mobile wallet apps. In fact, around the same period, users had been tricked into downloading counterfeit wallet apps that stole keys – essentially phishing via app stores. While not a “supply chain attack” on official code, these social engineering tricks achieved a similar goal. The Slope wallet hack in August 2022 (which we’ll cover under key compromises) also had a flavor of supply chain risk: it wasn’t the Solana protocol or even Slope’s blockchain code that was at fault, but an analytics service (Sentry) integrated into Slope’s app that became the weak link.
The key lesson is that securing the base layer and dApps is not enough if the libraries, APIs, and infrastructure around them are subverted. Solana’s community now places heavy emphasis on code provenance and integrity. Developers are more wary of upgrading dependencies blindly and are adopting tools to verify exactly what code they’re pulling from npm or GitHub. In an ecosystem that moves as fast as Solana’s, this careful approach is a cultural shift – a necessary “pause and inspect” mentality injected into the rapid pace of innovation.
Core Protocol Bugs: Halting the Heartbeat
While application bugs can lead to theft, core protocol bugs strike at the very functionality of the blockchain. These are flaws in Solana’s validator client or consensus mechanisms that can cause network outages or consensus failures. Such incidents don’t directly steal money (there’s no hacker draining funds, typically), but they are highly disruptive – akin to the entire Solana “city” experiencing a power outage due to a software glitch in the power grid. Solana’s mainnet, still officially in “beta” for much of this history, suffered a handful of these critical bugs, especially in 2021–2022 as it rapidly evolved. Let’s examine a few notable ones:
The Durable Nonce Bug (June 2022). In early June 2022, Solana went down for about four and a half hours due to a consensus bug triggered by a feature called durable transaction nonces. Durable nonces are meant for use cases like exchanges or custodians that need to sign transactions in advance without worrying about the normal short-lived blockhash expiration. Ironically, this convenience feature became a bane when a certain valid “durable nonce” transaction caused validators to generate different outputs. Specifically, a bug in how the runtime handled durable nonce accounts led to nondeterministic behavior – some nodes thought the transaction was valid, others thought it was a double-spend, splitting consensus (06-01-22 Solana Mainnet Beta Outage Report). The cluster stopped processing new blocks (a stall) as it couldn’t reach supermajority agreement.
Validators, in coordination with core devs, chose to restart the network after disabling the durable nonce feature to prevent recurrence. A post-mortem revealed the precise code flaw, and a patch was issued in the next release. The incident was Solana’s fifth outage of 2022 at that point (Solana developers tackle bugs hoping to prevent further outages), fueling critics but also spurring swift improvements. The nonce feature was temporarily disabled until a more robust implementation could be deployed. This bug highlighted how even “niche” features can have outsized impact. It also underscored the challenge of testing a live, high-throughput system – the code path that failed had passed unit tests and devnet, but the particular sequence of events on mainnet unveiled a scenario not caught before. After this, Solana put even greater emphasis on test coverage for edge-cases and added more fault injection testing in its consensus code.
Duplicate Block Bug (Sept 2022). In late September 2022, Solana experienced another roughly 8-hour outage due to a consensus failure, dubbed the duplicate block bug. In this case, a validator produced two blocks for the same slot (likely by accident, perhaps due to a temporary network partition or delay). This shouldn’t be catastrophic – the network is designed to handle forks. However, a bug in the fork choice algorithm’s implementation prevented validators from properly resolving the fork. One validator failed to switch forks because it didn’t correctly recognize the other fork’s common ancestor (owing to the duplicate block) . Essentially, a rare sequence of events (two blocks with the same slot number) led a subset of nodes to get stuck on the wrong fork, unable to rejoin the main fork.
Once again, a coordinated restart was needed after the bug was identified. The fix involved patching the fork selection logic to handle this duplicate block scenario. While no funds were lost, confidence was certainly rattled. However, the silver lining was that each of these outages helped the core dev team harden the codebase. Solana’s GitHub saw a flurry of updates in late 2022 to improve reliability: better handling of unusual fork scenarios, more aggressive turfing of invalid forks, and importantly, features to prioritize vote transactions so that validator consensus messages don’t get lost in a sea of regular transactions. During the earlier outages caused by spam, one issue was validators’ voting transactions – which signal their view of the chain – were not getting through, worsening the consensus stall. Fixing that was vital.
