Configuring Kerberos Authentication for Amazon RDS PostgreSQL
 Rahul wath
Rahul wath
Introduction
With more applications, users, and databases in organizations, auditing and user management are becoming increasingly challenging for DBAs and security teams using traditional database authentication methods.
Integrating RDS/Aurora with Active Directory helps both teams to centrally add, remove, and audit user access.
In this article, we will explore Kerberos authentication for Aurora PostgreSQL using AWS Managed Microsoft AD.
Steps expected to design Kerberos validation for PSQL DB
Configure an AWS Microsoft Active directory
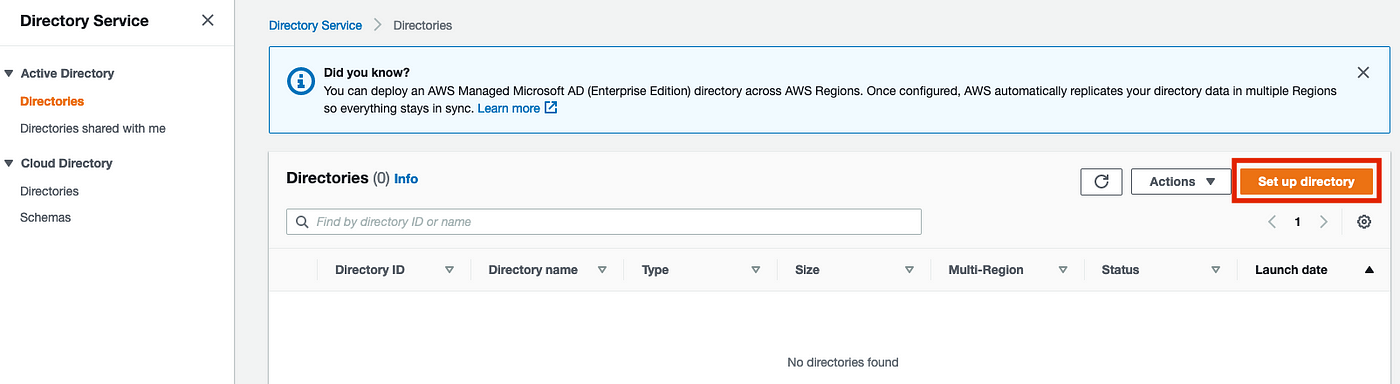
Select AWS Managed Microsoft AD under directory types and click next.
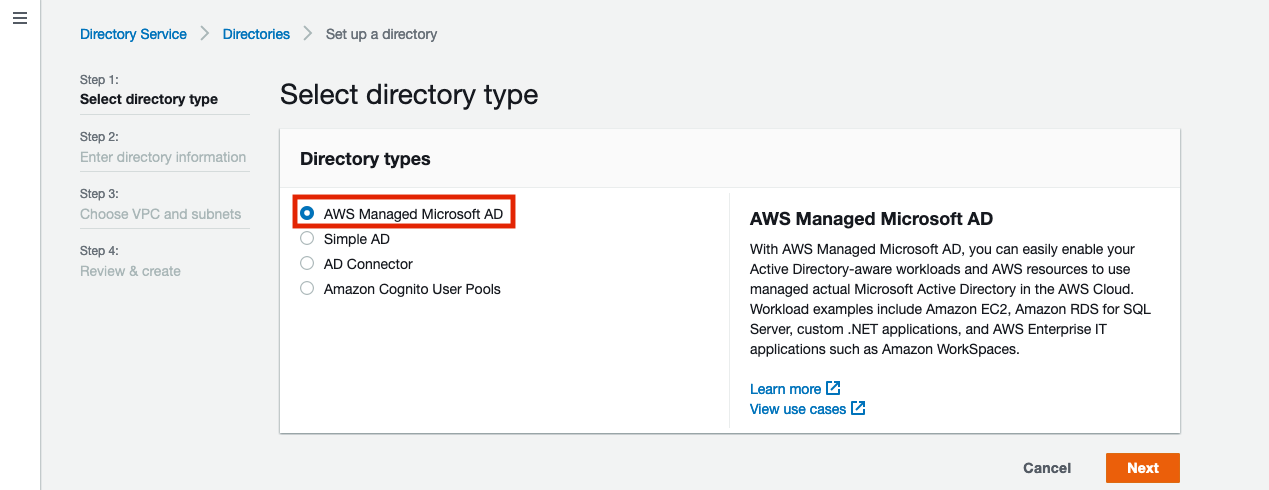
Specify the FQDN (Fully Qualified Domain Name) of the directory, its NetBIOS name, and the admin password:
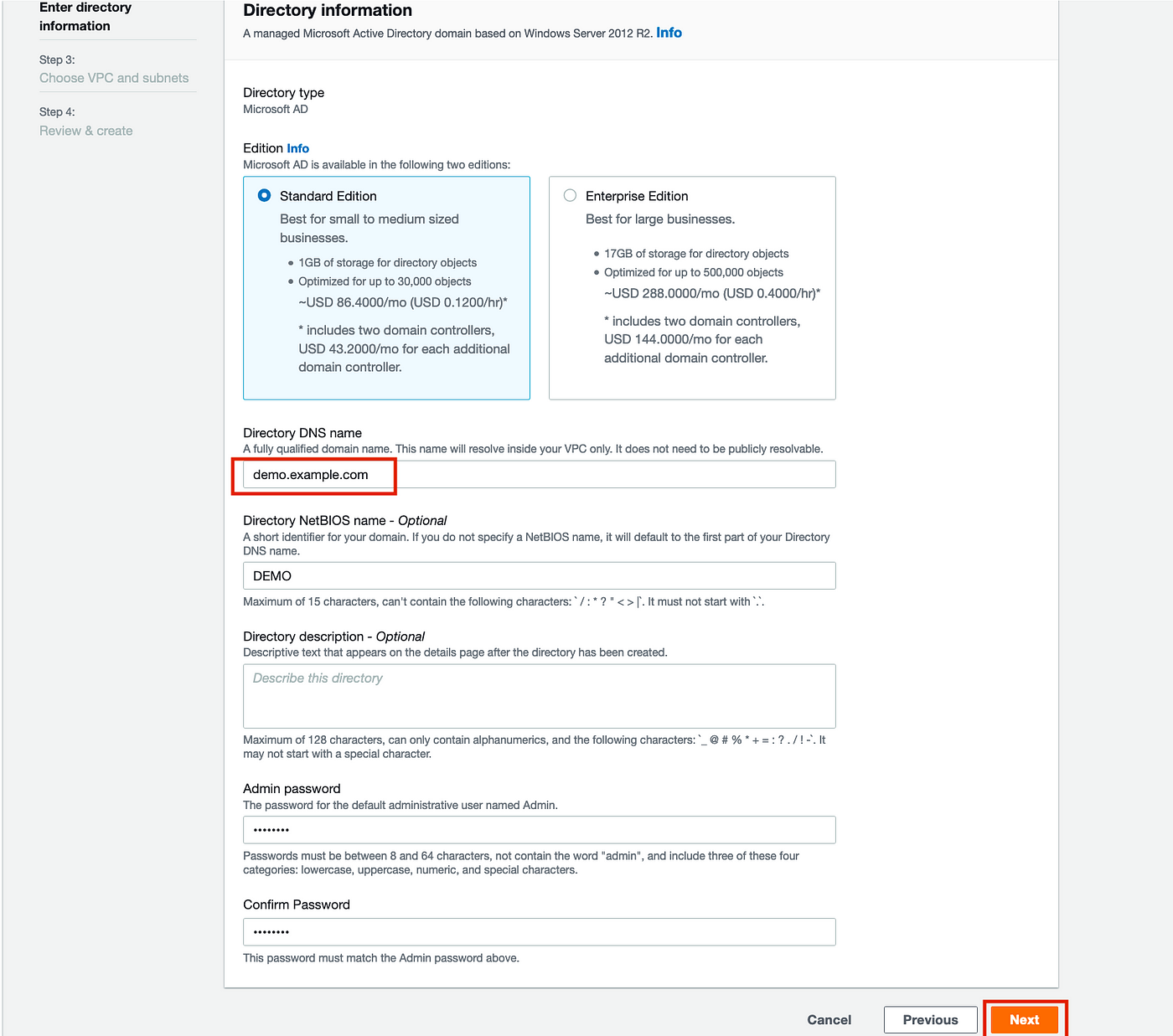
Choose a VPC and subnets for Active Directory deployment:
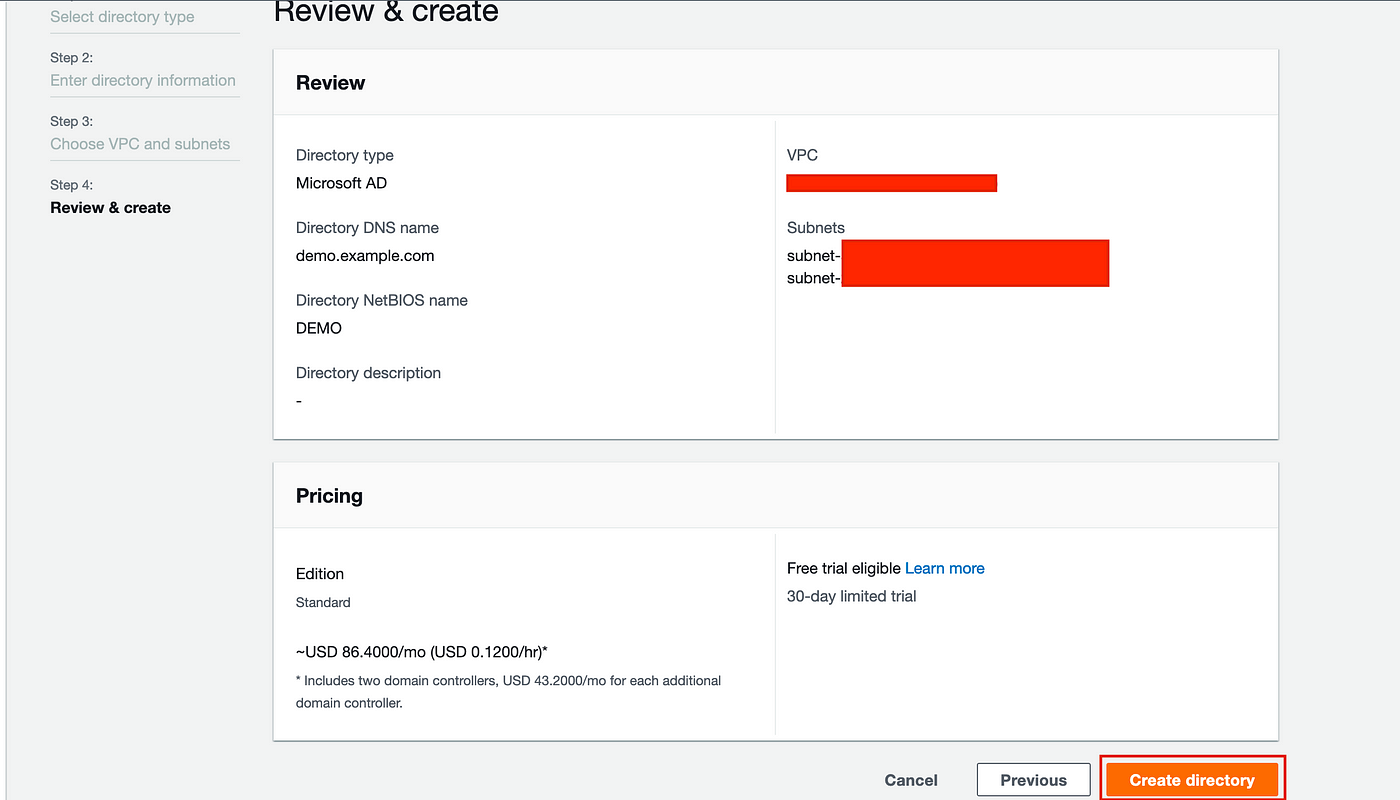
