Complete Guide to Enterprise Single Sign-On: From Planning to Deployment
 Andy Agarwal
Andy Agarwal
Let’s start with a scenario that’ll probably sound familiar. Picture Sarah, an employee at a growing tech company. Every morning, she opens her laptop and goes through the same routine: logging into her email, then the CRM system, then the project management tool, then the HR portal, then the expense reporting system. By the time she’s entered all her passwords (and probably reset at least one she forgot), she’s already spent 15 minutes just getting access to the tools she needs to do her job.
Now multiply Sarah’s experience by 500 employees doing the same thing every day. That’s 125 hours of productivity lost daily, just on logging into systems. And we haven’t even talked about the security risks of people reusing passwords or writing them down because they can’t remember them all.
This is exactly the problem that Enterprise Single Sign-On (SSO) solves. Think of SSO as a master key for your digital workplace – one login that opens the door to every application your employees need. But here’s the thing: implementing enterprise SSO isn’t just about making logins easier. It’s about fundamentally changing how your organization manages identity, security, and access to digital resources.
Let me walk you through everything you need to understand about enterprise SSO, from the basic concepts to the practical steps for implementing it in your organization. We’ll build this understanding step by step, starting with the fundamentals and working our way up to the more complex considerations.
Understanding Enterprise SSO: Building the Foundation
Before we dive into implementation details, let’s make sure we’re all on the same page about what enterprise SSO actually is and why it’s different from simpler SSO solutions you might have encountered.
Enterprise SSO is a centralized authentication system that allows employees to access multiple applications and services using a single set of credentials. But calling it “centralized authentication” doesn’t really capture what makes enterprise SSO special. Let me give you a better way to think about it.
Imagine your company’s digital ecosystem as a large office building with dozens of different departments, each with their own locked rooms. Without SSO, every employee needs a different key for every room they need to access. They’re constantly fumbling with key rings, losing keys, and waiting for security to make new ones when they need access to a new room.
Enterprise SSO is like having a smart building where one security badge gives you access to exactly the rooms you’re supposed to enter, based on your role in the company. When you badge in at the main entrance, the building knows who you are and automatically unlocks the appropriate doors as you move through the building. You never have to think about access again – it just works.
But here’s where the analogy gets really interesting: this smart building system also keeps track of who went where and when, can instantly revoke someone’s access to all rooms when they leave the company, and can temporarily disable access if something seems suspicious. That’s the kind of comprehensive identity management that enterprise SSO provides.
Why Your Company Needs Enterprise SSO: The Business Case
Let’s talk about why organizations invest in enterprise SSO, because understanding the business drivers will help you build a stronger case for implementation and make better decisions about how to approach it.

The most obvious benefit is productivity improvement. Remember Sarah from our opening example? With SSO, her morning routine becomes: log in once, and all her applications are immediately accessible. That 15 minutes she was spending on logins can now be spent on actual work. Across a 500-person organization, that productivity gain adds up to significant cost savings.
But productivity is just the tip of the iceberg. The real business value of enterprise SSO comes from three areas that often get overlooked in initial discussions: security improvement, operational efficiency, and compliance capabilities.
From a security perspective, SSO dramatically reduces the attack surface for credential-based attacks. When employees only need to remember one strong password instead of dozens of weak ones, password security naturally improves. When IT teams can manage access centrally instead of across dozens of different systems, they can respond faster to security threats and ensure that access policies are consistently enforced.
The operational efficiency gains might be even more significant than the productivity gains. Think about what happens today when a new employee joins your company. Someone needs to create accounts for them in every system they’ll need access to. When someone changes roles, their permissions need to be updated across multiple systems. When someone leaves, their access needs to be revoked everywhere. With SSO, all of this happens centrally and can be largely automated.
Compliance is becoming increasingly important as data protection regulations become more stringent. SSO provides the kind of detailed audit trails and centralized access controls that compliance frameworks require. You can easily answer questions like “who accessed this sensitive data and when?” and “how do we ensure that only authorized personnel can access customer information?”