Turbine Overload: The 2023 Mega-Block Incident. Not all bugs were purely consensus logic – some were about network propagation. In February 2023, after a period of relative stability, Solana faced one of its longest downtimes (~19 hours) caused by a quirk in how data is gossiped across the network. The culprit was a validator’s custom block-forwarding setup that went haywire, emitting an exceptionally large block (over 32MB, when normally blocks are a tiny fraction of that). This monster block – carrying perhaps 30x the usual number of transactions – overwhelmed Solana’s Turbine protocol (the UDP-based block propagation layer). Turbine is meant to chop data into small packets (shreds) and relay them efficiently, even through unreliable networks. But this validator’s aberrant behavior bypassed some of the deduplication safeguards. The network got stuck repeatedly retransmitting this jumbo block’s data, saturating nodes’ bandwidth in a loop. Block production stalled as the cluster struggled to recover from the traffic storm.
Engineers diagnosed that a failure in shred deduplication logic allowed the same data to propagate ad infinitum, effectively a self-DDoS from within. The emergency fix was to restart the network with that validator removed and to push a patch requiring nodes to abort if they generate a block exceeding a certain shred count. Solana v1.13.7 was released with improved filtering to prevent runaway propagation. This was a learning moment: it wasn’t a malicious attack per se, but a misconfiguration that had similar impact to a denial-of-service attack. It led to tightening the protocol’s sanity checks – no single validator should be able to overwhelm the rest, even unintentionally.
By 2024, Solana’s core protocol had matured significantly, and it showed. A noteworthy event occurred in August 2024 when a critical vulnerability was discovered in private by security researchers. Instead of waiting for an exploit, Solana’s team coordinated a covert patch rollout: they quietly got a fix into validators’ hands, avoiding any public disclosure until the majority had upgraded. This prevented attackers from learning of the vulnerability and exploiting it in the wild. It was a sign of a more proactive security posture – something one would expect from an increasingly battle-tested network.
In essence, Solana’s core codebase went through a trial by fire. Early outages exposed weaknesses in consensus and networking that have since been addressed one by one. It’s notable that since the big Feb 2023 incident, Solana saw no further major outage for over a year, achieving a stability milestone that the community had long been striving for. Plans to finally remove the “beta” label from mainnet coincided with this improved reliability. Moreover, the development of a second independent validator client (Firedancer by Jump Crypto) promises to reduce the likelihood of single-bug-induced halts in the future – if one client has a bug, the other might keep the network alive.
Network-Level Attacks: Spam, Outages, and DDoS
Closely related to core bugs, but distinct in cause, are the network-level attacks or outages that result from overwhelming the blockchain’s capacity. These incidents often resembled distributed denial of service (DDoS) attacks, sometimes deliberate, other times the unintended consequence of bot stampedes during hype events. Solana’s high throughput capacity was stress-tested by these events, which exposed insufficient safeguards against spam. Let’s recount a few famous (or infamous) episodes:
The Grape Protocol IDO – Solana’s 17-Hour Blackout (Sept 2021). This was Solana’s first major outage and a wake-up call to the realities of uncontrolled load. On September 14, 2021, a project called Grape was launching its token sale (IDO) on Raydium. It was first-come, first-serve – a perfect scenario for arbitrage bots to swarm in. And swarm they did. Bots generated an “unprecedented flood” of transactions – at peak, the network saw 400,000+ TPS bombardment at the ingress. Validators were utterly overwhelmed: they were ingesting over 1 Gbps of transaction data (more than some network cards could handle). In one critical twist, a particular bot or set of bots began crafting transactions that locked down key resources (it write-locked 18 important accounts, including the main token program). This prevented parallel transaction processing – normally Solana’s forte – forcing many transactions to run one-by-one and creating a massive bottleneck.
The result was that Solana’s validator consensus stalled. The flood was so heavy that vote transactions (which have to get through for the network to finalize blocks) were getting drowned out. It was as if the traffic jam became so bad that even the traffic cops couldn’t move to sort things out. After 12 minutes of chaos, block production ceased. Solana was offline from midday into the night. Finally, the dev team and validators coordinated a manual restart with patched code. No funds were lost, but confidence took a hit and headlines blared about Solana’s “first crash”.
