Understanding Ethereum’s Consensus Mechanism: A Complete Guide to Proof of Stake
 JVC
JVCWhat is a Consensus Mechanism?
Imagine you and your friends are trying to decide which movie to watch tonight. Without a way to agree, you might end up splitting into different groups or arguing endlessly. A consensus mechanism is like the method your group uses to reach agreement — perhaps you vote, discuss, or use some other process to ensure everyone agrees on the final decision.
In the world of blockchain technology, a consensus mechanism serves a similar purpose but on a much larger scale. It’s the system that allows thousands of computers around the world to agree on what transactions are valid and what the current state of the blockchain should be. Without this agreement, the blockchain would fracture into different versions, making it unreliable and unusable.
Think of a blockchain as a digital ledger that records all transactions. Just like a bank needs to ensure all its branches have the same account balances, a blockchain network needs all its computers (called “nodes”) to agree on the same transaction history. A consensus mechanism is the set of rules, protocols, and incentives that makes this agreement possible.
The Two Main Types of Consensus Mechanism
Proof of Work
Bitcoin, the first successful cryptocurrency, introduced a consensus mechanism called Proof of Work (PoW). In this system, computers called “miners” compete to solve complex mathematical puzzles. The first miner to solve the puzzle gets to add the next block of transactions to the blockchain and receives a reward in cryptocurrency.
Here’s how Proof of Work operates:
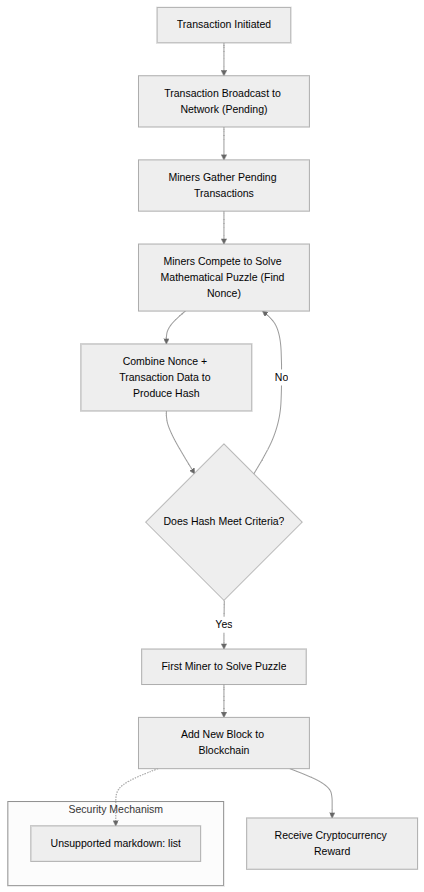
Flowchart of Proof of Work (POW) mechanism.
Block Creation Process: Miners gather pending transactions and attempt to create a new block. They must find a specific number (called a “nonce”) that, when combined with the transaction data, produces a hash (a unique digital fingerprint) that meets certain criteria. This process requires enormous computational power and energy consumption.
Security Through Energy: The security of Proof of Work comes from the fact that changing any past transaction would require redoing all the computational work for that block and every subsequent block. Since this would require controlling more than 51% of the network’s total computing power, it becomes economically unfeasible for most potential attackers.
Ethereum originally used Proof of Work but transitioned to a different system called Proof of Stake in 2022. This change was driven by environmental concerns and the desire for greater efficiency.
Proof of Stake
Proof of Stake (PoS) represents a fundamental shift in how blockchain networks reach consensus. Instead of miners competing with computational power, PoS relies on validators who “stake” their cryptocurrency as collateral to participate in the network’s security.
How Proof of Stake Works:
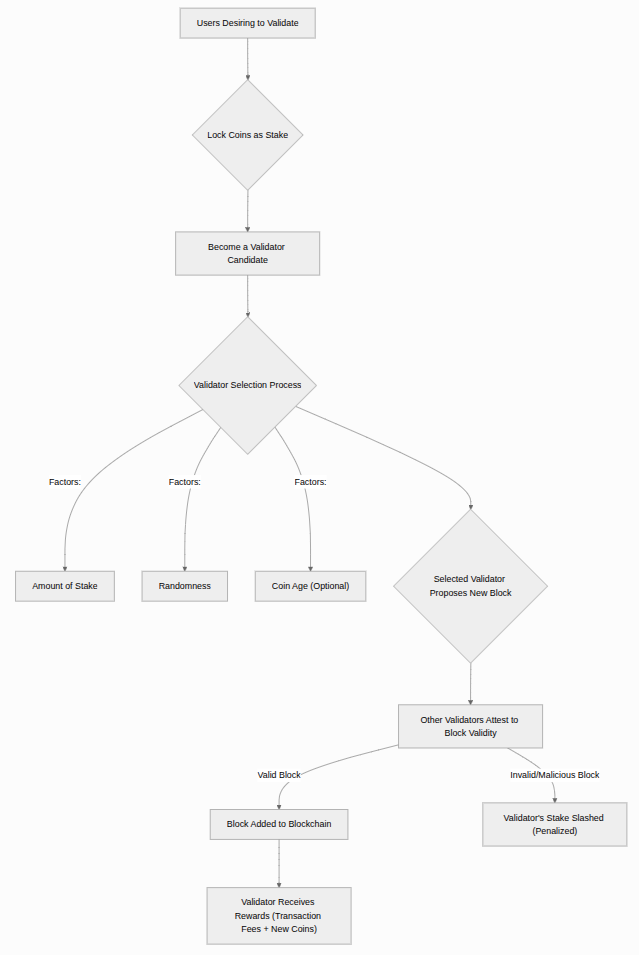
In Ethereum’s Proof of Stake system, participants must deposit 32 ETH (Ethereum’s native cryptocurrency) to become a validator. This deposit acts as a security bond — validators earn rewards for honest behavior but lose part of their stake if they act maliciously.