How Enterprise SSO Works: The Technical Foundation
Now that we understand why enterprise SSO matters, let’s build an understanding of how it actually works. Don’t worry – we’re going to start with the basic concepts and build up to the more technical details.
The fundamental architecture of enterprise SSO involves three main components: the identity provider (IdP), the service providers (the applications your employees use), and the authentication protocols that allow these systems to communicate securely.
Think of the identity provider as the central authority for user authentication – it’s like the security desk in our office building analogy. When an employee tries to access an application, instead of logging directly into that application, they’re redirected to the identity provider to prove who they are. Once the identity provider confirms their identity, it sends a secure message to the application saying “this person is John from the Marketing department, and here are the permissions they should have.”
The applications (called service providers in SSO terminology) trust the identity provider to handle authentication correctly. They don’t need to maintain their own user databases or password systems – they just need to understand the secure messages from the identity provider and grant access accordingly.
This trust relationship is established using standardized protocols like SAML (Security Assertion Markup Language) or OAuth/OpenID Connect. These protocols define exactly how the identity provider and applications should communicate to ensure that authentication information can’t be intercepted or forged by attackers.
Let me walk you through what happens when an employee tries to access an application with SSO enabled. First, the employee clicks on the application in their company portal or navigates to the application URL. The application recognizes that the user isn’t authenticated and redirects them to the company’s identity provider. The identity provider checks if the user is already logged in from a previous session – if they are, the process continues automatically. If not, the identity provider presents a login screen where the user enters their credentials.
Once the identity provider confirms the user’s identity, it creates a secure assertion (a digitally signed message) that contains information about the user and their permissions. This assertion is sent back to the original application, which validates the signature and extracts the user information. The application then logs the user in and grants them access based on the permissions specified in the assertion.
The beautiful thing about this process is that once a user is authenticated with the identity provider, they can access other SSO-enabled applications without logging in again. The identity provider remembers that they’re authenticated and can immediately create assertions for other applications.
Understanding SSO Protocols: SAML vs OAuth vs OpenID Connect
As you start planning your SSO implementation, you’ll encounter different protocols and standards, and it’s important to understand what each one does and when to use it. Let’s break down the three most common protocols you’ll encounter.
SAML (Security Assertion Markup Language) is the oldest and most established enterprise SSO protocol. Think of SAML as the formal, enterprise-grade protocol that was designed specifically for business environments where security and compliance are paramount. SAML assertions are XML documents that contain detailed information about the user and their permissions, and they’re cryptographically signed to prevent tampering.
SAML works particularly well in traditional enterprise environments where you have a clear identity provider (like Active Directory) and a set of applications that need to integrate with it. Many enterprise software vendors have built-in SAML support, making it relatively straightforward to integrate existing applications.
OAuth and OpenID Connect represent a more modern approach to authentication that was originally designed for web and mobile applications. If SAML is like a formal business letter with official letterhead and signatures, OAuth/OpenID Connect is like a secure text message – it accomplishes the same goal but with a more lightweight, flexible approach.
OAuth is actually an authorization protocol rather than an authentication protocol – it’s designed to answer the question “what is this user allowed to do?” rather than “who is this user?” OpenID Connect builds on top of OAuth to add authentication capabilities, creating a complete solution for both identity verification and permission management.
The choice between SAML and OpenID Connect often depends on your specific environment and requirements. SAML tends to work better in traditional enterprise environments with established identity management systems. OpenID Connect tends to work better in cloud-native environments or when you’re integrating with modern SaaS applications.
Many organizations end up supporting both protocols because different applications have different requirements. Your identity provider should be able to speak both languages, allowing you to integrate with whatever applications your organization needs to use.
Planning Your Enterprise SSO Implementation
Now that we’ve built a solid understanding of what enterprise SSO is and how it works, let’s talk about how to plan a successful implementation. This is where many organizations make critical mistakes that can derail the entire project, so we’re going to take a systematic approach to planning.