In response, Solana introduced multiple fixes: ignoring write-locks on program accounts (so that one program can’t be used to stall all others, as happened with the token program) was already in the works and got deployed. They added rate limits on transaction forwarding, so validators wouldn’t blindly propagate an unbounded flood to peers. Critically, as mentioned, they made sure votes are prioritized in the pipeline so that even under duress, consensus can make progress. These changes over the next couple of versions greatly improved Solana’s resilience. The Grape IDO incident is often cited as an example of how cheap fees without proper QoS controls can invite trouble – something Solana addressed by later rolling out a lightweight fee market (congestion fees) in 2022 to disincentivize endless spam on popular apps.
The Candy Machine Bot War (April 2022). In the spring of 2022, NFTs on Solana were all the rage. A tool called Candy Machine was the standard for launching NFT mints. On April 30, 2022, a particularly hyped NFT drop led bot operators to go wild, sending 6 million+ transactions per second at the network at peak, according to Solana Labs’ figures – far beyond even Solana’s theoretical throughput. The network buckled under the load, and block production halted for about 7 hours. This was a DDoS by greed: botters were trying to win scarce NFTs by brute force.
Solana’s immediate reaction (besides another restart) was pragmatic and a bit humorous – Metaplex, the developer of Candy Machine, implemented a “bot tax”: a small fee (0.01 SOL) charged on invalid or duplicate mint transactions. In other words, if you try to spam Candy Machine and fail, you pay a price. This simple economic disincentive sharply reduced the spam incentive. It was an early form of rate-limiting via fees, foreshadowing Solana’s broader fee prioritization updates. The event also accelerated work on stake-weighted QoS, ensuring that validators process transactions from reliable sources preferentially, rather than treating a bot’s 1000 TPS and a normal user’s 1 TPS equally.
Service Denial vs. Decentralization. Some critics labeled these incidents as Solana being “DDoS’ed,” sometimes even implying malicious intent (there were rumors: was it rival chains or just profiteers?). Whether or not any specific event was a deliberate attack, the effect was the same: the network’s capacity was saturated. Solana had to learn to shed load gracefully – a tough lesson for a system designed to be as permissive as possible. Over time, the introduction of fee markets (small fees that rise during congestion, burning the excess) helped. By 2023, if someone tried a Grape-like spam, they’d have to pay exponentially higher fees for their transactions to be included, making it economically impractical to sustain a flood. This is similar to how Ethereum’s gas mechanism self-regulates load, albeit Solana’s fees remain far lower.
It’s worth noting that Solana never experienced a malicious 51% attack or a consensus cartel double-spend – the “attacks” were essentially feeding it too many transactions or triggering bugs. In a sense, these are attacks on availability (make the service unavailable), not attacks on correctness. Still, availability is crucial; a downed network is of little use. Solana’s improvements have paid off. As of late 2024, despite occasional traffic bursts (e.g., popular token launches or viral game moments), the network has stayed online and recovered without needing a full restart. The painful episodes of 2021–2022 led to a more robust network in 2023 and beyond.
Governance and Control: The Human Factor
Decentralized governance – where token holders or community members vote on protocol changes – is often touted as a strength of crypto projects. But it can also be a security vector. If an attacker can game the governance process (for instance, by acquiring a majority of governance tokens cheaply or temporarily), they might push through malicious changes. Additionally, many Solana programs have upgrade authorities or admin keys – essentially a centralized control that can override or alter the smart contract. These are necessary during early stages for bug fixes, but they represent high-value targets if compromised.
In Solana’s history so far, there hasn’t been a headline-grabbing “governance hack” in the mold of Ethereum’s Beanstalk exploit (where an attacker used a flash loan to win a governance vote and steal ~$182M). However, elements of governance issues did surface:
Mango Markets Governance Aftermath: As discussed, post-exploit the attacker used Mango’s own governance process in an attempt to absolve themselves and walk away with a bounty. This quasi-hostage situation – “vote to let me keep $X million, or I keep everything” – revealed a vulnerability in governance design. A malicious actor who gains a lot of tokens (even through theft) can influence or hijack proposals. Mango’s community was stuck between a rock and hard place: pursue the attacker (with uncertain recovery prospects) or negotiate via governance. They chose the latter, a controversial decision. The takeaway for other protocols was to consider governance attack prevention: e.g., quorum rules that exclude recently acquired tokens, time locks for proposals, and circuit breakers for sudden changes. Since then, some Solana projects have added safeguards – like requiring longer voting periods for critical changes or multisig approval for emergency actions, to reduce the risk of a quick governance ambush.
