Staying Safe from Modern Phishing Attacks: A Guide for BoldSign Users
 BoldSign
BoldSign
Phishing attacks are evolving rapidly, with attackers exploiting trusted platforms to steal sensitive data. BoldSign is dedicated to keeping your information secure, but staying safe requires awareness of modern phishing tactics. This guide explains how these attacks work, how to spot them, and what BoldSign does to protect you.
Why phishing matters
Phishing attacks have evolved far beyond traditional email scams, now employing sophisticated tactics like QR code phishing and OAuth exploitation. These methods trick users into sharing sensitive credentials, clicking malicious links, or installing malware. As a pervasive and growing threat, phishing compromises personal and organizational security worldwide. BoldSign empowers users to recognize and avoid modern phishing scams while maintaining robust security measures.
QR code phishing
Attackers send emails posing as a business, where they embed QR codes that seem legitimate. Scanning these codes leads to malicious websites that steal credentials, install malware, or prompt unauthorized actions. The QR code hides the true URL, making it hard to spot the danger.

| Full URL extracted from QR code | Redirect to phishing URL |
| hxxp://legit_domain/ViewSwitcher/SwitchView?mobile=False&returnUrl=hxxps://ebjv[.]com[.]au/filesharer | hxxps://ebjv[.]com[.]au/filesharer |
| hxxp://legit_domain/redirect/head/?u=hxxps://trusted_domain[.]statementquo[.]com/ey8YO?e={user_email} | hxxps://trusted_domain[.]statementquo[.]com/ey8YO?e={user_email} |
How to stay safe:
To avoid phishing scams, here are a few tips to follow:
Avoid scanning QR codes from unsolicited emails.
Contact support@boldsign.com to verify the email’s authenticity.
Use online QR code scanners to preview URLs before visiting.
Check for suspicious domains or non-secure (HTTP) links.
Screenshot and report suspicious QR codes to BoldSign support.
Note: BoldSign never uses QR codes in emails to prompt app access or actions. Do not scan any QR code claiming to be from BoldSign, and report it immediately instead.
OAuth consent phishing
Attackers sometimes create fake OAuth apps that mimic BoldSign, displaying consent screens that request minimal access to gain access tokens. These screens appear harmless but allow attackers to infiltrate accounts or redirect users to malicious sites without needing passwords.
For example, an email with a link or attachment could trigger a Microsoft OAuth prompt. An “unverified” label below the app’s name indicates it’s malicious.
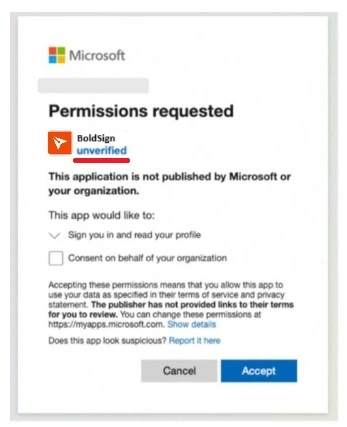
How to stay safe:
To avoid fake OAuth consent, here are a few tips:
Verify the source of any OAuth app requesting access.
Be cautious of unexpected or vaguely named apps.
Look for “unverified” labels on consent screens.
Cancel suspicious requests and confirm with BoldSign support.
