Carnege Room | TryHackMe
 Dhwanit Pandya
Dhwanit PandyaWelcome to the Carnage Room on Try Hack Me!
So, it's extremely important to have your Wireshark basics clear before starting this room, as it is a medium-difficulty room and definitely not going to be a walk in the park.
Scenario: One of the employees of a company received an email with a malicious file attachment from a known contact. The SOC team comes into action when they are alerted about the suspicious outbound connections established by that user's workstation.
Alright, let's get started!
TASK 2: Traffic Analysis
1. What was the date and time for the first HTTP connection to the malicious IP?
In order to find the first HTTP connection to the malicious IP, we first need to identify the user's IP and then look for any GET requests made by the user, maybe to fetch a file, and that IP is in fact the malicious IP that we are looking for.
We begin by resolving the IP addresses by
Edit-> Preferences-> Name Resolution-> Resolve IP addresses
We get the user's IP that corresponds to the resolved address, Desktop... and then we simply use the display filter
http.request.method=="GET"
And the first row gives us the answer.
Note: To get the answer in the desired format, we need to change the time display format by using View-> Time Display Format-> Date and Time of Day.
2. What is the name of the zip file that was downloaded?
From the previous task, the file that was associated with that packet is the file that was downloaded.
3. What was the domain hosting the malicious zip file?
Inspecting the same packet after IP address resolution gives us the answer.
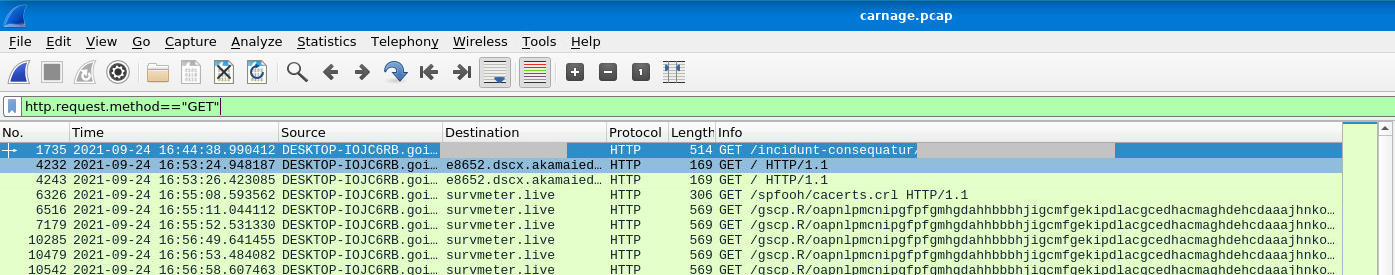
4. Without downloading the file, what is the name of the file in the zip file?