Solend Whale Incident (June 2022): In this case, the exploit didn’t occur, but a governance crisis did. Solend (a Solana lending platform) had a single whale with an enormous loan that risked liquidation in a volatile market. Fearing that a chaotic on-chain liquidation of this whale’s collateral might crash Solana (due to size), Solend’s team proposed a governance vote to temporarily take over the whale’s account (a very extraordinary measure that broke decentralization ideals). The proposal passed with one big voter’s support, sparking outrage in the community and beyond. It was seen as governance being used to violate a user’s property rights. Under pressure, Solend quickly held a second vote to overturn the first, and the whale managed to gradually wind down without incident. While not a hack, this saga showed how governance can introduce trust issues: if users fear that token holders can just vote to seize funds in a crisis, that undermines confidence. Solend learned to implement more robust risk management (to avoid getting to that point), and the incident sparked debate about the limits of DAO governance intervention.
Admin Key Risks: Several Solana programs started with upgrade authorities fully controlled by the dev team (a common practice to allow rapid iterations). Over time, best practice is to hand those keys to a multi-signature wallet or a DAO governance to decentralize control. The Raydium hack already illustrated the danger of a single admin key compromise (CertiK - 2022 Solana Exploits Overview). Another example was Serum – Solana’s orderbook DEX – which had an upgrade key that became inaccessible after FTX (its sponsor) collapsed. The community ended up forking Serum into a new community-owned version (OpenBook) because no one could trust the old program’s key, which might have been compromised. This underscores that an admin key is both a guardian and a vulnerability; if the key holder goes rogue or is hacked, users are at risk. Thus, Solana projects increasingly advertise being “keyless” or governed by DAO – not just for optics, but to eliminate that single point of failure.
Moving forward, governance exploits remain a potential threat on Solana as DeFi protocols evolve. Attackers might not bother with flash loans on Solana (due to its smaller lending pools compared to Ethereum), but they could try bribery or collusion attacks in low-turnout votes. Solana’s community funds and treasuries could be targets if not enough voters pay attention. The shield here is active and educated governance participation, and possibly Safeguard contracts – like moderators that can veto blatant malicious proposals or at least flag them for community review.
In summary, the human layer of decision-making in Solana’s ecosystem has seen its share of drama. While not as directly costly as technical hacks, governance and key management issues have significant impact on user trust. The network learned that decentralization of control is not just an idealistic goal, but a practical security measure.
Validator Misconfigurations and Lapses
Solana’s validator community is the backbone of its network. By 2022–2023, Solana had thousands of validators distributed globally. With that comes variability: not everyone runs the exact same hardware, software version, or network setup. Validator misconfigurations or lapses can sometimes cause disproportionate issues – either for the network or for the validators themselves.
One stark example we discussed was the February 2023 incident where a single validator’s custom setup produced an out-of-spec block that tipped the network over. In that case, it was an overly aggressive block propagation setting. This taught the community that even well-meaning tinkering (running custom node modifications for performance) can introduce instability. Post-mortem discussions encouraged validators to stick to recommended settings and coordinate any custom changes with core devs.
Another area is validator updates. Solana has seen instances where not all validators updated to the latest patch that fixed a critical bug, which then hampered recovery during an outage. For example, during one restart attempt in Sept 2021, the first try failed partly due to some validators running a slightly different software version that had a bug – they had to quickly push another patch and restart again. Now there’s more emphasis on timely updates and better alerting so validators know when a critical upgrade is a must.
Also, insufficient hardware or poor network peering by some validators can slow down consensus. Solana’s design expects validators to have solid hardware (especially fast SSDs and high CPU for signature verification) and good internet connectivity. In the early days, a few validators running on underpowered machines or cloud instances could become lagging nodes that, in worst cases, might contribute to forks or just drop out under load. The community now has clearer benchmarks and even incentives (via the stake weighting and quality of service) for validators to meet performance standards.
