DDoS Attack & Sword Of Blackhole Routing
 Shivam (Anirudh) Nandy
Shivam (Anirudh) Nandy
In a single line - “If you can’t save the castle, burn the gate”, that’s blackhole routing in a nutshell
DDoS Problem We All Hate
In the new world of digital infrastructure, DDoS (Distributed Denial of Service) attack are the the digital equivalent of a crowd barging your gate. It can be anything starting from a kid testing a botnet which he bought from him friends to state sponsored takedown campaigns, the goal is very simple flood the system until it chokes out.
The nightmare isn’t just in the volume, but it is in the unpredictability. One moment your production is running smooth as butter, and in the next moment your load balancer is crying for help. And in these moments of chaos, some dev teams turn to brute-force mitigation tactic which is known as Blackhole Routing.
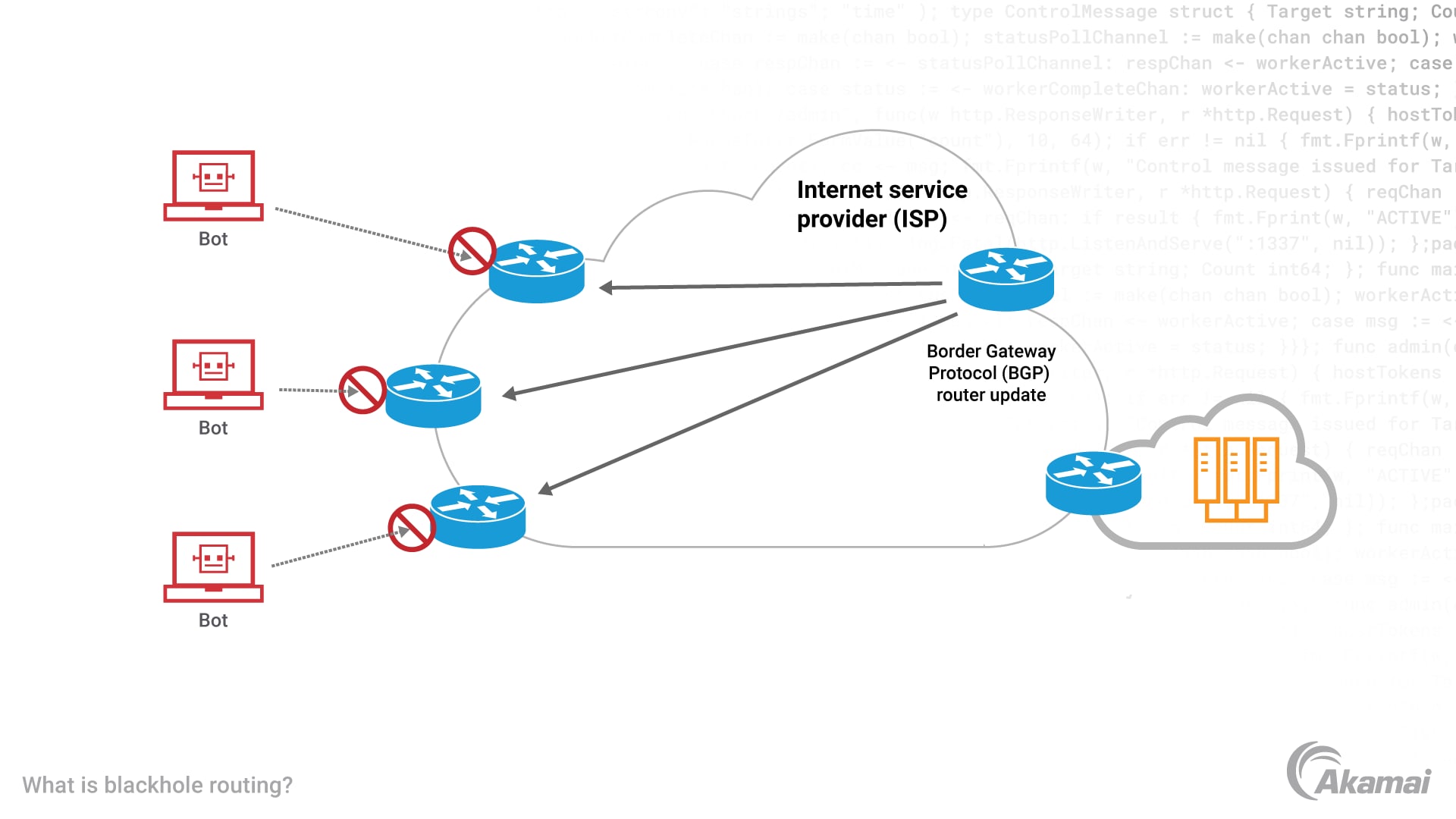
What is Blackhole Routing?
Blackhole Routing (aka null routing) is what happens when you decide to sacrifice the victim to save the village.
So, It is a method where you reroute all traffic, meant for the attacked IP address to a non-existent destination, effectively dropping all packets on the ground. It doesn’t matter if it is malicious or legitimate.
