Use Syft and Grype to cement your Software Supply Chain Security
 Deepak Garg
Deepak GargTable of contents
- Why Software Supply Chain Security Is More Critical Than Ever
- Meet the Tools: Syft and Grype
- Understanding the Foundations: SCA, SBOM, and Security Vulnerability Detection
- Integrating Syft and Grype into Your Workflow
- Real-World Benefits for SaaS Companies
- Final Thoughts: From Awareness to Action
- Resources
Why Software Supply Chain Security Is More Critical Than Ever
In an era where open-source software forms the backbone of most SaaS products, managing dependencies, identifying vulnerabilities, and maintaining software transparency have become fundamental to operational security.
This is where tools like Syft and Grype, developed by Anchore, step in.
These open-source tools help development and security teams to:
Generate accurate software bills of materials (SBOMs)
Perform deep software composition analysis (SCA)
Detect and triage vulnerabilities in container images, file systems, and source code
Meet the Tools: Syft and Grype
🛠️ What Is Syft?
Syft is a CLI tool and Go library for generating SBOMs for container images and filesystems.

Key Features:
Supports a wide array of formats: Docker, OCI, directories, and archives
Outputs SBOMs in multiple formats: JSON, SPDX, CycloneDX
Integrates easily into CI/CD pipelines
Use Case for SaaS Companies:
Track every open-source dependency in your product
Maintain transparency across your build environments
Feed SBOMs into automated security and compliance checks
🔍 What Is Grype?
Grype is a CLI vulnerability scanner that consumes SBOMs and identifies known vulnerabilities in dependencies.

Key Features:
Pulls data from various sources: NVD, GitHub Security Advisories, and more
Supports SBOM input from Syft
Integrates with CI/CD pipelines for DevSecOps workflows
Use Case for SaaS Companies:
Scan application containers before production releases
Automate patching cycles with actionable vulnerability alerts
Provide auditors with vulnerability management documentation
Understanding the Foundations: SCA, SBOM, and Security Vulnerability Detection
📦 Software Composition Analysis (SCA)
SCA involves identifying all the open-source components in a codebase and analyzing them for risks. Syft enables this by:
Discovering all the packages and dependencies in images
Tagging them with metadata (version, origin, license)
Benefits:
Avoid shipping apps with risky or outdated packages
Stay compliant with licensing and governance rules
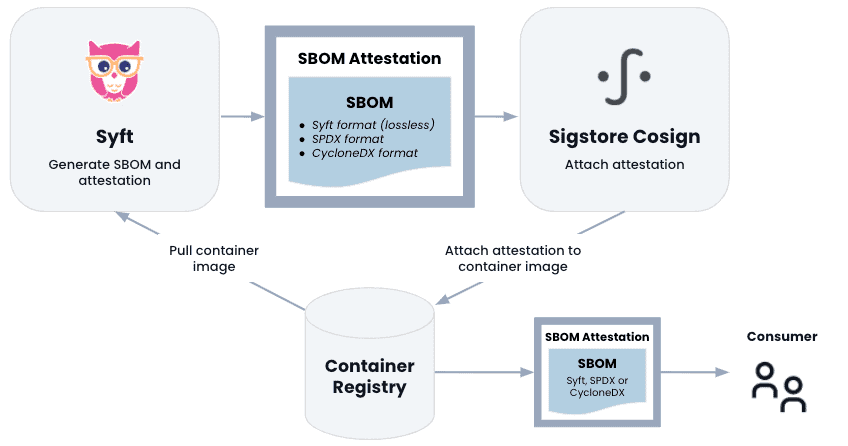
📄 Software Bill of Materials (SBOM) With Syft
An SBOM is a list of all components in a piece of software. It's vital for understanding:
What your software is made of: For example, a mobile app might include components like a user interface library, a database engine, and various third-party plugins.
What components are vulnerable or outdated: For instance, if your software uses an old version of a logging library that has a known security flaw, the SBOM will help identify this risk.
How to respond in the case of a security advisory: For example, if a security advisory is issued for a specific version of a library your software uses, the SBOM allows you to quickly determine if your software is affected and needs updating.
Syft automates SBOM generation, enabling:
Compliance with executive orders (e.g., U.S. Executive Order on Cybersecurity)
Easier incident response and remediation
To automate SBOM generation with Syft, you can use a command like the following to generate an SBOM for a Docker image:
syft docker:your-image-name -o json > sbom.jsonExample Output (snippet):
{ "artifacts": [ { "name": "openssl", "version": "1.1.1k", "type": "library", "locations": [ { "path": "/usr/lib/libssl.so.1.1" } ], "licenses": ["OpenSSL"], "language": "C" }, { "name": "nginx", "version": "1.21.0", "type": "application", "locations": [ { "path": "/usr/sbin/nginx" } ], "licenses": ["BSD-2-Clause"], "language": "C" } ], "source": { "type": "image", "target": { "userInput": "docker:your-image-name", "imageID": "sha256:abc123...", "manifestDigest": "sha256:def456..." } } }This command and output demonstrate how Syft can generate an SBOM in JSON format, which can be used for compliance with cybersecurity executive orders and facilitate easier incident response by providing a detailed inventory of software components.
🚨 Security Vulnerability Scanning With Grype
With Grype, your team can:
Detect CVEs associated with your dependencies
Use SBOMs as input for more accurate scanning
Automate vulnerability reporting as part of your CI/CD workflow
Why it matters:
SaaS products ship fast and frequently
Every release introduces potential security debt
Automated scanning ensures continuous protection
Integrating Syft and Grype into Your Workflow
⚙️ In the CI/CD Pipeline
# Generate SBOM with Syft
syft your-image:latest -o cyclonedx-json > sbom.json
# Scan for vulnerabilities with Grype
grype sbom:sbom.json
Best Practices:
Automate this scan on every pull request and build
Fail builds that include critical vulnerabilities
Export reports to your SIEM or dashboard for visibility
🔗 DevSecOps Automation
Hook Syft and Grype into GitHub Actions, GitLab CI, Jenkins, or CircleCI
Alert security teams with integrations like Slack or email
Maintain a centralized repository of SBOMs for audits
Real-World Benefits for SaaS Companies
✅ Proactive Risk Management
Identify issues before they reach production
Reduce attack surface by removing unused dependencies
✅ Faster Incident Response
Know exactly what’s affected when a new CVE is released
Cross-reference SBOMs to patch quickly and efficiently
✅ Improved Transparency and Compliance
Produce SBOMs as part of SOC 2, ISO 27001, and FedRAMP audits
Support customer assurance with detailed component disclosure
Final Thoughts: From Awareness to Action
Modern SaaS companies can’t afford to treat software supply chain security as an afterthought. Tools like Syft and Grype make it possible to:
See what you’re shipping
Understand the risk
Act with confidence
By integrating these tools into your development and deployment pipelines, you gain not only security visibility but also a competitive advantage.
Resources
Subscribe to my newsletter
Read articles from Deepak Garg directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