It’s worth noting what hasn’t happened: no validator has been slashed or penalized on Solana for misbehavior (Solana hasn’t enabled slashing in mainnet-beta so far, focusing on liveness). We haven’t seen a malicious validator attack consensus, like signing two blocks intentionally to try to confuse the network – partly because the economic incentives are aligned (doing so would hurt the value of SOL they likely have at stake). But as Solana grows, the validator set’s security (both physical and cyber) will face more scrutiny. We did see attempts to phish validators or attack their systems off-chain (for instance, using fake Docker images or exploits targeting their GPU card drivers), though no known successful case caused a network event.
One “misconfiguration” incident that affected users indirectly was when RPC node providers (which many wallets rely on) went down or were rate-limited, causing users to think the network was down when it wasn’t. For example, in early 2022 some public RPC endpoints crashed under heavy load. The network was producing blocks, but wallet apps couldn’t fetch data. This wasn’t a validator fault per se, but it highlighted that running robust infrastructure (RPC, APIs) is part of the security equation – if users can’t access the chain, it’s as bad as the chain being down to them. Now multiple community RPC operators and services exist to decentralize this layer (and Solana is exploring light clients and other trust-minimized access methods).
In conclusion, while validator missteps have occasionally caused or exacerbated incidents, the network’s resilience has improved by setting strong norms and standards for operators. Solana’s documentation and community channels emphasize correct configuration, and there are quick patch releases when issues arise. The fact that Solana has attracted professional validators (including big ones like Chorus One, Everstake, etc.) means there’s generally a high level of competence in running the nodes. And with the forthcoming Firedancer client, diversity in software will further reduce the chance that a single bug or misconfig takes down everyone.
Trends and Trajectory: Are Things Getting Better?
After dissecting this long list of incidents, an obvious question arises: Has Solana’s security posture improved over time? It’s helpful to zoom out and look at trends across the years – in terms of number of incidents, severity, and underlying causes. Data and visualizations can cut through anecdote to reveal patterns.
[Chart: Bar chart showing the number of major Solana incidents per year (X-axis: 2020, 2021, 2022, 2023, 2024; Y-axis: count of incidents). The chart reveals a low incident count in 2020 (beta stage), a jump in 2021 with a couple of outages, a peak in 2022 with numerous exploits and outages, then a decline in 2023 and 2024. This suggests that 2022 was the worst year for Solana’s security, while subsequent years saw fewer major incidents as fixes took effect.]
2022 Spike: The year 2022 stands out with the highest number of incidents. Solana faced multiple outages (five in that year) and many of the largest DeFi hacks (Wormhole, Mango, etc.). This coincided with Solana’s peak adoption and load – more usage exposed more bugs. It’s evident that many root causes in 2022 were first-time discoveries, requiring fundamental fixes.
Post-2022 Improvement: 2023 shows a marked drop in incidents. Only one significant outage (early in the year) and far fewer high-profile hacks occurred. 2024 continued that positive trend. This decline correlates with the mitigation measures implemented after 2022 – the introduction of fee prioritization, hardened core code, and a generally more security-conscious development approach. It also helped that the crypto market cooled off in 2023, reducing the immediate incentive for attackers (less TVL to target, less frenzy to exploit).
[Chart: Stacked bar chart of total value lost ($) in Solana incidents by year, broken down by category (application exploits vs. key compromises vs. exit scams). X-axis: Years 2021–2024, Y-axis: USD lost. The chart shows 2022 with an enormous bar (~$520M lost, mostly from application exploits in red). 2021’s bar is negligible. 2023’s bar is small, and 2024 has a modest uptick (due to one or two incidents like DEXX). This indicates that 2022 was not only the busiest year for incidents, but also by far the costliest.]
Loss Concentration in 2022: Over half a billion dollars were stolen from Solana-related projects in 2022. The Wormhole hack alone accounts for ~60% of that sum. This made Solana one of the hardest-hit ecosystems in that DeFi exploit wave (though Binance Chain and Ethereum also had big hits like Ronin). In contrast, losses in 2021 were minimal (Solana was just rising; no major hacks reported on Solana in 2021 aside from some rug pulls).