Block Creation in Proof of Stake: Every 12 seconds, the network randomly selects one validator to propose a new block. This validator bundles pending transactions into a block and broadcasts it to the network. Other validators then check the block’s validity and vote on whether to accept it. If the majority agrees, the block becomes part of the official blockchain.
Why Proof of Stake is More Efficient: Unlike Proof of Work, which requires massive energy consumption for mining, Proof of Stake uses minimal energy. Validators don’t need to run energy-intensive computations; they simply need to run software that validates transactions and participates in the consensus process.
Understanding Ethereum’s Specific Implementation
Ethereum uses a sophisticated Proof of Stake system called “Gasper,” which combines two important components:
Casper FFG (Friendly Finality Gadget): This provides “finality” to blocks, meaning that once a block is finalized, it cannot be changed or removed from the blockchain. This happens every 32 blocks (called an “epoch”).
GHOST Fork-Choice Rule: When validators see multiple possible versions of the blockchain, this rule helps them choose which version to follow by selecting the chain with the most validator support.
The Reward System: Encouraging Good Behavior
Ethereum’s Proof of Stake system uses a carefully designed reward structure to encourage validators to act honestly and maintain network security.
How Rewards Are Calculated
Every validator can earn rewards through several activities:
Source Vote Rewards: Validators earn rewards for correctly identifying and voting on checkpoint blocks that mark the beginning of each epoch (a period of 32 blocks).
Target Vote Rewards: These rewards come from correctly voting on the checkpoint block that should end the current epoch.
Head Vote Rewards: Validators earn additional rewards for correctly identifying the most recent valid block at the head of the blockchain.
Block Proposal Rewards: When randomly selected to propose a new block, validators earn extra rewards for including valid transactions and attestations from other validators.
Sync Committee Participation: Some validators are chosen to participate in special committees that help newly joining nodes sync with the network, earning additional rewards.
The system calculates a “base reward” for each validator based on their stake and the total number of active validators. Interestingly, as more validators join the network, the individual rewards decrease, but the overall security increases.
The Penalty System: Discouraging Bad Behavior
Just as important as rewards are the penalties that discourage malicious or careless behavior:
Missed Duties: If a validator fails to vote or votes late, they lose potential rewards. The penalty typically equals the reward they would have earned.
Inactivity Penalties: When the network can’t finalize blocks (usually due to too many offline validators), inactive validators gradually lose their staked ETH until the network can resume normal operation.
Slashing: This is the most severe penalty, reserved for clearly malicious behavior such as:
Proposing multiple conflicting blocks for the same time slot
Voting for conflicting blocks
Attempting to change finalized history
When slashed, a validator immediately loses about 1/32 of their stake, is removed from the network, and faces additional penalties that increase if many validators are slashed simultaneously.
Security Considerations and Attack Vectors
Understanding how Ethereum’s Proof of Stake system can be attacked helps us appreciate its security measures.
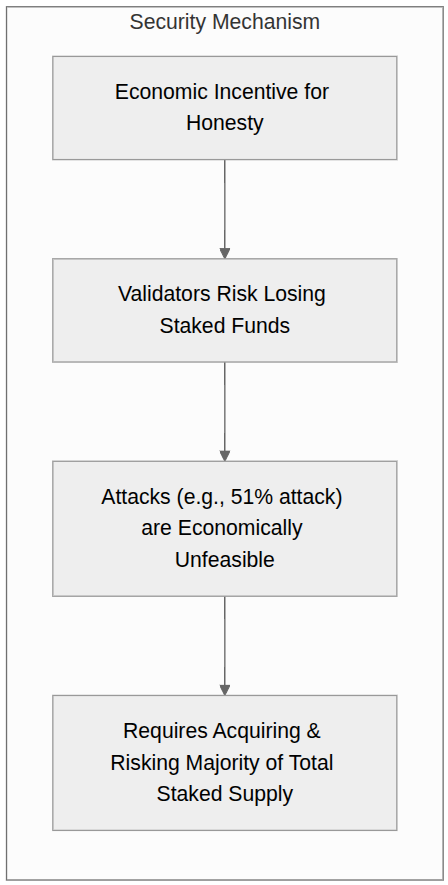
Small-Scale Attacks (Using Less Than 33% of Total Stake)
Reorg Attacks: An attacker might try to reorganize recent blocks to exclude certain transactions or create temporary confusion. However, Ethereum’s “proposer boosting” mechanism makes blocks from timely, honest validators significantly harder to displace.
