Secure Shell(SSH) — An Introduction
 NonStop io Technologies
NonStop io Technologies
SSH is a protocol that is predominantly used in Linux Systems to provide remote access to Linux terminals. It was initially designed as a replacement for Telnet and other shell protocols. However, it can be used for other use cases like Port Forwarding, Tunnelling, File Transfer, etc. as well.
SSH was first released in 1995. At that time there were multiple programs that were used for remote access to shell. However, they used plaintext for the data in transit. SSH uses a three-way handshake in order to authenticate the server and clients when configured for key-based authentication.
Anyone who has dealt with Linux Systems must have heard this abbreviation RTFM or RTFD. What is the full form of RTFM? Read The Feature(keeping profanity away 😇) Manual/Document. If you haven’t, it is recommended to get used to reading.
SSH Client
Since you are already here.. Let’s start with the Feature Manual by running ssh --help it on your unix-like machines. Here’s the excerpt from the description:
ssh (SSH client) is a program for logging into a remote machine and for executing commands on a remote machine. It is intended to provide secure encrypted communications between two untrusted hosts over an insecure network. X11 connections, arbitrary TCP ports and UNIX-domain sockets can also be forwarded over the secure channel.
ssh connects and logs into the specified destination, which may be specified as either [user@]hostname or a URI of the form ssh://[user@]hostname[:port]. The user must prove their identity to the remote machine using one of several methods (see below).
If a command is specified, it will be executed on the remote host instead of a login shell. A complete command line may be specified as command, or it may have additional arguments. If supplied, the arguments will be appended to the command, separated by spaces, before it is sent to the server to be executed.
An SSH Client is a program that will allow access to a remote server via a secure connection. The client is responsible for initiating the connection with the SSH server which is defined in the URI. The security between SSH Client and Server is ensured by using a combination of asymmetric key encryption along with Symmetric Key encryption mechanisms. SSL-based protocols also use this combination to ensure a secure connection. (Check out my article on SSL-based Security — An Introduction)
ssh client can be used to connect using the following command:
ssh <user>@<host>
This command is a very basic command. We can do a lot more than this.
If you are not on Linux, no worries! Windows also has its own program Putty. Here’s the link to it Manual. However, I will not recommend the beginners to RTFM though.
The first thing mentioned in the description is ssh (SSH client). This means that it is just a client and another part application will be the server. It is called sshd. Let’s RTFM in the next section.
SSHD (SSH server)
We run sshd --help on our unix-like system(it may not be pre-installed in some distros) to get the manual for SSH Server. SSH server applications are available for other operating systems. However, we will limit ourselves to Linux servers in this article.
Here’s the excerpt of the description:
sshd (OpenSSH Daemon) is the daemon program for ssh(1). It provides secure encrypted communica‐
tions between two untrusted hosts over an insecure network.sshd listens for connections from clients. It is normally started at boot from /etc/init.d/ssh.
It forks a new daemon for each incoming connection. The forked daemons handle key exchange, en‐
cryption, authentication, command execution, and data exchange.
sshd is a server application that runs as a service that listens to client. It governs how SSH clients will connect and establish a secure connection. It is responsible for authenticating the clients.
Authentication
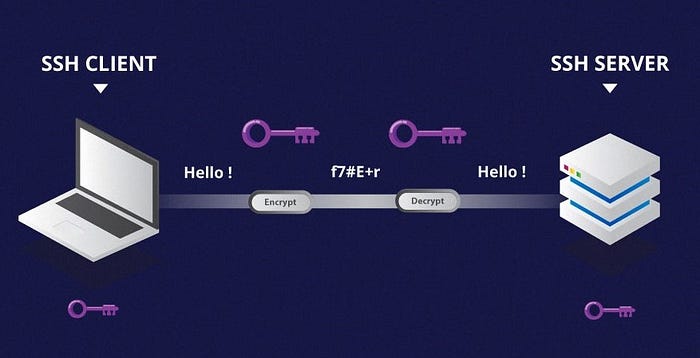
Source: https://iot4beginners.com/
OpenSSH supports multiple authentication mechanisms. The available authentication methods are:
1. Public key Authentication
SSH public key authentication is a method of logging in to an SSH server using a cryptographic key pair instead of a password. The key pair consists of a public key and a private key. The public key is stored on the SSH server, and the private key is stored on the client computer.
