🔐 API Authentication Explained: API Key vs JWT vs OAuth
 Nishank Koul
Nishank Koul
Have you ever wondered how websites and apps ensure the right person or system is accessing the right data? Why can you log into your email from your phone but not someone else’s?
That’s the magic of API authentication, a fundamental part of modern app security. Every time you check your bank balance, send a message, or get directions from Google Maps, an API works in the background to fetch that data. But first, the API needs to ask:
Who are you? Should you be allowed to access this data?
API authentication ensures that only authorized users and apps can access protected resources, preventing data leaks, fraud, and misuse.
In this blog, we'll break down three of the most widely used API authentication methods:
API Keys
JWT (JSON Web Tokens)
OAuth 2.0
By the end, you'll understand how each works, when to use them, and their pros and cons.
Why API Authentication Matters?
Imagine if anyone could withdraw money from a bank just by knowing a specific URL. Or post to your Twitter account without logging in. Without authentication, APIs would be wide open to abuse, attacks, and data breaches.
Authentication mechanisms protect sensitive information and ensure that:
Only verified users or systems can make specific API requests
Unauthorized actors are blocked
Access can be tracked and limited
🔑 What Is an API Key?
Think of it as a VIP pass to an exclusive event. Show the pass, and you’re let in, no questions asked.
An API Key is a simple, unique string (like b89f1a4e-a8e7-4a72-abc7-5671efcc12cd) used to authenticate an app or user making requests to an API. It’s often used in basic authentication scenarios where complex security requirements aren’t necessary.
How It Works:
Your app sends the API key with each request.
The API server checks if the key is valid.
If valid, the server processes the request.
Where to Place API Keys:
In URL parameters (⚠️ not secure — easily exposed in logs/browser history)
In HTTP headers (✅ recommended — more secure)
Best Use Cases:
Internal microservices
Public APIs (weather, stock market, etc.)
Rate-limiting and usage tracking
Prototyping and internal tools
Limitations:
No built-in expiration or fine-grained permissions
Easy to leak if not handled properly
No user-specific data or identity validation

🛡️ What Is JWT (JSON Web Token)?
Imagine wearing a tamper-proof wristband at a concert. It proves you’re allowed in without showing your ID every time.
JWT (JSON Web Token) is a self-contained, digitally signed token that securely transmits information about a user or system. It’s widely used in stateless authentication for web and mobile apps.
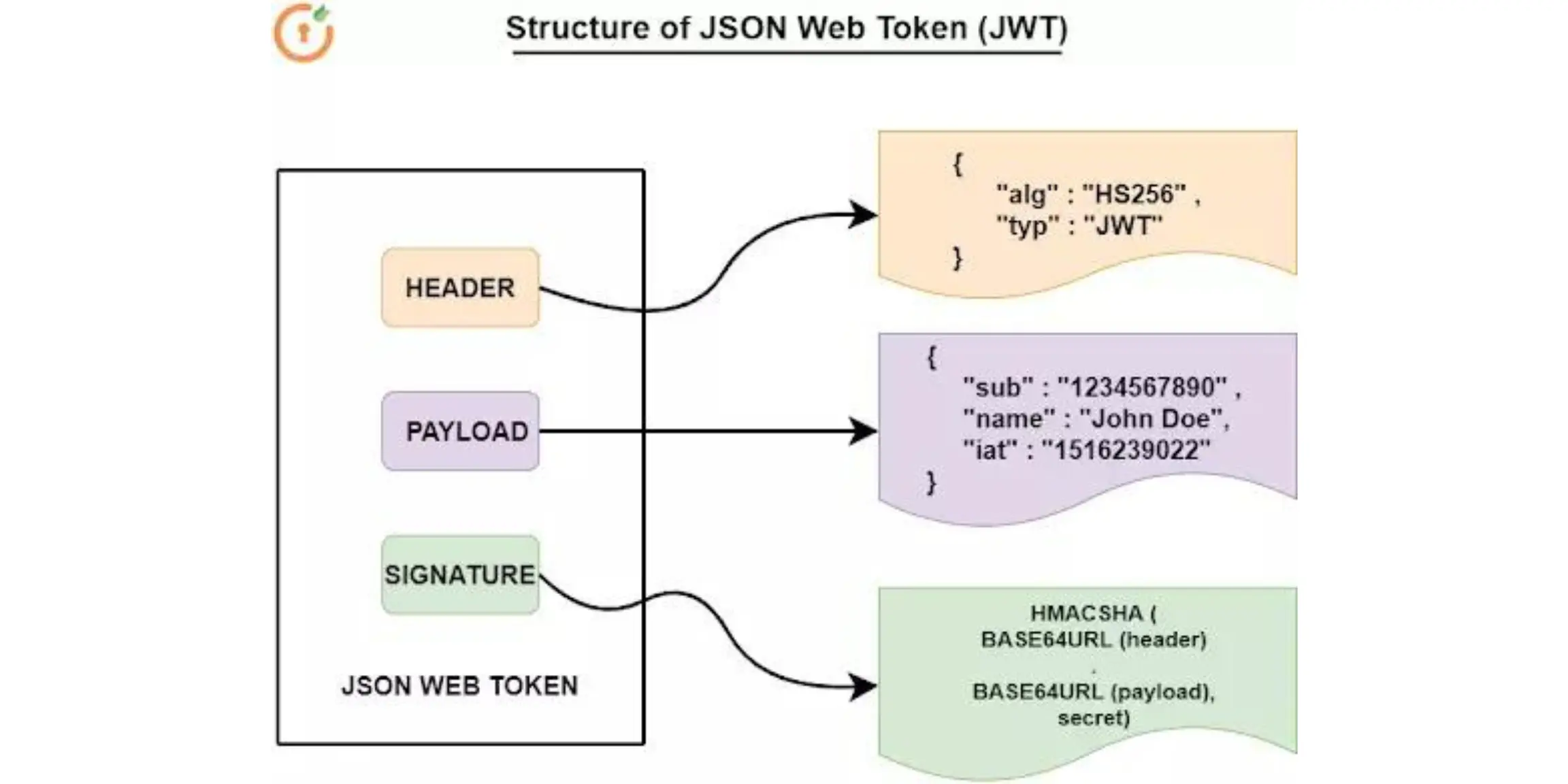
JWT Structure:
A JWT is made up of three parts:
header.payload.signature
Example:eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySWQiOjEyMywicm9sZSI6InVzZXIifQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Header: contains metadata (e.g., algorithm)
