What Is a WAF — and Why Your Web App Needs One
 Sharon
SharonWhen it comes to web security, most developers think of HTTPS, firewalls, and maybe some rate-limiting. But there’s one often-overlooked tool that can make a huge difference: the Web Application Firewall, or WAF.
Let’s break down what a WAF really does, how it works, and why it’s a critical layer in your website’s defense strategy.
What Is a WAF?
A Web Application Firewall (WAF) is a security tool designed to protect your web applications from common attacks by filtering, monitoring, and blocking HTTP traffic.
Unlike traditional firewalls that operate at the network layer, a WAF operates at the application layer (Layer 7 of the OSI model). It specifically guards against threats like:
SQL injection
Cross-site scripting (XSS)
Cross-site request forgery (CSRF)
Command injection
Path traversal
Malicious file uploads
How Does a WAF Work?
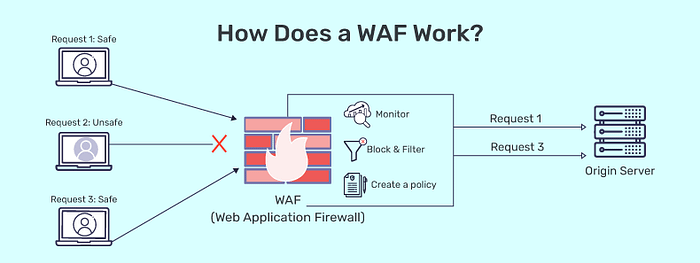
A WAF inspects all incoming traffic and uses predefined security rules to determine whether requests should be allowed or blocked. These rules are designed to identify suspicious patterns or known attack signatures.
When a user makes a request to your web server, the WAF intercepts it first, evaluates it for potential threats, and then decides whether to pass it on. It’s like a smart bouncer standing at the entrance of your application.
Why Use a WAF?
Web apps are constantly exposed to the internet — and attackers know it. Even small misconfigurations or unpatched libraries can open the door to devastating breaches.
Here’s what a WAF adds to your security toolkit:
Real-time protection from known and unknown attacks.
Application-layer filtering, going beyond what traditional firewalls can do.
Centralized rule management, making it easier to apply security consistently.
Visibility into traffic, which helps with threat hunting and incident response.
How to Choose a WAF
Not all WAFs are built the same. When evaluating your options, consider:
Security Coverage: Does it protect against OWASP Top 10 threats?
Performance: Will it slow down your site or scale with your traffic?
Integration: Is it compatible with your existing infrastructure?
Automation: Can it auto-update rulesets or work with CI/CD tools?
Cost: Open-source or commercial? SaaS or self-hosted?
Deployment and Configuration
Setting up a WAF depends on your stack. Here’s a general approach:
Identify your threat model: Understand what you need to protect.
Choose a suitable WAF: Options range from AWS WAF, Cloudflare, to open-source WAFs like SafeLine.
Configure rulesets: Apply default policies, and fine-tune as needed.
Monitor and iterate: No WAF is “set and forget.” Monitor logs, adjust rules, and stay updated.
The Future of WAFs
WAFs are evolving fast. Here’s what to expect:
AI-powered detection: Behavioral analysis and anomaly detection will make WAFs smarter and less reliant on static rules.
Cloud-native deployment: Seamless integration with modern infrastructure like Kubernetes and serverless platforms.
Security-as-code: Integration with DevSecOps workflows will turn WAF rules into version-controlled assets.
Final Thoughts
WAFs are no longer optional — they’re essential. As attacks grow more sophisticated, relying solely on HTTPS or network firewalls just doesn’t cut it. Whether you’re running a small blog or a high-traffic SaaS platform, a WAF can be the difference between staying safe and becoming a headline.
Subscribe to my newsletter
Read articles from Sharon directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