2023 and Beyond: The dramatic drop in funds lost by 2023 is a positive sign. Some of this is due to attackers shifting focus – in 2023, cross-chain bridges and Ethereum sidechains were more in the crosshairs, and Solana’s DeFi TVL had shrunk post-FTX, making it a smaller target. But it also reflects that Solana’s existing protocols were battle-tested by then. Many weak projects had already been exploited or faded away, and the survivors (plus new ones) were generally more security-hardened. By 2024, when Solana usage started ticking up again (e.g., with new zk-proof-based apps, and the network stabilizing), we still didn’t see a return to 2022 levels of mayhem – implying lessons were learned.
Another trend worth noting is the nature of incidents shifting. In 2021, the big issues were outages from overload. In 2022, code exploits and key thefts took center stage. In 2023–2024, supply chain and infrastructure became the focus (as with the web3.js incident and the DEXX hot wallet compromise). This evolution might indicate that as the obvious bugs were fixed, attackers moved to softer targets like third-party tools and centralized lapses.
Yet, not all trends are rosy. Social engineering and rug pulls (scams by project insiders) remain as prevalent as ever in the broader crypto space. Solana had its share of these, e.g., the Big Daddy Ape Club NFT rug in 2022 where the creators vanished with $1+ million of buyer funds. Those kinds of frauds don’t show up in protocol “incidents” charts but do affect the community’s security experience. Education and community vigilance are ongoing needs.
Common Root Causes and Remedies
Having reviewed the gamut of incidents, certain root causes pop up repeatedly. Identifying these is crucial, because they point to where structural improvements make the biggest impact. Let’s highlight some recurring themes:
Unchecked Inputs and Assumptions: Many application exploits (e.g., Cashio’s infinite mint, Wormhole’s signature bypass) boiled down to smart contract code not fully validating an input or assuming something that an attacker proved false. The remedy here is rigorous auditing and formal verification. Teams learned to bring in external auditors to scrutinize their programs before launch. Tools for static analysis of Solana programs improved. There’s an increasing interest in formal methods – proving certain invariants about the code (for instance, “token X cannot be minted unless condition Y is met”). While formal verification is still niche, high-value programs like bridges now treat it as a worthwhile investment.
Hot Keys and Centralized Secrets: Several incidents traced to a single private key compromise – from Slope’s wallet keys leak, to the Raydium admin key Trojan, to the DEXX platform hack affecting thousands of user keys. The root issue is having too much sensitive power in one place, and sometimes poor operational security around it. Remediation patterns include multisig wallets (so that no one person’s key can move funds), hardware security modules (HSMs) or secure enclaves (Solana’s validator clones on Ledger and even the new Saga phone aim to secure keys in hardware), and limiting the scope of what keys can do (principle of least privilege). For user wallets, the push towards hardware wallets and seed vaults is strong – Solana even built the Saga smartphone with a secure element to store keys isolated from Android. After the Slope hack, wallet devs ensured they never send or store mnemonic phrases in third-party services, and they urged users to rotate to new wallets if there was any doubt.
High-throughput Bugs: Solana’s unique selling point – high TPS – also meant unique bugs (like the durable nonce and turbine issues) that only manifested under stress. The root cause here is often concurrency issues or overflow conditions (as seen with the integer overflow during the restart after Grape IDO). The remedy has been simulation and testnet chaos testing. Solana now runs a load-testing cluster where they intentionally push insane traffic to try to break it in a controlled environment before code hits mainnet. They’ve also improved the telemetry and diagnostics so that if a bug is brewing (say, memory creeping up abnormally), they catch it early. Another remedy is the development of Firedancer, an independent validator client in C++ that is extremely optimized. Not only will it increase performance, but having two different codebases means one might handle edge-cases better or at least not fail the same way as the other, providing redundancy.
Insufficient Rate Limiting: Spam and DDoS issues revealed Solana lacked internal throttles initially. The fix pattern was to implement backpressure mechanisms – like the fee-per-signature after Candy Machine, the RPC rate limits, and stake-weighted QoS. Essentially, Solana moved from “open gates” to “metered gates” where needed. This doesn’t mean sacrificing the low-fee ethos, it means in extreme scenarios, spammers have to pay escalating costs. The network also started leveraging advanced networking (like QUIC, a UDP-based protocol with congestion control) to replace raw UDP, ensuring more fair and efficient packet delivery under load.