To log in to an SSH server using public key authentication, the client sends its public key to the server. The server then verifies the public key and authenticates the client. If the authentication is successful, the client is logged in to the server.
Public key authentication is more secure than password authentication because it is much more difficult to crack a cryptographic key than it is to guess a password. Additionally, public key authentication does not require the user to enter a password, which makes it less susceptible to man-in-the-middle attacks.
2. Password-based authentication
SSH password-based authentication is a method of logging in to an SSH server using a password. It is the simplest form of SSH authentication, but it is also the least secure.
To log in to an SSH server using password-based authentication, the client sends its username and password to the server. The server then verifies the username and password and authenticates the client. If the authentication is successful, the client is logged in to the server.
If you are using SSH password-based authentication, it is important to use a strong password and to change it regularly. You should also enable two-factor authentication to add an additional layer of security.
3. No Authentication
What!!! Yes. SSH supports access without authentication. SSH allows logging in to an SSH server without using any authentication. This means that anyone can log in to the server, regardless of their username or password. This is called none authentication.
SSH none authentication is disabled by default on most SSH servers. However, it can be enabled by setting the PermitEmptyPasswords option to yes in the SSH server configuration file.
None authentication should only be used in very specific cases, such as when you need to allow access to a server without requiring a password. For example, you might use none authentication to allow a monitoring script to connect to a server without having to enter a password.
However, it is important to note that none authentication is very insecure. Anyone can log in to the server, regardless of their username or password. This means that an attacker could easily gain access to the server and steal data or install malware.
Here are some of the risks of using SSH none authentication:
Anyone can log in to the server, regardless of their username or password
An attacker could easily gain access to the server and steal data or install malware
The server is more vulnerable to denial-of-service attacks
If you are considering using none authentication, you should carefully weigh the risks and benefits. Only use none authentication if you absolutely need to and take steps to mitigate the risks, such as using a firewall to restrict access to the server.
3. Keyboard Interactive Authentication
SSH keyboard-interactive authentication is a method of logging in to an SSH server by answering a series of prompts. The prompts can be anything, such as a password, a one-time password, or a security question.
Keyboard-interactive authentication is more secure than password authentication because it allows the server to ask the user for additional information to verify their identity. This makes it more difficult for an attacker to gain access to the server.
Keyboard-interactive authentication is also more flexible than password authentication. It can be used to implement a variety of different authentication mechanisms, such as two-factor authentication and single sign-on.
To use keyboard-interactive authentication, the client and server must agree on a keyboard-interactive authentication method. This is done during the SSH handshake. Once the client and server have agreed on a method, the server can start sending prompts to the user.
4. Host-Based Authentication
SSH host-based authentication is a method of logging in to an SSH server by verifying the identity of the client host. This is done by comparing the client host’s public key to a list of known public keys on the SSH server. If the client host’s public key is in the list of known public keys, the client is authenticated and logged in to the server.
Host-based authentication is more secure than password authentication because it does not require the user to enter a password. This makes it less susceptible to man-in-the-middle attacks.
Host-based authentication is also more convenient than password authentication because the user does not have to remember a password.
5. GSSAPI Authentication
SSH GSSAPI-with-mic authentication is a method of logging in to an SSH server using the GSSAPI (Generic Security Services Application Program Interface) framework. GSSAPI is a set of standards that define how to perform authentication, authorization, and data integrity protection.
GSSAPI-with-mic authentication is more secure than password authentication because it uses a cryptographic key to verify the identity of the client and server. This makes it more difficult for an attacker to gain access to the server.
GSSAPI-with-mic authentication is also more convenient than password authentication because the user does not have to enter a password.
GSSAPI-with-mic authentication can also be used with authentication protocols, such as Kerberos and NTLM.
Conclusion
SSH is a secure network protocol that allows users to remotely access other computers. The most secure authentication method is public key authentication. It supports multiple authentication methods. Public key authentication uses a cryptographic key pair to verify the identity of the client and server. SSH is a powerful and versatile tool that can be used to improve the security and convenience of remote access.
Subscribe to my newsletter
Read articles from NonStop io Technologies directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

NonStop io Technologies
NonStop io Technologies
Product Development as an Expertise Since 2015 Founded in August 2015, we are a USA-based Bespoke Engineering Studio providing Product Development as an Expertise. With 80+ satisfied clients worldwide, we serve startups and enterprises across San Francisco, Seattle, New York, London, Pune, Bangalore, Tokyo and other prominent technology hubs.