🚀 Mastering Nuclei — The Ultimate Tool for Web Vulnerability Scanning & Bug Bounties
 Shahabaj Khan
Shahabaj Khan
In the modern bug bounty and offensive security landscape, automation is the key to speed, scale, and success. Among the many tools available, Nuclei by ProjectDiscovery has rapidly become one of the most powerful and widely adopted scanners for web vulnerability hunting.
In this blog, I’ll break down:
✅ What Nuclei is
✅ Why it’s essential for recon and vulnerability scanning
✅ How to install and use it
✅ Types of Nuclei templates
✅ Pro tips, settings, and real-world examples
✅ Conclusion for bug bounty pros
🔍 What is Nuclei?
Nuclei is a fast, customizable vulnerability scanner developed by ProjectDiscovery.io. It uses YAML-based templates to check for known vulnerabilities, misconfigurations, exposed secrets, CVEs, and more across web assets.
Unlike generic scanners, Nuclei is modular, scalable, and tailored for bug bounty automation and offensive security workflows.
🧠 Why Nuclei?
⚡ Blazing fast scanning (Go-based)
📦 Thousands of public templates (community-driven)
🔧 Fully customizable rules (write your own detection logic)
📊 Easy integration into recon pipelines
💥 Supports multiple protocols: HTTP, DNS, TCP, SSL, File, Headless browser
✅ Great for finding low-hanging fruit and known CVEs at scale*.*
🛠️ How to Install Nuclei
Option 1: Using Go
go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latest
Ensure Go is installed and $GOPATH/bin is in your PATH.
Option 2: Using Prebuilt Binary
wget https://github.com/projectdiscovery/nuclei/releases/latest/download/nuclei-linux-amd64.zip
unzip nuclei-linux-amd64.zip
chmod +x nuclei
./nuclei -version
🔄 Updating Nuclei Templates
Nuclei uses YAML templates to define vulnerabilities. These templates are constantly updated.
nuclei -update-templates
Default path: ~/.local/nuclei-templates or $HOME/nuclei-templates
🚀 Basic Usage
Scan a Single URL:
nuclei -u https://target.com
Scan a List of URLs:
nuclei -l urls.txt
Use Specific Template:
nuclei -u https://target.com -t cves/CVE-2021-41773.yaml
Scan with All Templates:
nuclei -u https://target.com -t ~/nuclei-templates/
🧩 Types of Templates
Nuclei templates are categorized for specific testing needs:

You can also write your own custom templates for private vulnerabilities!
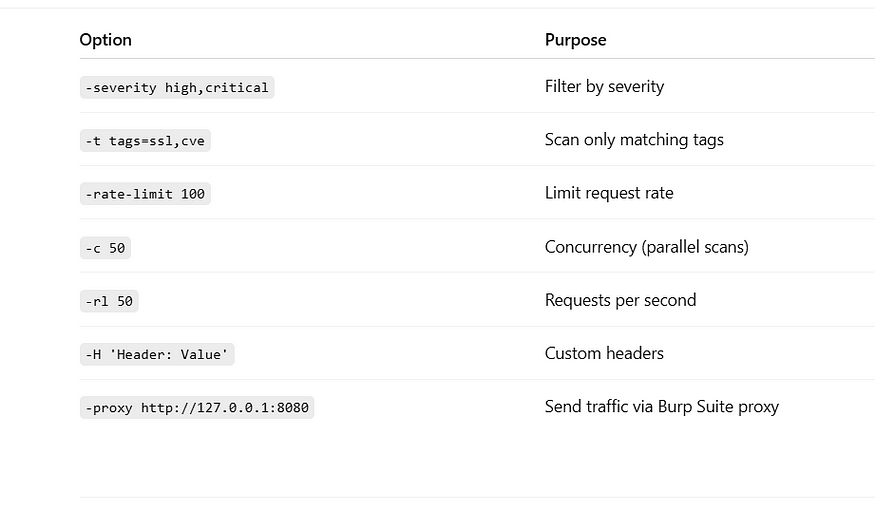
⚙️ Useful Settings & Flags
📦 Example: Finding Git Exposure
nuclei -u https://target.com -t files/git-config.yaml
Output:
[git-config-exposure] [critical] https://target.com/.git/config
🪓 Follow up with manual exploitation (dump repo, secrets, credentials).
🛡️ Use in Bug Bounty Recon Workflow
Collect subdomains using
subfinder,assetfinder, oramassProve which ones are live with
httpxRun Nuclei:
subfinder -d target.com | httpx -silent | nuclei -l - -o results.txt📖 Writing Custom Templates
id: my-custom-check info: name: Custom Admin Panel Finder author: shahabaj severity: low tags: custom requests: - method: GET path: - "{{BaseURL}}/admin" matchers: - type: status status:Save it as
custom-admin.yaml, and run:nuclei -u https://target.com -t custom-admin.yaml🧠 Pro Tips
🎯 Prioritize
criticalandhighseverity templates🔄 Update templates weekly
🔌 Integrate into CI/CD or recon automation scripts
🧪 Combine with Burp, Gf patterns, JSFinder, LinkFinder
📤 Export results in JSON/CSV for reporting
Resources
Official Templates: https://github.com/projectdiscovery/nuclei-templates
Docs & Wiki: https://nuclei.projectdiscovery.io
✅ Conclusion
Nuclei is not just a scanner — it’s an offensive framework. Whether you’re scanning for CVEs, detecting exposed secrets, or fuzzing APIs, it can automate large-scale vulnerability discovery in minutes.
For bug bounty hunters, integrating Nuclei into your recon process can give you the edge over competitors — and help you identify juicy bounties faster.
- 💬 Have you used Nuclei in your bug bounty workflow? Share your success stories in the comments or reach out if you want help customizing templates!
Subscribe to my newsletter
Read articles from Shahabaj Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shahabaj Khan
Shahabaj Khan
I am Shahabaj Khan, a Certified Ethical Hacker (CEH) and Electronics & Telecommunication Engineer with strong expertise in cybersecurity, penetration testing, and mobile application development. My experience spans across vulnerability assessment, SAST/DAST methodologies, and cloud, API, and mobile security. I’ve gained practical experience through internships and projects, focusing on real-world security scenarios and modern threat landscapes. I'm also creating educational content on my YouTube channel eHackopedia, covering cybersecurity concepts, tools, and tutorials to empower aspiring professionals.