The first step in planning is conducting a comprehensive application inventory. You need to understand every application your organization uses, how employees currently access these applications, and what SSO capabilities each application supports. This sounds straightforward, but it’s often more complex than organizations expect.
Start by creating a list of all the applications your IT department officially supports. Then survey your employees to find out what other applications they’re using for work – you’ll probably discover shadow IT applications that aren’t on your official list. For each application, document how many users access it, how frequently it’s used, whether it contains sensitive data, and what authentication methods it currently supports.
Next, you need to prioritize which applications to include in your initial SSO rollout. Not every application needs to be included from day one, and trying to do everything at once can make the project unmanageable. Focus first on applications that are used by the most people, contain the most sensitive data, or cause the most password-related support tickets.
As you’re doing your application inventory, pay special attention to applications that don’t support modern SSO protocols. These legacy applications will require special handling – you might need to use a web proxy or screen scraping solution to provide SSO capabilities, or you might need to plan application upgrades as part of your SSO project.
The next major planning consideration is choosing your identity provider platform. This decision will affect every other aspect of your SSO implementation, so it’s worth taking time to evaluate your options carefully.
If your organization already uses Active Directory for internal authentication, you might want to consider Azure Active Directory (now called Microsoft Entra ID) as your SSO identity provider. This provides a natural migration path and integrates well with other Microsoft services your organization might be using.
Alternatively, you might consider specialized identity providers like Okta, Auth0, or Ping Identity. These platforms are designed specifically for SSO and often provide more flexibility and better integration with non-Microsoft applications.
The key factors to consider when choosing an identity provider include: integration capabilities with your existing systems, support for the SSO protocols your applications require, scalability to handle your user base, compliance with your industry’s regulatory requirements, and the vendor’s roadmap for future development.
Implementation Steps: From Design to Deployment
Let’s walk through the actual implementation process step by step. I’m going to break this down into phases that build on each other, allowing you to deliver value incrementally while minimizing risk.
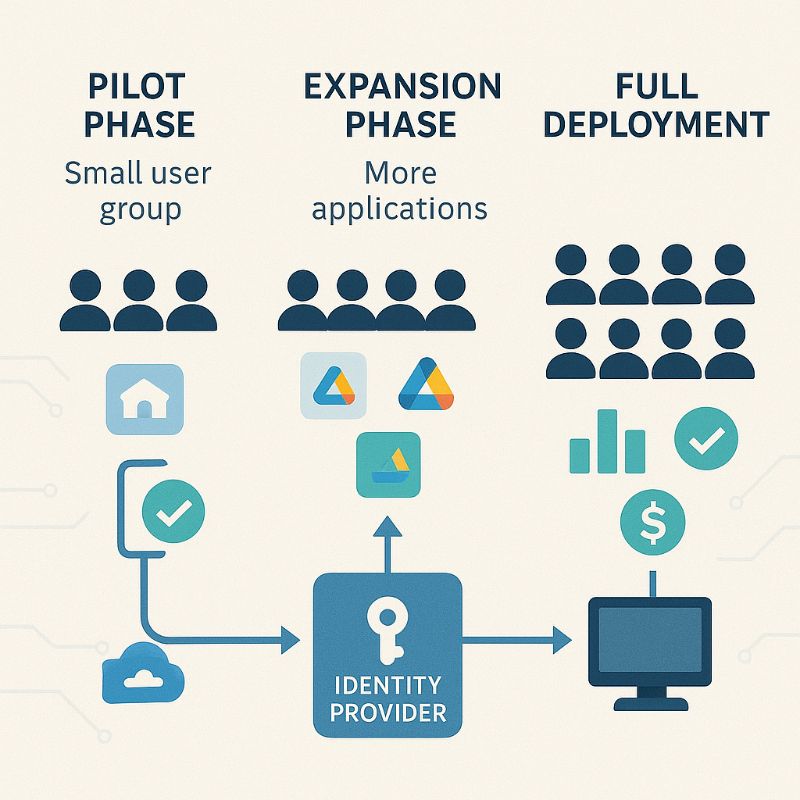
Phase one is pilot deployment with a small group of users and a limited set of applications. The goal of this phase is to validate your technical architecture and work out any integration issues before rolling out to your entire organization. Choose a group of tech-savvy users who can provide good feedback and are willing to help troubleshoot any issues that arise.