We can directly see the metadata of a file under the packet bytes window in plaintext. Now, in order to get the name of the file inside the zip file, we need to look at the corresponding response that is the very next response, and check the ASCII that you can find in the packet bytes window, we look for extensions (eg, .doc or .xls) for easy identification.
We also need to apply the display filter of http
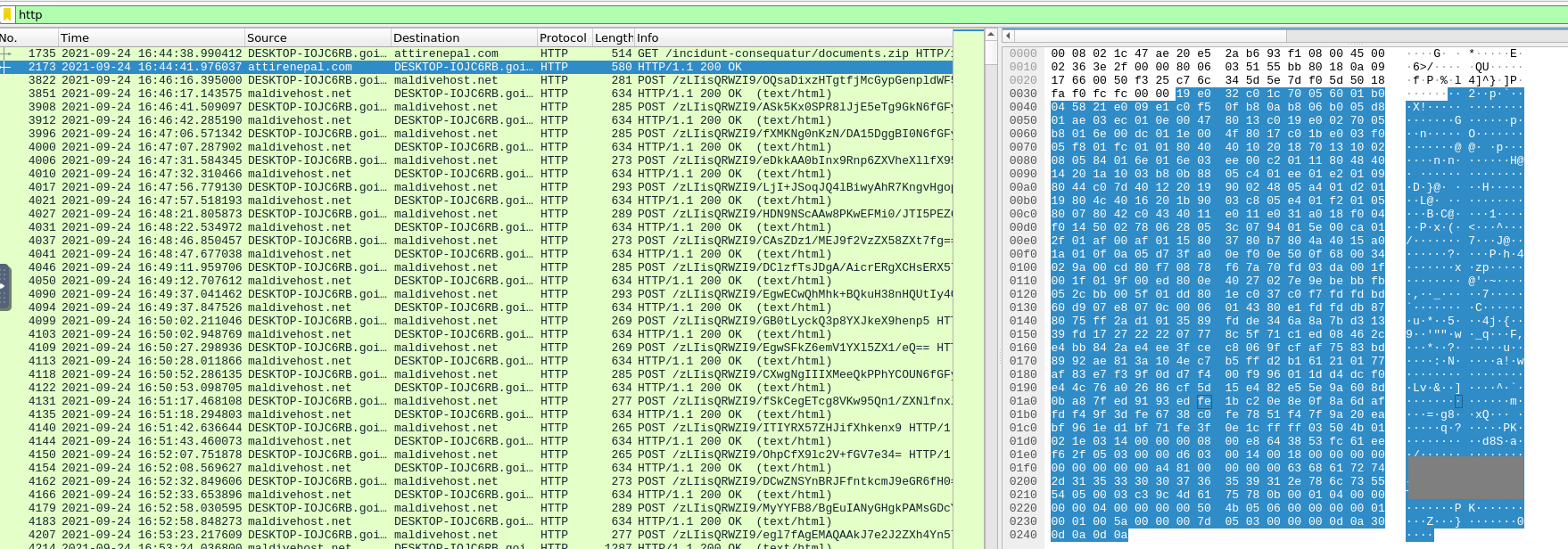
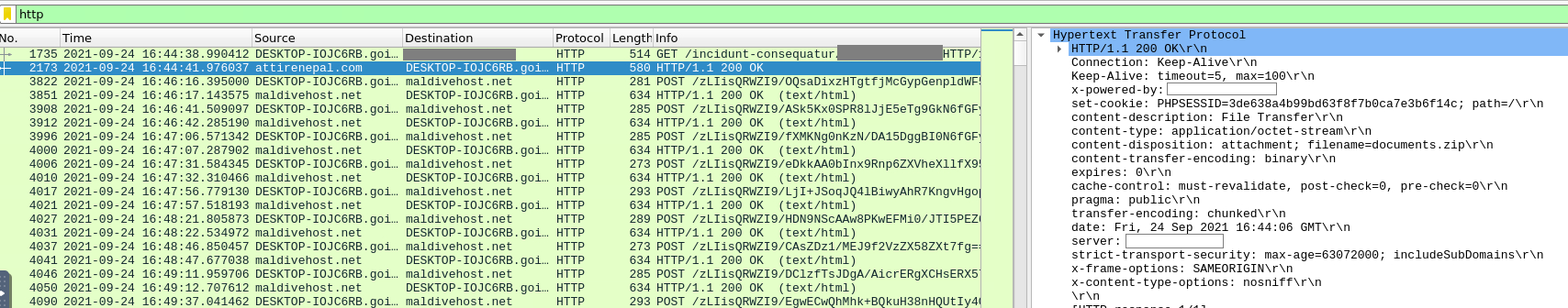
5. What is the name of the webserver of the malicious IP from which the zip file was downloaded?
This was very easy to find, webserver details are generally found inside the HTTP details under the packet details section. So, we inspect the packet we received the HTTP response from.
6. What is the version of the webserver from the previous question?
On the same window, the version of the server is also clearly mentioned
7. Malicious files were downloaded to the victim host from multiple domains. What were the three domains involved with this activity?
This question really took me a bit longer in order to determine which filters would work best for me in this scenario. I already had the IP addresses resolved to their domains from the start. I started by filtering the traffic with the source IP as the user's IP. But there were a lot of packets, and it was difficult to figure out.
Then I thought there should be some more filtering criteria, which I found out in the hint, which was the time frame and the protocol being used i.e, HTTPS
HTTPS works on port 443, so using this along with the time frame given, I created a display filter
tcp.port==443 and (frame.time>="2021-09-24 16:45:11") && (frame.time<="2021-09-24 16:45:30") and ip.src_host=="DESKTOP-IOJC6RB.goingfortune.com"
I was able to reduce the number of filtered packets significantly, but I still had a chunk of packets. One good sign was that domains were reduced to a max of 6-8.
