What is SAML
 Shahrukh Ahmad
Shahrukh AhmadSAML (Security Assertion Markup Language) is an open standard that allows Single Sign-On (SSO) between identity providers (IdP)(eg: Okta,Azure AD) and service providers (SP)(eg:Salesforce,Dropbox,Gmail).
It is XML-based and securely transfers authentication and authorization data between two parties.
Commonly used for
Enterprise SSO (Single Sign-On), cloud-based app access control (eg: salesforce, office365, AWS, Console), and Federated indentity management.
in simple term:
SAML allows user to login once (eg: with their corporate credentials) and access multiple application without re-entering their login details.
Where Is SAML Used
| Use Case | Example |
| 🌐 SSO for Web Apps | Google Workspace login with company AD credentials |
| 🏢 Enterprise Portals | Login to Salesforce, Zoom, Workday using SAML SSO |
| ☁️ Cloud Platforms | Login to AWS, Azure, or GCP via corporate IdP (Azure AD, Okta) |
| 🔐 Third-Party SaaS Tools | SAML lets users log in securely without managing local credentials |
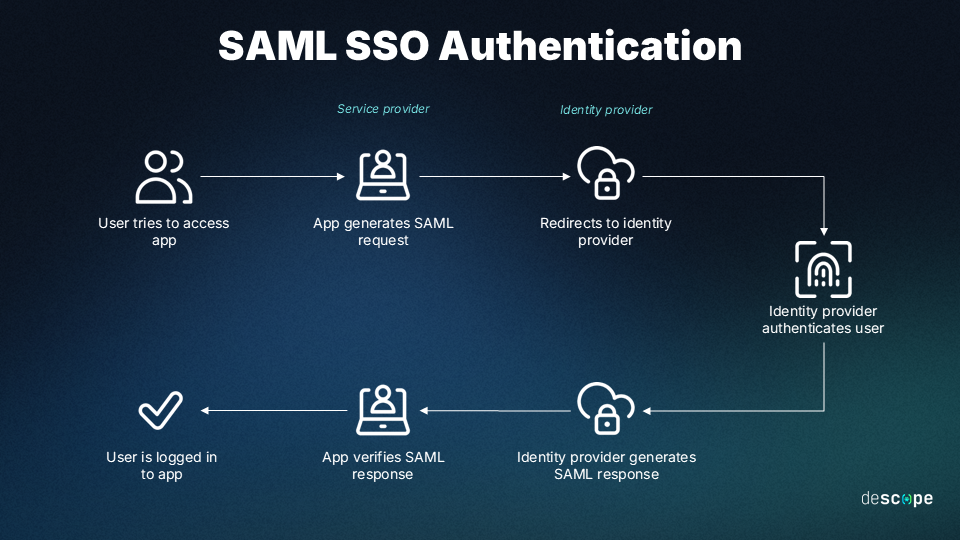
How SAML works
You try to access a service (eg: Salesforce)
The service provider (SP) redirect you to on identity provider(eg:Okta, AD).
you log in to the identity provider
The Identity provider Authenticates you and sends a SAML Aseertion(XML document) to the SP.
The service provider reads this assertion and grants access to the user.
Practice Approach (Build Lab Project)
🔧 Tools You Can Use for Practice
Identity Provider (IdP):
🔹 Azure AD (Free Tier)
🔹 Okta Developer Account (Free)
🔹 ADFS (Active Directory Federation Services – for on-prem)
Service Provider (SP):
🔹 WordPress with SAML Plugin
🔹 Any free SAML demo app (e.g., SAMLTool, OneLogin Demo App)
Real-Life Example: SAML SSO Using Okta + Web App
Scenario:
Company wants users to log in to their internal Leave Management System using Okta SSO, instead of creating separate user accounts in the app.
Step-by-Step Setup:
Step 1: Setup Okta as Identity Provider
Create a free Okta Developer account
Go to Applications > Create App Integration
Choose SAML 2.0
Fill:
Single Sign-On URL – where Okta will POST the SAML assertion (e.g., your app URL)
Audience URI (SP Entity ID) – identifier for your app
Download IdP metadata XML (contains certificate and SSO endpoint)
Step 2: Configure the Web App (Service Provider)
Use a sample SAML-enabled web app or install WordPress + miniOrange SAML Plugin
Enter:
IdP Entity ID
SSO URL
X.509 Certificate (from Okta)
Step 3: Add User in Okta
Add user
employee1@example.comin OktaAssign the app to that user
Step 4: Test the Login Flow
Visit your app (SP)
Click "Login via SSO"
You are redirected to Okta (IdP)
Enter Okta credentials
You are redirected back to app with a SAML assertion
Access is granted based on that token (no password stored in app)
What Is Transferred?
