Silver RAT: New Threat That Sidesteps Antivirus Protection
 Tran Hoang Phong
Tran Hoang Phong
Content: Silver RAT v1.0, a newly emerged Remote Access Trojan (RAT), is gaining attention in the cybersecurity community due to its ability to bypass modern antivirus software and its dangerous destructive features targeting Windows operating systems.
What is Silver RAT?
Developed by a group of Syrian programmers operating under the alias “Anonymous Arabic”, Silver RAT was first detected in the wild in November 2023. Prior to that, the software was announced via an official Telegram channel on October 19, 2022, and quickly spread across underground hacker forums such as TurkHackTeam, 1877, and Russian-speaking communities. The development team also established a dedicated distribution system consisting of e-commerce websites and multiple Telegram channels with over 1,000 members, serving for sales and technical support.
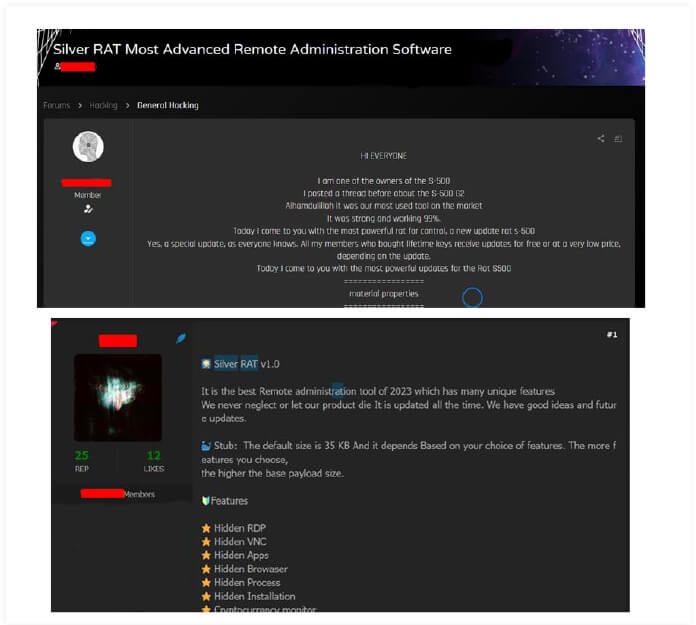
Figure 1. Illegal sale of Silver RAT 1.0 malware on underground hacker forums
Impact Level
According to analysis from Cyfirma, Silver RAT primarily uses social engineering techniques to distribute a small payload (40–50KB). When executed, the RAT requests administrative privileges, displays a brief command line window, and establishes a reverse shell to a command and control (C2) server. The communication channel can be an IP address with a port or an HTML link, allowing flexible deployment.
More than just a remote control tool, Silver RAT integrates several dangerous functions, including:
Encrypting data like ransomware
Keylogging
Stealing browser cookies
Deleting system restore points
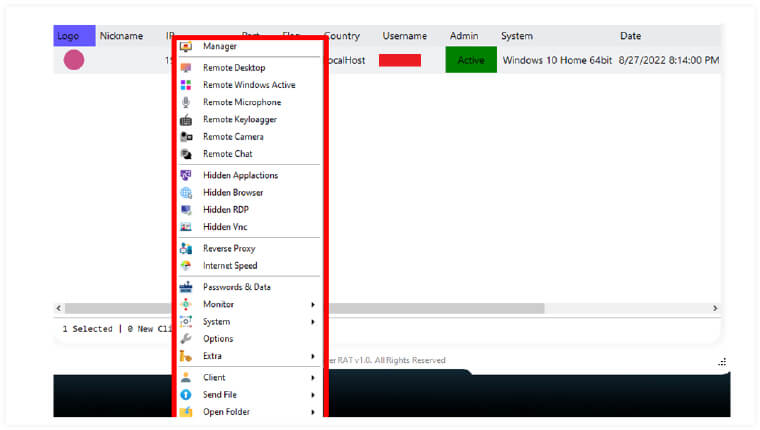
Figure 2. Some features of the Silver RAT malware
These features allow attackers to extract large-scale data and can cause victims to completely lose system recovery capabilities. The development team also announced plans to release a new version supporting Android, significantly expanding the attack range.
