Ethereum's Proof of Stake: its attack, its defense
 Ifeoluwa Sanni
Ifeoluwa Sanni
Search
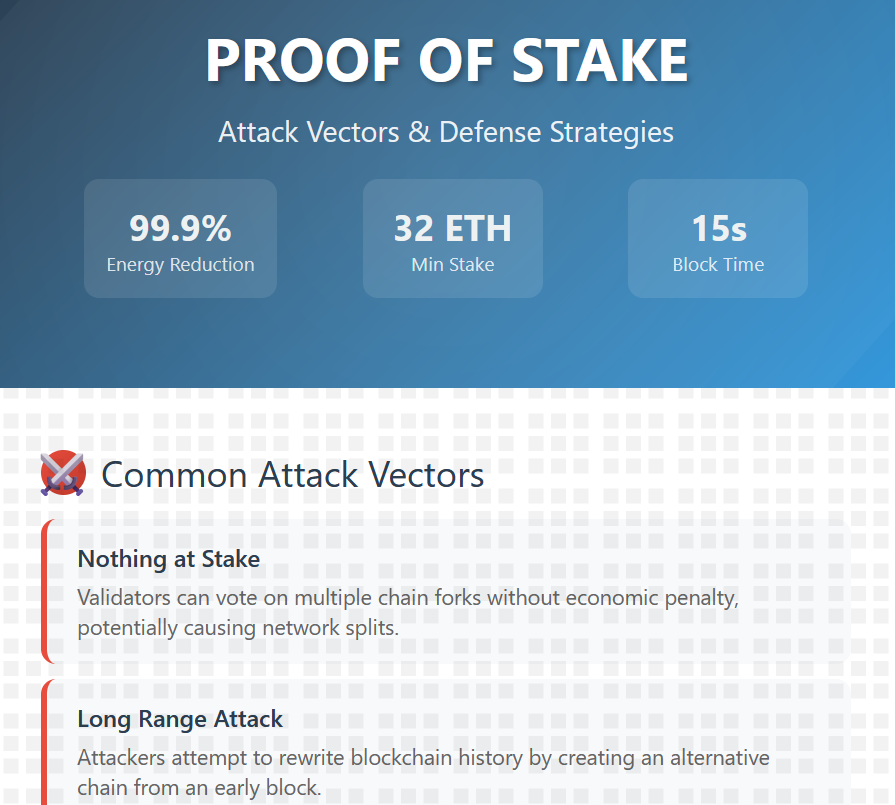
Can Ethereum be attacked?
Ethereum switched from proof-of-work to proof-of-stake in September 2022 because PoS is more secure, less energy-intensive, and better for implementing new scaling solutions.
What is Proof-of-Stake?
Proof-of-stake in Ethereum is a mechanism where validators must put a valuable asset into the network, which can be forfeited if they act dishonestly. To be a validator on the Ethereum network, you have to stake 32ETH.
Validator
Requirements to be a validator: Must deposit 32 ETH into the deposit contract and run three separate pieces of software:
Execution client
Consensus client
Validator client
Process: Users join an activation queue that limits the rate of new validators joining the network
Responsibilities: The validator checks the validity of new blocks and occasionally creates and propagates new blocks itself.
Penalty: Staked ETH can be destroyed if they try to defraud the network
Network Timing Structure
Slots: 12 seconds each
Epochs: 32 slots each
Block Proposer: One validator randomly selected per slot to create new blocks
Committee: Validators are randomly chosen for each slot to vote on block validity
Attestations: Validator votes that determine block validity

Transaction Execution Process
User creates and signs a transaction with private key via a wallet, behind the scenes, this means that a user is making a request to the node via the Ethereum RPC(Remote Procedure Call) API. The user defines the amount of gas he/she is prepared to pay as a tip to the validator, which will be paid to the validators when base fees get burnt.
The transaction is submitted to the execution client for validity verification.
Valid transactions are added to the local mempool (A list of pending transactions)and broadcast to the network.
Block proposer (randomly selected via RANDAO) bundles transactions into an execution payload.
Execution payload wrapped in beacon block with additional consensus information.
Other nodes receive the beacon block and re-execute transactions locally.
