🛡️ How to Recover a Hacked Social Media Account: A Complete Guide by a Cybersecurity Investigator
 Shahabaj Khan
Shahabaj Khan
🔎 Introduction
In today’s digital world, your social media identity is your online asset. Whether it’s Facebook, Instagram, LinkedIn, Snapchat, or X (Twitter), a hacked account can not only disrupt your social presence but also lead to serious privacy breaches, scams, or reputation loss. This guide is crafted for everyone — from non-tech users to ethical hackers — to understand how to detect, recover, and secure a compromised social media account, using both free tools and expert techniques.
🚨 Signs Your Social Media Account Has Been Hacked
You are unexpectedly logged out.
Strange posts or DMs are sent from your account.
Your recovery email or phone number is changed.
Unknown login alerts from new devices or locations.
Friends report spam or phishing messages from you.
Your account is suspended or flagged for suspicious behavior.
🔐 Immediate Steps to Take If Your Account Is Hacked:
🔄 1. Attempt to Recover Using the Platform’s Official Tools
Platform Recovery Link
Facebookfacebook.com/hacked
Instagram”Need More Help?”
from login pageX (Twitter)twitter.com/forms/hacked Snapchatsupport.snapchat.com
LinkedInlinkedin.com/help/linkedin/ask/TS-NCI
🔄 2. Use “Forgot Password” and Access Backup Email/Phone
Check your inbox and spam folders for any login alert, password reset, or suspicious activity notifications.
⚙️ 3. Change Passwords Immediately
Use a strong and unique password for each platform. Example: eH@ck0pedia#2025!Secure.
✅ 4. Enable Two-Factor Authentication (2FA)
Prefer app-based 2FA (Authy, Google Authenticator) over SMS.
🧪 Advanced Recovery and Investigation Techniques (Ethical Hacker Tools)
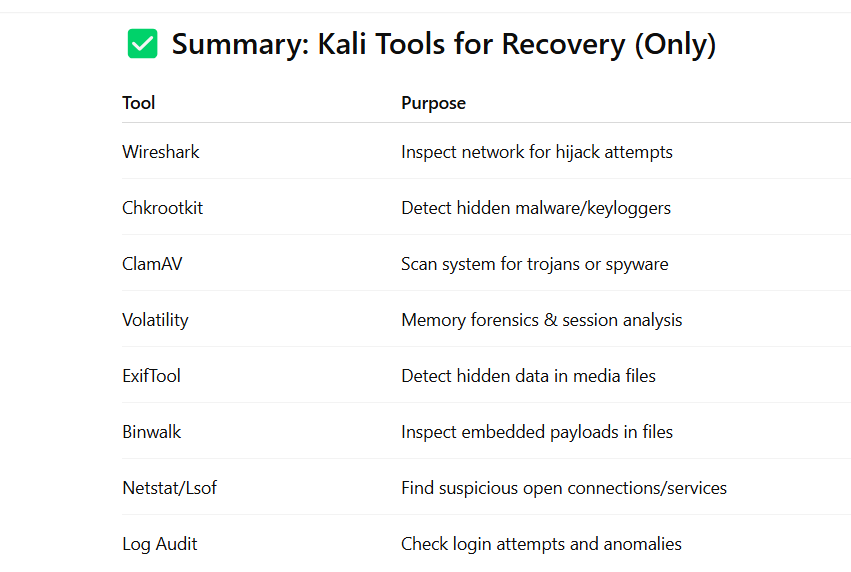
🛠️ Kali Linux Tools for Social Media Account Recovery & Forensics
These tools help you investigate how the account was compromised, remove malware or keyloggers, and restore secure access to the account or device.
🔎 1. Wireshark — Network Traffic Analyzer
Purpose: Analyze suspicious network connections that may indicate stolen session tokens, data exfiltration, or phishing attempts.
Use:
Detect outgoing traffic to suspicious domains.
Identify possible session hijacking attempts.
Command:
sudo wireshark
🧬 2. Chkrootkit — Rootkit Detection Tool
Purpose: Scan for rootkits that might be logging keystrokes or stealing credentials on your system.
