How Ransomware's "Bring Your Own Installer" Method Bypasses EDR Systems
 Tran Hoang Phong
Tran Hoang Phong
The new "Bring Your Own Installer" technique has been exploited in attacks to bypass SentinelOne's protection, allowing attackers to disable Endpoint Detection and Response (EDR) capabilities to install Babuk ransomware.
Background
Endpoint Detection and Response (EDR) is an essential defense layer in modern cybersecurity strategies, particularly in detecting and responding to advanced malware like ransomware. Among these, SentinelOne is a prominent EDR solution, designed with various protective features such as tamper protection, real-time process monitoring, and malware recovery. However, researchers from Stroz Friedberg, an investigation unit of Aon, have discovered a new exploitation technique used in ransomware attacks that bypasses this protection mechanism without third-party tools. This technique, named “Bring Your Own Installer” (BYOI), targets a vulnerability in SentinelOne's agent upgrade process.
Exploitation Scenario
In a real-world ransomware attack investigation, Stroz Friedberg experts found that the threat actor gained administrative access to the target system (often through exploiting vulnerabilities or credential theft). They then downloaded a legitimate installer of SentinelOne—undetected by security software—and initiated the upgrade process.
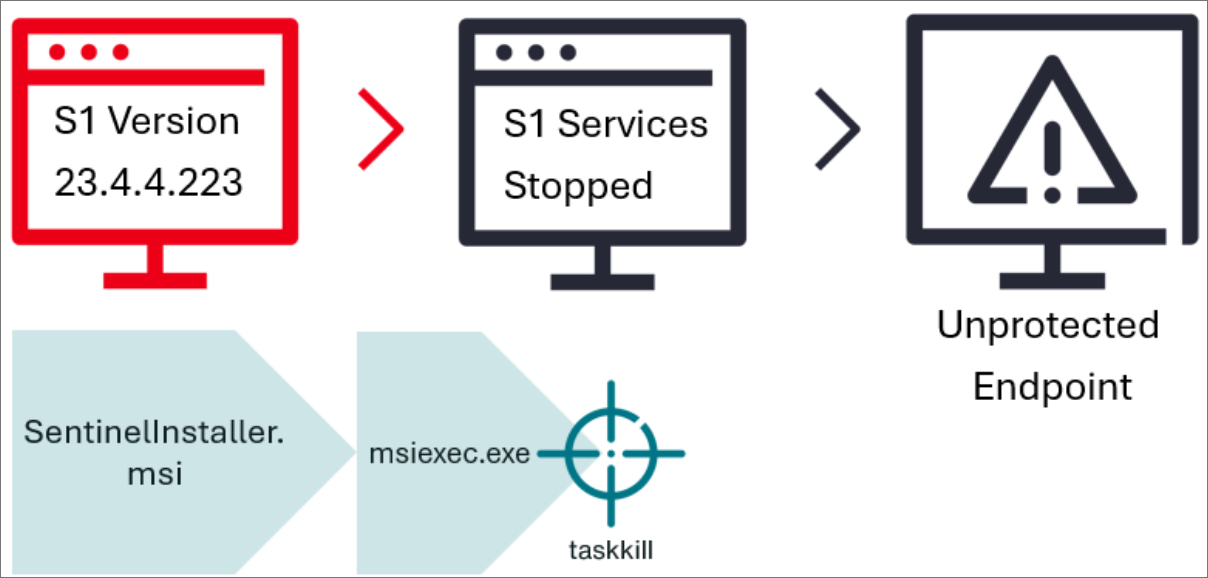
Figure 1. Bring Your Own Installer EDR bypass attack chain
During the installation process, the installer temporarily disables the active agent processes to replace files with a new version. However, before the installation completes, the attacker forcibly terminates the “msiexec.exe” process (the Windows installer). This creates a “protection gap”—a moment when the old agent is stopped, but the new agent is not yet installed or activated. During this brief period, the system lacks any EDR protection, allowing the attacker to easily deploy Babuk ransomware or other payloads.
Technical Analysis
This BYOI EDR bypass technique does not use malicious drivers or kernel exploits like traditional methods but relies entirely on SentinelOne's original installer—making it sophisticated and hard to detect. This also allows the technique to bypass most file control measures or allowlist policies typically applied in tightly controlled environments.
A key exploited feature here is the agent upgrade process—a function that often does not require additional authentication if performed internally. In many versions of SentinelOne, the default “Online Authorization” feature—which requires approval from the central console before performing local upgrades/removals—is not enabled by default. This allows attackers to perform dangerous actions with just local administrative access.
Additionally, the device being removed from the console after the msiexec.exe process is blocked is a critical indicator that the agent is no longer active—a point that can be leveraged to build monitoring or attack detection rules.
According to SentinelOne, all agent versions can be affected if not configured correctly. However, if features like local agent password protection or Local Upgrade Authorization are enabled, this technique cannot be successfully executed.
Recommendations
FPT Threat Intelligence recommends organizations and individuals take several measures to prevent this particularly dangerous attack campaign:
Enable “Online Authorization” or “Local Upgrade Authorization” in SentinelOne's policy to ensure all upgrades, removals, or agent changes must be approved from the central console. This is a crucial measure to prevent BYOI.
Monitor unusual installation processes, especially the activity of
msiexec.exe, combined with events related to the agent disappearing from the console—this could be a sign of an attack.Apply password protection policies for local agents to block unauthorized actions such as manual removal or upgrades.
Verify that the entire system has updated policies, especially organizations deploying EDR through third-party systems like SCCM or RMM, as default configurations may not enable local upgrade protection features.
Enhance audit log checks and set up abnormal alerts when the SentinelOne agent is stopped without reason or loses connection to the console.
Re-evaluate Zero Trust policies in the network environment, ensuring all installation actions, even from legitimate software, are clearly identified and purpose-checked.
References
Subscribe to my newsletter
Read articles from Tran Hoang Phong directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tran Hoang Phong
Tran Hoang Phong
Just a SOC Analyst ^^