Quantum Time Bomb: When Encryption Stops Working
 Harshit Narang
Harshit Narang
The Clock is Ticking And Your Data Isn’t Ready
Quantum computers aren’t just lab experiments anymore. They’re real, evolving faster than a ‘Brainrot trend’ , and primed to detonate the encryption protecting almost everything you do online. Imagine hackers in 2035 cracking today’s encrypted data, which can include your bank details, medical records, and that cringe google search for “why do cats ignore me when I pspsps at them?”, as easily as popping a balloon.
This is not a Mission: Impossible movie plot, it’s the quantum time bomb lurking beneath our digital lives. So here is how it works, why your data is at risk, and how we’re defusing it - with lasers, math mazes, and a sprinkle of chaos.

Quantum Computing: The Atomic Clock on Espresso (and Why you should care)
Classical computers are like sundials, steady but slow. Quantum computers? They’re atomic clocks on espresso, with a side of Red Bull.
Classical bits are light switches: 0 (off) or 1 (on).
Qubits are like dimmer switches - thanks to superposition, they can be both 0 and 1, or anything in between. It’s like getting out of the labyrinth by exploring every path at once instead of step by step.
Entanglement: Einstein’s “Spooky” BFFs
- If two qubits are entangled, changing one instantly affects the other - even if they’re on opposite sides of the galaxy. Think of it as twin librarians who finish each other’s sentences… and shelves.
Why Quantum Isn’t Mainstream (Yet):
Qubits are like divas: they demand near‑absolute‑zero temperatures and complete isolation from vibrations, stray light, and even Wi‑Fi signals to prevent decoherence. Error correction, meanwhile, is the real nightmare—like herding a bunch of overly caffeinated cats.
Real-World Quantum Players:
IBM’s Quantum Eagle: Handles 127 qubits but still makes mistakes.
D-Wave’s Annealers: Solve optimization problems but can’t crack RSA… yet.
Why This Matters
Shor’s Algorithm - a quantum cheat code - could crack RSA encryption (the lock guarding 90% of the internet) in hours. For classical computers, it’s like running a marathon barefoot but for quantum computers it’s a hoverboard sprint.
Analogy: RSA is a timed safe whereas quantum computers are lockpicks with a stopwatch and a PhD in chaos theory.
Real-World Stakes:
The NSA recommends preparing for PQC by 2030.
China claims it’s built a quantum computer that cracks RSA-2048 in minutes. Yikes.
The EU’s Quantum Flagship Program is investing €1 billion to deploy quantum-safe infrastructure by 2030, prioritizing defense and healthcare.
JPMorgan Chase is stress-testing PQC to secure $10+ trillion in daily transactions, fearing quantum-driven financial chaos.
Ransomware groups like LockBit are stockpiling encrypted data, betting on future quantum paydays.
RSA’s Rise and Fall: From Hero to Zero
A Brief History of RSA:
In 1977, three MIT nerds (Rivest, Shamir, Adleman) invented RSA, turning encryption into a math puzzle:
Pick two massive primes (like 1,000-digit monsters).
Multiply them.
Security relies on one fact: Factoring that product back into primes is brutally hard for classical computers.
Prime Factorization 101:
Factoring primes is like reverse engineering a cake. If you bake 17 x 23 = 391, it’s easy. But if I give you 391 and ask for the original primes … well it’s game over for you. Now imagine the numbers are 600 digits long.
Why RSA Ruled the World:
It’s like hiding a needle in a haystack which is almost the size of Jupiter. Even the world’s fastest supercomputer would take 300 trillion years to crack RSA-2048.
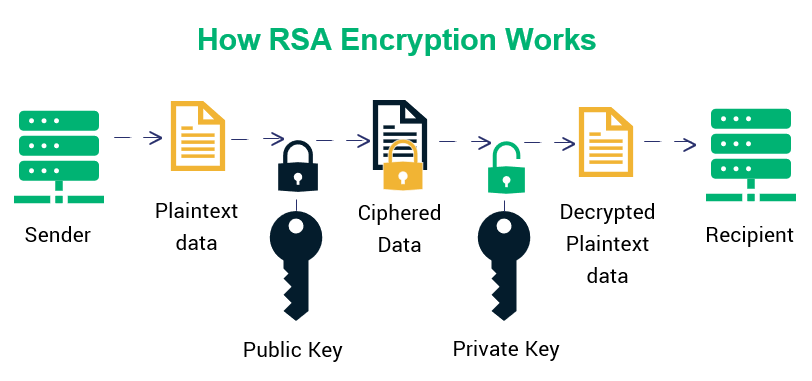
But Quantum computers couldn’t care less:
Shor’s Algorithm tests all possible factors at once using superposition. Imagine brute forcing a password by guessing every combination simultaneously.