Community & Process: Early on, Solana was shipping new features fast (e.g., durable nonce, runtime upgrades) to support burgeoning demand. Some bugs showed a need for more careful code review and community feedback. Today, the core dev process is more open; Solana Improvement Documents (similar to EIPs) allow discussion of major changes. Additionally, a robust bug bounty program incentivizes white-hat hackers to find vulnerabilities before black-hats do. Solana’s bug bounties (run via platforms like Immunefi) have paid out significant rewards for critical findings, which is money well spent compared to the cost of an exploit.
Incident Response Maturity: The way incidents were handled improved over time – that’s a kind of meta-remedy. In 2021, coordination was ad-hoc via Twitter and Discord to restart. By 2022, there were established incident response channels among validators, regular outage reports published by Solana Labs for transparency, and even contingency tools (like the ability to spin up a minimal RPC service to coordinate in case Discord/Google Docs fails). After the August 2024 stealth patch event, the community gained confidence that Solana’s team can handle a 0-day in a professional manner, quietly fixing it across the network without tip-off – something that comes with experience.
In essence, the arc of Solana’s security response has been bending toward robustness. Each category of root cause we identified has seen focused improvements. The ethos has shifted from “move fast and break things” to “move fast, but with seatbelts and airbags installed.” It’s an ongoing journey, of course.
Looking Ahead: Fortifying Solana’s Future
Having survived these trials, what’s next for Solana’s security? The network today is arguably more secure than ever, but new challenges will emerge. Here are some forward-looking recommendations and speculative insights (grounded in what we know):
Diversify and Decentralize Everything: This is a broad theme. Encourage multiple implementations (Firedancer alongside the Rust client) to avoid single points of failure in code. Decentralize control by eliminating single-key authorities – more DAOs, more multisigs, more time-locked upgrades. Even infrastructure decentralization: more community-run RPC nodes and alternative block explorers so that the ecosystem isn’t reliant on one company’s endpoint. The more distributed the ecosystem, the harder it is for any single attack or bug to have systemic impact.
Formal Security Audits as Standard Practice: By 2025, any serious Solana project should undergo one or more audits before and after launch. This was once seen as optional (or teams rushed to market without it), but the cost of skipping has been proven to be far higher. Perhaps the community or Solana Foundation could sponsor a security review DAO – a body of experts that does rotating peer reviews of new protocols. Also, expanding bug bounty programs is key: the greater the reward for responsible disclosure, the less appealing it is to try to exploit and get away with it. Imagine a future where a $10M bug bounty (like Wormhole offered post-hack) is available pre-emptively – that could shift a lot of incentive.
Enhanced Developer Tools: Simplify writing secure programs. The Anchor framework already makes common checks easier, but more can be done. For instance, incorporate formal verification tools that plug into the development cycle (so a dev can run a formal check that certain invariants hold). Perhaps create templates for common use-cases (a safe token vault, a time-lock contract, etc.) that are formally verified once and then reused – reducing re-invention errors. Ethereum has tools like OpenZeppelin libraries; Solana could have an equivalent set of vetted primitives.
On-Chain Monitoring and Circuit Breakers: Solana’s speed means things can go south quickly (Mango’s exploit happened in minutes). Implementing on-chain “circuit breakers” could help – these are conditions coded into contracts or the runtime that detect anomalies and pause operations. For example, a DeFi protocol could automatically halt if a vault is drained below a threshold in one block, giving humans a chance to intervene. At the network level, if transaction floods are detected, the validator software could proactively raise minimum fees to stem the tide (somewhat like how miners raise gas limits in response to sustained load, but automated).
User Protection Features: Improve wallets to guard users. Phantom and others are already adding features like transaction simulation and warnings (“This transaction will transfer 5 SOL to an unknown address, are you sure?”). Future wallets might integrate revoke all approvals easily (to combat malware that grabs an approval to spend NFTs for example). There’s also talk of local fee delegators – so bots can pay extra fees without locking out normal users (Solana’s localized fee markets concept). This ensures even in high demand events, regular users can still get a few transactions in by being in a different fee domain.
