ToolShell: Critical SharePoint Zero‑Day RCE in Active Exploitation
 FPT Metrodata Indonesia
FPT Metrodata Indonesia
🚨 Overview
A critical zero‑day Remote Code Execution (RCE) vulnerability in on‑premises Microsoft SharePoint Server—tracked as CVE‑2025‑53770 (with a related CVE‑2025‑53771)—is being actively exploited worldwide. The attack chain, dubbed ToolShell, allows unauthenticated attackers to execute code, deploy stealth web shells, and steal MachineKey secrets, compromising entire environments.
🔍 Technical Deep Dive
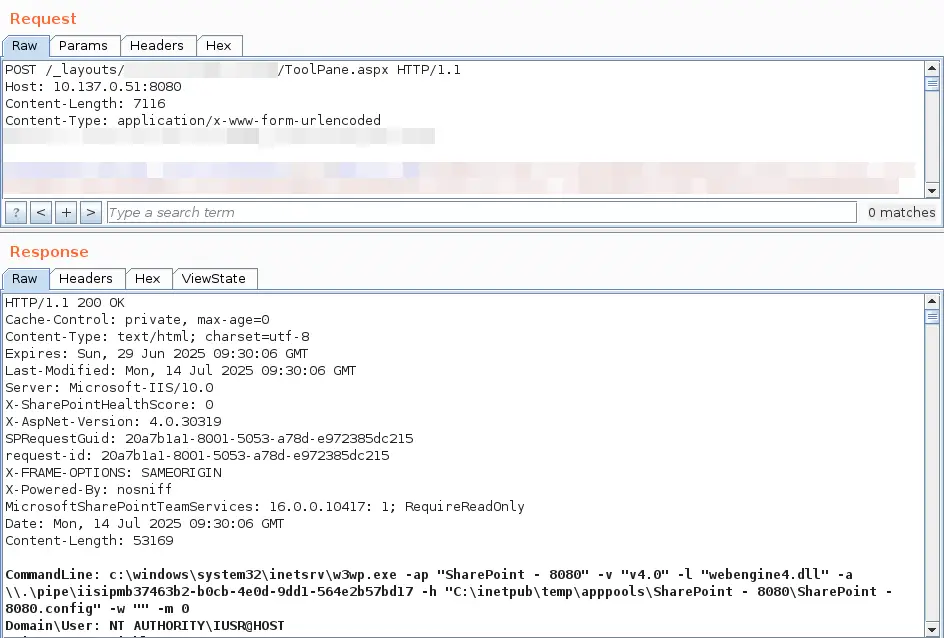
Root Cause
A deserialization flaw in SharePoint’s
__VIEWSTATEhandling enables unauthenticated RCE (CVSS 9.8—network, no privileges, no user interaction).Exploitation leverages the
/_layouts/15/ToolPane.aspx?DisplayMode=Editendpoint to drop malicious payloads.
Attack Chain (“ToolShell”)
Step 1: Attacker sends a crafted POST request to
ToolPane.aspx?DisplayMode=Edit.Step 2: A stealth web shell (e.g.,
spinstall0.aspx) is uploaded into the SharePoint layouts directory.Step 3: The web shell extracts the server’s ASP.NET MachineKey, enabling forged
__VIEWSTATEpayloads for persistence.
Persistence & Evasion
Stolen MachineKey allows attackers to sign valid state objects and evade standard verification checks.
Even after patching, unless the MachineKey is rotated, the old key remains valid.
🌍 Real‑World Impact
Timeline: First in‑the‑wild exploitation from July 18–20, 2025.
Scope: Dozens to over 75 organizations across sectors (education, government, finance).
Regulatory Response: Added to CISA’s Known Exploited Vulnerabilities list; U.S. federal agencies mandated to patch by July 21, 2025.
🛡️ Mitigation & Response
Microsoft Emergency Guidance
Patches Released For:
SharePoint Server 2019
SharePoint Server Subscription Edition
(SharePoint 2016 patch pending)
Immediate Actions:
Enable AMSI integration and deploy Microsoft Defender AV on all SharePoint servers.
Deploy Defender for Endpoint or equivalent EDR solution.
Rotate ASP.NET MachineKeys post‑patch and restart IIS.
CISA Recommendations
Disconnect public‑facing SharePoint servers if AMSI/EDR cannot be enabled immediately.
Monitor IIS logs for POSTs to
ToolPane.aspx?DisplayMode=Edit.Block known attacker IP ranges observed during the July 18–19 exploitation window.
🔍 Hunting & Indicators of Compromise (IOCs)
| IOC Type | Details |
| Web Shell Filename | spinstall0.aspx inside …\LAYOUTS\15\ |
| Suspicious Requests | POST to /_layouts/15/ToolPane.aspx?DisplayMode=Edit |
| Malicious Referrer | Abnormal Referer: _layouts/SignOut.aspx headers |
| Example IPs | 96.9.125.147 · 107.191.58.76 · 104.238.159.149 |
| Defender Alerts | Exploit:Script/SuspSignoutReq.A · Trojan:Win32/HijackSharePointServer.A |
🚨 Immediate Action Plan
Apply Emergency Patches
- Install today on all affected SharePoint versions.
Enable/Deploy AMSI & Defender
- Or isolate servers until protection is in place.
Rotate MachineKeys
- Generate new keys and restart IIS to invalidate old ones.
Deploy EDR & Hunt for IOCs
- Use the table above to guide log searches and alerts.
Update Network Defenses
- Block attacker IPs and tighten WAF/IPS rules.
✅ Conclusion
ToolShell represents a zero‑minute vulnerability scenario: exploitation began just as emergency patches were released. If you manage on‑prem SharePoint, act now—patch, enable protections, rotate keys, and hunt for any signs of compromise.
Subscribe to my newsletter
Read articles from FPT Metrodata Indonesia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

FPT Metrodata Indonesia
FPT Metrodata Indonesia
PT FPT Metrodata Indonesia (FMI) is a joint venture between FPT IS and Metrodata Electronics, focusing on providing Cybersecurity-as-a-Service—including SOC, managed security, professional services, consulting, and threat intelligence—to support Indonesia’s rapidly growing digital economy. FMI is expanding into AI and cloud GPU services to deliver innovative protection and solutions for enterprises. Learn more at https://fmisec.com.