For your pilot applications, start with ones that have native SAML or OpenID Connect support and don’t require complex customization. This allows you to focus on getting the basic SSO flow working correctly without getting bogged down in application-specific integration challenges.
During the pilot phase, pay close attention to the user experience. How intuitive is the login process? Are there any steps that confuse users? How long does it take to access applications? The feedback you gather during this phase will be crucial for refining the experience before broader deployment.
Phase two expands the deployment to additional user groups and applications. This is where you’ll encounter more complex integration challenges and need to develop processes for handling edge cases. You’ll also start to see the operational benefits of centralized user management as you onboard new users and manage access changes through your SSO system.
During this phase, focus on developing your operational procedures. How will you handle access requests for new applications? What’s the process for troubleshooting SSO issues? How will you communicate changes to users? These operational aspects are just as important as the technical implementation.
Phase three is full organizational deployment. By this point, you should have worked out most of the technical and operational challenges, and the focus shifts to change management and user adoption. Plan for comprehensive user training and support during this phase, because even though SSO makes authentication easier, the change in process can be confusing for users initially.
Throughout all phases, maintain detailed documentation of your configuration, integration procedures, and troubleshooting guides. This documentation will be invaluable for ongoing maintenance and for training new team members who need to support the SSO system.
Overcoming Common Implementation Challenges
Let me share some of the most common challenges organizations face during SSO implementation and how to address them. Understanding these challenges upfront will help you plan more effectively and avoid common pitfalls.
The first major challenge is legacy application integration. Many organizations have critical applications that were built before modern SSO protocols existed, and these applications can’t be easily modified to support SAML or OpenID Connect. There are several strategies for handling these applications.
One approach is using a web proxy or gateway that sits between users and the legacy application. The proxy handles the SSO authentication and then automatically logs users into the legacy application using stored credentials or form-filling techniques. This approach works well for web-based applications but can be complex to set up and maintain.
Another approach is screen scraping or robotic process automation (RPA) to automate the login process for legacy applications. This is more complex but can work for applications that don’t have web-based interfaces.
The second major challenge is user adoption and change management. Even though SSO makes authentication easier in the long run, the transition period can be confusing for users. They need to learn new processes for accessing applications, and they might encounter temporary issues as applications are migrated to SSO.
Successful change management for SSO requires clear communication about the benefits users will experience, comprehensive training on the new processes, and robust support during the transition period. Consider creating video tutorials, quick reference guides, and having extra help desk support available during the rollout.
The third challenge is maintaining security during the transition. As you’re migrating applications to SSO, you might temporarily have inconsistent security policies across different systems. It’s important to maintain visibility into who has access to what during this transition period.
Consider implementing additional monitoring and alerting during the SSO rollout to detect any unusual access patterns or potential security issues. You might also want to require additional verification for access to particularly sensitive applications during the transition period.
Best Practices for Enterprise SSO Success
Based on what I’ve seen work well in successful SSO implementations, let me share some best practices that can make the difference between a smooth deployment and a problematic one.
First, invest heavily in user experience design. The goal of SSO isn’t just to centralize authentication – it’s to make accessing applications easier and more intuitive for users. Spend time designing login flows that make sense to your users, and test these flows with real users before rolling them out broadly.
Pay particular attention to error handling and recovery processes. When something goes wrong with SSO (and something always goes wrong eventually), users need clear guidance on how to get back to work. Design error messages that explain what happened and what users should do next, rather than just displaying technical error codes.