A SAML Assertion (XML-based) is sent from IdP to SP
It includes:
Authentication details
User attributes (name, email, role)
Digital signature
How to Explain in an Interview:
“SAML is an open standard used for secure Single Sign-On.
I implemented a lab where I used Okta as the Identity Provider and a WordPress app as the Service Provider.
I configured SAML 2.0 integration, tested the login flow, and verified how the SAML assertion is securely passed and used to authenticate the user.”
Top 12 SAML Interview Questions with Sample Answers
Q1. What is SAML?
Answer (Say this confidently):
“SAML stands for Security Assertion Markup Language.
It’s an open standard based on XML used to exchange authentication and authorization information between an Identity Provider (IdP) and a Service Provider (SP), primarily used for Single Sign-On (SSO).”
Q2. Why do we use SAML?
Answer:
“SAML allows Single Sign-On, so users can log in once and access multiple applications securely.
It improves security by centralizing authentication, reduces password fatigue, and helps organizations enforce access policies from a single identity source like Okta or Azure AD.”
Q3. What are the main components of SAML?
Answer:
Identity Provider (IdP) – Authenticates the user (e.g., Okta, Azure AD)
Service Provider (SP) – The app or service the user wants to access (e.g., Salesforce, WordPress)
SAML Assertion – An XML token sent by the IdP to the SP with user identity and access permissions
Q4. What is a SAML Assertion?
Answer:
“A SAML assertion is an XML document that includes the user's identity and access rights.
It is digitally signed by the Identity Provider to ensure it's tamper-proof.
The Service Provider uses it to grant access without needing the user’s password.”
Q5. What is the difference between IdP and SP?
Answer:
IdP (Identity Provider) authenticates the user (e.g., Okta, ADFS)
SP (Service Provider) provides the service the user is trying to access (e.g., Gmail, Salesforce)
The SP trusts the IdP to validate the user's identity via the SAML token.
Q6. How does the SAML login flow work?
Answer (Say this step-by-step):
User tries to access a Service Provider (e.g., app)
The SP redirects the user to the Identity Provider (IdP)
The IdP authenticates the user
The IdP sends back a SAML assertion to the SP via browser
SP validates the assertion and logs the user in
Q7. What are the different bindings used in SAML?
Answer:
Common bindings include:
HTTP Redirect Binding – Sends requests via URL (used for initial login requests)
HTTP POST Binding – Sends SAML assertions via HTML form (most common for responses)
HTTP Artifact Binding – Passes reference instead of full assertion
Q8. What’s the difference between SAML and OAuth?
Answer:
| Feature | SAML | OAuth |
| Purpose | SSO (Authentication) | Authorization (API access) |
| Format | XML-based | JSON or Token-based |
| Use Case | Login to apps via IdP | Give apps permission to act on your behalf (e.g., access your Google Drive) |
“SAML is for authentication and used in enterprise SSO.
OAuth is for delegated authorization, often used in mobile and web apps.”
Q9. Can SAML be used for mobile apps?
Answer:
“SAML is XML-based and heavy for mobile apps.
OAuth2 + OpenID Connect (OIDC) is more common for mobile use due to its lightweight JSON format.”
Q10. What’s the role of metadata in SAML?
Answer:
“SAML metadata is an XML file that contains important configuration details like:
Entity ID
SSO URLs
Certificates
Both the IdP and SP exchange metadata to establish trust and enable secure communication.”
Q11. How do you implement SAML in a project?
Answer:
“I set up SAML-based SSO using Okta as the IdP and a WordPress app as the SP.
I configured the SAML integration in Okta, provided the metadata to the app, and enabled login via Okta.
I tested the login flow, verified SAML assertions, and ensured secure SSO was working end-to-end.”
Q12. What are some common issues in SAML and how do you troubleshoot them?
Answer:
Common issues:
Clock skew – Time mismatch between IdP and SP servers
Wrong Entity ID or ACS URL
Expired certificate
Mismatched NameID or user attribute
I troubleshoot using browser dev tools, SAML trace extensions, and server logs to inspect the SAML request/response.
Subscribe to my newsletter
Read articles from Shahrukh Ahmad directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shahrukh Ahmad
Shahrukh Ahmad
Passionate about coding and the limitless possibilities of cloud technology. I thrive on turning ideas into scalable, efficient solutions. Let's connect and explore the exciting synergy between code and the cloud! 🤖 AI / ML🧠| 📊 - Data Science |Azure☁️AWS | Linux🐧| Windows🖥️| Python | JAVA | 🐳 Docker | Git | Gitlab | ⚓️Kubernetes | 🚀 Jenkins CI/CD | 🏗️ terraform | SQL.