Understanding Network Security in the Cloud
 Ronney Otieno
Ronney Otieno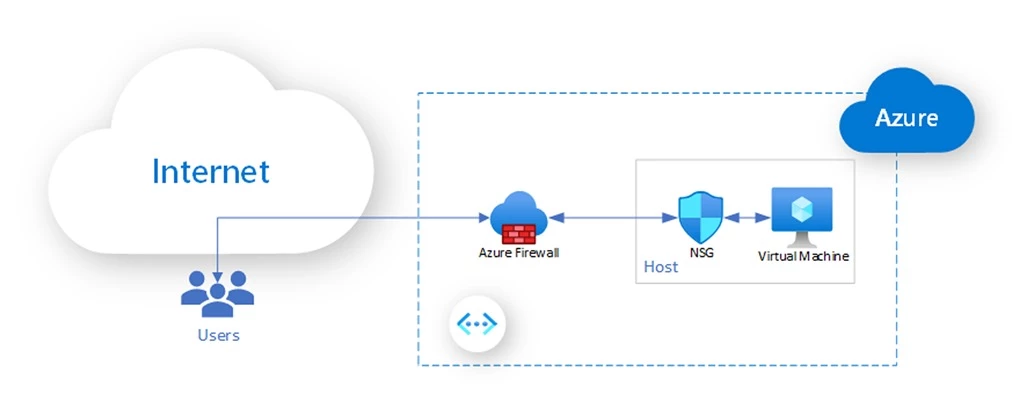
Securing Your Azure Environment from the Outside In
When deploying applications and services to the cloud, it's not enough to just "launch and go." Just like physical buildings need fences, locks, and security guards, cloud environments need perimeter defense, and that’s where network security comes in.
In this blog, you will learn the basic concepts about network security in the cloud.
First, let’s understand what the cloud is…
What Is the Cloud?
The cloud is a way to access and use computing resources — like servers, storage, databases, and software — over the internet, instead of owning and managing physical computers yourself.
So instead of: Buying a physical server, setting it up in your office, installing and updating software manually,
You can just rent what you need from a cloud provider (like Microsoft Azure, Amazon Web Services, or Google Cloud) — and only pay for what you use.
This is how it works
When you use the cloud:
Your data and applications are stored in data centers run by cloud providers.
You can access them from anywhere, using just a browser or command line.
You can scale up or down instantly depending on your needs.
Simple Analogy
Think of the cloud like electricity.
You don’t need your own power plant at home — you just plug into the grid and pay for what you use.
The cloud works the same way — it’s computing power on-demand.
Types of Cloud Services
| Type | What It Means | Example |
| IaaS (Infrastructure as a Service) | Rent servers and networking hardware | Azure VMs, AWS EC2 |
| PaaS (Platform as a Service) | Use ready-to-go platforms to build apps | Azure App Service, Google App Engine |
| SaaS (Software as a Service) | Use software through the browser | Gmail, Microsoft 365, Zoom |
Why the Cloud Matters
Faster to build and deploy apps
Cheaper (no hardware to buy upfront)
Scalable (grow or shrink instantly)
Secure (built-in updates, backups, and compliance tools)
So What Is Network Security in the Cloud?
Network Security refers to the set of technologies, configurations, and policies used to protect your cloud infrastructure from unauthorized access, misuse, or attacks. This includes controlling who can talk to what, how they connect, and what kind of traffic is allowed in and out.
In Azure, network security starts with properly isolating resources using Virtual Networks (VNets) and then layering protection using:
Network Security Groups (NSGs)
Application Security Groups (NSGs)
Azure Firewall
Distributed Denial-of-Service (DDoS) Protection
think of vnets as your own isolated network environment in the cloud, in this case “microsoft’s big cloud” called Azure. And with vnets we can create sub divisions called subnets to separate concerns. Below is the detailed explanation:
Virtual Networks (VNets) in Azure
An Azure Virtual Network (VNet) is the fundamental building block for private networking in Azure. It’s essentially your own isolated network environment in the cloud, similar to a traditional network in your on-premises datacenter.
With a VNet, you can:
Host and securely connect Azure resources like Virtual Machines (VMs), App Services, Azure Kubernetes Service, and more.
Define your own IP address space, subnets, routing policies, and security settings.
Connect to other VNets, on-prem networks, or the public internet using VPN gateways, ExpressRoute, or peering.
VNets provide logical isolation and lets you build secure, isolated environments for your applications, and give you control over how traffic flows between resources and to/from the internet. — Each VNet is independent, even if it’s in the same Azure region and subscription.
Subnets in Azure
A subnet is a smaller range of IP addresses within a VNet, used to divide the network into more manageable sections.
In Azure, subnets help you:
Apply Network Security Groups (NSGs) to specific subnets for traffic control.
Enforce routing rules, firewall policies, or service endpoints on a per-subnet basis.
For example, you might have:
A web subnet that allows HTTP/HTTPS inbound traffic from the internet.
An application subnet that only communicates with the web and database tiers.
A database subnet that blocks all internet traffic and only accepts traffic from the app subnet.
Why Does It Matter?
Misconfigured networks are one of the most common causes of security incidents in the cloud. For example:
Leaving RDP (port 3389) or SSH (port 22) open to the internet exposes VMs to brute-force attacks.
Allowing unrestricted traffic to resources can lead to malware injection, data breaches, or denial-of-service attacks.
By applying least privilege, segmentation, and traffic filtering, you reduce the attack surface and make your infrastructure much harder to compromise.
Key Concepts & Services
| Concept | What It Does | Why It’s Important |
| Virtual Network (VNet) | A private network space in Azure where resources (VMs, services) communicate securely. | Creates isolation and control within your Azure environment. Think of it as your cloud’s internal network. |
| Network Security Group (NSG) | A set of inbound/outbound rules that control traffic to resources, typically at the subnet or NIC level. | Acts as a basic firewall to allow or block specific traffic. Useful for enforcing tight access control. |
| Azure Firewall | A cloud-native, fully managed firewall with built-in high availability and scalability. | Adds a centralized layer of control for logging, rule management, FQDN filtering, and threat intelligence. |
| DDoS Protection | Monitors and auto-mitigates volumetric or protocol-based attacks that try to overwhelm your network. | Protects apps and services from availability disruptions caused by large-scale traffic floods. |
Real-World Analogy
Think of your cloud infrastructure like a secure office building:
The VNet is the building and its internal hallways.
NSGs are like access cards controlling who can open which doors.
Azure Firewall is security at the front gate with CCTV and a guest list.
DDoS Protection is your backup response team when a mob rushes the gate.
Summary
This challenge is more about learning to think like a defender. You'll gain practical experience applying defense-in-depth in a cloud-native environment.
By the end of this, you’ll walk away with a better understanding of:
How to design secure network boundaries
How to enforce controlled access
How to think proactively about threats in the cloud
Written for the SecureCloudX Network Security Challenge. Join Now: https://securecloudx.pages.dev/day2
Subscribe to my newsletter
Read articles from Ronney Otieno directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ronney Otieno
Ronney Otieno
"Cloud Security Engineer | Exploring Cloud Security, DevOps, and Software Engineering | Sharing my learning journey to inspire and grow 🚀 | Open to internships and collaborations in Cloud Security."