- Install:
sudo apt install chkrootkit
Scan:
sudo chkrootkit
🦠 3. ClamAV — Antivirus and Malware Scanner
Purpose: Scan for malware or keyloggers that could have stolen social media credentials.
- Install:
sudo apt install clamav
sudo freshclam
Scan:
sudo clamscan -r /
🔐 4. Volatility Framework — Memory Forensics
Purpose: Analyze a memory dump to detect session hijacks, stored credentials, or credential-stealing malware.
Use:
Extract active sessions, browser data, clipboard content.
Useful for investigating compromised machines.
Example:
volatility -f memory.img --profile=Win10x64_19041 pslist
🧾 5. ExifTool — Metadata Analysis
Purpose: Review media files (sent over chats or DMs) for hidden links or malicious redirects used in social engineering attacks.
- Command:
exiftool suspicious_image.jpg
🔍 6. Binwalk — File Analysis
Purpose: Unpack any malicious file (e.g., browser extensions or downloaded media) used to steal social media credentials.
- Command:
binwalk suspect_file.zip
🧠 7. Log File Auditing (Manual)
Purpose: Use built-in Linux logs to identify suspicious login attempts or credential exfiltration on your system.
- Commands:
cat /var/log/auth.log | grep ssh
grep -i "login" /var/log/syslog
📤 8. Netstat + Lsof — Identify Connections & Open Files
Purpose: See if any suspicious service is running that could be exfiltrating data to an attacker.
- Commands:
sudo netstat -tulpn
sudo lsof -i
📁 9. Browser Session & Cookie Recovery (Manual from Disk)
Purpose: Recover saved sessions/cookies for manual analysis or clean-up.
Browser Paths:
Chrome:
~/.config/google-chrome/Default/CookiesFirefox:
~/.mozilla/firefox/*.default-release/cookies.sqlite
You can use SQLite tools to inspect and delete suspicious cookies or sessions.
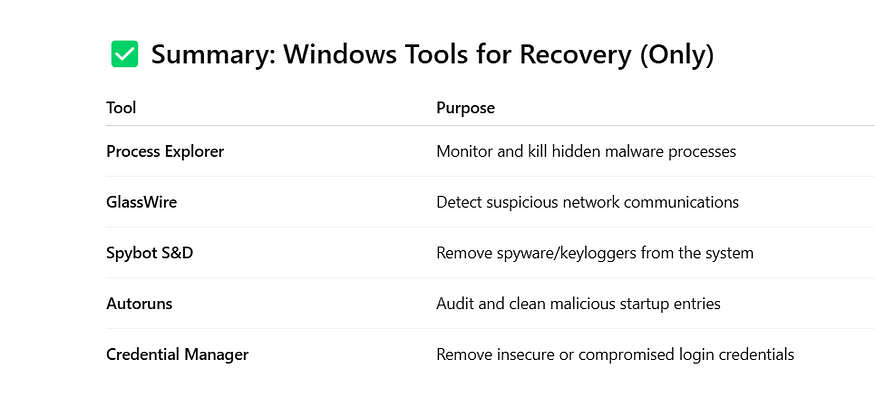
🪟 Windows Tools for Social Media Account Recovery & Security (Free)
These tools help you investigate compromised accounts, remove hidden malware/keyloggers, and restore secure system behavior — all without simulating attacks.
🧠 1. Process Explorer (by Sysinternals)
Purpose: Identify malicious or unauthorized processes running in the background that might steal credentials or sessions.
🔹 How to Use:
Download: Process Explorer
Run as Administrator.
Look for unknown or unsigned processes.
Right-click → Properties → Check network activity or strings.
🌐 2. GlassWire (Free Edition)
Purpose: Monitor real-time network connections for suspicious outbound traffic that could be sending stolen session data.
🔹 How to Use:
Download: GlassWire
Track bandwidth spikes, unusual connections.
Check “Alerts” tab for unusual app behavior.
Block suspicious programs or IPs.
🕵️ 3. Spybot Search & Destroy
Purpose: Scan for keyloggers, spyware, and tracking cookies that may steal credentials from browsers and apps.