Second, implement comprehensive monitoring and alerting from the beginning. SSO becomes a critical piece of infrastructure that affects access to all your applications, so you need to know immediately if there are any issues. Monitor not just the availability of your SSO system, but also success rates, response times, and error patterns.
Set up alerts for unusual authentication patterns that might indicate security issues – things like login attempts from unusual locations, multiple failed authentication attempts, or access to applications outside normal business hours.
Third, plan for disaster recovery and high availability from the start. If your SSO system goes down, users can’t access any of their applications, which means your entire organization stops working. This makes SSO availability even more critical than the availability of individual applications.
Design your SSO architecture with redundancy and failover capabilities. Have procedures for quickly switching to backup systems if your primary SSO system fails. And make sure you have emergency access procedures that allow critical personnel to access essential systems even if SSO is unavailable.
Fourth, maintain detailed documentation and runbooks for your SSO implementation. This includes not just technical documentation about how the system is configured, but also operational procedures for common tasks like onboarding new applications, troubleshooting authentication issues, and managing user access.
Your documentation should be detailed enough that a new team member could understand and maintain your SSO implementation. This is particularly important because SSO expertise tends to be specialized, and you don’t want your organization to be dependent on one or two people who understand how everything works.
Security Considerations for Enterprise SSO
Let’s spend some time talking about the security implications of enterprise SSO, because while SSO can significantly improve your organization’s security posture, it also creates new types of risks that need to be managed.
The most obvious security benefit of SSO is password security improvement. When users only need to remember one password instead of dozens, they’re more likely to choose strong passwords and less likely to reuse passwords across multiple systems. This reduces the risk of credential-based attacks significantly.
SSO also improves your ability to enforce consistent access policies across all applications. Instead of trying to manage user permissions in dozens of different systems, you can define access policies centrally and have them enforced consistently everywhere. This reduces the risk of users having inappropriate access to sensitive systems.
However, SSO also creates new security risks that need to be carefully managed. The most significant risk is that SSO creates a single point of failure for authentication. If an attacker compromises a user’s SSO credentials, they potentially gain access to all applications that user can access. This makes protecting SSO credentials even more critical than protecting individual application passwords.
The solution to this risk is implementing multi-factor authentication (MFA) for SSO access. MFA requires users to provide something they know (their password) plus something they have (like a phone or hardware token) to authenticate. This makes it much harder for attackers to gain access even if they steal or guess passwords.
Choose MFA methods that balance security with user experience. Push notifications to mobile apps tend to work well for most users, while hardware tokens might be appropriate for users who access particularly sensitive systems. Avoid SMS-based MFA if possible, as SMS can be intercepted or redirected by attackers.
Another important security consideration is session management. With SSO, users typically stay logged in for extended periods to avoid having to re-authenticate frequently. This creates the risk that an unattended device could be used to access applications without authorization.
Implement intelligent session management that considers factors like user location, device characteristics, and access patterns to determine when to require re-authentication. For example, you might require re-authentication if a user tries to access a sensitive application from a new device or location, even if their SSO session is still valid.
Integration Patterns and Architecture Decisions
As you design your enterprise SSO architecture, you’ll need to make several important decisions about how to structure the system and integrate it with your existing infrastructure. Let me walk you through the key architectural patterns and help you understand when to use each one.
The first architectural decision is whether to use a cloud-based identity provider or deploy an on-premises solution. Cloud-based providers like Azure Active Directory or Okta offer the advantage of managed infrastructure and automatic updates, but they require trusting a third party with your authentication data. On-premises solutions give you more control but require more internal expertise to manage and maintain.
Many organizations choose a hybrid approach, using a cloud-based identity provider for most applications but maintaining on-premises identity systems for particularly sensitive applications or compliance requirements. This approach requires careful planning to ensure consistent user experiences and security policies across both environments.
The second major architectural decision is how to handle user provisioning and lifecycle management. User provisioning is the process of creating, updating, and deleting user accounts across all your applications when employees join, change roles, or leave the organization.
