Module 3 : Network Security Explained
 GarudaSec Team
GarudaSec Team
Think about how often you connect to public Wi-Fi — checking emails, logging into your bank account, sending messages, just because its free. That convenience often comes at the cost of your security and privacy.
ICANN & IANA
Internet Corporation of Assigned Names and Numbers (ICANN) & Internet Assigned Numbers Authority (IANA) are the two key organizations that help keep the internet running smoothly by managing domain names, IP addresses, and essential technical standards.
ICANN is the organization that oversees the overall policy, coordination and governance of the domain name system, including domain names IP address.
IANA is a department within ICANN responsible for the technical management and implementation of these policies, such as allocating IP address blocks to Regional Internet Registries, managing the DNS root zone, and assigning protocol parameters.
IP Address and its versions
IP address is a unique 32 bit numerical identifier assigned to each device in the network.
Analogy - Each house in the city has its own address (IP address). This address ensures that letter (data) reaches the intended destination.

Each octet (8 bits) can contain any numbers between 0-255.
IP address is separated into 2 parts -
Network Address -
Identifies the specific network a device belongs to. All devices on the same network share this part.
Analogy - Like a building number or wing in an apartment complex — it tells you the general location.
Host Address -
Identifies the individual device (host) within that network. Must be unique within the same network.
Analogy - Like a flat or house number — it tells you exactly which unit inside the building.
To know which part is network address and host address, subnet mask is used.
A subnet mask is a 32-bit number that divides an IP address into two parts:
The network portion
The host portion

The box part of IP address is the Network ID and rest is Host ID. Today, instead of using the traditional subnet mask notation, CIDR notation is commonly used.
Eg. CIDR (Classless Inter-Domain Routing) Notation - 192.168.2.56/24 This means first 24 bits is Network ID and rest is Host ID
Comparative study of IPv4 & IPv6
| Feature | IPv4 | IPv6 |
| Length | 32 bits | 128 bits |
| Format | Decimal (192.168.2.56) | Hexadecimal (2001:0db8:85a3::8a2e:0370:7334) |
| Address count | ~4 billion address | ~340 undecillion addresses |
IPv4 Classes
Classful classification is a method of dividing IP addresses into fixed classes (A, B, C, D, E) based on their leading bits and subnet masks.
| Class | Start Address | End Address | Subnet Mask | No. of Network Address |
| A | 1.0.0.0 | 126.255.255.255 | 255.0.0.0 | 16,777,216 |
| 127.0.0.0 | 127.255.255.255 | 255.0.0.0 | Localhost | |
| B | 128.0.0.0 | 191.255.255.255 | 255.255.0.0 | 65,536 |
| C | 192.0.0.0 | 223.255.255.255 | 255.255.255.0 | 256 |
| D | 224.0.0.0 | 239.255.255.255 | NA | Multicast |
| E | 240.0.0.0 | 255.255.255.255 | NA | For future use; currently for testing. |
IPv6 Address Types