While analyzing the packets, I realized I could also filter by the TLS Handshake, as HTTPS uses TLS for encryption. So I replaced this with the port in my filter.
tls.handshake.type==1 and (frame.time>="2021-09-24 16:45:11") && (frame.time<="2021-09-24 16:45:30") and ip.src_host=="DESKTOP-IOJC6RB.goingfortune.com"
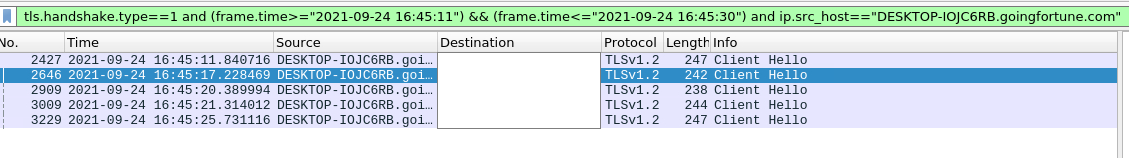
After applying this filter, I was just left with 5 Packets with 5 domains, out of which 3 were malicious. To find the malicious domains, I used VirusTotal, which clearly flagged 3 malicious and 2 safe domains.
8. Which certificate authority issued the SSL certificate to the first domain from the previous question?
Honestly, I did not know where I could find the certificate, but I knew that the TLS handshake process makes use of a certificate, so I began exploring TLS handshake filter options and found tls.handshake.certificate which I used in my filter, keeping the timeframe intact.
(frame.time>="2021-09-24 16:45:11") && (frame.time<="2021-09-24 16:45:30") and tls.handshake.certificate
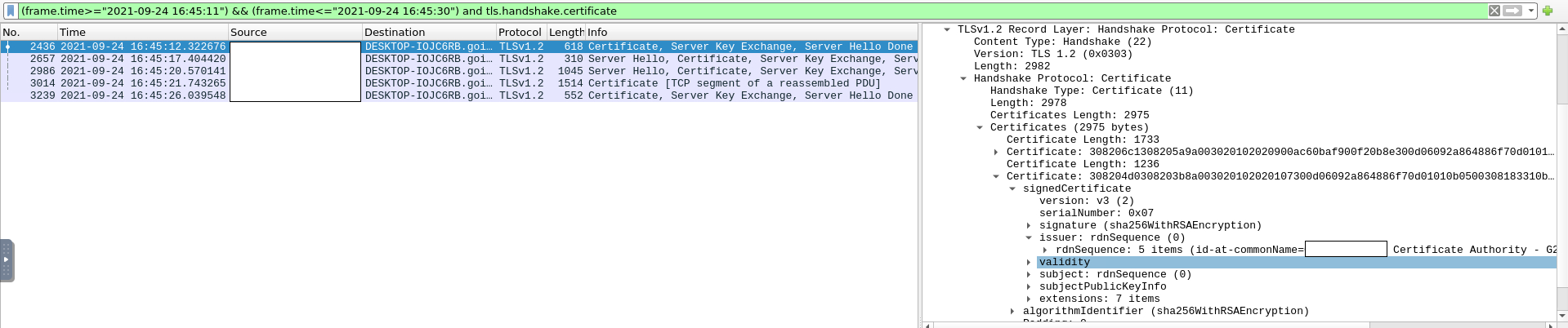
From there, I inspected the packet details window, and under TLS, I found the certificate field, and inside that issuer field, which was the answer.
9. What are the two IP addresses of the Cobalt Strike servers? Use VirusTotal (the Community tab) to confirm if IPs are identified as Cobalt Strike C2 servers.
This question was challenging for me as I did not know much about the Cobalt strike servers and had never identified a C2 server before using packet analysis. What I knew was that Command and Control is a central server used by the attacker to send malicious commands to the machines infected by malware.
I knew for sure that I could use POST to filter as commands are being sent. Using this as a filter, I got 28 filtered packets. One interesting thing was that there were 2 packets that were pointing to the same IP, and their packet length was around 4 times bigger than the others.
I took that IP and checked with VirusTotal, and it was associated with a Cobalt Strike server when I looked at the community section. Additionally, I also learned that they were in the network range 185[.]0[.]0[.]0 - 185[.]255[.]255[.]255.
With a bit of additional research about Cobalt Strike servers, I found that these generally run on ports 80 443 and 8080.
Using this knowledge, I created this filter
http.request.method=="POST" or tcp.dstport in {80 443 8080}
Using this filter, I found the other IP, which was in the network range that I talked about.