Cross-Chain and Bridge Security: Bridges will remain targets. Solutions like validity proofs (a.k.a. trustless bridges using zk-SNARKs) could eliminate or reduce the trust in multi-sig keys that Wormhole had. Solana is exploring being a hub for many chains, which means integrating with bridges that are more secure by construction (like Wormhole V2, or new protocols using light clients). Until then, extra monitoring of bridge contracts (perhaps real-time watchdog programs that can flag irregular mint events) would be wise.
Community Education and Bug Tales: Continue to share and learn from incidents. One positive outcome of 2022 was a trove of post-mortems and analyses (as we’ve cited). This collective memory should be preserved. New developers coming into Solana should read about Mango, Wormhole, etc., the way pilots study past airplane incidents. Perhaps a Solana Security Archives site could host these case studies. The more people know the pitfalls, the more mistakes can be avoided.
In terms of Solana’s trajectory: The network is positioning not just as a DeFi chain but also for consumer apps (payments, gaming, mobile integration via Saga). This shift means security has to be even more foolproof – everyday users demand reliability and safety. We might see more hardware integrations (like Solana Pay enabling hardware-signed transactions to avoid malware on phones). Also, as regulatory focus sharpens, being able to demonstrate strong security and quick incident response will make institutions more comfortable with Solana.
Conclusion
Solana’s evolving security posture can be summarized in a single phrase: from chaos to crucible. The chaos of its early explosive growth revealed cracks in the foundation, but each incident became a crucible that forged a stronger, more resilient network. Just as steel is tempered through repeated heating and quenching, Solana’s infrastructure and community have been tempered by each hack, outage, and exploit.
Today, Solana stands battle-hardened. The blockchain that once drew notoriety for sporadic outages has now clocked significant uptime with no major interruptions for over a year. The free-for-all DeFi environment that enabled nine-figure attacks has given way to audited protocols and cautious risk management. Importantly, the culture around security has matured: there’s no longer bravado about “we can always fix forward later” – instead, there’s a deep respect for adversaries’ capabilities and a proactive drive to prevent issues before they happen.
That said, security is a journey, not a destination. Solana will never be “finished” with security – no complex system ever is. New innovations (like state compression for NFTs, or on-chain AI experiments) will introduce new attack surfaces. Adversaries adapt, perhaps shifting to phishing users or finding creative arbitrage in protocol interactions. The measure of success will be how quickly and effectively Solana can respond – ideally making big crises a thing of the past.
Encouragingly, all signs point to an upward trajectory of learning. The introduction of a second client, the ongoing bounty programs, the core devs’ dedication to transparency with incident reports, and the community’s continued support through turbulent times all bode well. Solana’s story has never been one of playing it safe – it’s about pushing boundaries. Naturally, that meant sometimes learning the hard way. But those lessons “hidden since the foundation” of Solana are now out in the open, steering its future.
In the broader context of blockchain evolution, Solana’s experiences contribute to the collective knowledge of how to scale without breaking. Its pioneering of high-throughput blockchain tech, combined with hard-earned security know-how, might well influence designs of the next generation of chains. The network’s commitment to improvement shows in tangible metrics: fewer incidents, quicker recoveries, more value secured.
As we look to the future, one can imagine Solana shedding the “mainnet-beta” label and simply being “mainnet”, denoting a coming-of-age. The narrative shifts from “Solana is fast but can it be trusted?” to “Solana is fast and robust – here’s how it overcame early scars.” In the end, users and developers want a blockchain that feels like solid ground, not shifting sands. Solana is on its way to providing that solid ground, with the scars to prove it’s been tested.
Solana’s security saga – from multi-million dollar exploits to cutting-edge defenses – is a microcosm of the entire crypto industry’s growth. It reminds us that innovation and risk are two sides of the same coin. The key is managing that risk through continuous learning and adaptation. If the past is any guide, Solana will continue to ask the hard questions of itself: How could this be abused? What’s the worst-case scenario? – and in doing so, turn potential weaknesses into strengths. The fires of adversity have forged a stronger Solana, one that stands as a testament to resiliency in the fast-paced world of blockchains. How secure is a web-speed blockchain? After all these trials, the answer is: more secure than it’s ever been – and getting stronger by the day.
Subscribe to my newsletter
Read articles from Abraham Dahunsi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Abraham Dahunsi
Abraham Dahunsi
I enjoy solving problems by writing code and breaking down technical contents by writing.