Usage of IPv6 address types
Web browsing (HTTP/HTTPS): A user’s computer communicates with a web server using Unicast.
Streaming services (audio, video): Applications like YouTube, Netflix, and live video broadcasts use Multicast to efficiently distribute video or audio content to multiple viewers.
DNS: Multiple DNS servers around the world might share the same Anycast address, and a client will automatically be routed to the nearest DNS server based on network topology.
Content Delivery Networks (CDNs): Anycast is used to route requests for web content to the closest server in a CDN, minimizing latency.
Internet Protocols (IP)
Both TCP and UDP are transport layer protocols in the Internet Protocol Suite (TCP/IP model) that enable data communication between devices over a network. They define how the data is delivered over the network.
TCP (Transmission Control Protocol) is a connection-oriented (requires handshake) transport layer protocol that provides reliable, ordered, and error-checked delivery of data between applications over an IP network.
Thanks, TCP — for making sure your email didn’t get lost, broken, or show up out of order!😂
Without TCP, those attachments might never make it!
Use cases -
Web browsing (HTTP, HTTPS) — ensures web pages load completely and correctly
Email (SMTP, IMAP, POP3) — guarantees messages arrive without loss
File transfers (FTP, SFTP) — reliable delivery of files
UDP (User Datagram Protocol) is connection less (no handshake) transport layer protocol that provides fast but unreliable and unordered delivery of between applications over an IP network.
Use cases -
Video streaming — fast delivery, some data loss is acceptable
Online gaming — speed is critical, small packet loss doesn’t ruin experience
VoIP (Voice over IP) — real-time communication where delays are worse than loss
OSI Model
The OSI Model (Open Systems Interconnection Model) is a conceptual framework that standardizes how different computer systems communicate over a network by dividing the communication process into 7 distinct layers, each with specific functions.
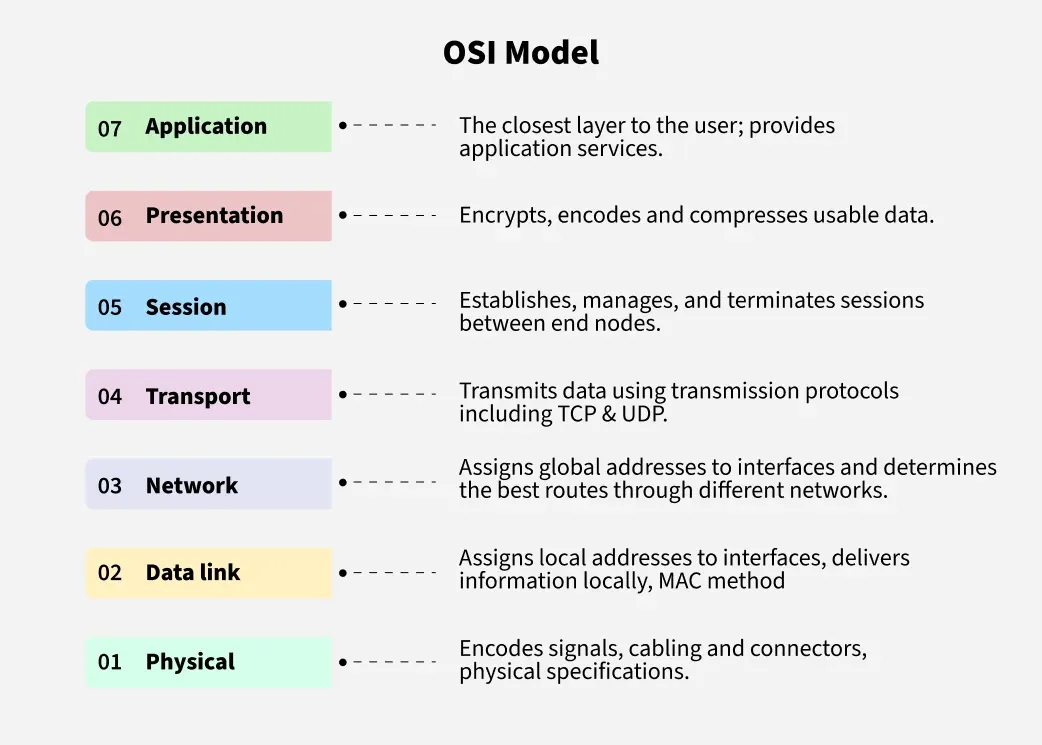
Source - GeeksforGeeks
TCP/IP Model
The TCP/IP model (also called the Internet Protocol Suite) is a simplified and practical model used to describe how data is transmitted across the internet. It has 4 layers, each responsible for part of the communication process.
Source - Kyle Law - Medium
| Layer | Key Role | Examples |
| Application | Interface for user apps | HTTP, DNS, FTP |
| Transport | Reliable or fast delivery | TCP, UDP |
| Internet | Routing and addressing | IP, ICMP |
| Network Access | Physical connection and data transfer | Ethernet, Wi-Fi, ARP |
Types of Networks
| Type | Full Form | Coverage Area | Example |
| LAN | Local Area Network | Small (room/building) | Home/office network |
| MAN | Metropolitan Area Network | Medium (city) | City-wide university net |
| WAN | Wide Area Network | Large (nation/world) | The Internet |
Type of IPs
| Type | Description | Example |
| Private IP | Used within private networks; not routable on the internet | 192.168.0.1, 10.0.0.5 |
| Public IP | Assigned to devices connected directly to the internet | 8.8.8.8 (Google DNS) |
Discover your public IP instantly with our GarudaSec Tools — fast, accurate, and easy to use!
Basic Network Commands
ipconfigis a network command that shows configuration details of all network interfaces on a Windows computer.
ping <ip or domain name>The ping command is a network diagnostic tool used to test the connectivity between your computer and another device (such as a server, router, or website) over a network. It works by sending ICMP Echo Request packets to the destination and waits for an **ICMP (**Internet Control Message Protocol) Echo Reply.By default, the ping command sends several echo requests, typically four or five. The result of each echo request is displayed, showing whether the request received a successful response, how many bytes were received in response, the Time to Live (TTL), and how long the response took to receive, along with statistics about packet loss and round trip times.
The time-to-live value instructs a network router when a packet should be discarded.
This output shows the results of using the ping command to test the connection to Google’s public DNS server at IP address 8.8.8.8