Validators attest to block validity
Blocks are added to the local database of the attesting nodes
Finality
Transaction finality occurs when it’s part of a block that can’t change without burning large amounts of ETH
Checkpoints: The First block in each epoch serves as a checkpoint
Justification: Checkpoints with votes from at least two-thirds of the total staked ETH become “justified”
Finalization: Previously justified checkpoints become “finalized”
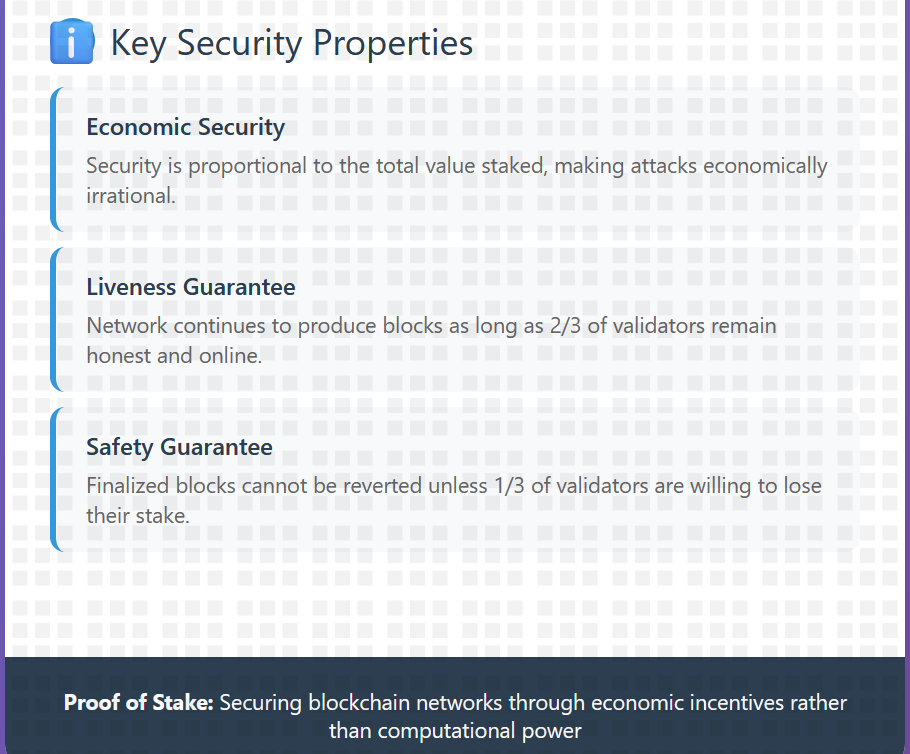
Security: Reverting a finalized block requires the attacker to lose at least one-third of the total staked ETH supply
Crypto-Economic Security
Rewards: Validators are paid in ETH for proper participation.
Penalties: Validators lose ETH rewards for non-participation.
Slashing: Dishonest behaviour results in stake destruction
Dishonest behaviours include proposing multiple blocks in single slot (equivocating) and submitting contradictory attestations
Correlation Penalty: The Amount slashed depends on how many validators are slashed simultaneously (1% for a single validator, up to 100% for mass slashing)
Exit Process: 36-day forced exit period with penalties on Days 1, 18, and final ejection on Day 36
Fork Choice Algorithm
LMD-GHOST: Algorithm used to decide which fork to favour when validators have different views
Weight-Based: Identifies the fork with the greatest weight of attestations in its history
Security Considerations
51% Attack Risk: Still exists, but more costly for attackers
Community Defence: Honest validators can counter-attack by building on the minority chain and removing attackers
Other Attack Vectors:
Long-range attacks (neutralized by the finality gadget)
Short-range reorgs (mitigated by proposer boosting)
Bouncing and balancing attacks (mitigated by proposer boosting)
Avalanche attacks (neutralized by fork choice rules)
Inactivity Leak: Mechanism to defend against validators preventing finality by voting with one-third of the total stake
Advantages vs Disadvantages
✓ Pros
Easier individual participation in network security
More decentralized (economies of scale don’t apply like in PoW mining)
Greater crypto-economic security than proof-of-work
Less ETH issuance is required for network incentives
Validator nodes can run on normal laptops
Staking pools allow participation without 32 ETH
✓ Cons
Younger and less battle-tested than proof-of-work.
More complex to implement than proof-of-work.
Users need to run three pieces of software to participate.
Comparison to Proof-of-Work
Energy Efficiency: No need for energy-intensive computations
Lower Barriers: Reduced hardware requirements, no need for elite hardware
Reduced Centralization: Should lead to more nodes securing the network
Economic Efficiency: Less ETH issuance required due to low energy requirements
Attack Costs: 51% attacks are more costly due to economic penalties
Recovery Options: The Community can use social recovery for an honest chain if attacked
Ethereum Proof-of-Stake Attack and Defense
Ethereum attackers realistically target three main outcomes:
1. Reorgs
This is the reshuffling of blocks into a new order with addition/subtraction of blocks. This enables double-spending, Value extraction through MEV (front-running/back-running), Censorship (preventing certain transactions)
- The Extreme form: Finality reversion (removing previously finalized blocks). This is only possible if the attacker destroys more than ⅓ of the total staked ether.