Review all information on the screen and click the ‘Create directory’ button:
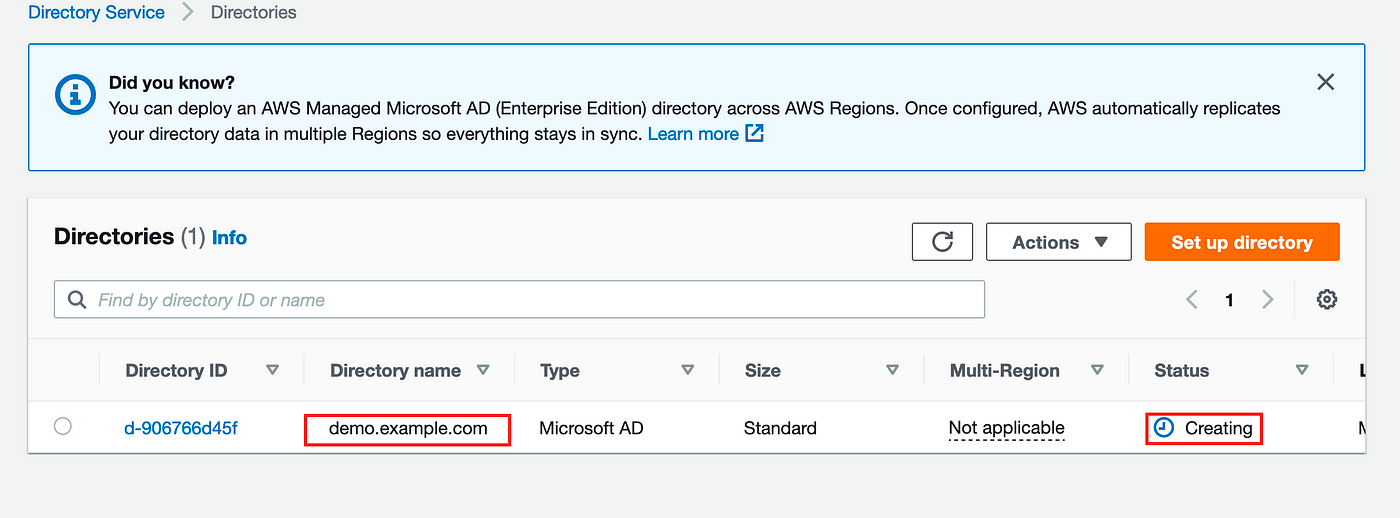
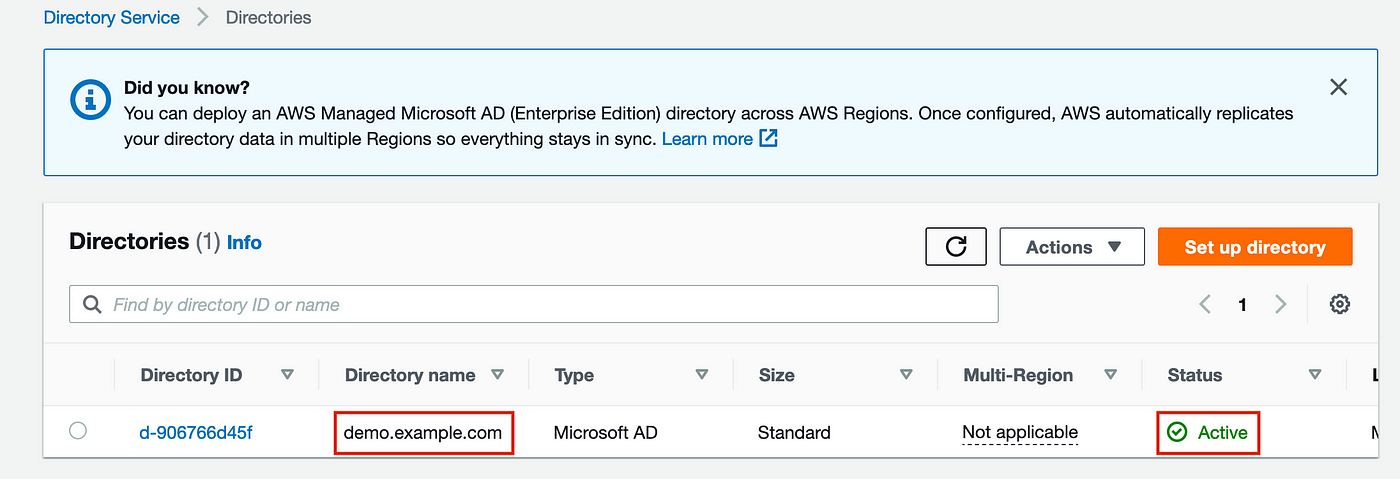
You will now see a screen similar to below with status ‘Active’:
Refer linked documents to create an EC2 instance, join it to domain and create Active Directory user.
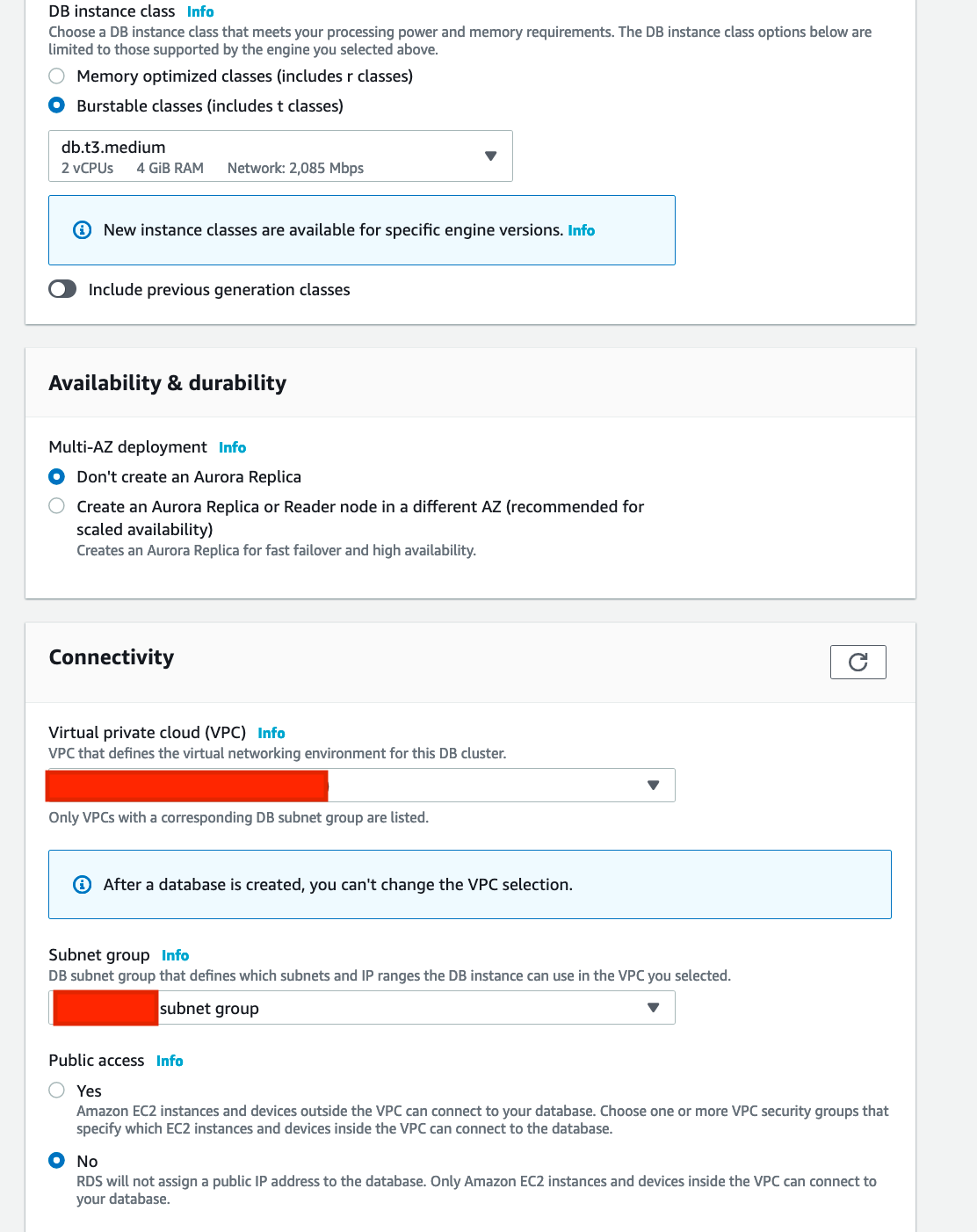
Create RDS/ Aurora PSQL instance and add Kerberos authentication:
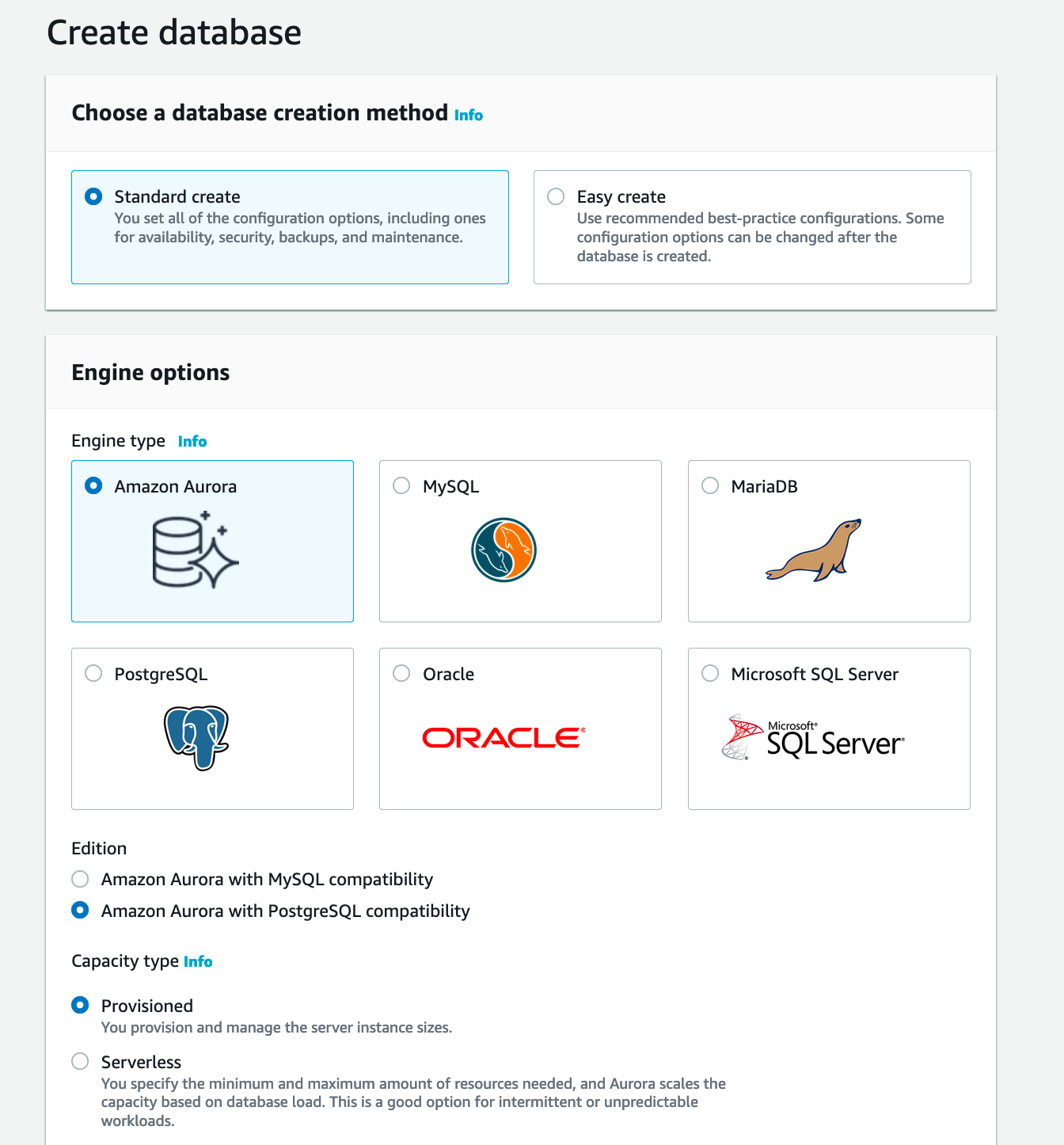
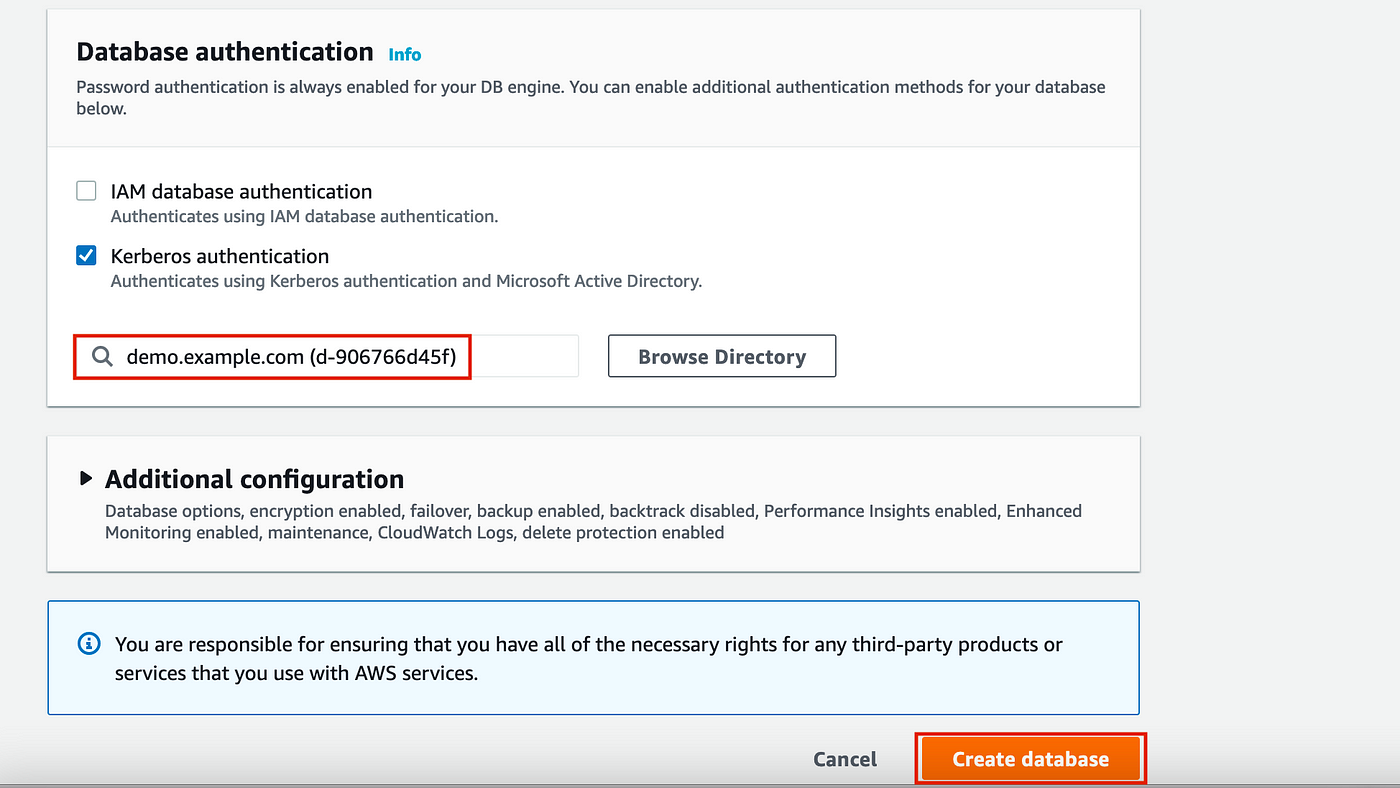