Ping sweep script
for /L %i in (1, 1, 254) do ping 192.168.0.%i -n 1 -w 100 | find “TTL=”The above command is a Windows batch loop used to ping a range of IP addresses—typically to check for live hosts on a subnet.
find “TTL=”this command will only display successful ping responses.
-
Advanced IP Scanner is a tool that scans your local network to -
Identify live hosts on the network
Show IP and MAC Address
Identify device names and manufacture

tracert <ip or domain name>The tracert command (short for trace route) is a network diagnostic tool used in Windows to track the path that packets take from your computer to a specified destination across an IP network. It shows each hop along the route and how long each hop takes.
Ports
Physical Ports
Physical ports in computers are the hardware interfaces where peripheral devices connect to the computer. These ports allow for data transfer, power delivery, and communication between the computer and external devices.

Virtual Ports
Virtual Port is a layer 4 Transport Layer concept in OSI Model. A port is a virtual point where network connections start and end. Ports are software based and managed by computer’s OS. Each port is associated with a service/process. Ports allow computers to easily differentiate between different kinds of traffic: emails go to a different port than webpages, for instance, even though both reach a computer over the same Internet connection.
Ports are standardized across all network-connected devices, with each port assigned a number. Most ports are reserved for certain protocols — for example, all Hypertext Transfer Protocol (HTTP) messages go to port 80. While IP addresses enable messages to go to and from specific devices, port numbers allow targeting of specific services or applications within those devices.
There are total 65335 ports.
| Port Range | Type | Description |
| 0 – 1023 | Well-known ports | Reserved for common protocols (HTTP, FTP, etc.) |
| 1024 – 49151 | Registered ports | Assigned to user processes or applications |
| 49152 – 65535 | Dynamic / Private ports | Used temporarily by client applications |
Well Know Ports
| Port | Protocol | Service |
| 20, 21 | TCP | FTP (File Transfer Protocol) |
| 22 | TCP | SSH (Secure Shell) |
| 23 | TCP | Telnet |
| 25 | TCP | SMTP (Email sending) |
| 53 | TCP/UDP | DNS (Domain Name System) |
| 67, 68 | UDP | DHCP (Dynamic Host Configuration Protocol) |
| 80 | TCP | HTTP (Web) |
| 110 | TCP | POP3 (Email retrieval) |
| 143 | TCP | IMAP (Email retrieval) |
| 161, 162 | UDP | SNMP (Simple Network Management Protocol) |
| 443 | TCP | HTTPS (Secure Web) |
| 3306 | TCP | MySQL Database |
| 3389 | TCP | RDP (Remote Desktop Protocol) |
Detecting open ports through Nmap
Nmap is a powerful, open source network scanning tool that helps in
Host Discovery - Finds active devices on a network.
Port Scanning - Detects open ports and services running on a host
Service and Version detection - Identifies applications and versions on open ports
OS Detection - Tries to determine the operating system of hosts
Port Scanning is the method used to identify ports that are open and actively listening for connections and services running on those ports.
Basic Nmap Commands
nmap <domain or ip>to scan a single hostIt displays open ports and service running on those ports

nmap [ip] >> result.txtTo store scan results in a text fil



nmap <target1 target2>to scan multiple hosts

nmap -- open <ip>Only display open ports.