Balancing Attacks: In theory, an attacker could try to split the validator set by broadcasting conflicting blocks to different groups of validators. However, Ethereum’s fork-choice algorithm has been specifically designed to resist such manipulation.
Finality Delay Attacks: An attacker might try to prevent the network from finalizing blocks by withholding votes or creating confusion about which blocks should be finalized. The network’s design makes such attacks extremely difficult and expensive.
Medium-Scale Attacks (Using 33–50% of Total Stake)
With about one-third of the total staked ETH, an attacker could potentially prevent the network from finalizing new blocks. However, Ethereum’s “inactivity leak” mechanism gradually reduces the stake of non-participating validators, eventually allowing the honest majority to regain control.
This type of attack would be enormously expensive, requiring the attacker to control hundreds of thousands of ETH (worth billions of dollars) and accept the gradual loss of this stake through inactivity penalties.
Large-Scale Attacks (Using More Than 50% of Total Stake)
An attacker controlling more than half the total stake could potentially:
Censor specific transactions
Reorganize recent blocks
Control which transactions get included in new blocks
However, such an attack would require an investment of approximately $19 billion USD at current ETH prices, making it one of the most expensive attacks possible in the cryptocurrency space.
The Ultimate Attack: Controlling 66% or More
With two-thirds of the total stake, an attacker could theoretically finalize their own version of the blockchain, potentially rewriting history and reversing past transactions. However, this would require an investment of over $25 billion USD and would likely trigger a community response.
The Social Layer: Humanity as the Final Defense
One of Ethereum’s unique strengths is its recognition that technology alone cannot solve every problem. The “social layer” — the human community of users, developers, and stakeholders — serves as the ultimate defense against attacks.
If a malicious actor somehow managed to attack the network successfully, the Ethereum community could coordinate to:
Forcibly remove the attacker’s validators from the network
Adopt an alternative version of the blockchain that excludes the attack
Implement additional penalties against the attacker’s stake
This social coordination has happened before in Ethereum’s history and represents a powerful deterrent against large-scale attacks.
Why This System Works
Ethereum’s Proof of Stake system succeeds because it aligns economic incentives with network security:
High Cost of Attack: Attacking the network requires enormous financial resources that would be lost if the attack is detected and the community responds.
Clear Consequences: The penalty system ensures that malicious behavior is economically punishing, while honest behavior is rewarded.
Gradual Penalties: Rather than imposing harsh penalties immediately, the system often gives validators time to correct their behavior, reducing the risk of accidental losses.
Community Oversight: The social layer provides a safety net that can respond to attacks that might not be fully covered by the technical protocols.
The Future of Consensus
Ethereum’s Proof of Stake system continues to evolve. Researchers are working on improvements such as:
Single Slot Finality: Reducing the time it takes for blocks to become finalized from about 15 minutes to just 12 seconds.
Secret Leader Election: Hiding the identity of the next block proposer to prevent targeted attacks.
View Merge: Helping validators synchronize their view of the blockchain more effectively.
These improvements will make the system even more secure and efficient while maintaining its core principle of economic security through staked assets.
Conclusion
Ethereum’s transition from Proof of Work to Proof of Stake represents one of the most significant technological achievements in blockchain history. By replacing energy-intensive mining with economic staking, Ethereum has created a system that is more environmentally sustainable while maintaining strong security guarantees.
The system’s elegant design aligns economic incentives with network security, making attacks extremely expensive while rewarding honest participation. The combination of technical protocols, economic incentives, and social coordination creates multiple layers of defense that protect the network against various types of attacks.
As the system continues to evolve and improve, it serves as a model for other blockchain networks seeking to balance security, efficiency, and decentralization. Understanding these mechanisms helps us appreciate not just how Ethereum works, but how careful design and community coordination can create robust, decentralized systems that serve millions of users worldwide.
The success of Ethereum’s Proof of Stake system demonstrates that blockchain technology can evolve and improve while maintaining the core principles of decentralization and security that make these networks valuable. As we move forward, these lessons will undoubtedly influence the design of future blockchain systems and the broader development of decentralized technologies.
Subscribe to my newsletter
Read articles from JVC directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