Payload – contains claims like user ID, role, expiration
Signature – used to verify that the token hasn’t been tampered with
How JWT Authentication Works:
User logs in with credentials
Server verifies and returns a JWT
Client stores the JWT (e.g., in localStorage or cookies)
JWT is sent with each API request (typically in the
Authorizationheader)Server validates the token and processes the request
Best Use Cases:
Scalable, stateless authentication
SPAs (Single Page Applications)
Mobile apps
APIs where session storage is not feasible
Benefits:
Compact and efficient
Doesn’t require server-side session storage
Verifiable using a secret or public key
Limitations:
If leaked, JWTs can be used until expiry
Cannot be easily revoked without additional infrastructure
Larger in size than API keys
🌐 What Is OAuth 2.0?
Ever used “Login with Google” or “Sign in with Facebook”? That’s OAuth in action.
OAuth 2.0 is an authorization framework that allows apps to access user resources (like profile or calendar) without requiring the user to share their password. It’s ideal for third-party integrations and delegated access.
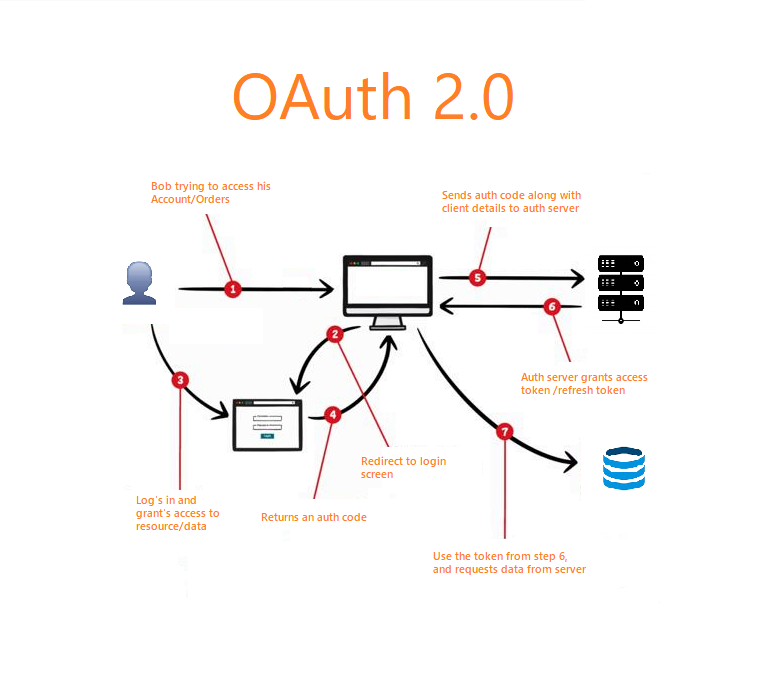
OAuth Flow (Authorization Code Grant):
User chooses to log in with a third-party service (e.g., Google)
They’re redirected to that service and prompted for consent
After approval, an authorization code is sent to the app
The app exchanges the code for an access token
The app uses the token to make API calls on behalf of the user
Best Use Cases:
Social logins
Accessing user data from third-party APIs (Google Drive, Twitter, etc.)
Applications requiring delegated permissions
Benefits:
No need to handle or store passwords
Granular access control via scopes (e.g., read-only email access)
Secure and standardized
Limitations:
More complex to implement
Tokens often expire and require refresh handling
Needs careful handling of redirects and token storage
⚖️ API Key vs JWT vs OAuth: Quick Comparison
| Feature | API Key | JWT | OAuth 2.0 |
| Type | Static token | Signed token | Authorization framework |
| Contains user info? | No | Yes | Yes (via external identity) |
| Scalable | Limited | Yes (stateless) | Yes |
| Expiration support | No | Yes | Yes (with refresh token) |
| Can be revoked? | No (manually) | Not easily | Yes |
| Best for | Simple services | User sessions in apps | 3rd-party logins & delegated access |
When to Use What?
API Keys → Quick, simple, non-sensitive services (internal tools, public APIs)
JWT → Scalable authentication in modern web/mobile apps (user login, dashboards)
OAuth → When users need to authenticate via Google, Facebook, or when accessing third-party data
Pro Tip: Combine methods for enhanced security. For example, use OAuth for user authentication and JWTs for session management.
Subscribe to my newsletter
Read articles from Nishank Koul directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