In very clear words, it doesn’t clean your traffic. it doesn’t scrub it. It doesn’t filter it. it simply kills it. Every bit of it.
Let me wear my physicist hat and say this ;
You’ve turned your server into Schrödinger’s host: technically up, but practically dead.
Why use it?
Simple dude, It’s fast and simple. Because sometimes, it’s the only thing between your upstream provider and a full-blown network collapse.
When your cloud provider or ISP sees one of your IPs eating 10Gbps of UDP junk traffic, they can null-route that IP at the edge. Such that, suddenly the rest of your network breathes again. Business resumes except for whatever was on that IP. It’s not ideal. It’s not elegant. But it works.
The RTBH (Remote Triggered Black Hole) Upgrade - But Still Meh
Remote Triggered Black Hole (RTBH) routing adds some automation and BGP (Border Gateway Protocol) magic to the mix. You tag an IP (via routing protocols) for blackholing, and edge routers handle the drop closer to the attack source.
It’s tactical. It’s fast. But it’s still like dropping a nuclear bomb to the specific target IP. So now, your blackholing decisions are faster, but not smarter.
Let there be Collateral Damage
Let’s not pretend this is a good long-term solution. Blackhole routing is a temporary containment, not a cure, a method that kills availability for the attacked system. A decision made often under pressure, with little time for precision.
It also assumes that losing one service temporarily is better than losing the whole network which is sometimes true, but always painful.
If you’re building high-availability systems, you’d better have failovers, redundant nodes, and cloud-level BGP smarts to make sure your business doesn’t hinge on a single blackholed IP.
So What Is The Solution?
Relying on blackhole routing is equivalent to call the fire-department after your house has been burnt down. It’s wiser to have DDoS Protection Plan. There are numerous tools (detailed blogs in the future) like Cloudflare, AWS Shield, Akamai or dedicated DDoS mitigation appliances.
You can also deploy BGP (Border Gateway Protocol) anycast networks for distribution and mitigation.
Monitoring your network in real-time with tools that can alert and route dynamically. For example, FastNetMon, ntopng or you can also write your custom BGP Automation Scripts.
Educate, Blackhole Routing is a tool, Not A Solution or Strategy
One ISP, One Route, Global Chaos: How YouTube Vanished in 2008
Back in 2008, YouTube crashed for several hours globally and the perpetrator was a blackhole routing blunder by Pakistan Telecom. Here's what went down: The government of Pakistan wished to censor a YouTube video containing a provocative Dutch cartoon of the Prophet Muhammad. As a result, Pakistan Telecom (a state-owned carrier) was ordered to censor YouTube nationwide.
To accomplish this, they utilized blackhole routing basically creating a false route that would eat up all traffic destined for YouTube. But it all went off the rails quickly.
Rather than keeping that false route within Pakistan, they somehow ended up announcing it to the entire Internet via something called BGP (Border Gateway Protocol), which we discussed in the above section, an implementation that informs the rest of the world how to reach certain places on the web. So essentially, Pakistan informed global internet providers:
"Hello, YouTube? Yes, it here with us." Consequently, YouTube traffic from users across the globe began flowing directly into a digital blackhole.
Fortunately, YouTube's networking group was perceptive enough to realize something was amiss and redirect traffic after a few hours. But this episode became the ultimate lesson plan for why blackhole routing, when improperly performed, can bring on enormous, unintended outages way beyond its original intent.
Conclusion
Blackhole routing isn't smart, but sometimes smartness is a luxury you can't afford. When you’re under siege, and latency is climbing, the blackhole is a big red button that says “please make it fucking stop.”
But it’s a button that drops your service into oblivion. If you’re serious about uptime, blackholing should be your last resort, not your go-to move. Because the only thing worse than getting hit with a DDoS is nuking your own infrastructure in response.
References
Cloudflare: DDoS Blackhole Routing Explained
A beginner-friendly breakdown of what blackhole routing is and how it works during DDoS attacks.Imperva: What Is Blackholing?
Detailed overview of blackhole routing as a DDoS mitigation technique, including pros, cons, and alternatives.Noction: BGP Blackhole Community and Best Practices
A deep dive into using BGP for blackholing, with community tags and automation strategies for advanced network operators.
Subscribe to my newsletter
Read articles from Shivam (Anirudh) Nandy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shivam (Anirudh) Nandy
Shivam (Anirudh) Nandy
I break things. A lot. But I fix them even better. I live and breathe open source, especially when it comes to scaling with Kubernetes, pushing the frontiers of Artificial Intelligence, and getting my hands dirty with system-level programming. My journey started deep in Theoretical and Advanced Mathematical Physics, because I couldn’t resist understanding what really happens inside the "brain" of a neural network — spoiler: it’s just math, but it feels like magic. Along the way, I developed an unhealthy obsession with database optimization, squeezing performance like my life depends on it. And if there’s one language that truly speaks to my soul, it’s RUSSSSTTTT — yes, I scream it like that because I love it that much. And of course, I fuel all of this with loud, unapologetic doses of Bengali rock music. It's the perfect background to break things fast, build them better, and maybe scare my neighbors a little.