Real-World UDP: How WebRTC and DNS Use the Fast but Unreliable Protocol
 Prateek Kumar
Prateek Kumar
🔙 Previously: Inside the UDP Protocol: Anatomy, Features, and “Non-Services”
UDP may be lightweight and “unreliable” by design, but that hasn’t stopped developers from building powerful real-world systems on top of it. In this of the series, we’ll see how two critical technologies — WebRTC and DNS — successfully use UDP and turn its limitations into strengths.
🎥 WebRTC: Real-Time Communication via UDP
What is WebRTC?
WebRTC (Web Real-Time Communication) is a technology that allows peer-to-peer communication directly in the browser. Think of video calls on Google Meet, Discord voice chat, or screen sharing — all powered by WebRTC.
Why WebRTC uses UDP:
Real-time communication can’t afford to wait for retransmissions. Dropping a few video frames or audio samples is better than pausing to retry. UDP allows low-latency transmission, which is perfect for real-time voice, video, and data.
But UDP alone isn’t enough — so WebRTC uses helper protocols:
ICE (Interactive Connectivity Establishment): Tries multiple network paths and chooses the most efficient one.
STUN (Session Traversal Utilities for NAT): Helps devices discover their public IPs and port mappings.
TURN (Traversal Using Relays around NAT): Relays traffic through a server when peer-to-peer fails.
SRTP (Secure RTP): Encrypts media over UDP to keep it secure.
WebRTC essentially builds a reliable and secure system on top of UDP, customizing retransmission and jitter buffering where necessary.
VoIP and Online Gaming: Where Lag is the Enemy
VoIP (Voice over IP) and multiplayer online games are two more major use cases of UDP. These applications require minimal delay and can tolerate some packet loss.
Why UDP is perfect for them:
VoIP: Missing a syllable is better than waiting for a retry. UDP ensures the voice stream keeps flowing.
Gaming: Actions like jumping, shooting, or moving must happen in real-time. Even if one update is missed, the next one quickly follows.
Just like with WebRTC, these systems often use NAT traversal techniques like STUN, TURN, and ICE to establish connections between players or participants.
Some gaming engines even implement custom reliability mechanisms on top of UDP to resend only critical data (like hit registration), leaving non-critical updates (like player position) to flow freely.
Understanding NAT Types and Why They Matter
When two devices are behind NAT (Network Address Translation), peer-to-peer communication becomes tricky. The type of NAT can dramatically affect connection success.
Common NAT Types:
Full-cone NAT: Easiest to connect through. Once a port is open, anyone can send to it.
Restricted-cone NAT: Allows responses only from IPs that the internal host contacted first.
Symmetric NAT: Most strict. Only the exact external IP:port pair can respond. Each outbound request uses a unique mapping.
Why this matters:
Symmetric NATs often break peer-to-peer connections. That’s where TURN servers become necessary as relays.
STUN works well for cone NATs, but fails in symmetric scenarios.
Understanding NAT types is crucial when building or troubleshooting peer-to-peer UDP applications.
DNS: Fast Name Resolution with UDP
What is DNS?
The Domain Name System (DNS) translates human-friendly domain names like openai.com into IP addresses like 104.20.21.46.
Why DNS uses UDP:
DNS queries are small (typically < 512 bytes)
It’s a simple request/response model
Using UDP avoids the overhead of setting up a TCP connection
What if UDP fails?
DNS falls back to TCP for large responses (e.g., DNSSEC)
TCP is also used when responses are truncated or if security extensions are involved
DNS makes the most of UDP’s speed, while still having a safety net.