10. What is the Host header for the first Cobalt Strike IP address from the previous question?
The host header is generally found in the HTTP details under the packet details window under HOST for that particular IP.
11. What is the domain name for the first IP address of the Cobalt Strike server? You may use VirusTotal to confirm if it's the Cobalt Strike server
We have this in front of us under destination since I already had resolved the IP addresses at first.
An interesting observation is that the Host header in the HTTP request claims to target a legitimate domain, but the actual connection is made to a different, likely malicious domain. Ideally, the destination IP and the Host header should align, since the DNS resolution of the domain typically determines the IP to connect to. However, in this case, they don’t match.
This mismatch is often a sign of malicious activity. Malware commonly uses this technique to disguise outbound connections, making it appear as if it’s communicating with a trusted service, while in reality, it’s contacting a command-and-control (C2) server. This tactic is typically used after a system is infected to evade detection by security tools.
12. What is the domain name of the second Cobalt Strike server IP? You may use VirusTotal to confirm if it's the Cobalt Strike server
We can simply repeat the same process that we followed above to get the domain for the first one.
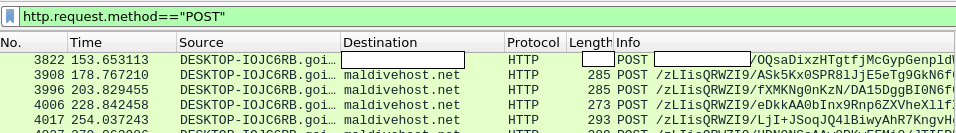
13. What is the domain name of the post-infection traffic?
This was straightforward, simply filter using
http.request.method=="POST"
The first packet that we get is the answer
14. What are the first eleven characters that the victim host sends out to the malicious domain involved in the post-infection traffic?
It is the same packet that we inspected above; the information asked for can be found in the Info column.
15. What was the length of the first packet sent out to the C2 server?
The packet that we are inspecting from the last 2 questions is, in fact, the first packet sent, and the length can be found under the Length column.
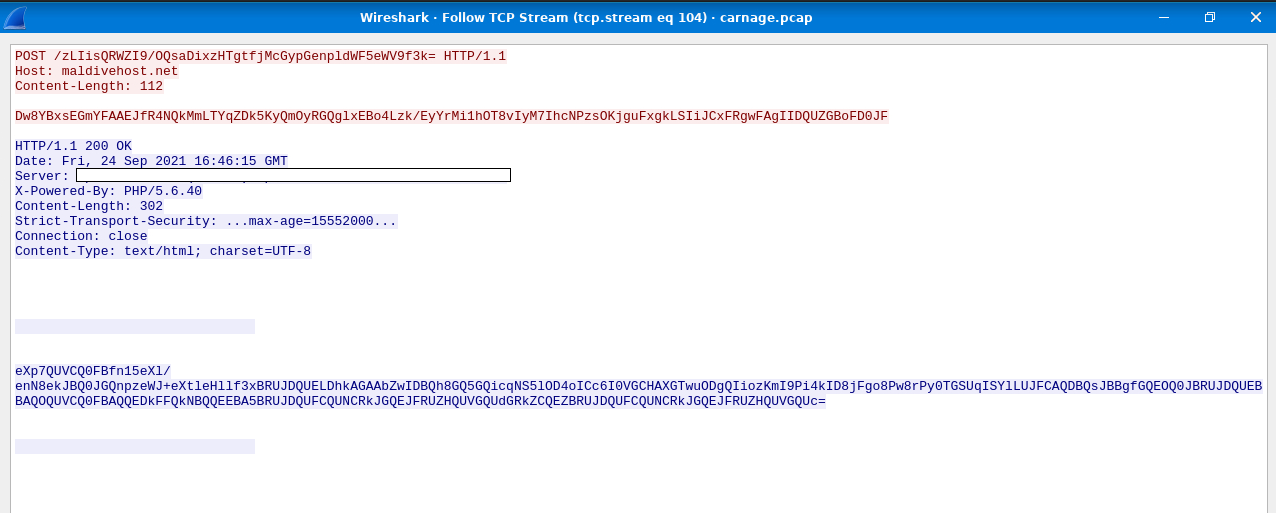
16. What was the Server header for the malicious domain from the previous question?
We know we can find it in the TCP flow (Analyze-> Follow-> TCP), Red-Client, and Blue-Server.