For Database authentication select Kerberos and browse for previously created directory:
Configure Krb5.conf for Ubuntu/Mac:
Install psql client and krb5-user
## Ubuntusudo apt-get update
sudo apt-get install krb5-user
sudo apt-get install postgresql-client
## MACbrew doctor
brew update
brew install krb5
brew install libpq
brew link --force libpq
Configuring krb5.conf as below:
## UBUNTU/MAC
sudo vi /etc/krb5.conf
Copy below contents into the file:
[libdefaults]
default_realm = EXAMPLE.COM
default_cc_type = FILE
default_ccache_name = FILE:/tmp/krb5cc_%{uid}
[realms]
DEMO.EXAMPLE.COM = {
kdc = demo.example.com
admin_server = demo.example.com
}
[domain_realm]
.demo.example.com = DEMO.EXAMPLE.COM
demo.example.com = DEMO.EXAMPLE.COM
Create Kerberos authentication PostgreSQL logins/
Login to RDS with master username/password and create Kerberos/AD logins as below:
CREATE USER "username@DEMO.EXAMPLE.COM" WITH LOGIN;
GRANT rds_ad TO "username@DEMO.EXAMPLE.COM";
Connect to AWS Aurora/ RDS PSQL Server using Kerberos authentication:
## MAC/Ubuntu
kinit username ### this will ask you for password and creates ticket
klist -a ### shows you all expire/active tickets
psql -U username@DEMO.EXAMPLE.COM -d postgres -h database-1.cluster-xxxxxxxxxxxxxx.us-east-1.rds.amazonaws.com -p 5432
### Above command should give you successful connection to database
Conclusion
We successfully configured Kerberos authentication for Aurora/RDS PSQL, which provides significant data security and auditing advantages for organizations. By implementing Kerberos, we ensure that only authenticated users can access the database, thereby enhancing the security of sensitive data. This setup allows for secure, encrypted connections and helps maintain compliance with various security standards. Additionally, Kerberos authentication supports detailed auditing capabilities, enabling organizations to track and log user access and activities within the database. This level of security and accountability is crucial for organizations that handle sensitive information and need to adhere to strict data protection regulations.
Stay Tuned!
Be sure to follow and subscribe for more updates and upcoming blogs.
Subscribe to my newsletter
Read articles from Rahul wath directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rahul wath
Rahul wath
An experienced DevOps Engineer understands the integration of operations and development in order to deliver code to customers quickly. Has Cloud and monitoring process experience, as well as DevOps development in Windows, Mac, and Linux systems.