Diagram: P2P Setup with STUN/TURN/ICE
Here’s a simplified overview of how peer-to-peer communication works with NAT traversal:
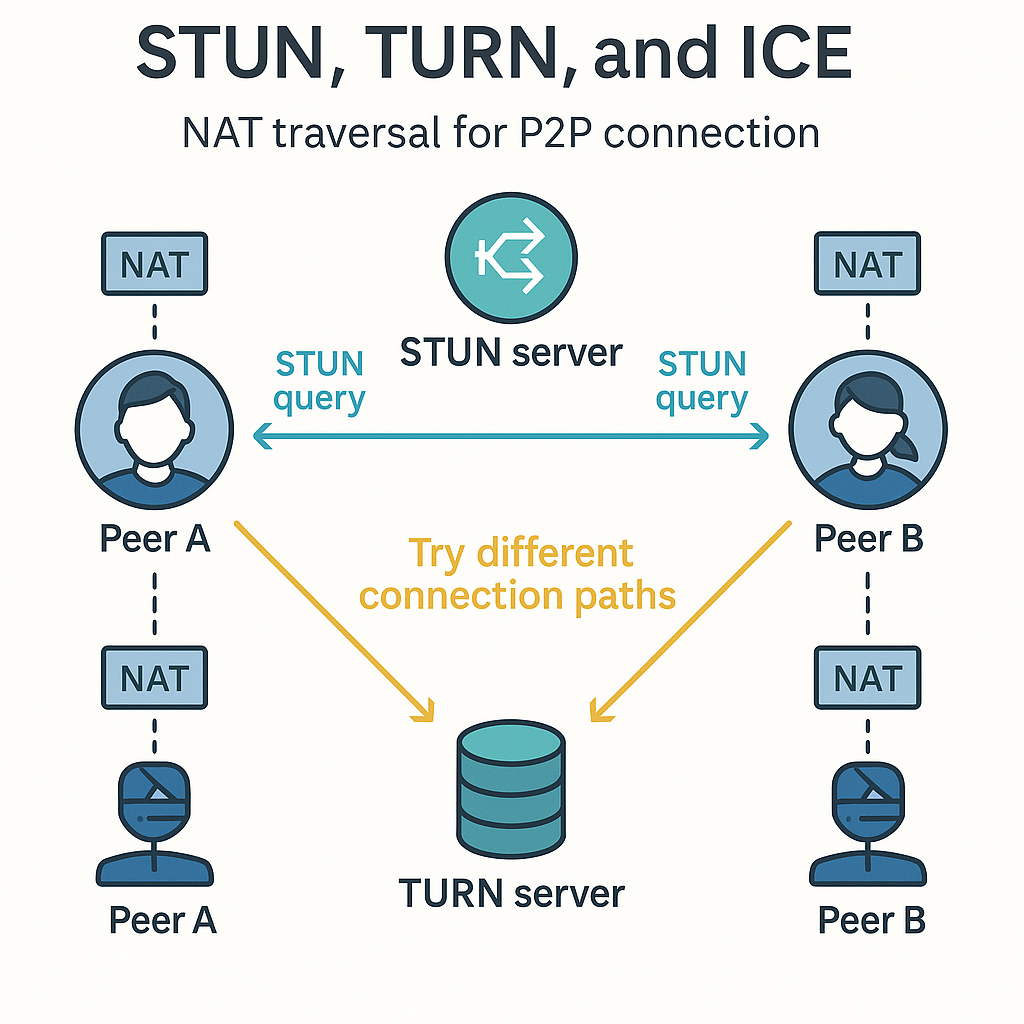
Peers use STUN to discover their public IP/port.
ICE coordinates connection attempts.
If direct connection fails, traffic is relayed via TURN.
This approach enables real-time UDP-based connections even when both peers are behind strict NATs.
The Big Picture
WebRTC, VoIP, gaming, and DNS show us that UDP isn’t broken — it’s just incomplete. But with some clever layering, it becomes a foundation for:
Real-time communication
Rapid-fire lookups
Flexible and scalable internet applications
By understanding how systems like WebRTC and DNS work around UDP’s limitations, you can design your own networked applications more confidently.
Final Thoughts
UDP gives you raw, fast, no-frills communication. But to make it production-ready, you need to:
Handle NAT
Secure your data
Deal with lost or unordered packets
Monitor your traffic
That’s exactly what protocols like WebRTC, VoIP, online games, and DNS do — and they do it brilliantly.
In Part 4, we’ll explore how to design robust applications over UDP, including flow control, retransmission strategies, and developer best practices inspired by RFC 5405.
Subscribe to my newsletter
Read articles from Prateek Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Prateek Kumar
Prateek Kumar
Software Developer