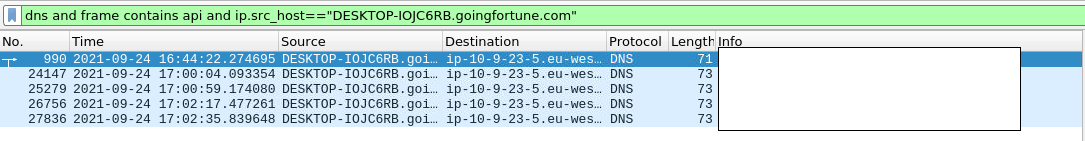
17. The malware used an API to check for the IP address of the victim’s machine. What was the date and time when the DNS query for the IP check domain occurred?
We simply filter by the victim's machine's IP address, filter by the 'api' word, and obviously also by DNS since we have dns query.
dns and frame contains api and ip.src_host=="DESKTOP-IOJC6RB.goingfortune.com"
We only have 2 domains, and it is not difficult to identify the suspicious one from the two. The answer is the time associated with the first packet of interaction.
18. What was the domain in the DNS query from the previous question?
The previous question easily answers this since you have already identified the malicious domain.
19. Looks like there was some malicious spam (malspam) activity going on. What was the first MAIL FROM address observed in the traffic?
Since mail is used, the first thing that clicked was the use of the email protocol SMTP. Additionally, we can find the hint in the question itself, i.e, to filter using 'MAIL FROM'
smtp and frame contains "MAIL FROM"
The first packet that contains the email is our answer.
20. How many packets were observed for the SMTP traffic?
The last one is a freebie, just filter by SMTP.
The count of packets is displayed at the bottom.
It was a challenging room, I must say. Congratulations on completing this room! 🎉
Professional Analysis
Detection & Impact
Wireshark is truly an underrated tool. Despite having used it for a long time, each session continues to reveal just how powerful it really is. This room demonstrated that Wireshark is far more than just a packet analysis tool, it's an essential asset for security teams. Not only can it identify malicious traffic, but it can also help detect command-and-control (C2) server communications. By applying specific filters, Wireshark can uncover unusual data exfiltration patterns and unauthorized captures. It also plays a crucial role in identifying malware-infected machines through network behavior, infections that, if left undetected, could escalate into ransomware attacks or credential theft.
Real-World Application
In real-world environments, Wireshark is a critical tool for network administrators, cybersecurity professionals, and incident responders. It is widely used for troubleshooting network issues, such as latency, packet loss, and misconfigured protocols. In the field of cybersecurity, Wireshark helps detect malicious traffic patterns, unauthorized data exfiltration, and command-and-control (C2) communications. For instance, during a suspected malware outbreak, analysts can use Wireshark to trace unusual DNS requests, identify beaconing behavior, or analyze payload delivery over HTTP/S. Additionally, it supports forensic investigations by allowing teams to reconstruct the timeline of an attack using packet captures. From corporate networks to critical infrastructure, Wireshark provides deep visibility that’s essential for both reactive and proactive security.
Security Implications
For businesses, these attacks can result in stolen credentials, loss of intellectual property, and violations of regulatory compliance. To reduce these risks, it is crucial to have robust endpoint monitoring in place, as was done in this case, along with well-defined Incident Response Plans aligned with NIST 800-61r3 (or the latest version). Employee education on phishing and insider threats is also vital. Users should be encouraged to promptly report any suspicious behavior to the security team. Moreover, since social engineering remains the primary cause of cyberattacks, fostering a strong security culture and providing continuous user awareness training are essential steps to safeguard organizational assets.
Subscribe to my newsletter
Read articles from Dhwanit Pandya directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Dhwanit Pandya
Dhwanit Pandya
I am a passionate computer science enthusiast deeply invested in software development, Cybersecurity, and Cloud Security. Throughout my academic journey, I've showcased my passion by crafting innovative projects for competitions and hackathons, honing my problem-solving skills. As a Senior Analyst in Tech Consulting (Cybersecurity) at EY, I've actively contributed to various projects, leveraging my analytical skills, and delving into emerging fields like DevSecOps and cloud security. Now, I'm eagerly seeking opportunities to apply my technical skills, gain valuable experience, and contribute to impactful projects.