CVE-2025-31324 Zero Day Analysis
 Rishi
RishiOverview
CVE-2025-31324 is a critical zero-day vulnerability affecting SAP NetWeaver Visual Composer, a component used for developing enterprise applications within the SAP NetWeaver platform. Discovered by ReliaQuest and disclosed by SAP on April 24, 2025, this vulnerability carries a maximum CVSS v3.1 score of 10.0, indicating its severe risk. It allows unauthenticated attackers to upload malicious files, potentially leading to full system compromise. The flaw has been actively exploited in the wild since at least March 27, 2025, targeting organizations globally, particularly in manufacturing and critical infrastructure sectors.
Vulnerability Details
Type: Unrestricted File Upload
Affected Component: SAP NetWeaver Visual Composer
Affected Versions: SAP NetWeaver 7.xx versions
Affected endpoint:
/developmentserver/metadatauploader
Detection
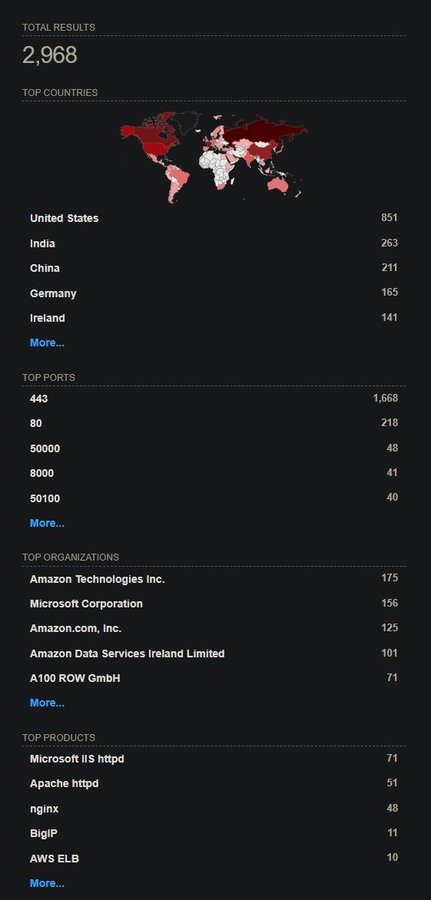
From looking at Shodan I discovered 2,968 devices exposed to the internet as of April 25th 2025 using this query:
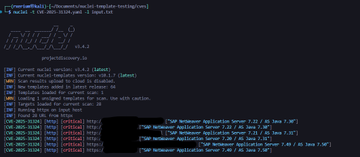
I decied to create a Nuclei Template to detect for this vulnerability, by being able to examine server headers, I was able to determine whether or not a host was vulnerable to CVE-2025-31324:
Below is the request, matchers and extractors used in the Nuclei template:
http:
- method: GET
path:
- "{{BaseURL}}"
redirects: true
max-redirects: 2
matchers-condition: and
matchers:
- type: word
part: header
words:
- "SAP NetWeaver Application Server"
condition: or
case-insensitive: true
- type: regex
part: header
name: version-check
regex:
- (?i)SAP NetWeaver Application Server 7\.(0[0-9]|[1-4][0-9]|50)(\b|[^0-9])
extractors:
- type: kval
part: header
kval:
The template performs a HTTP GET request to the target's base URL and examines the response headers to identify SAP NetWeaver Application Server instances
The Nuclei template can be found here if you would like to run tests against your own infrastructure at scale.
Mitigation and Remediation
Patching involves applying SAP Security Note #3594142, which includes patches for affected SAP NetWeaver versions. The updated note (v18, released May 1, 2025) extends support to earlier service packs.
For unsupported versions (e.g., older NetWeaver Java systems), upgrade to a supported version or apply workarounds from SAP Note #3593336, such as disabling the Metadata Uploader endpoint.
Workarounds
Restrict external access to the
/developmentserver/metadatauploaderendpoint.Check for the presence of the VISUAL COMPOSER FRAMEWORK component via system info (http://host:port/nwa/sysinfo) and disable it if unused.
Subscribe to my newsletter
Read articles from Rishi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by