Third-Party Data Sharing and Supply Chain Risks: What You Must Know in 2025
 Davies Parker
Davies Parker“T**hird-party vendors can drive business growth — but they can also be the weakest link in your security chain.”
In today’s interconnected business environment, third-party relationships are essential for delivering exceptional customer service, expanding global operations, and improving internal efficiency. From CRM platforms to logistics providers, outsourcing is no longer a luxury — it’s a necessity.
However, when sensitive data changes hands or flows through a supply chain, it introduces a web of potential risks. A single vulnerability in one of your vendors can disrupt operations, cause regulatory fines, or even destroy customer trust.
So, how do you strike the right balance between leveraging third-party services and securing your business?
Let’s explore third-party data sharing, the associated supply chain risks, and proven strategies to mitigate them effectively.
🧾 What Is Third-Party Data Sharing?
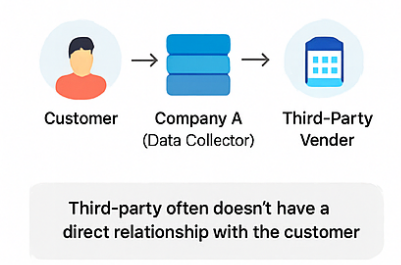
Third-party data sharing refers to the process of transferring customer or proprietary data from the original data collector (usually your organization) to an external party (a vendor or partner) for business-related purposes.
✅ Common examples include:
CRM tools like HubSpot or Salesforce
Marketing automation platforms
Cloud-based data storage providers
Recruiting firms and outsourcing agencies
Logistics and supply chain vendors
While this data exchange streamlines operations, it also exposes businesses to risks — especially when those third parties are not held to the same data security and compliance standards.
⚠️ Major Risks in Third-Party Data Sharing
Let’s break down the most significant threats businesses face when sharing data with external vendors or service providers.

1. 💡 Competency Risk
Not all vendors are created equal. If a recruitment agency, for example, does not align with your hiring standards, it might deliver misaligned candidate profiles. While technically considered “data,” this information could be inaccurate or unusable — resulting in wasted time, poor decisions, and downstream inefficiencies.
2. 🔐 Data Breaches
The most notorious third-party risk. If a vendor is hacked, your data is compromised — even if your internal systems are secure.
Case in point:
In 2021, Volkswagen Group of America suffered a massive breach due to a vendor storing unencrypted customer data online. This leak exposed loan numbers, emails, and even social security numbers of 97% of Audi customers.
Impact:
Reputational damage
Legal repercussions
Loss of customer trust
Regulatory penalties
3. 🛠️ Loss of Data Control
Vendors serving hundreds of clients manage vast amounts of data. This makes it harder to:
Control access rights
Monitor data usage
Ensure consistent privacy protocols
Without proper segmentation and visibility, even a minor misconfiguration could result in data leaks or unauthorized access.
🌐 Supply Chain Risks Amplified in a Globalized World
As companies increasingly outsource to international partners, third-party risks extend beyond just data.
🚨 Key Supply Chain Risks:
Cybersecurity vulnerabilities in third-party systems
Regulatory compliance gaps across jurisdictions
Operational disruptions from weather, politics, or pandemics
Data privacy violations under laws like GDPR or CCPA
Financial instability of suppliers causing fulfillment delays
🔎 How to Identify & Assess Third-Party Risks
Before you can mitigate risks, you must identify and evaluate them. Here’s a proven framework:
✅ 1. Vendor Due Diligence Checklist
Before onboarding any third party:
Review cybersecurity posture (firewalls, encryption, incident response)
Check data protection and privacy policies
Examine historical compliance violations
Assess financial health and credit score
Conduct on-site audits or third-party assessments
✅ 2. Compliance Verification
Ensure your vendors comply with:
International laws (e.g., GDPR, DORA)
Regional laws (e.g., CCPA, UAE PDPL, Saudi PDPL)
Industry standards (e.g., ISO 27001, HIPAA, SOC 2)
💡 Tip: Create a compliance scorecard to rank each vendor’s risk level.
✅ 3. Cybersecurity Risk Assessment
Ask these key questions:
Do vendors encrypt data at rest and in transit?
Do they regularly test for vulnerabilities?
How quickly can they detect and respond to cyber threats?
Are they backed by cyber insurance?
🔄 Regularly update assessments — especially after breaches or major system changes.
✅ 4. Operational Continuity Analysis
Determine:
How vendors handle natural disasters, strikes, or geopolitical events
Their reliance on single points of failure
Backup strategies and disaster recovery plans
🚚 Example: A supplier relying on one shipping partner may be more vulnerable than one with three fallback logistics providers.
🛡️ Strategies to Mitigate Third-Party Risks
Now that you’ve assessed the risks, here’s how to reduce them:
🔁 1. Establish Clear Data Sharing Agreements
Use Data Processing Agreements (DPAs) and SLAs
Define roles (controller vs. processor)
Limit data access to only what’s necessary
🔒 2. Implement Zero Trust Architecture
Adopt a “never trust, always verify” model across your tech stack. Control:
Who accesses your data
When and why they access it
From which devices and locations
🧪 3. Continuous Monitoring
Use tools that offer real-time monitoring of third-party activity. Track:
Data movement
Access logs
Anomalies or behavioral shifts
🔁 Integrate third-party risk management (TPRM) tools with your SIEM or GRC platform.
👨🏫 4. Educate & Train Internally
Train employees on recognizing phishing scams and unsafe third-party tools. Human error often opens the door to vendor-related attacks.
📉 5. Limit Vendor Overload
Avoid depending on too many vendors. Streamlining your vendor list reduces your risk surface area.
📌 Final Thoughts: Trust, but Verify
Third-party vendors play an essential role in modern business. From cloud services to recruitment partners, they help streamline operations and enhance customer experiences.
But don’t mistake convenience for security.
By establishing a robust third-party risk management program, conducting regular audits, and building strong compliance protocols, your organization can benefit from outsourcing — without sacrificing data integrity or customer trust.
Thank you for reading until the end. Before you go:
Subscribe to my newsletter
Read articles from Davies Parker directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Davies Parker
Davies Parker
Tsaaro is India's leading security & privacy consulting company, enable orgnaizations to take charge of their data privacy and cyber security compliance, developing a strategic and tactical plan for best practices.