Evasion and Anti-Analysis Mechanisms of the Malware
Silver RAT v1.0 employs multiple anti-analysis mechanisms to avoid detection and investigation. The source code includes protective flags such as RuntimeProcessCheckerProtection, RuntimeAntiDebugProtection, KillDebuggerProtection, KillMaliciousProcess, DetectDllInjection, and RunSingleThread, designed to detect debugging or malware analysis activities.
Additionally, there is a blacklist named BadPList containing 95 common processes often used in malware analysis such as dnspy, x64dbg, IDA, Wireshark, and Fiddler. When any process from the list is detected running, the malware will automatically cease operation to avoid analysis.
Furthermore, Silver RAT uses:
FUD crypter to bypass antivirus software,
Hides processes from Task Manager,
Automatically adds itself to the Windows Defender exclusion list, making detection after execution nearly impossible.
.webp)
Figure 3. Ability to bypass AV using FUD Crypters
IOCs Related to Silver RAT Malware
| Hash | Description |
| 79a4605d24d32f992d8e144202e980bb6b52bf8c9925b1498a1da59e50ac51f9 | Silver RAT v1.0 Builder |
| a9fa8e14080792b67a12f682a336c0ea9ff463bbcb27955644c6fcaf80023641 | Silver RAT v1.0 Builder |
| 7a9aeea5e65a0966894710c1d9191ba4cbd6415cba5b10b3b75091237a70a5b8 | Silver RAT Payload |
| 0ace7ae35b7b44a3ec64667983ff9106df688c24b52f8fcb25729c70a00cc319 | Silver RAT Payload |
| 3b06b4aab7f6f590aeac5afb33bbe2c36191aeee724ec82e2a9661e34679af0a | Silver RAT Payload |
| 27b781269be3b0d2f16689a17245d82210f39531e3bcb88684b03ae620ac5007 | Silver RAT Payload |
| 0ace7ae35b7b44a3ec64667983ff9106df688c24b52f8fcb25729c70a00cc319 | Silver RAT Payload |
Recommendations
FPT Threat Intelligence recommends organizations and individuals take several measures to prevent this dangerous attack campaign:
Enhance user awareness and training:
Conduct regular training on social engineering techniques, especially recognizing phishing emails, fraudulent links, and dangerous attachments.
Encourage users not to open unfamiliar files or run software from unknown sources, even if sent by acquaintances.
Implement multi-layered protection (Defense-in-Depth):
Use antivirus software and EDR (Endpoint Detection & Response) capable of real-time behavior monitoring.
Update Windows Defender exclusion list monitoring to detect if malware attempts to add itself to the exclusion list.
Deploy internal Firewalls to block outbound connections from unknown sources (e.g., C2 connections from Silver RAT).
Enhance detection and response capabilities:
Install and configure process monitoring tools like Sysmon or Windows Event Logging to detect abnormal activities.
Use sandbox and honeypot to test unfamiliar software in an isolated environment.
Integrate tools like VirusTotal, Any.Run to scan and analyze malware behavior before actual deployment.
Apply strict security policies:
Disable script/macro execution rights in emails or office documents for users who do not need them.
Apply the principle of least privilege: do not grant users administrative rights unless absolutely necessary.
Block and monitor unused ports/applications, such as preventing access from unverified applications to the internet.
Maintain backup and recovery plans:
Establish automatic periodic data backup mechanisms and check the availability of backups.
Ensure backups cannot be accessed or encrypted by malware, for example, stored on separate (offline/offsite) devices.
References
Subscribe to my newsletter
Read articles from Tran Hoang Phong directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tran Hoang Phong
Tran Hoang Phong
Just a SOC Analyst ^^