Colab Fellowship - Week 2 project
 talk2felly
talk2felly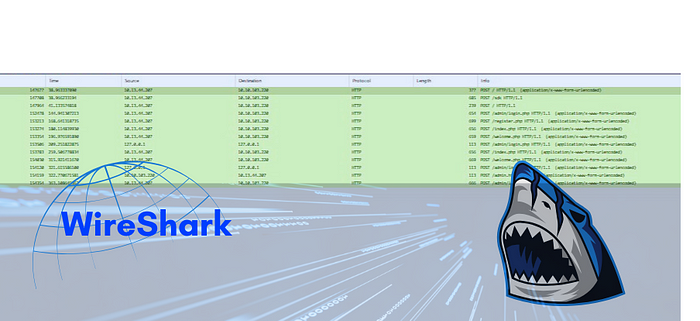
Practical - Network Security and Traffic Analysis
Capture and analyse HTTP vs HTTPS traffic
Detect malicious activity in a PCAP file using Wireshark filters
The objective of this project is to capture and analyze both HTTP and HTTPS network traffic using Wireshark, and to compare their differences in terms of visibility, security, and structure. This project aims to demonstrate an understanding of encrypted vs unencrypted web traffic and the role of protocols like HTTP and TLS in securing data in transit.
What is Wireshark?
Basically, it is an open-source tool that provides a user-friendly interface for analyzing network packets. It is widely used by security professionals and is very powerful. It offers a lot of information, which may be difficult to understand at first. However, as you spend more time using this tool, your skills will sharpen over time.
I have Wireshark installed on your system, and I also have a Pcap file to do further investigation.
- I selected the Ethernet network interface because it had a more active packet flow.

Above is my captured screen.
A. Capture and analyse HTTP vs HTTPS traffic
To distinguish between the two protocols, the following filters were used:
httpto display only unencrypted HTTP traffictlsto display only encrypted HTTPS traffic

The above image shows only HTTP traffic
HTTP Packet Analysis
From the screenshot, several HTTP GET and POST requests were logged, mostly from IP 192.168.241.3 to 51.222.109.195 and others. These requests were unencrypted. Also, most traffic originated from my machine (192.168.241.3) and reached out to multiple external IPs (e.g., 51.222.109.195).
I noticed Several interactions with smadav.net happened. This suggests that the application was checking for updates or sending statistics. I saw that Headers like User-Agent, Host, and even query parameters are visible, and this will pose a risk if it were a real-world application, especially if sensitive data is involved.

The above image shows encrypted HTTPS traffic.
HTTPS (TLS) Packet Analysis
The second screenshot reveals encrypted traffic using TLSv1.2 and QUIC. I checked and I saw that TLSv1.2 and QUIC are modern secure protocols used by browsers and apps like Chrome or GitLab. I observed more security features in the HTTPS packets.
To test the HTTPS, I went to my Chrome and opened the Gitlab.com website. Here’s what I found in the Transport Layer Security (TLS) session.
First, What is TLS?
TLS (Transport Layer Security) is a system that helps protect our data when we visit websites. It makes sure that:
No one can see our private information (like passwords).
No one can change what we send or receive.
That we’re talking to the right website, not a fake oneWhat is a TLS Session?
A TLS session is the secure connection between my device and any website I visit. In this case, I visited Gitlab.com
This session has 3 important steps: It’s popularly called the 3-way handshake
Summary
| Step | Name | What It Does |
| 1️⃣ | Client Hello + SNI | Browser says "Hi, I want to connect to gitlab.com" (domain visible). It includes a special field called SNI (Server Name Indication). |
| 2️⃣ | Encrypted Handshake | Browser and server agree on how to talk secretly |
| 3️⃣ | Application Data | Real data (like web pages) gets exchanged securely (can't be seen by anyone else) |
This info (gitlab.com) is not encrypted yet, so anyone monitoring the traffic (like a firewall or ISP) can see the domain name, but not the content.
Why Does This Matter?
SNI lets others see which site I’m visiting (but not what I’m doing on it).
The rest of the communication (handshake and data) is secure and hidden.
Firewalls, filters, or parental controls may use the SNI to block or allow certain websites.
Comparison Between HTTP and HTTPS Captures
Visibility of Payload Data
HTTP: Fully visible
HTTPS: Payload is encrypted
Encryption Indicators
TLSv1.2 and QUIC indicate secure channels. Their presence suggests modern app usage.
Security Implications
Any sensitive data over HTTP is vulnerable.
HTTPS ensures safer communication but limits deep inspection unless decrypted.
Weaknesses and Observations
HTTP exposes Sensitive Information
If a website loads some resources over HTTP and others over HTTPS, it's exposed to man-in-the-middle (MITM) attacks.
Auto-update mechanisms using plain HTTP are easily spoofed, they should be upgraded to HTTPS.
Detect malicious activity in a PCAP file using Wireshark filters
Aside checking the HTTP and HTTPS above, I also went deeper into my search to check more vulnerabilities.
DNS Tunnelling
I checked DNS (Domain Name Server) to check only DNS traffic just incase there are odd domain lookups or exfiltration attempts.

From what’s visible in the image above, the DNS queries are for legitimate and commonly used domains, such as:
These are related to known services (Grammarly, Google, Microsoft NTP, etc.).
They are using secure protocols (like HTTPS), and following normal DNS behavior (query + response).
There are no signs of:
Obfuscated or random-looking domains
Excessive or repeated DNS requests in short time (DNS tunneling or beaconing).
Suspicious Top-Level Domains (e.g.,
.tk,.xyz,.club, which are commonly abused).
This traffic doesn't look malicious.
Port Scan
In other to detect malicious activites, I check the tcp.flags.syn == 1 and tcp.flags.ack == 0 so I can see if there are new connection attempts (SYN packets). This will help me spot port scans or brute-force attacks.

From the image above I can see a normal number of SYN packets to trusted domains or IPs, and that’s expected. Also, responses are coming back which shows a SYN-ACKs communiaction.
We can also see that the standard ports are 80, 443, and the frequesncy is happening periodically.
This shows that the port scan is secure.
Malware Download
I also checked the comman-line use in traffic just incase there are malware activities. I used the following command
frame contains "cmd"orframe contains "powershell"

From the mage above, there is no attempt to download any executables. As such, this scan is does not show the presence of any malware activites. It is save.
I went further into my kali Linux to capture and scan strictly TCP and UDP ports, here’s what I found below.

The image above are TCP and UDP packets captured in my Linux Machine.
It was insightul doing this. I hope my fellowship mentor finds this a thorough work done.
See you in week 3… Until then, practice cyber hygiene.
Subscribe to my newsletter
Read articles from talk2felly directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

talk2felly
talk2felly
Cybersecurity Analyst// SecOps//Technical Writer//