🔹 How to Use:
Download: Spybot Free Edition
Run full scan.
Clean all detected threats.
Use Immunization feature for protection.
⚙️ 4. Autoruns (by Sysinternals)
Purpose: Investigate and disable suspicious programs or scripts that start automatically with Windows (e.g., persistent keyloggers).
🔹 How to Use:
Download: Autoruns
Run as Admin.
Review entries under “Logon” and “Scheduled Tasks.”
Uncheck unknown or unsigned entries.
🔐 5. Credential Manager Audit
Purpose: Clean up and re-secure saved passwords from browsers and Windows Credential Store that could have been compromised.
🔹 How to Use:
Open:
Control Panel > User Accounts > Credential ManagerRemove saved entries for websites like Facebook, Instagram, Gmail, etc.
Re-login with fresh, strong passwords.
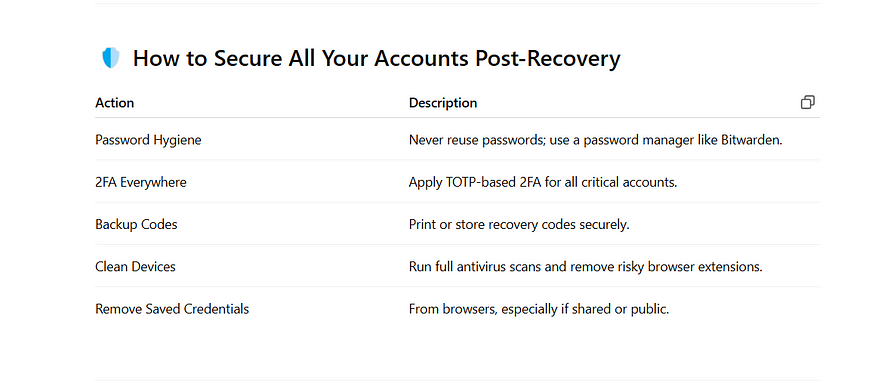
🔍 Forensic Steps to Trace the Hack
Login History — Check if login came from unknown IPs or geolocations.
Recovery Info Audit — Ensure phone numbers and backup emails haven’t changed.
App Permissions — Revoke access to unknown third-party apps.
Browser History — Check if phishing sites were accessed.
Email Logs — Look for unauthorized recovery emails or password reset attempts.
💬 Final Thoughts
Recovering a hacked social media account is not just about resetting a password — it’s about understanding the attack vector, securing your environment, and staying vigilant. Ethical hackers and investigators must think like attackers but act with integrity. This guide equips you with the tools and mindset to protect yourself and others.
✍️ About the Author
Shahabaj Khan is a Certified Ethical Hacker, cybersecurity trainer, cybercrime investigator, and founder of eHackopedia. With a passion for cyber hygiene awareness and practical hacking defense, he helps people reclaim their digital identities and teaches others how to protect theirs.
🔚 Conclusion
Recovering a hacked social media account requires a forensic mindset — you need to detect the root cause, clean the infected system, and secure future access. Whether you use Kali Linux for forensic-level investigation or Windows tools for detection and cleanup, the goal is to restore access and harden your security posture.
⚠️ Important Disclaimer
This article is intended solely for educational and awareness purposes.*If you are not confident in using these tools or lack technical knowledge, it is highly recommended to **consult a certified cybersecurity expert or cybercrime investigation agency*. Mishandling these tools or your system settings may result in *data loss or further compromise*. Always work on a *backup or non-critical system** when using forensic tools.*
Subscribe to my newsletter
Read articles from Shahabaj Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shahabaj Khan
Shahabaj Khan
I am Shahabaj Khan, a Certified Ethical Hacker (CEH) and Electronics & Telecommunication Engineer with strong expertise in cybersecurity, penetration testing, and mobile application development. My experience spans across vulnerability assessment, SAST/DAST methodologies, and cloud, API, and mobile security. I’ve gained practical experience through internships and projects, focusing on real-world security scenarios and modern threat landscapes. I'm also creating educational content on my YouTube channel eHackopedia, covering cybersecurity concepts, tools, and tutorials to empower aspiring professionals.