Reality Check: RSA is like milk in the sun - already going bad. Quantum computing is the heatwave speeding it up.
Case in Point:
In 2022, Chinese researchers simulated breaking 2048-bit RSA. The fuse is now lit.
Harvest Now, Decrypt Later: The Heist of the Century
Hackers aren’t waiting for quantum tech - they’re hoarding encrypted data today. Your tax returns, corporate secrets, and that Spotify blend with your crush? All are sitting ducks in a digital storage locker.
Did You Know?
70% of organizations admit they can’t detect encrypted data theft (Ponemon Institute).
95% of web traffic is encrypted (Google Transparency Report).
How It Works:
Steal encrypted data (easy, since most traffic is encrypted).
Wait 5-10 years for quantum computers to mature.
Decrypt everything, from military intel to your middle-school blog-diary.
The Fallout? Digital Mayhem:
🔓 HTTPS/TLS: Secure websites become glass houses and even worse - your passwords added to rockyou2.txt .
💸 Blockchain: Crypto wallets? Emptied. NFTs? Repossessed by quantum-powered bots.
📜 Digital Signatures: Forged contracts, fake software updates, and literally counterfeit money.
Industry-Specific Chaos:
Finance: Banks could lose billions overnight if transaction histories are altered.
Healthcare: Your DNA data? Auctioned to the highest bidder.
Government: Diplomatic cables leaked, sparking geopolitical crises.
Worst thing that can happen: A hacker group leaks 2030’s decrypted data, revealing your “visionary leadership” speech was ChatGPTed.

Post-Quantum Cryptography: Cybersecurity’s Avengers (Explained for Beginners)
Meet PQC—the superhero squad of encryption. These algorithms make quantum computers rage-quit.
🌀 Lattice-Based Cryptography: Math Mazes in 500+ Dimensions
Imagine navigating a maze, but instead of 2D walls, you’re dodging obstacles in nearly 500 dimensions. Lattice-based cryptography uses grids (lattices) in mind-bending dimensions to hide data. Quantum computers struggle here because solving these mazes requires guessing all paths at once - something even their multitasking qubits have a skill issue with. Why is it cool: Because it’s the backbone of algorithms like Kyber and powers privacy tools like secure messaging apps.
🔐 Hash-Based Signatures: Tamper-Proof Fingerprints
Hash-based signatures work like a wax seal for data. When you “sign” a document, it’s stamped with a unique hash - a fixed-length code (e.g., a random string like a3F9A2xZ). Tamper with the document? The hash changes completely and screams “FAKE!”
Drawback: They’re one-time use, like disposable glovesgr - eat for critical systems, clunky for Netflix binges.
📜 Code-Based Cryptography: Errors as Locks
This method borrows from error-correcting codes which means math is used to fix twisted texts. Imagine sending a message with intentional typos. Only someone with the “typo rulebook” (your private key) can decode it. Quantum computers hate this because finding errors in massive codes is like finding a single misspelled word in the Harry Potter novels written in Morse code.
📊 Multivariate Polynomials: Equations from Hell
These algorithms use systems of equations with hundreds of variables (e.g., x³y² + 4xy – 7z⁴ = 42). Solving them requires brute-forcing endless combinations - a nightmare even for quantum machines.
Real-world use: They’re niche but secure, like a vault guarded by a troop of kangaroos with boxing gloves.
⚡ Kyber & Dilithium: The Dynamic Duo, Explained
Kyber (Key Exchange):
Uses lattice math to securely share encryption keys.
Imagine whispering a password in a crowded room, but the password is hidden inside a 100D maze. Only your intended recipient has the map.
Used in: Google’s PQ-TLS experiments, VPNs.
Dilithium (Signatures):
Creates unforgeable signatures using lattices.
Think of it as a wax seal that explodes if tampered. Even quantum bots can’t fake it.
Used in: Software updates, legal e-signatures.
Why They’re Cool: They’re fast, efficient, and already being tested by tech giants.
🛡️ Hybrid Encryption: Double the Locks, Zero the Regrets
Hybrid encryption pairs RSA with PQC algorithms. Why?
Backward compatibility: Old systems still understand RSA.
Quantum-proofing: PQC adds a futuristic lock.
How it works: Your data is wrapped in both RSA and PQC encryption. Hackers need to crack both - like breaking into a bank vault while dodging laser sharks.
Real-World Use: AWS, Microsoft Azure, and Signal already use hybrid approaches
NIST’s PQC Timeline:
2016: Launched global competition for quantum-safe algorithms.