nmap -p- <ip>scan all virtual portsnmap -O <ip>OS Detection

nmap -sV <ip>Service Version Detection

nmap -sT <ip>TCP Connect ScanDescription: Completes a full TCP 3-way handshake.
Detectable? Yes, very.
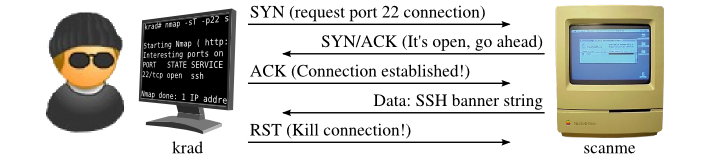
Source - Nmap
| Privilege Level | Default Scan Type |
| Root/Admin | TCP SYN scan (-sS) |
| Non-root | TCP Connect scan (-sT) |
nmap -sS <ip>TCP SYN scanDescription: Sends SYN packets to the target ports and analyzes responses without completing the TCP handshake. Therefore known as half open scan. Scans 1000 most common ports.
Detectable?: Stealthier than TCP connect scan.
| Probe Response | Assigned State |
| TCP SYN/ACK response | open |
| TCP RST response | closed |
| No response received (even after retransmissions) | filtered |
| ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) | filtered |
SYN scan of open port
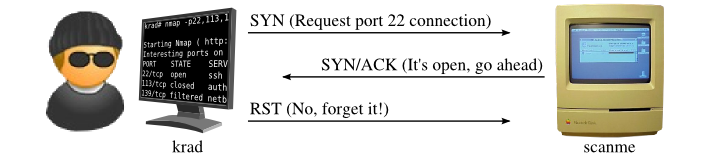
Source - Nmap
SYN scan of closed port
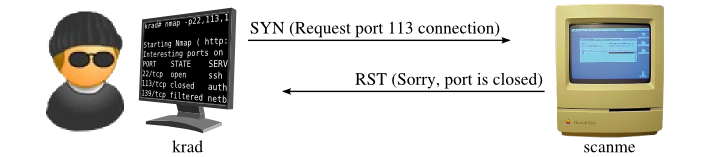
Source - Nmap
SYN scan of filtered port
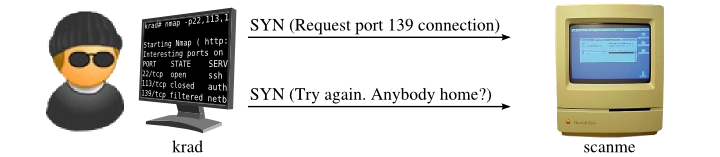
Source - Nmap
A filtered port in Nmap's results means that Nmap cannot determine whether the port is open or closed because packet filtering is preventing the probe packets from reaching the port (or the responses from coming back).
nmap -sUUDP scanDescription: Since UDP is a connectionless protocol, there is no 3 way handshake in this. Nmap sends a UDP datagram to the target port (often an empty payload or protocol-specific payload).
Some popular services we look for in UDP scan -
DHCP - Port 67
DNS - Port 53
Kerberos Authentication Protocol - Port 88
Detectable? : moderately stealthy
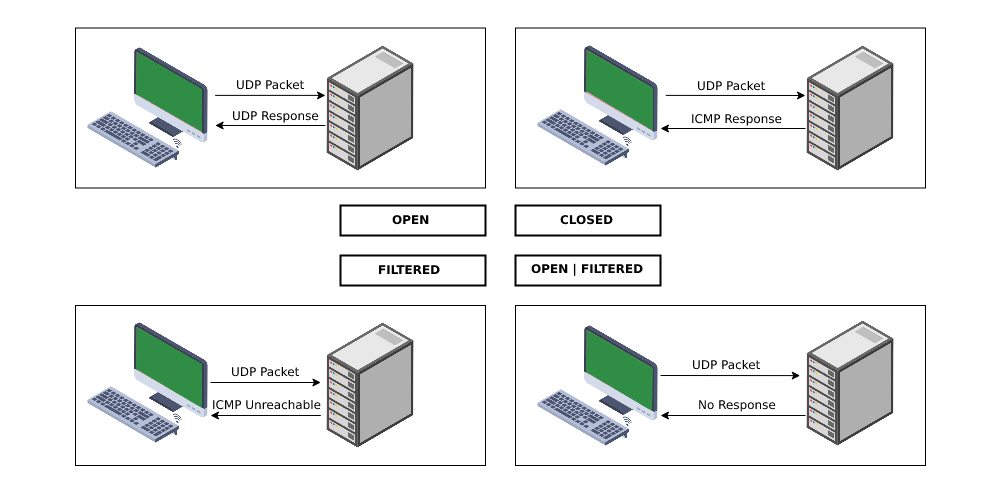
Source - GeeksforGeeks
| Response Type | Port Status |
| ICMP Port Unreachable (Type 3, Code 3) | Closed |
| No response (no reply or filtered ICMP) | **Open |
| Valid UDP reply (e.g., DNS, SNMP response) | Open |
| ICMP unreachable (type 3, code 1, 2, 9, 10, 13) | Filtered |
Inverse TCP Scanning / Stealth scans
They're called inverse or stealth TCP scans because they invert the normal behavior of how a TCP connection is initiated — essentially doing the opposite of a standard TCP handshake.
In a typical TCP Handshake -
Client sends SYN packet to the server
Server responds to the client with SYN-ACK packet
Client responds to the server with ACK packet to establish the connection.
This is the expected behaviour and can be easily detectable by intrusion detection systems. Instead of starting with a SYN packet, these scans send packets with illegal combination of flags to avoid detection.
How Nmap interprets responses to a NULL, FIN, or Xmas scan probe
| Probe Response | Assigned State |
| No response received (even after retransmissions) | open |
| TCP RST packet | closed |
| ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) | filtered |
These scans are OS dependent. These scans relies on specific behavior outlined in the TCP standard (RFC 793). But not all operating systems follow this standard exactly.
Before understanding these scans we’ll first understand what TCP flags are and their types -
TCP flags are signals used by computers to start, manage and end a conversation.
We’ll understand this through an analogy -
Imagine 2 people trying to talk on a phone -
| Flag | Full Name | What it Means | Easy Example |
| SYN | Synchronize | “Let’s start talking.” | Hello! 📞 |
| ACK | Acknowledge | “I got your message.” | Got it ✅ |
| FIN | Finish | “I’m done talking.” | Bye 👋 |
| RST | Reset | “Stop! I don’t know you.” | Hang up! ❌ |
| PSH | Push | “Send this now!” | Urgent! 🚨 |
| URG | Urgent | “This is extra important!” | Top priority ⚠️ |
FIN scan
nmap -sF <ip or domain>FIN scan is stealthy port scanning technique that sends a TCP packet with FIN flag set to a target port.
FIN flag in TCP is set to close an established connection. Sending a FIN packet without establishing a connection is unusual.