Note: BoldSign does not initiate OAuth requests for third-party apps without user consent. Never approve such requests claiming to be from BoldSign, and report them to support@boldsign.com instead.
Fake login pages
Phishing emails with urgent messages like “View an important document” direct users to fake login pages that mimic the BoldSign login portal. Entering credentials on these pages hands them directly to attackers.
Note: For more information, please visit https://phishingeducation.uconn.edu/
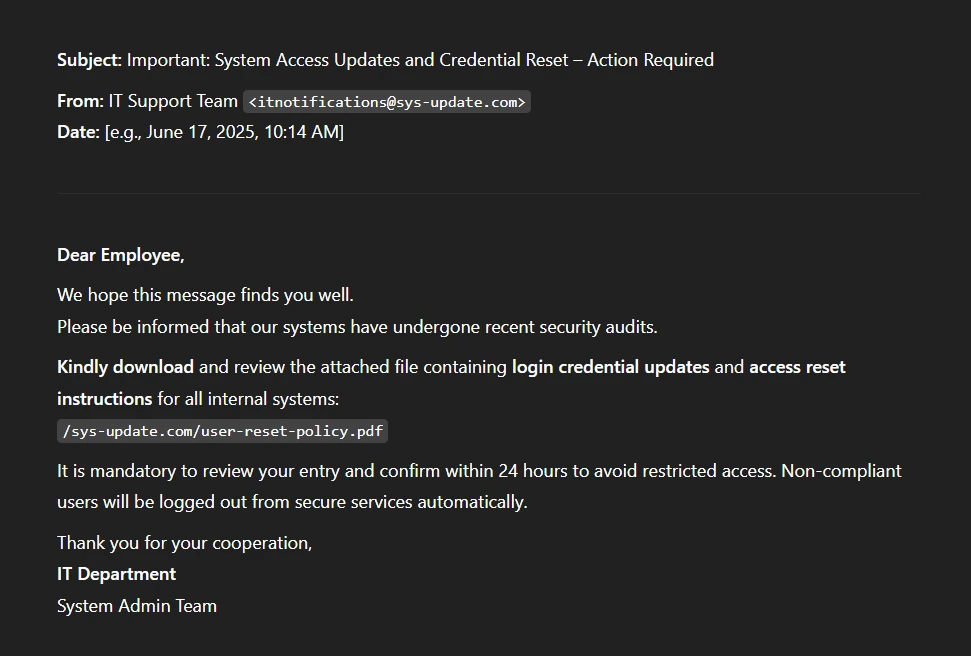
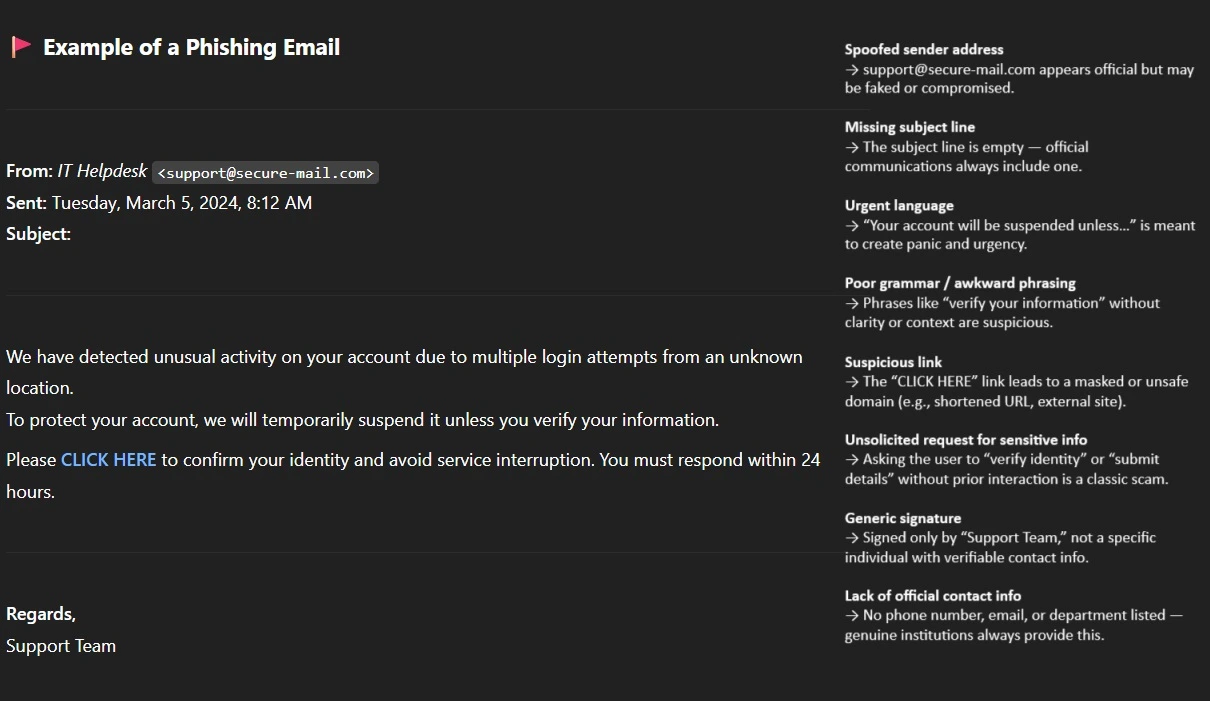
How to stay safe:
Avoiding fake login screens can be tricky, but here are a few tips:
Hover over links to preview their destination.
Watch for suspicious domains or pages with subtle design flaws.
Avoid entering credentials via email links.
Use tools like Norton Safe or VirusTotal to check site safety.
Navigate directly to www.boldsign.com for login.
Note: BoldSign never requests credentials through email links. Only log in via official .boldsign.com domains. Report suspicious links to support.
How to spot suspicious emails
Before acting on any email, ask:
Were you expecting this message?
Does the sender’s email address look legitimate?
Is the email’s tone, grammar, or design unusual?
Does it use current branding?
Are links or QR codes directing to boldsign.com with https at the start?
Is there an urgent or emotional appeal?
Tips:
Enable multi-factor authentication (MFA) for extra protection.
Use unique, strong passwords.
Keep antivirus software updated.
How BoldSign keeps you secure
BoldSign prioritizes your safety with:
Verified communications: All emails come from secure, authenticated channels.
No QR codes: We never use QR codes in emails for any purpose.
No unauthorized OAuth: We don’t request third-party app access without your explicit consent.
Secure logins: Only .boldsign.com domains are used for login prompts.
Proactive defenses: AI-driven tools analyze threats reported to support@boldsign.com, and we collaborate with security experts to neutralize malicious sites.
DMARC protection: Spoofed emails claiming to be from boldsign.com are blocked and analyzed through domain-based message authentication, reporting, and conformance (DMARC).
Take action
Stay vigilant and report suspicious emails to support@boldsign.com. By combining your awareness with BoldSign security measures, we can keep your data safe from phishing threats.
Related blogs
How BoldSign Users Can Stay Safe Online from Fraud and Email Scams
BoldSign Wins Crozdesk’s Quality Choice Award and Happiest Users Award!
Explore BoldSign eSignature APIs in Postman: A Step by Step guide
Note: This blog was originally published at boldsign.com
Subscribe to my newsletter
Read articles from BoldSign directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

BoldSign
BoldSign
BoldSign is a secure, legally compliant e-signature solution for businesses and individuals. It simplifies document signing with a user-friendly platform and powerful API & SDK for easy integration. Send, sign, and manage contracts effortlessly.