2022: Announced Kyber, Dilithium, and others as finalists.
2024: Final standards released
Who is NIST?
The National Institute of Standards and Technology (NIST) is the U.S. federal agency setting the gold standard for cybersecurity. Since 2016, they’ve spearheaded the global effort to vet and standardize quantum-resistant algorithms—because even hackers need rules to break.
Why This Squad Matters:
Protects WhatsApp chats, online banking, and even your smart fridge.
Guards critical infrastructure (power grids, self-driving cars) from quantum chaos.
Future-proofs IoT: Medical implants, connected cars, and yes, even your smart fridge.
The EU wants PQC in banks and hospitals by 2025 and even NASA’s testing it for space comms.
PQC is not just a shield, it’s more of a time machine which plans on securing today’s tech for tomorrow’s quantum world.

Your Countdown Checklist: How to Dodge the Quantum Apocalypse
1. Stay Calm (But Move Fast):
- Treat this like climate change: act now or drown later. Why? Transitioning to PQC takes years—start before the clock hits zero.
- Nudge Your IT Team:
“Hey, maybe peek at NIST’s PQC drafts?”
Tools to Try: Open Quantum Safe (free PQC libraries).
- Password Hygiene:
Use a password manager (cough Bitwarden cough).
“yourdogsname123” won’t save you and neither will “YourName@dob.”
- Learn the Basics:
YouTube “quantum for dummies.”
Free Course: Coursera’s Cryptography I.
- Advocate Loudly:
CEOs should brag about PQC in earnings calls.
Normies just tweet #QuantumProofMe on X.
Myth Busting: Quantum Nonsense vs. Reality
🔥 Myth: “Quantum computers exist already! My data’s gone!”
Reality: Today’s quantum machines are toddlers—cute but useless.
🔥 Myth: “PQC will slow the internet to dial-up.”
Reality: Modern PQC is faster than RSA.
🔥 Myth: “Only governments need to worry.”
Reality: If you use Wi-Fi or oxygen, you’re on the team.
Bonus Myth: “Quantum can break all encryption.”
Reality: Symmetric encryption (like AES-256) is quantum-resistant. PQC handles the rest.
What If We Do Nothing?
Imagine waking up in 2035 to:
Bankrupt banks: Quantum hackers drain accounts globally.
Fake news 2.0: Forged government documents spark wars.
Identity apocalypse: Your medical history is just waiting to be meme fodder.
This is not me trying to be fearmonger, it’s just simple math.
FAQ: Your Quantum Questions, Answered
Q: When will quantum computers crack RSA?
A: Although projections place the timeline between 2030 and 2050, hackers have already begun hoarding data.
Q: How soon will PQC be everywhere?
A: Though NIST's standards were introduced in 2024, full adoption may take 5–10 years.
Q: Is my iPhone safe?
A: For the time being, Apple is looking into implementing PQC in upcoming iOS updates.
Q: Can I buy a quantum computer?
A: At $15 million per D-Wave annealer, your dog’s influencer career might need to be on hold for a bit.
Final Countdown: Encryption Isn’t Dead—It’s Evolving
The quantum time bomb isn’t doom — it’s a wake-up call. We survived Y2K, spam, and Flash; now, PQC is the next chapter.
TL;DR:
Quantum will break RSA.
PQC is the fuse we’re cutting.
Your job? Stay alert, install upgrades, and for the love of the quantum gods stop reusing the same password for every social media account.

What’s Next?
For Tech Teams:
Start stress-testing Post-Quantum Cryptography (PQC) libraries like Open Quantum Safe—a free, open-source toolkit that lets you experiment with quantum-resistant algorithms today. Think of it as a “quantum-proof helmet” for your data. Dive into hybrid encryption prototypes, collaborate with frameworks like PQ-TLS, and join industry trials (Google and Cloudflare are already inviting beta testers). The goal? Ensure your systems aren’t caught with their encryption pants down when quantum arrives.
For Everyone Else:
Bookmark NIST’s PQC updates and follow tech giants like IBM and Microsoft, who blog about quantum readiness. Not a developer? No problem. Advocate for PQC adoption in your workplace (“Hey, shouldn’t our app be quantum-safe?”), and keep an eye on apps/software announcing PQC upgrades. Knowledge is power—and in this case, it’s also your underground bunker in case the quantum time bomb goes off.
Got questions? Drop them below. Conspiracy theories? We’ll bring popcorn. 🍿
Stay secure, stay snarky, and remember: Time’s ticking, but we’ve still got the codes. 🔒⏳
Subscribe to my newsletter
Read articles from Harshit Narang directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