Source - Oreilly
XMAS scan
nmap -sX <ip or domain>XMAS scan = Nmap sends TCP packet with FIN + URG + PSH flag set.
This combination is unusual and unexpected by normal systems.
It is called Xmas scan because the scan “lights up” bits in the TCP header like a Christmas tree.
NULL scan
nmap -sN <target ip or domain>Nmap sends TCP packet with not flags set.
Nessus
Nessus is a vulnerability scanner—a powerful cybersecurity tool used to identify security holes, misconfigurations, and vulnerabilities in computers, servers, networks, and applications.
Developed by: Tenable Inc.
What Nessus can do ?
Vulnerability scanning
Configuration auditing
Malware detection
Web application scanning
Compliance checks (e.g., CIS, PCI DSS)
What is Scan Policy?
Scan Policy is a set of rules and configurations that define how vulnerability scanning is conducted. Think of it as a checklist Nessus follows during a scan.
It determines -
What plugins to use
Speed and depth of the scan
What types of vulnerabilities to look for
Whether to use credentials
We can create our own scan policy as well.
The preconfigured scan policies provided by Tenable Inc. are known as Scan Templates

Select Advanced Scan
Enter the target IP and details


Click on Launch button

Subscribe to my newsletter
Read articles from GarudaSec Team directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