2. Double Finality
This is when two forks are finalizing simultaneously, creating a permanent chain schism. The attacker will be willing to risk 34% of the total staked ether. The community is forced to coordinate off-chain to choose which chain to follow.
3. Finality Delay
This occurs when preventing the network from finalizing sections of the chain. It makes financial applications hard to trust. It would likely disrupt Ethereum rather than direct profit.
Attack Methods
a)Layer 0 (Social Layer) Attacks
Target: The social foundation underlying Ethereum
Examples:
Misinformation campaigns: Erode community trust in roadmap/developers
Developer intimidation: Targeted attacks causing voluntary developer exit.
Over-zealous regulation: Rapidly disincentivizing participation
Malicious infiltration: Bad actors are slowing progress through bike-shedding
Bribery: Influencing key ecosystem players
Defense Strategies:
Maintain a high signal-to-noise ratio in public information
Clear mission statement and governance protocols
Open, welcoming community (avoiding tribalism)
Quality information through blogs, specs, books, and podcasts.
EIP (Ethereum Improvement Proposal) review process
b) Protocol-Level Attacks
Small-Stake Attacks (Using Small Amounts of ETH)
Basic Attack Types:
Under-activity: Failing to attest/propose or doing so late
Over-activity: Proposing/attesting too many times in a slot
Specific Attack Vectors:
1. One-Block Ex Ante Reorg
2. Balancing Attacks
3. Bouncing Attacks
4. Avalanche Attacks
5. Finality Delay Attacks
6. Long Range Attacks
7. Denial of Service (DoS)
Large-Stake Attacks
1.33% Stake Attacks
2. 34% Stake Attacks
3. 50% Stake Attacks
4. >50% Stake Attacks
4. 66% Stake Attacks
Defense Mechanisms
Technical Defenses
Proposer Boosting: Additional weighting for prompt messages vs. slow ones
Attestation Deadlines: Limit when justified checkpoints can switch
LMD-GHOST Algorithm: Latest-message-driven fork choice, discards equivocations
Inactivity Leak: Gradually reduces the stake of non-attesting validators
Correlation Penalties: Higher slashing for coordinated attacks
Future Upgrades
View-Merge: Attesters freeze fork choice view before the slot begins
Single-Slot Finality: Finalize chain after just one slot
Single Secret Leader Elections: Hide the block proposer's identity until proposal time
Social Layer Defense (Layer 0)
The Ultimate Backstop: Community coordination when technical defenses fail
Response Options:
Minimal: Forcibly exit attackers without additional penalty
Moderate: Revoke past rewards
Severe: Burn up to 100% of attackers’ staked capital
Community Decisions:
Whether to follow dishonest but canonical chain or honest alternative
How to handle rolled-back transactions
Balance between “code is law” and community protection
Challenges:
Governance complexity
Potential user losses from chain switch
Disruption to application layer
Institutional opposition to protecting gains
Coordination Efforts:
Calls to rehearse community response to >51% attacks
Discussions on targeted, specific punishments
Minimizing effects on honest users
Economic Deterrents
Huge costs: Attacks require billions of dollars in staked ether
Risk of loss: Attackers’ stakes can be destroyed or devalued
Social coordination: The Community can adopt an honest fork, making the attacker’s stake worthless.
Comparative Security
Risk lower than proof-of-work equivalents
Built-in incentive layer protects against most malfeasance
Multiple defensive layers from technical to social
Importance of Social Layer
Investment in a cohesive social layer with aligned values is crucial
The community’s ability to respond out-of-band is a strong attack deterrent
The race between the attacker and the community coordination determines the outcome.
Conclusion
While various attack vectors exist, Ethereum’s proof-of-stake system provides strong security through:
Economic incentives that make attacks extremely expensive
Technical defenses that close known attack vectors
Social coordination as the ultimate backstop
Multiple threshold levels that increase attack costs significantly
The combination of these factors makes successful attacks highly unlikely and economically irrational for most potential attackers.
References: https://ethereum.org/en/developers/docs/consensus-mechanisms/pos/, https://ethereum.org/en/developers/docs/consensus-mechanisms/pos/attack-and-defense/
Subscribe to my newsletter
Read articles from Ifeoluwa Sanni directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ifeoluwa Sanni
Ifeoluwa Sanni
I am a Web3 Software developer