The simplest approach is just-in-time (JIT) provisioning, where user accounts are created automatically in applications the first time a user accesses them via SSO. This works well for applications that don’t require complex permission structures, but it doesn’t handle role changes or account cleanup when users leave.
A more comprehensive approach is implementing SCIM (System for Cross-domain Identity Management) provisioning, where your identity provider actively manages user accounts across all applications. This provides better lifecycle management but requires more complex integration work.
The third architectural consideration is how to handle applications that can’t support modern SSO protocols. As we discussed earlier, legacy applications often require special handling through proxies, gateways, or screen scraping solutions.
When designing these integrations, prioritize solutions that provide audit trails and session management capabilities. You want to maintain visibility into who accessed what applications and when, even for legacy systems that don’t natively support these capabilities.
Measuring Success and Continuous Improvement
Once your SSO system is deployed, it’s important to establish metrics for measuring success and processes for continuous improvement. SSO isn’t a “set it and forget it” technology – it requires ongoing attention to maintain security, improve user experience, and adapt to changing organizational needs.

Start by establishing baseline metrics before SSO deployment so you can measure the impact accurately. Key metrics to track include password reset requests (which should decrease significantly with SSO), time spent on authentication (which should decrease), security incidents related to credential compromise (which should decrease), and user satisfaction with the login experience (which should improve).
Also track operational metrics like SSO system availability, authentication success rates, and response times. These metrics help you identify potential issues before they affect users and provide data for capacity planning as your organization grows.
Set up regular reviews of your SSO implementation to identify opportunities for improvement. This might include adding new applications to SSO, improving integration with existing applications, or updating security policies based on new threats or compliance requirements.
Pay particular attention to user feedback about the SSO experience. Users often identify pain points or inefficiencies that aren’t obvious from technical metrics alone. Regular user surveys or feedback sessions can provide valuable insights for improving the system.
Consider implementing advanced capabilities like adaptive authentication, which adjusts security requirements based on risk factors like user location, device characteristics, and access patterns. These capabilities can improve both security and user experience by requiring additional verification only when it’s actually needed.
Future-Proofing Your SSO Investment
As you’re implementing enterprise SSO, it’s worth thinking about how your needs might evolve in the future and designing your system to accommodate those changes. Technology trends like remote work, cloud adoption, and zero-trust security are changing how organizations think about identity and access management.
The shift to remote work has made SSO even more critical, as employees access applications from a variety of locations and devices. Make sure your SSO solution can handle authentication from any location and provides appropriate security controls for remote access scenarios.
Cloud adoption is changing the application landscape, with organizations using more SaaS applications and fewer on-premises systems. Ensure that your SSO solution integrates well with cloud applications and can adapt as your application portfolio evolves.
Zero-trust security models assume that no user or device should be trusted by default, requiring verification for every access request. Modern SSO systems are evolving to support zero-trust principles through capabilities like continuous authentication and risk-based access controls.
Consider how emerging technologies like artificial intelligence and machine learning might enhance your SSO implementation. These technologies can improve fraud detection, automate access policy management, and provide better insights into user behavior patterns.
The most important thing is choosing an SSO platform and architecture that can evolve with your organization’s needs. Avoid solutions that lock you into proprietary protocols or limit your ability to integrate with new technologies as they emerge.
Enterprise SSO is a foundational investment in your organization’s digital infrastructure. When implemented thoughtfully, it provides immediate benefits in productivity and security while establishing a platform for future identity and access management capabilities. The key to success is understanding both the technical and organizational aspects of SSO, planning carefully for implementation, and maintaining focus on continuous improvement.
Remember that SSO implementation is as much about change management and user experience as it is about technical integration. The organizations that achieve the most success with SSO are those that treat it as a strategic initiative that affects how people work, not just a technical project that affects how systems authenticate users.
Subscribe to my newsletter
Read articles from Andy Agarwal directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
