LetsDefend Challenge: Fight the Virus
 Tameem Amjad
Tameem Amjad
lab link: https://app.letsdefend.io/challenge/Presentation-As-a-Malware/
MD5: 0289ee3c551ba84d34ab1760d042ab420733d96dbfedfae9718f8eb138c3259b
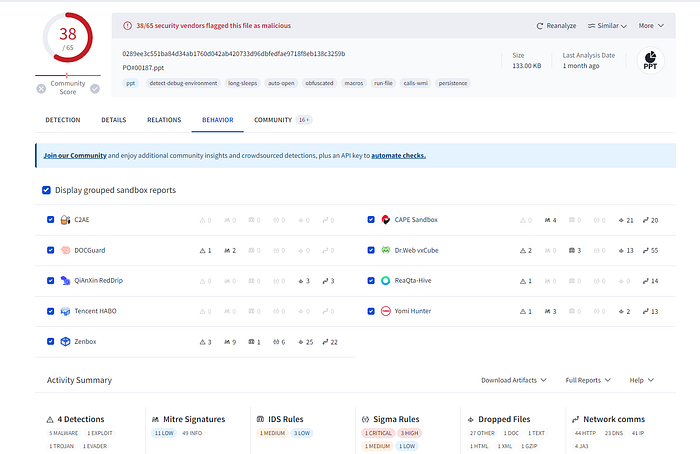
Question 1: What was the general name / category of the malicious file in the analyzed ppt file?
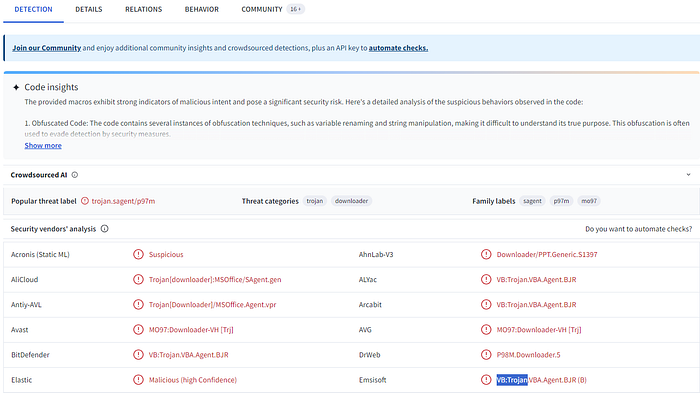
ANSWER : VB:Trojan
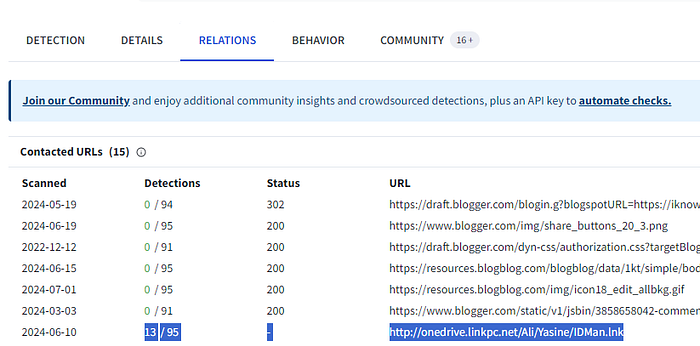
Question 2: Which of the url addresses it communicates with has been detected as harmful by sandboxes?
You can find this answer by navigating to the “Relations” tab in VirusTotal and reviewing the contacted URLs for the one that is marked as malicious.
Question 3: What is the name of the htm file that drops to disk?
This answer can be found in the “Relations” tab of VirusTotal under “Dropped Files”

Question 4: Which process is running persistently under mshta.exe after the relevant malware executes?
In the “Behavior” tab of VirusTotal, select Dr.Web from the dropdown menu to view the processes that have been created.
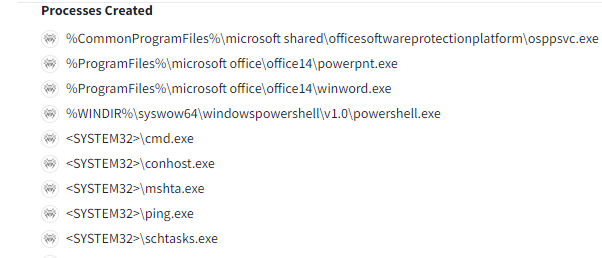
In the process tree, you can find the mshta.exe process. You'll notice it shows PowerPoint opening, followed by another process.
Answer is : “Schtasks.exe
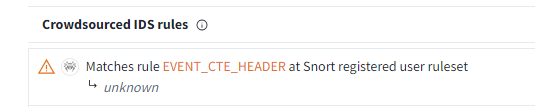
Question 5: If there had been a Snort IDS in the environment during the incident, which rules would it have matched?
To determine this, you’ll need to log in to VirusTotal. Once logged in, you can review the rules triggered by the file.
Subscribe to my newsletter
Read articles from Tameem Amjad directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tameem Amjad
Tameem Amjad
SOC Analyst @ Techpace | Top 2 @cyberdefender | VAPT | KQL | Azure sentinel | SentinelOne |EJPTv2 | CCD | CRTA | CEH | NETWORK+ | EDR | OSCP⌛️ | DFIR & cybersecurity